Tadawul Information Security Website V 3 0
advertisement
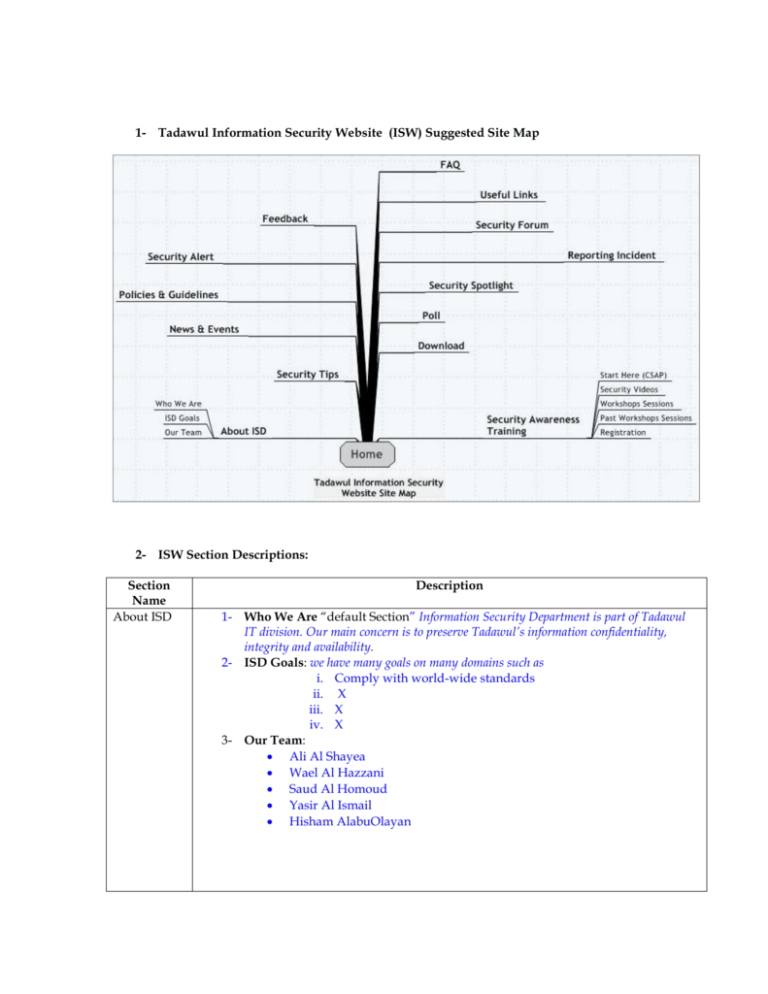
1- Tadawul Information Security Website (ISW) Suggested Site Map 2- ISW Section Descriptions: Section Name About ISD Description 1- Who We Are “default Section” Information Security Department is part of Tadawul IT division. Our main concern is to preserve Tadawul’s information confidentiality, integrity and availability. 2- ISD Goals: we have many goals on many domains such as i. Comply with world-wide standards ii. X iii. X iv. X 3- Our Team: Ali Al Shayea Wael Al Hazzani Saud Al Homoud Yasir Al Ismail Hisham AlabuOlayan Security Spot Light http://www.us-cert.gov/current/index.atom http://digg.com/rss/indexsecurity.xml http://www.sans.org/newsletters/newsbites/rss/ http://rssnewsapps.ziffdavis.com/eweeksecurity.xml http://blogs.securiteam.com/index.php/feed/ Security Tips 1 . Anti Virus - Viruses have are one of the oldest threats to computers. You should be running an active and updated virus scanner at all times. 2 . Firewall - A firewall helps stop people on the Internet getting access to your computer by placing a ‘wall’ between them and your computer. This can be done with software, hardware or a combination of both. 3. Anti Spyware - The Internet’s newest threat is Spyware and Adware. Programmes that people try to load onto your computer. These programmes are designed to either generate someone money by placing advertisements throughout your computer, or to spy on your computer and steal your important information. 4. Back-Up - One of the most important thing you can do is back up your files. In case something does go wrong, your computer breaks down, or you lose your notebook. Normally people don’t realise how much valuable information and files they have on their computer until they are lost. Simply creating a backup onto CD could save you a lot of time in the future. 5. Spam Prevention - Spam, or junk email, is becoming a nightmare. More then three quarters of email is spam. There are may things you can do to help prevent spam. 6. Protecting yourself from Scams - All the computer security in the world wont mean anything if you cant recognise a scam when you see one. Protect your credit card numbers with your life! 7. Staying Safe - What information not to give out. Password Tip’s Here is a tactics to use when choosing a password: * Don't use passwords that are based on personal information that can be easily accessed or guessed * Don't use words that can be found in any dictionary of any language * Develop a mnemonic for remembering complex passwords * Use both lowercase and capital letters * Use a combination of letters, numbers, and special characters * Use different passwords on different systems Security Awareness Training (it should be editable easily from administration interface) This Section is divide to four Subsections: 1- Start Here (CSAP) : 2- Security Videos: 3- Workshops Session: 4- Past Workshops Sessions: 5- Registration on the security awareness workshops includes: a. ISO to put dates, time, location and the capacity (number of seats) of the workshops. User will be able to register, remove & change him self from any workshops he wants. c. User shouldn’t register to the workshop when it reaches its limit, these workshops should be locked for the new users. d. Send a confirmation email to the user contain details about the registered workshop. e. Send reminder to the user. f. ISO should able to see/print all registered /unregistered (from Active Directory “AC”) users and fro each workshop. b. News & Events Reporting Incident Polices & Guidelines Security Alert Today we established our Information Security Website. The site contains useful content and tips and helps staff to maximize there awareness in information security. The link will be provided at installation phase. Useful Link Previously provided in CD. (there must be away for adding/deleting policies. http://isc.sans.org/images/status.gif OR Symantec ThreatCon http://www.cert.org http://www.microsoft.com/security http://www.securityfocus.com http://www.securiteam.com (Network Security) http://www.itsecurityportal.com/network.asp (Web & Internet Security) http://www.itsecurityportal.com/internet_security.asp (Malware & Spyware News) http://www.itsecurityportal.com/malware.asp Security Forum Feedback these links for the moment, it should be easily added through the administration interface. A Forum TISD will use a tools to lets Tadawul users shares there thought regarding Information security This section will contains a form that Tadawul user use to send there feedback to the TISD. FAQ Q. How do malicious web scripts get to my web browser? A malicious web developer may attach a script to something you send to a web site, such as a URL, an element in a form, or a database inquiry. When the web site responds to you, the malicious script comes along, so that it is now on your browser. Among the ways you can potentially