Type of addressing in IPv4
advertisement

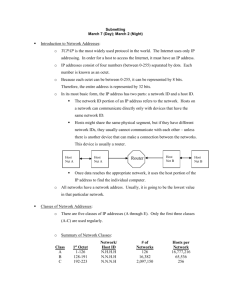
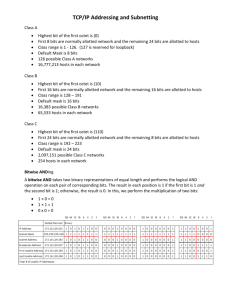
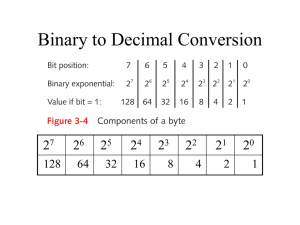
University of Babylon/College of Information Technology/ Information Network Dept. / First Class / Second Semester/ Subject : Network and Distributed System/ Lecture : 2 Type of addressing in IPv4 Within the address range of each IPv4 network, we have three types of addresses: Network address - The address by which we refer to the network Broadcast address - A special address used to send data to all hosts in the network Host addresses - The addresses assigned to the end devices in the network Network Prefixes An important question is: How do we know how many bits represent the network portion and how many bits represent the host portion? When we express an IPv4 network address, we add a prefix length to the network address. The prefix length is the number of bits in the address that gives us the network portion. For example, in 172.16.4.0 /24, the /24 is the prefix length - it tells us that the first 24 bits are the network address. This leaves the remaining 8 bits, the last octet, as the host portion. Later in this chapter, we will learn more about another entity that is used to specify the network portion of an IPv4 address to the network devices. It is called the subnet mask. The subnet mask consists of 32 bits, just as the address does, and uses 1s and 0s to indicate which bits of the address are network bits and which bits are hosts bits. Networks are not always assigned a /24 prefix. Depending on the number of hosts on the network, the prefix assigned may be different. Having a different prefix number changes the host range and broadcast address for each network. Notice that the network address could remain the same, but the host range and the broadcast address are different for the different prefix lengths. In this figure you can also see that the number of hosts that can be addressed on the network changes as well. Lecturer : Ahmed M. Al-Saleh & Mouayad Najim Page 14 University of Babylon/College of Information Technology/ Information Network Dept. / First Class / Second Semester/ Subject : Network and Distributed System/ Lecture : 2 Understanding Subnetting Subnetting allows you to create multiple logical networks that exist within a single Class A, B, or C network. If you do not subnet, you will only be able to use one network from your Class A, B, or C network, which is unrealistic. Formula for calculating subnets Use this formula to calculate the number of subnets: 2^n where n = the number of bits borrowed The number of hosts To calculate the number of hosts per network, we use the formula of 2^n - 2 where n = the number of bits left for hosts. Each data link on a network must have a unique network ID, with every node on that link being a member of the same network. If you break a major network (Class A, B, or C) into smaller subnetworks, it allows you to create a network of interconnecting subnetworks. Each data link on this network would then have a unique network/subnetwork ID. Any device, or gateway, connecting n networks/subnetworks has n distinct IP addresses, one for each network / subnetwork that it interconnects. Lecturer : Ahmed M. Al-Saleh & Mouayad Najim Page 15 University of Babylon/College of Information Technology/ Information Network Dept. / First Class / Second Semester/ Subject : Network and Distributed System/ Lecture : 2 To subnet a network, extend the natural mask using some of the bits from the host ID portion of the address to create a subnetwork ID. For example, given a Class C network of 204.15.5.0 which has a natural mask of 255.255.255.0, you can create subnets in this manner: 204.15.5.0 - 11001100.00001111.00000101.00000000 255.255.255.224 - 11111111.11111111.11111111.11100000 ------------------------------------------------|sub|---By extending the mask to be 255.255.255.224, you have taken three bits (indicated by "sub") from the original host portion of the address and used them to make subnets. With these three bits, it is possible to create eight subnets. With the remaining five host ID bits, each subnet can have up to 32 host addresses, 30 of which can actually be assigned to a device since host ids of all zeros or all ones are not allowed (it is very important to remember this). So, with this in mind, these subnets have been created. 