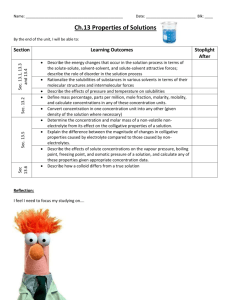
The correct configuration of the example network:
advertisement

The correct configuration of the example network: • Download the Software Configuration Guide (For Cisco 2600 series etc.) from the Recommended Readings site (Click IOS Configuration). • Download the Configuring RIP document from the Setting up RIP section of the Hands-on-session chapter (Click: Do you have problems with RIP? click here). • Read carefully(!) at least the first chapter of the Software Configuration Guide and the sections Configuring the Host Name and Password and Configuring Fast Ethernet Interfaces of the second chapter of this document. • Read carefully(!) the Configuring RIP document. • Only now enter the Exercises (after you have reserved a corresponding timeslot in the reservation system). • Click a router and proceed as described in the Configuring the Host Name and Password section. Note that you don’t have to enable secret password! • Now, configure the two fastethernet interfaces as described in the Configuring Fast Ethernet Interfaces section. Note that you should choose ip routing in Step 3 and afterwards you should type in the router rip command to configure the IP-routes. This is fairly easy since Cisco router support RIP, i.e., the routers are able to adapt their routing tables among each other. Proceed as described in the document Configuring RIP. Note that you just have to put in the network IP addresses, the neighbor IP address and choose version 2, before you leave the router configuration with exit. You should proceed with Step 4 of fastethernet configuration. Fill in the corresponding IPadresses with subnetmasks. In Step 6, type in ip rip send version 2, ip rip receive version 2 and (really important!) type in no shutdown to put the interface into an operational mode. Proceed with Step 7. • Now you should have a working network, i.e., you should be able to ping the hosts and routers, use traceroute etc. • Do the first part of the exercises. After having configured the routers, show interfaces should look very similar to this output: router1: router1#show interfaces FastEthernet0/0 is up, line protocol is up Hardware is AmdFE, address is 0004.4db9.0961 (bia 0004.4db9.0961) Internet address is 10.2.0.10/24 MTU 1500 bytes, BW 10000 Kbit, DLY 1000 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation ARPA, loopback not set Keepalive set (10 sec) Half-duplex, 10Mb/s, 100BaseTX/FX ARP type: ARPA, ARP Timeout 04:00:00 Last input 00:00:08, output 00:00:00, output hang never Last clearing of "show interface" counters never Queueing strategy: fifo Output queue 0/40, 0 drops; input queue 0/75, 0 drops 5 minute input rate 0 bits/sec, 0 packets/sec 5 minute output rate 0 bits/sec, 0 packets/sec 7065 packets input, 4040694 bytes Received 78 broadcasts, 0 runts, 0 giants, 0 throttles 0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored 0 watchdog 0 input packets with dribble condition detected 7302 packets output, 4075045 bytes, 0 underruns(3/4/0) 0 output errors, 7 collisions, 2 interface resets 0 babbles, 0 late collision, 35 deferred 0 lost carrier, 0 no carrier 0 output buffer failures, 0 output buffers swapped out FastEthernet0/1 is up, line protocol is up Hardware is AmdFE, address is 0004.4db9.0962 (bia 0004.4db9.0962) Internet address is 10.1.0.10/24 MTU 1500 bytes, BW 10000 Kbit, DLY 1000 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation ARPA, loopback not set Keepalive set (10 sec) Half-duplex, 10Mb/s, 100BaseTX/FX ARP type: ARPA, ARP Timeout 04:00:00 Last input 00:00:20, output 00:00:02, output hang never Last clearing of "show interface" counters never Queueing strategy: fifo Output queue 0/40, 0 drops; input queue 0/75, 0 drops 5 minute input rate 0 bits/sec, 0 packets/sec 5 minute output rate 0 bits/sec, 0 packets/sec 6991 packets input, 4046236 bytes Received 9 broadcasts, 0 runts, 0 giants, 0 throttles 0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored 0 watchdog 0 input packets with dribble condition detected 7178 packets output, 4049644 bytes, 0 underruns(23/88/0) 0 output errors, 111 collisions, 2 interface resets 0 babbles, 0 late collision, 17 deferred 0 lost carrier, 0 no carrier 0 output buffer failures, 0 output buffers swapped out router2: router2#show interfaces Ethernet0/0 is up, line protocol is up Hardware is AmdP2, address is 0002.16e9.b000 (bia 0002.16e9.b000) Internet address