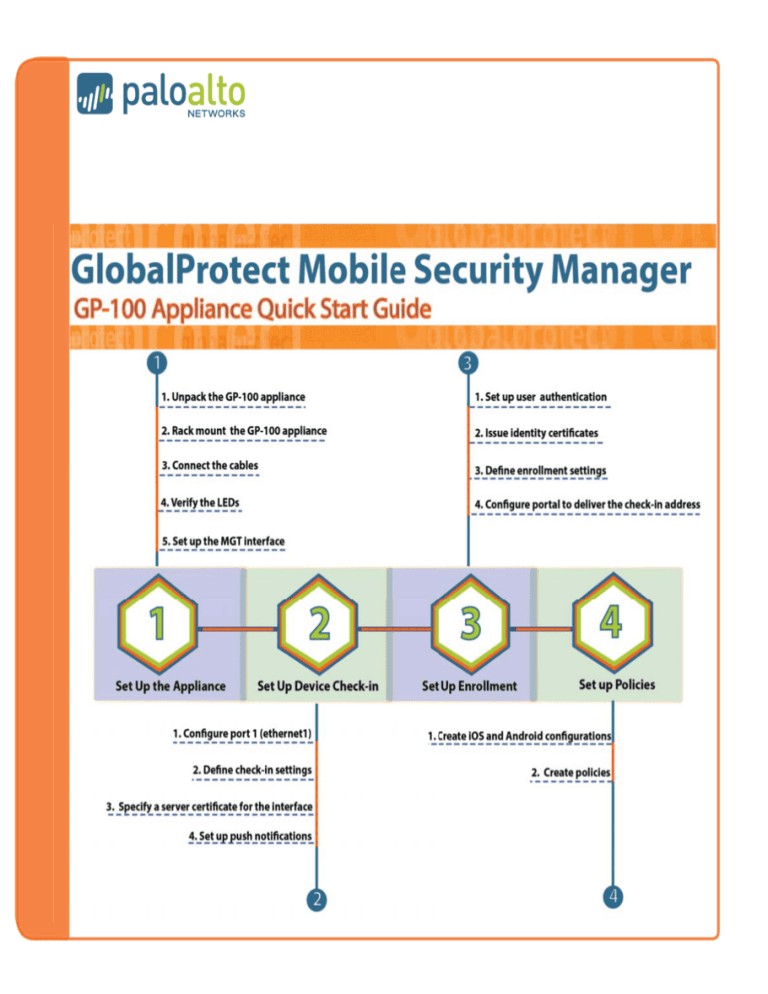
Set up the GP-100 Appliance
*
Before you begin:
* Obtain IP addresses for the MGT port and the ethernet1 port. The IP addresses must be on separate subnets and the IP address for ethernet1 must be accessible from the external network.
* Obtain a server certificate for the device check-in interface to enable device access. (Certificate
signed by a trusted Certificate Authority (CA) such as VeriSign is recommended but not required.)
1. Unpack the shipment and verify the contents of the box:
* GP-100 appliance
* Rail kit
* Accessory kit that includes this Quick Start Guide, a power cord, a DB9 to DB9 console cable, an
Ethernet cable, and the software license agreement and hardware warranty.
2. Use the rail kit to rack mount the appliance. Refer to the GP-100
Appliance Hardware Reference Guide for instructions.
D1 / D2
GP-100
3. Connect the Ethernet cable to the MGT port (Figure 1) and the
power cable in to the rear of the appliance.
4. Verify LEDs (Figure 2).
Red: System error
1. System health Green: Healthy
2. HDD activity Blinks green to indicate activity
1 / D2
Blinks green to indicate activity
3. LAN activity
Green: System is powered on
4. Power
Top: Blinks green to indicate activity
5. Disk drive
Bottom: Green indicates disk healthy
Red indicates disk failure
Figure 1
1
MGT
Internet
Management
Network
5
1 2 3
Device Check-in /
GlobalProtect Gateway HIP Retrieval
4
GP-100
Figure 2
5. Configure the management (MGT) interface:
a. Connect the Ethernet cable from your computer to the MGT port on the appliance (Figure 1). From a
browser, go to https://192.168.1.1. Note that you may need to change the IP address on your computer to
an address in the 192.168.1.0 network, such as 192.168.1.2, in order to access this URL.
b. Log in using the default username/password admin/admin.
6. Define the network settings.
a. Select Setup > Settings and edit the Management Interface Settings section of the screen to configure the
IP Address, Netmask, and Default Gateway.
b. Select which management services to allow on the interface. At a minimum, select HTTPS, SSH and Ping.
7. Configure DNS.
Select Setup > Settings > Services and edit the Services section of the screen to enter the IP address of the
Primary DNS Server and optionally the Secondary DNS Server.
8. Change the default administrator’s password. Select Setup > Administrators and edit the admin role.
9. Commit your changes.
You will be logged out of the web interface; use the IP address and password you configured above to log
back in to the web interface.