204.15.5.0 255.255.255.224 host address range 1 to 30 204.15.5.32 255.255.255.224 host address range 33 to 62 204.15.5.64 255.255.255.224 host address range 65 to 94 204.15.5.96 255.255.255.224 host address range 97 to 126 204.15.5.128 255.255.255.224 host address range 129 to 158 204.15.5.160 255.255.255.224 host address range 161 to 190 204.15.5.192 255.255.255.224 host address range 193 to 222 204.15.5.224 255.255.255.224 host address range 225 to 254 Note: There are two ways to denote these masks. First, since you are using three bits more than the "natural" Class C mask, you can denote these addresses as having a 3-bit subnet mask. Or, secondly, the mask of 255.255.255.224 can also be denoted as /27 as there are 27 bits that are set in the mask. This second method is used with CIDR. Using this method, one of thse networks can be described with the notation prefix/length. For example, 204.15.5.32/27 denotes the network 204.15.5.32 255.255.255.224. When appropriate the prefix/length notation is used to denote the mask throughout the rest of this document. Lecturer : Ahmed M. Al-Saleh & Mouayad Najim Page 16 University of Babylon/College of Information Technology/ Information Network Dept. / First Class / Second Semester/ Subject : Network and Distributed System/ Lecture : 2 The network subnetting scheme in this section allows for eight subnets, and the network might appear as: Figure 2 Notice that each of the routers in Figure 2 is attached to four subnetworks, one subnetwork is common to both routers. Also, each router has an IP address for each subnetwork to which it is attached. Each subnetwork could potentially support up to 30 host addresses. This brings up an interesting point. The more host bits you use for a subnet mask, the more subnets you have available. However, the more subnets available, the less host addresses available per subnet. For example, a Class C network of 204.17.5.0 and a mask of 255.255.255.224 (/27) allows you to have eight subnets, each with 32 host addresses (30 of which could be assigned to devices). If you use a mask of 255.255.255.240 (/28), the break down is: 204.15.5.0 - 11001100.00001111.00000101.00000000 255.255.255.240 - 11111111.11111111.11111111.11110000 --------------------------------------------------|sub |--- Since you now have four bits to make subnets with, you only have four bits left for host addresses. So in this case you can have up to 16 subnets, each of which can have up to 16 host addresses (14 of which can be assigned to devices). Take a look at how a Class B network might be subnetted. If you have network 172.16.0.0 ,then you know that its natural mask is 255.255.0.0 or 172.16.0.0/16. Extending the mask to anything Lecturer : Ahmed M. Al-Saleh & Mouayad Najim Page 17 University of Babylon/College of Information Technology/ Information Network Dept. / First Class / Second Semester/ Subject : Network and Distributed System/ Lecture : 2 beyond 255.255.0.0 means you are subnetting. You can quickly see that you have the ability to create a lot more subnets than with the Class C network. If you use a mask of 255.255.248.0 (/21), how many subnets and hosts per subnet does this allow for? 172.16.0.0 - 10101100.00010000.00000000.00000000 255.255.248.0 - 11111111.11111111.11111000.00000000 ---------------------------| sub |------------------- You are using five bits from the original host bits for subnets. This will allow you to have 32 subnets (25). After using the five bits for subnetting, you are left with 11 bits for host addresses. This will allow each subnet so have 2048 host addresses (211), 2046 of which could be assigned to devices. Note: In the past, there were limitations to the use of a subnet 0 (all subnet bits are set to zero) and all ones subnet (all subnet bits set to one). Some devices would not allow the use of these subnets. Cisco Systems devices will allow