is 10.2.0.20/24 MTU 1500 bytes, BW 10000 Kbit, DLY 1000 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation ARPA, loopback not set Keepalive set (10 sec) ARP type: ARPA, ARP Timeout 04:00:00 Last input 00:00:17, output 00:00:07, output hang never Last clearing of "show interface" counters never Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0 Queueing strategy: fifo Output queue :0/40 (size/max) 5 minute input rate 0 bits/sec, 0 packets/sec 5 minute output rate 0 bits/sec, 0 packets/sec 7113 packets input, 4061722 bytes, 0 no buffer Received 77 broadcasts, 0 runts, 0 giants, 0 throttles 0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored 0 input packets with dribble condition detected 7210 packets output, 4049493 bytes, 0 underruns 0 output errors, 7 collisions, 2 interface resets 0 babbles, 0 late collision, 56 deferred 0 lost carrier, 0 no carrier 0 output buffer failures, 0 output buffers swapped out Ethernet1/0 is up, line protocol is up Hardware is AmdP2, address is 0002.16e9.b010 (bia 0002.16e9.b010) Internet address is 10.3.0.20/24 MTU 1500 bytes, BW 10000 Kbit, DLY 1000 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation ARPA, loopback not set Keepalive set (10 sec) ARP type: ARPA, ARP Timeout 04:00:00 Last input 00:10:08, output 00:00:09, output hang never Last clearing of "show interface" counters never Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0 Queueing strategy: fifo Output queue :0/40 (size/max) 5 minute input rate 0 bits/sec, 0 packets/sec 5 minute output rate 0 bits/sec, 0 packets/sec 6930 packets input, 4024717 bytes, 0 no buffer Received 0 broadcasts, 0 runts, 0 giants, 0 throttles 0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored 0 input packets with dribble condition detected 7201 packets output, 4066675 bytes, 0 underruns 0 output errors, 34 collisions, 2 interface resets 0 babbles, 0 late collision, 49 deferred 0 lost carrier, 0 no carrier 0 output buffer failures, 0 output buffers swapped out Setting up the VPN: • Download the IPsec Network Security document from the Recommended Readings site (Click IPsec Configuration Guide) and read it carefully(!). • Create DSS keys on the routers (in config-mode, type in crypto key generate dss <routername>). • Exchange the DSS keys (in config-mode, use the crypto key exchange dss-command). • Configure the routers to encrypt both TCP and UDP traffic between the two subnets 10.1.0.0/24 and 10.3.0.0/24 (in config mode, use the command ip access-list extended 100. You will reach the config-ext-nacl mode. Type in permit tcp 10.1.0.0 0.0.0.255 10.3.0.0 0.0.0.255 and permit udp 10.1.0.0 0.0.0.255 10.3.0.0 0.0.0.255). • Create a crypto map (use the command create crypto map <map-name mapnumber> as described in the IPsec Network Security document (page 18). Fill in the match adress and set peer. Make sure the routers use des ((Data Encryption Standard) algorithm with a Cipher Feedback Modus (CFB) of 64 bit (use the command set algorithm des cfb-64 in config-crypto-map modus). • Apply the Crypto Map Set to the corresponding interface as described in the IPsec Network Security document (page 23). • Now you should have a working VPN and you can proceed with the second part of the exercises. In the end, you access lists and crypto maps should be similar to those: router1: router1#show access-lists Extended IP access list 100 permit tcp 10.1.0.0 0.0.0.255 10.3.0.0 0.0.0.255 permit udp 10.1.0.0 0.0.0.255 10.3.0.0 0.0.0.255 router1#show crypto map Crypto Map "map1" 1 cisco Peer = router2 PE = 10.1.0.0 UPE = 10.3.0.0 Extended IP access list 100 access-list 100 permit tcp 10.1.0.0 0.0.0.255 10.3.0.0 0.0.0.255 access-list 100 permit udp 10.1.0.0 0.0.0.255 10.3.0.0 0.0.0.255 Connection Id = 1 (1 established, 0 failed) Interfaces using crypto map map1: FastEthernet0/0 router2: router2#show access-lists Extended IP access list 100 permit tcp 10.3.0.0 0.0.0.255 10.1.0.0 0.0.0.255 permit udp 10.3.0.0 0.0.0.255 10.1.0.0 0.0.0.255 router2#show crypto map Crypto Map "map2" 1 cisco Peer = router1 PE = 10.3.0.0 UPE = 10.1.0.0 Extended IP access list 100 access-list 100 permit tcp 10.3.0.0 0.0.0.255 10.1.0.0 0.0.0.255 access-list 100 permit udp 10.3.0.0 0.0.0.255 10.1.0.0 0.0.0.255 Connection Id = 1 (0 established, 0 failed) Interfaces using crypto map map2: Ethernet0/0 If you have any questions about these procedures, don’t hesitate to ask! Email: carolin.latze@unifr.ch Office: B402