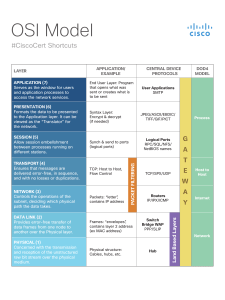
CYBER SECURITY GOPALAKRISHNAN MANISEKARAN CYBER SECURITY NETWORK SYSTEMS MOBILE NETWORK BASICS MOST IMPORTANT FOR NETWORK SECURITY OSI LAYER PORTS AND PROTOCOLS Ports 0–1023 –well-known ports Ports 1024–49151 –registered ports Ports 49152–65535 – dynamic ports EX: HTTP -80 HTTPS-443 Why protocols and ports matters here ???????????? HIGHLY TARGETED PROTOCOLS/PORT •TCP and UDP port 135 — Windows RPC •TCP and UDP ports 137–139 — Windows NetBIOS over TCP/IP •TCP port 1433 and UDP port 1434 — Microsoft SQL Server •RDP-3389 CIA – CONFIDENTIALITY INTEGRITY AVAILABILITY INCIDENT / ALERT TRIAGE False Positive False Negative True Positive True Negative THREAT – VULNERABILITY – RISK Threat – Anything that can exploit a vulnerability, intentionally or accidentally, and obtain, damage, or destroy an asset. Vulnerability – Weaknesses or gaps in a security program that can be exploited by threats to gain unauthorized access to an asset. Risk – The potential for loss, damage or destruction of an asset as a result of a threat exploiting a vulnerability. INFRASTRUCTURE SECURITY Router Firewall Application Delivery Controller aka Load Balancer Proxy(Forward and Reverse) WAF – Web Application Firewall UTM AV IDS IPS (IDPS) MALWARE Malicious Executable –( MAL + Ware = Malicious Software ) Types Adware Spyware Ransomware Trojan Malveristing Worm Viruses (More About :: Ransomware ) INFRA ARCHITECTURE PROXY PROXY Forward Proxy Reverse Proxy CAN WE SPOOF ? EMAIL ANALYSIS Process during the digital forensic investigation to detect the criminal activities occurs through the communication of the email messages Phishing (URL Phishing/ Hyperlink Spoofing) CAN WE SPOOF ? PREVENT FROM CYBER ATTACKS Keep Upto date your Software Don’t install unnecessary Tools Don’t visit unnecessary/malicious websites Install AV protection Use Secure Communication Link CAN WE SPOOF ? WEB SECURITY What is Web security Why ? Web security is important ? How can protect ? OWASP –TOP 10 • A1-Injection • A2-Broken Authentication • A3-Sensitive Data Exposure • A4-XML External Entities (XXE) • A5-Broken Access Control • A6-Security Misconfiguration • A7-Cross-Site Scripting XSS • A8-Insecure Deserialization • A9-Using Components with Known Vulnerabilities • A10-Insufficient Logging and Monitoring THANK YOU