the use of these subnets when the ip subnet zero command is configured. Examples Sample Exercise 1 Now that you have an understanding of subnetting, put this knowledge to use. In this example, you are given two address / mask combinations, written with the prefix/length notation, which have been assigned to two devices. Your task is to determine if these devices are on the same subnet or different subnets. You can do this by using the address and mask of each device to determine to which subnet each address belongs. DeviceA: 172.16.17.30/20 DeviceB: 172.16.28.15/20 Lecturer : Ahmed M. Al-Saleh & Mouayad Najim Page 18 University of Babylon/College of Information Technology/ Information Network Dept. / First Class / Second Semester/ Subject : Network and Distributed System/ Lecture : 2 Determining the Subnet for DeviceA: 172.16.17.30 - 10101100.00010000.00010001.00011110 255.255.240.0 - 11111111.11111111.11110000.00000000 ---------------------------| sub|--------------------subnet = 10101100.00010000.00010000.00000000 = 172.16.16.0 Looking at the address bits that have a corresponding mask bit set to one, and setting all the other address bits to zero (this is equivalent to performing a logical "AND" between the mask and address), shows you to which subnet this address belongs. In this case, DeviceA belongs to subnet 172.16.16.0. Determining the Subnet for DeviceB: 172.16.28.15 - 10101100.00010000.00011100.00001111 255.255.240.0 - 11111111.11111111.11110000.00000000 ---------------------------| sub|-----------subnet = 10101100.00010000.00010000.00000000 = 172.16.16.0 From these determinations, DeviceA and DeviceB have addresses that are part of the same subnet. Subnetting The procedure in which we browse some Host bits from the Host portion and add it in Network bits in Network Portion this procedure is called Subnetting. In Subnetting we increase the Network Portion and decrease the Host Portion. It means as Network Portion increases option of Sub networks also increases but the no of Hosts in each network start to decrease. For Example: 124.192.135.159 as we know an IP address is of 32 Bits It Is an IP address of Class A (Because in First Octet Value range is 0 – 126) Its Network Portion is of 8 bits Its Host Portion is of 24 bits Its Subnet mask is 255.0.0.0 Its Network ID is 124.0.0.0 Lecturer : Ahmed M. Al-Saleh & Mouayad Najim Page 19 University of Babylon/College of Information Technology/ Information Network Dept. / First Class / Second Semester/ Subject : Network and Distributed System/ Lecture : 2 Note: IP addresses are also represented as (IP/Network Bits) Class A 124.192.135.159/8 In Class A Network Portion is of 8 Bits Class B 189.200.191.239/16 In Class B Network Portion is of 16 Bits Class C 193.220.164.223/24 In Class C Network Portion is of 24 Bits 200.100.100.0/24 (IP of Class C + Network Portion = 24 Bits + Host Portion = 8 Bits) Let us Borrow 2-Bits from Host Portion (which have Host Portion = 8-Bits) Now Host Portion have Total Bits = 6 Add it in Network Portion (which have Network Portion = 24-Bits) Now Network Portion have Total Bits = 26 What is Custom Sub net Mask After Subnetting Default Subnet Mask of the IP address becomes Custom Subnet Mask. How many Subnets can form when we borrow some Bits from Host portion and add it in Network Portion? We can produce 2n (n = is equal to number of bits Borrow from Host Portion) If we Borrow 1 Bit 2nn = 1 21 2 Subnets can form If we Borrow 2 Bits 2nn = 2 22 4 Subnets can form If we Borrow 3 Bits 2nn = 3 23 8 Subnets can form If we Borrow 4 Bits 2nn = 4 24 16 Subnets can form If we Borrow 5 Bits 2nn = 5 25 32 Subnets can form If we Borrow 6 Bits 2nn = 6 26 64 Subnets can form Lecturer : Ahmed M. Al-Saleh & Mouayad Najim Page 20 University of Babylon/College of Information Technology/ Information Network Dept. / First Class / Second Semester/ Subject : Network and Distributed System/ Lecture : 2 How may Maximum Bits be able to borrow from Host Portion? We can borrow maximum 6 bits from Host Portion Note: If number of subnets increases congestion in the routing tables would be happened because size of routing tables increases