Set up Device Check-In
1. Configure the device check-in interface.
a. Connect the ethernet1 port (labeled 1 on the front panel; see Figure 1) to your network using an Ethernet
cable. Make sure that the switch port you cable the interface to is configured to auto-negotiate.
b. Select Setup > Network > ethernet1 and configure the IP Address, Netmask, and Default Gateway.
c. Enable the Mobile Device Check-in service and any other services you want to allow on this interface.
2. Define check-in settings.
a. (Optional, but recommended) Change the port used for device check-in by selecting Setup > Settings >
Server and edit Device Check-in Settings. Set the port to 8443 or 7443.
3. Import a server certificate for the device check-in interface. As a best practice use a server certificate from a
trusted CA. The CN in the certificate must match the IP address/FQDN of the interface.
a. Select Setup > Certificate Management > Certificates > Device Certificates.
b. Click Import and enter a Certificate Name.
c. Enter the path and name to the Certificate File received from the CA, or Browse to find the file.
d. Select Encrypted Private Key and Certificate (PKCS12) as the File Format.
e. Select Import private key, and enter the path and name to the PKCS#12 file in the Key File field or
Browse to find it.
f. Enter and re-enter the Passphrase that was used to encrypt the private key.
g. To use this certificate for device check-in, select Setup > Settings > Server and then edit the SSL Server
Settings to select the certificate you just imported.
4. Configure the push notification settings.
a. Obtain credentials to enable over-the-air (OTA) push notifications:
» For Android devices: Obtain a key and sender ID for the Google Cloud Messaging (GCM) service at
https://cloud.google.com/console.
» For iOS devices: Obtain a certificate for the Apple Push Notification service (APNs).
i. Select Setup > Certificate Management > Certificates > Device Certificates, and click Generate.
ii. Set Signed by to External Authority (CSR), Number of Bits to 2048, Digest to sha1, and then
Generate the certificate.
iii. Export the CSR, and select Sign CSR for Apple Push Notification Service as the File Format.
iv. Upload the CSR to https://identity.apple.com/pushcert.
v. Download the signed certificate from the Apple portal and Import it on the GP-100 appliance using the
same name you used when generating the CSR.
b. Select Setup > Settings > Server and then edit the Push Notification Settings section to enable push
notifications.
» For Android devices: To enable GCM push notifications, select the Google Cloud Messaging check
box and then enter the Android GCM API Key and Android GCM Sender ID you obtained.
» For iOS devices: To enable APNs, select the iOS APNs Certificate you obtained.
For more details on configuring push notifications, refer to the GlobalProtect Administrator’s Guide.
Set up Enrollment
1. Enable user authentication (LDAP, RADIUS, and Kerberos are supported).
a. Create the server profile for connecting to the authenticating service (Setup > Server Profiles).
b. Create an authentication profile and attach the server profile (Setup > Authentication Profile).
c. Use the authentication profile for enrollment (Setup > Settings > Server > Authentication Settings).
2. Set up identity certificate generation.
Note: You can use an existing SCEP server to issue identity certificates for your iOS devices.
a. To create a root CA certificate for signing identity certificates, select Setup > Certificate
Management > Certificates > Device Certificates and click Generate.
b. Enter a Certificate Name, such as GP-100_CA. The certificate name cannot contain any spaces.
c. Do not select a value in the Signed By field (this is what indicates that it is self-signed).
d. Select the Certificate Authority check box and then Generate the certificate.
3. Configure the enrollment settings.
a. Select Setup > Settings > Server and then edit the Enrollment Settings to configure the Host
Name of the device check-in interface (FQDN or IP address; it must match the value in the CN
field of the server certificate you imported in Section 2 Step 3).
b. Enter the Organization Name to display on the device profiles.
c. Enter a Consent Message that lets users know that they are enrolling in device management.
d. Select the Certificate Authority you configured for issuing identity certificates.
e. Commit the changes.
4. On the firewall hosting the GlobalProtect portal, perform the following steps to add the
GP-100 appliance address to push to the mobile devices in the client configuration.
a. Select Network > GlobalProtect > Portals and select the portal configuration to modify.
b. On the Client Configuration tab, select or add the client configuration.
c. In the Mobile Security Manager field, enter the IP address or FQDN of the device check-in
interface (must match the enrollment host name configured in Step 3a).
d. Commit the changes on the GlobalProtect portal.
Set up Policies
1. Create iOS and Android configurations (Policies > Configuration), and provisioning profiles (iOS
only) to push to managed devices.
2. Create policies by defining the match criteria and attaching the configurations/profiles (Policies >
Policies).
Next Steps
p
*
Schedule daily device state backups for recovery from misconfiguration or server failure (Setup >
Scheduled Backup Export).
* Define HIP objects and HIP profiles for use in device policy deployment (Policies > HIP Object).
* On the firewall hosting the GlobalProtect gateway, set up access to to the GP-100 appliance for HIP
report retrieval for mobile devices (Network > GlobalProtect > MDM).
* Integrate with your firewall’s security policy.
For detailed instructions, refer to the GlobalProtect Administrator’s Guide.
Copyright © 2013 Palo Alto Networks, Inc. All rights reserved.
P/N 810-000186-00C





