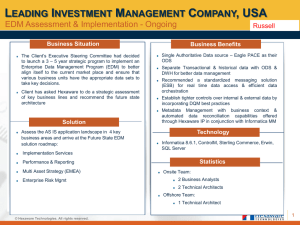
Data Sheet
Informatica Secure@Source
Identify, Analyze, Detect, and Monitor Sensitive Data Risks
Sensitive data is the foundation of your organization’s intellectual property, revenue stream,
and competitive advantage. That makes it imperative to protect your data from all types
of internal and external threats, from disgruntled or careless employees to cybercriminals
motivated by money or malice.
Benefits
• Continuously monitor and
track sensitive data risks
based on multiple risk factors
• Identify top risk areas and
prioritize data security
protection more effectively
• Uncover previously unknown
and undocumented risks
• Proactively detect high-risk
conditions and anomalous
user activities around
sensitive data
• Support audit and compliance
with standardized risk
scoring to easily track the
effectiveness of data security
measures over time
Cyber attacks and breaches will continue to escalate in the foreseeable future. Customers,
investors, and regulators all demand that organizations understand their risks and
implement strict policies and security controls for sensitive, private, and critical data. Most
organizations, however, do not have enough insights into their sensitive data risks—or even
the location, proliferation, usage, and access control of all their critical data assets.
Visibility into Sensitive Data Risks
Informatica Secure@Source provides insights into sensitive data risks by automating the process
of collecting all the information around sensitive data, analyzing, monitoring, and providing a
360-degree view of sensitive data risk. This enables security and IT teams to rapidly apply the right
policies and controls to the most critical data. It replaces costly, time-consuming manual efforts with
automated discovery, identification, detection, scoring, and analysis of sensitive data risks.
Many organizations believe that finding where sensitive data resides within the enterprise is
all they need in order to manage its risk. But many other factors contribute to the level of risks:
1.The existence of a combination of sensitive data elements can represent a higher risk
2.Not all sensitive elements represent the same risk
3.The volume and protection status of sensitive data impact risk
4.The more users who have access to the sensitive data, the higher the risk
5.Increased activity, access to larger volumes of sensitive data, and anomalous patterns of
activities all increases risk
Secure@Source addresses this challenge by analyzing data risk based on multiple
factors and taking into account the level of sensitivity, volume, context, protection status,
proliferation, cost, location, users who have access, and level and type of activity.
Organizations can interactively analyze the top data stores, departments, and location with
the highest risks as well as visually trace the sources of unprotected sensitive data and the
replication of sensitive data across data stores in the organization.
By continuously monitoring, tracking, and trending standardized risk scores for each data
store, in each department, and across the enterprise, organizations can measure progress
for each group as well as in aggregate over time.
Data Security Intelligence to Detect Anomalies and Prioritize Remediation
Secure@Source delivers data security intelligence by collecting user activity logs from data
stores across the enterprise in real time. By correlating this information with user access,
data sensitivity, protection status, and proliferation information, Secure@Source enables
organizations to detect abnormal user activities and potential threats from insiders or
outsiders with stolen credentials. This correlated analysis further pinpoints the highest priority
investments for data security and privacy initiatives.
Key Features
Sensitive Data Risk Analytics
The level of sensitive data risk is determined by
analyzing multiple factors including protection status,
user access, activity, location, data cost, classification,
and proliferation. Organizations can weight each
factor according to their own risk-measurement
requirements. This analysis produces risk scores that
pinpoint the highest risk areas to prioritize remediation
activities. Organizations can measure the effectiveness
of security investments by tracking how risk scores
trend over time. Risk analytics is presented in a
highly graphical, visual format that enables quick
identification of areas requiring attention.
Data Classification and Discovery
Secure@Source enables the discovery and classification
of sensitive data based on data and metadata patterns
and rules. From prebuilt and customizable definitions,
organizations define data domains and policies to
identify and locate sensitive data including PII, PCI, PHI,
and other confidential information.