but if Bandwidth is sufficient no congestion will take place. Types of Subnetting There are two types of Subnetting 1 Fixed Length Subnetting or Fixed Length Subnet Masking 2 Variable Length Subnetting or Variable Length Subnet Masking 1 Fixed Length Subnet Masking If we are sure that we have limit of subnets and not increases from the limit it is called Fixed Length Subnetting 2 Variable Length Subnet Masking --------------------------------------------------------------------------------------------------------------------------------------- Question: How Many Subnets can form using following IP Address we do sub netting of 2-Bits and How many Hosts Can be in each subnet? 200.100.100.0 Answer: Given IP address is 200.100.100.0 1 Class C 2 Network Portion 24-Bits 3 Host Portion 08-Bits 4 Representation of IP 200.100.100.0/24 Lecturer : Ahmed M. Al-Saleh & Mouayad Najim Page 21 University of Babylon/College of Information Technology/ Information Network Dept. / First Class / Second Semester/ Subject : Network and Distributed System/ Lecture : 2 5 Subnetting 6 After Subnetting Network Portion 7 After Subnetting Host Portion 06-Bits 8 After Subnetting IP 200.100.100.0/26 9 Number of Subnets 10 Number of Hosts per Subnet 2-Bits 26-Bits 2n n=2 22 4 2n n=6 26 64 Default Subnet Mask Default Subnet Mask of Class Full IP Address 200.100.100.0/24 As we know to find out the Default Subnet Mask we ON all 24-Bits of Network Portion of Class Full IP address 200 . 100 11111111. 255 . . 100 . 11111111. 255 . Network ID 0/24 1111111. 255 . of 0 0 Class Full IP 200.100.100.0/24 200.100.100.0 Custom Subnet Mask Custom Subnet Mask of Class Less IP Address 200.100.100.0/26 As we Know to find out the Custom Subnet Mask we ON all 26-Bits of Network Portion of class Less IP Address 200 . 100 11111111. 255 . . 100 11111111. 255 . 255 . 0/26 11111111. . 11000000 192 Lecturer : Ahmed M. Al-Saleh & Mouayad Najim Page 22 University of Babylon/College of Information Technology/ Information Network Dept. / First Class / Second Semester/ Subject : Network and Distributed System/ Lecture : 2 Subnet ID of Given Class Less IP 200 . 100 . 100 . 65 200 . 100 . 100 . 01000001 255 . 255 . 255 . 11000000 200 . 100 . 100 . 01000000 200 . 100 . 100 . 64 200.100.100.0/26 200.100.100.65/26 Custom Subnet Mask 200.100.100.65 100.100.100.01000001 255.255.255.11000000 255.255.255.192 100.100.100.01000000 200.100.100.64 Table 1 : Summery of Subnetting for Class A,B And C) # bits Subnet Mask CIDR # Subnets # Hosts 1 255.128.0.0 /9 2 8388608 2 3 4 255.192.0.0 255.224.0.0 255.240.0.0 /10 /11 /12 4 8 16 4194304 2097152 1048576 5 6 7 8 9 10 11 12 255.248.0.0 255.252.0.0 255.254.0.0 255.255.0.0 255.255.128.0 255.255.192.0 255.255.224.0 255.255.240.0 /13 /14 /15 /16 /17 /18 /19 /20 32 64 128 256 512 1024 2048 4096 524288 262144 131072 65536 32768 16384 8192 4096 13 14 255.255.248.0 255.255.252.0 /21 /22 8192 16384 2048 1024 Lecturer : Ahmed M. Al-Saleh & Mouayad Najim Page 23 University of Babylon/College of Information Technology/ Information Network Dept. / First Class / Second Semester/ Subject : Network and Distributed System/ Lecture : 2 15 16 17 18 19 20 21 22 255.255.254.0 255.255.255.0 255.255.255.128 255.255.255.192 255.255.255.224 255.255.255.240 255.255.255.248 255.255.255.252 /23 /24 /25 /26 /27 /28 /29 /30 32768 65536 131072 262144 524288 1048576 2097152 4194304 512 256 128 64 32 16 8 4 23 255.255.255.254 /31 8388608 2 # bits Subnet Mask CIDR # Subnets # Hosts 1 255.255.128.0 /17 2 32768 2 3 4 5 6 255.255.192.0 255.255.224.0 255.255.240.0 255.255.248.0 255.255.252.0 /18 /19 /20 /21 /22 4 8 16 32 64 16384 8192 4096 2048 1024 7 8 9 10 11 12 13 14 255.255.254.0 255.255.255.0 255.255.255.128 255.255.255.192 255.255.255.224 255.255.255.240 255.255.255.248 255.255.255.252 /23 /24 /25 /26 /27 /28 /29 /30 128 256 512 1024 2048 4096 8192 16384 512 256 128 64 32 16 8 4 15 255.255.255.254 /31 32768 2 # bits Subnet Mask CIDR # Subnets # Hosts 1 255.255.255.128 /25 2 128 2 3 4 5 6 255.255.255.192 255.255.255.224 255.255.255.240 255.255.255.248 255.255.255.252 /26 /27 /28 /29 /30 4 8 16 32 64 64 32 16 8 4 7 255.255.255.254 /31 128 2 