expose your web browser to malicious scripts are these: * following untrusted links in web pages, email messages, or newsgroup postings * using interactive forms on an untrustworthy site * viewing dynamically generated pages that contain content developed by anyone but yourself Q. What might happen if my web browser is exposed to a malicious script? Among the possibilities are that an attacker could capture your password and other information you believe is protected. You should also be concerned because malicious scripts can be used to expose restricted parts of your organization's local network (such as their intranet) to attackers who are on the Internet. Some web browsers contain vulnerabilities in the security systems that determine what access a script should have to your computer or other web sites. In the case of these crosszone or cross-domain vulnerabilities, a malicious script could download and install arbitrary software on your computer, or read or modify data on another web site. Malicious scripts can also be used to alter the appearance of the browser, thus making social engineering or "phishing" attacks more successful. For example, a malicious script might open a browser windows outside of the visible screen area or cover the address bar with a spoofed address. Attackers may be able to use malicious scripts to infect cookies with copies of themselves. If the infected cookie is sent back to a vulnerable web site and passed back to your browser, the malicious script may start running again. Note: This is not a vulnerability in web cookies; rather, a malicious script takes advantage of the functionality of cookies. Q. How can I avoid the problem? The most significant impact of this vulnerability can be avoided by disabling all scripting languages. Follow the steps below to turn off options in your web browser that allow malicious scripts to run. If you're not using a current version of Internet Explorer, Netscape, or Mozilla you might need to modify the steps. Note that even with scripting disabled, attackers may still be able to influence the appearance of content provided by a legitimate site by embedding other HTML tags. In particular, malicious use of the <FORM> tag is not prevented by disabling scripting languages. Q. How will turning off the options affect my use of the web? While turning off the options will keep you from being vulnerable to malicious scripts, it will limit the interaction you can have with some web sites. You may notice a difference in functionality when you visit legitimate sites that use scripts running within the browser to add useful features. Q. Should I disable Java applets? The risk associated with Java applets is significantly different from some of the other technologies. Java has a robust security mechanism designed to deal with situations like these that prevents sensitive information from being disclosed or client information from being damaged. However, Java applets written by an attacker can still be loaded while your are viewing a legitimate web page. The problems that can arise are similar to those involving the <FORM> and other HTML tags. For example, an attacker could develop a "Trojan Horse" program that presented misleading information and prompted you for a password. If you failed to recognize the malicious applet for what it was, you could accidentally disclose sensitive information. You must make your own determination about disabling Java applets, based on your tolerance for these risks. If you choose to disable Java, please see the detailed instructions below. Q. Is there any more information available about this problem? The CERT/CC has published an advisory containing more details about the problem, its impact, and ways to deal with it. CA-2000-02 is available from http://www.cert.org/advisories/CA-2000-02.html You can also find information at the vendor URLs listed in the advisory. The CERT/CC has also published a "tech tip" for web page developers and web site administrators, which you might want to pass along to the appropriate people in your organization. This document, "Malicious Content Mitigation for Web Developers," is available from Polls Download http://www.cert.org/tech_tips/malicious_code_mitigation.html Do you think that, this site will improve the security level of Tadawul staff? Yes No I don’t know You can add any word excel or pdf documents just for demonstration. The actual content will be provided at installation phase. And it should be easy to add new files to be downloaded in the administration interface. Additional Feature will be added to the TISAW: Search: the User will be apple to use the search functionally to search on any document in the website. News Ticker : A java Script will display the latest 10 News added to the RSS news Database Ad Banner : A banner will place in the Home page TISD can use this Banner to deliver a security Awareness massage or as an invitation tool to invite users to new workshop …