Secure@Source automates the discovery of
sensitive data across large numbers of databases,
big data repositories, and cloud data stores. It
uses flexible, high-performance, scalable scanning
to uncover sensitive data and show results quickly
and clearly.
Data Proliferation Analysis
It’s critical to understand not only where sensitive
data resides, but also where it’s moving and being
replicated to other data stores within the organization
and to cloud applications. Organizations may also
want to monitor sensitive data flowing in and out of
highly regulated countries or between partner and
client organizations.
Secure@Source analyzes data proliferation from
Informatica data flows and provides an aggregated
and visual map of sensitive data proliferation,
identifying sensitive data that has the greatest
proliferation.
Secure@Source provides 360-degree visibility of sensitive data through its dashboard (left) and discovers
sensitive data from cloud applications, big data repositories, and on-premise databases (right).
Collect and Correlate User Access and
Activity
Correlating information about user access control
as well as activity against sensitive data provides
a much richer dimension that enables detection
of abnormal activities and insider and outsider
threats. Secure@Source imports user and user
group information from LDAP and IAM systems. It
also collects activity logs in CEF, LEEF, and JSON
formats across databases, mainframe systems, big
data repositories, and SaaS applications to enable
detection of high-risk activities.
Alerts of High-Risk Conditions
Information security teams can define alert rules to
notify them when high risk conditions are detected,
such as a when a high volume of sensitive data is
leaving a highly regulated country.
Visual Analytics, Reporting, and Dashboards
Secure@Source has a rich array of dashboards that
clearly present the state of sensitive data risk to decision
makers and stakeholders. The highly interactive and
visual interface also lets practitioners drill down and
perform detailed analyses of sensitive data risk.
Information can be sorted to reveal trouble areas by
classification policy, location, region, department,
data store, or line of business. These reports let
security practitioners and decision makers share a
common platform for tactical and strategic analysis
and decision making.
Security and IT Infrastructure Integration
Secure@Source enables you to leverage your existing
IT and security assets by incorporating information
already captured and stored by other data security
solutions, delivering a much richer analysis.
The User Activity Summary allows you to analyze user access to sensitive data and
detect unusual activities or behavior.
Key Benefits
About Informatica
Prioritize Security Investments
Informatica is a leading
independent software
provider focused on delivering
transformative innovation for
the future of all things data.
Organizations around the world
rely on Informatica to realize their
information potential and drive
top business imperatives. More
than 5,800 enterprises depend on
Informatica to fully leverage their
information assets residing onpremise, in the Cloud and on the
internet, including social networks.
Organizations can prioritize and maximize their security investments by understanding
the highest areas of sensitive data risks, measuring risks over time, and aligning their data
security investments, policies, processes, and actions accordingly.
Eliminate Costly, Error-Prone Manual Efforts
Manually classifying, surveying, and reporting on sensitive data assets is costly, laborious,
and error-prone. Automating these tasks lets organizations allocate resources to corrective
actions and create more precise, repeatable results that improve ROI on security
investments.
Streamline Sensitive Data Audit and Governance
Secure@Source automates the analysis of critical data assets to support on-demand and
trend reports of sensitive data risks and user activity, for data privacy, security auditing, and
governance programs.
Visibility to Sensitive Data Proliferation
Tracking sensitive data proliferation lets organizations better comply with privacy laws and
data usage policies. With Secure@ Source, organizations know where their private and
sensitive data is proliferating—both inside and outside the enterprise, between partner and
client organizations
Worldwide Headquarters, 2100 Seaport Blvd, Redwood City, CA 94063, USA Phone: 650.385.5000 Fax: 650.385.5500
Toll-free in the US: 1.800.653.3871 informatica.com linkedin.com/company/informatica twitter.com/Informatica
© 2016 Informatica LLC. All rights reserved. Informatica® and Put potential to work™ are trademarks or registered trademarks of Informatica in the
United States and in jurisdictions throughout the world. All other company and product names may be trade names or trademarks.
IN17_0415_2878_0116