Network Defense & Countermeasures Alan Watkins, Adjunct Professor
advertisement

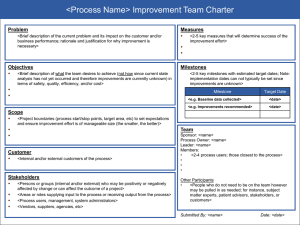
National University CYB606 – Network Defense & Countermeasures Alan Watkins, Adjunct Professor (April 2014) Defensible Network Architecture <vs> NSA’s Manageable Network Plan Instructor’s Comments For extra credit, students were asked to compare and contrast the Defensible Network Architecture (“DNA”) developed by Richard Bejtlich and the NSA’s Manageable Network Plan (“MNP”). It’s a good idea, when comparing two related approaches, to list their individual characteristics in a side-by-side table (as shown below). Following that would be an analysis of the relevant points – such as advantages/disadvantages of each or the pro’s and con’s of each. Comparison of Basic Characteristics Defensible Network Architecture (DNA) • 1. Monitored – Begin developing DNA on an existing enterprise by deploying Network Security Monitoring sensors to capture session data (at an absolute minimum), full content data (if you can get it), and statistical data. If you can access other data sources (e.g., firewall, router, IPS, DNS, and proxy logs), begin working that angle too. • 2. Inventoried – Know what you host on your network. If you've started monitoring, you can acquire a lot of this information passively. • 3. Controlled – Start implementing network-based controls (e.g., ingress filtering, egress filtering, network admission control, network access control, proxy connections, etc.). The idea is you transition from an "anything goes" network to one where the activity is authorized in advance, if possible. • 4. Claimed – Identify asset owners and develop policies, procedures, and plans for the operation of that asset. This step is a prerequisite for performing incident response. You can only work with an asset owner to respond to an incident when you know who owns the asset and Manageable Network Plan (MNP) • Milestone #1: Prepare to Document your Network – documentation will be a necessary part of every milestone; at this point, just setup a way/method to begin documenting information about your network • Milestone #2: Map your Network – create an accurate map (network topology) of your current network; create an accurate list of ALL devices on your network; create a list of ALL protocols running on your network • Milestone #3: Protect your Network (Network Architecture) – identify your current network enclaves (which groups of users on the network have access to what types of data/information); identify your current high-value network assets (business criticality value, not cost); identify the choke points in your network • Milestone #4: Reach your Network (Device Accessibility) – establish a process to properly, easily, and securely access (either remotely or physically) and administer EVERY device on your network • Milestone #5: Control your Network (User Access) – establish non-privileged user accounts for all users on your [File: CYB606 Defensible_Networks_vs_Manageable_Network_Plan - Instructor Comments.docx] (05/16/2014) Page 1 Comparison of Basic Characteristics Defensible Network Architecture (DNA) how you can contain and recover it. • 5. Minimized – This step is the first to directly impact the configuration and posture of assets. You work with stakeholders to reduce the attack surface of their network devices (e.g., clients, servers, applications, network links, etc.). By reducing attack surface areas, you improve your ability to perform all of the other steps, but you can't really implement minimization until you know who owns what. • 6. Assessed – This is a vulnerability assessment process to identify weaknesses in assets. Also consider performing an adversary simulation to test your overall security operations. Assessment is the step where you decide if what you've done so far is making any difference. • 7. Current – Keep your assets configured and patched such that they can resist known attacks by addressing known vulnerabilities. It's easy to disable functionality no one needs; however, upgrades can sometimes break applications. Manageable Network Plan (MNP) network (including Admins); normal users should only be allowed to use assigned non-privileged accounts; Admins should only use their privileged accounts when performing administrative tasks and should use their non-privileged accounts for everything else • Milestone #6: Manage your Network, Part I (Patch Management) – establish a patch management process for ALL the operating systems and application software for EVERY device on your network • Milestone #7: Manage your Network, Part II (Baseline Management) – create a list of all applications that are approved for use on your network; establish the criteria and process for getting an application on the approved list; create device baselines (which approved applications are allowed on the device) • Milestone #8: Document your Network – as time permits, your processes and procedures for your network should be documented; give priority to documenting those things that are most important to keeping your organization doing business • Network Security Tasks o Business Functionality Tasks o Host-Based Security Tasks o Network Monitoring & Control Tasks The DNA is process oriented toward operational networks, while the MNP provides a more strategic plan of action to create and maintain a secure network. The MNP’s Appendices include checklists with correlation to the SANS/CCS 20 Critical Security Controls and NIST standards. Either one can be used when designing and implementing a new network from scratch or when trying to retrofit security measures into an existing network. In fact, the two are not mutually exclusive and can work well together, depending on an organization’s environment and current network management practices, including security. Both approaches are scalable to different sizes of organizations, and both allow ‘partial implementation’ of different components within the organization’s capabilities (both skills and funding). One benefit of having these two guides [File: CYB606 Defensible_Networks_vs_Manageable_Network_Plan - Instructor Comments.docx] (05/16/2014) Page 2 and the MNP templates for action plans, is that organizations have the opportunity to fit what works into their existing business model, which helps increase their security posture without totally disrupting their operations or organizational culture. Both approaches can be taken as high-level and conceptual, as well as being vendor/device neutral, so organizations can select the most compatible hardware and software which fits within their infrastructure environment to actually implement the security architecture. An organization can use the MNP to design and implement a secure network architecture, and then use DNA as part of the ongoing network management outlined in MNP. Below is an integrated, prioritized outline of how I would use each of the tasks from both approaches to secure an existing network infrastructure (assuming a medium-to-large business): 1. MNP-1: Create a method and plan for documenting the network and your processes; including the documentation of the following processes 2. DNA-1: Begin monitoring the existing network at key points of ingress/egress, expand to cover major subnet segments, as appropriate 3. MNP-2 / DNA-2: Create a network topology map that includes an inventory of all network assets, as well as all devices connected to the network (start with host servers, network devices, and security devices; later add client systems); include network protocols in use 4. DNA-3: Implement network security controls that may not already be in place, to protect critical network segments/subnets 5. MNP-4: Start to gain necessary, secure access to all network devices for administrative purposes (both network operations and security management); ensure default device accounts are deleted/disabled or modified (changed password), as appropriate, without impacting functionality or interaction with other systems (which may require changing some configuration settings) 6. MNP-3 / DNA-4: Identify asset owners and their related network assets (hardware and software – servers, applications, and databases), prioritize assets by business criticality and start aligning security measures based on those priorities 7. MNP-5: Ensure policies and procedures are in place to manage user accounts, including ‘standard’ end-users, super-users, and system/network administrative users 8. MNP-6 / DNA-7: Implement policies and procedures for automated and manual system security patches (operating systems and applications); in addition, ensure there is a change management plan and process for handling the addition, modification, or removal of computing assets within the network; start disabling services/ports that are not needed for standard business operations (continue this process in the next step) 9. DNA-5: Using the device inventory, secure each device as much as possible, including hardening its OS, close all unnecessary ports, disable all unused/unnecessary services, lock out all users who do not need to access the device; where applicable, enable system audit logging and direct the output to another secure storage server (only accessible by security staff, and not by system/network administrators or software developers, etc.) 10. MNP-7: Gather further detailed inventory of applications and services approved to run on each device (usually servers); part of an organization’s IT governance process should [File: CYB606 Defensible_Networks_vs_Manageable_Network_Plan - Instructor Comments.docx] (05/16/2014) Page 3 include standard procedures for having new systems/applications approved, and old ones retired and removed 11. DNA-6 / MNP (Network Security Tasks): As part of ongoing network operations, create a regular schedule for different levels of security assessments, usually targeting specific areas of the network for each test/assessment (rather than across the organization’s whole network); use different types of assessments for internal servers, web servers, public applications (usually on a web server), databases, internal applications, and network equipment (routers, firewalls, switches, etc.); plan for unscheduled (“surprise”) system assessments to be conducted at certain intervals as determined by management 12. MNP-8: While documentation should be taking place at each of the prior steps, as actions are taken to gather inventory and make configuration changes, this step is aimed at completing as much documentation as possible, with a priority on those things which might impact business operations the most; ensure the security of the documentation and restrict access on a need-to-know basis for authorized persons only This is a lot of tasks and actions to take and, as others have noted elsewhere, this whole process may take months or years to actually complete. The important thing to remember is – get started! There are additional resources available for organizations (both public and private sector) which are owners/operators of critical infrastructure (refer to the U.S. Department of Homeland Security site - http://www.dhs.gov/critical-infrastructure-sectors). On Feb. 12, 2014, the National Institute of Standards and Technology issued the “Framework for Improving Critical Infrastructure Cybersecurity,” which provides further tools, including the Framework Core, which is an Excel spreadsheet with detailed categories and subcategories linked not only to NIST and SANS/CCS standards, but also COBIT, ISA and ISO/IEC standards and security controls. ~~~~~~~~~~~~~~~~~~~~ References: Bejtlich, Richard. “Defensible Network Architecture 2.0.” Jan. 10, 2008. http://taosecurity.blogspot.com/2008/01/defensible-network-architecture-20.html NIST “Framework for Improving Critical Infrastructure Cybersecurity” (v.1.0). Feb. 12, 2014. http://www.nist.gov/cyberframework/ http://www.nist.gov/cyberframework/upload/framework-for-improving-criticalinfrastructure-cybersecurity-core.xlsx NSA “Manageable Network Plan” (v.3.0). Sept. 25, 2013. http://www.nsa.gov/ia/_files/vtechrep/ManageableNetworkPlan.pdf [File: CYB606 Defensible_Networks_vs_Manageable_Network_Plan - Instructor Comments.docx] (05/16/2014) Page 4