Lecturer : Ahmed M. Al-Saleh & Mouayad Najim Page 24 University of Babylon/College of Information Technology/ Information Network Dept. / First Class / Second Semester/ Subject : Network and Distributed System/ Lecture : 2 Subnetting (Dividing Networks into Right Sizes) Every network within the internetwork of a corporation or organization is designed to accommodate a finite number of hosts. Some networks, such as point-to-point WAN links, only require a maximum of two hosts. Other networks, such as a user LAN in a large building or department, may need to accommodate hundreds of hosts. Network administrators need to devise the internetwork addressing scheme to accommodate the maximum number of hosts for each network. The number of hosts in each division should allow for growth in the number of hosts. Determine the Total Number of Hosts First, consider the total number of hosts required by the entire corporate internetwork. We must use a block of addresses that is large enough to accommodate all devices in all the corporate networks. This includes end user devices, servers, intermediate devices, and router interfaces. See Step 1 of the figure. Lecturer : Ahmed M. Al-Saleh & Mouayad Najim Page 25 University of Babylon/College of Information Technology/ Information Network Dept. / First Class / Second Semester/ Subject : Network and Distributed System/ Lecture : 2 Consider the example of a corporate internetwork that needs to accommodate 800 hosts in its four locations. Determine the Number and Size of the Networks Next, consider the number of networks and the size of each required based on common groupings of hosts. See Step 2 of the figure. We subnet our network to overcome issues with location, size, and control. In designing the addressing, we consider the factors for grouping the hosts that we discussed previously: Grouping based on common geographic location Grouping hosts used for specific purposes Grouping based on ownership Lecturer : Ahmed M. Al-Saleh & Mouayad Najim Page 26 University of Babylon/College of Information Technology/ Information Network Dept. / First Class / Second Semester/ Subject : Network and Distributed System/ Lecture : 2 Each WAN link is a network. We create subnets for the WAN that interconnect different geographic locations. When connecting the different locations, we use a router to account for the hardware differences between the LANs and the WAN. Although hosts in a common geographic location typically comprise a single block of addresses, we may need to subnet this block to form additional networks at each location. We need to create subnetworks at the different locations that have hosts for common user needs. We may also have other groups of users that require many network resources, or we may have many users that require their own subnetwork. Additionally, we may have subnetworks for special hosts such as servers. Each of these factors needs to be considered in the network count. We also have to consider any special security or administrative ownership needs that require additional networks. One useful tool in this address planning process is a network diagram. A diagram allows us to see the networks and make a more accurate count. To accommodate 800 hosts in the company's four locations, we use binary arithmetic to allocate a /22 block (2^10-2=1022). Allocating Addresses Now that we have a count of the networks and the number of hosts for each network, we need to start allocating addresses from our overall block of addresses. See Step 3 of the figure. Lecturer : Ahmed M. Al-Saleh & Mouayad Najim Page 27 University of Babylon/College of Information Technology/ Information Network Dept. / First Class / Second Semester/ Subject : Network and Distributed System/ Lecture : 2 This process begins by allocating network addresses for locations of special networks. We start with the locations that require the most hosts and work down to the point-to-point links. This process ensures that large enough blocks of addresses are made available to accommodate the hosts and networks for these locations. When making the divisions and assignment of available subnets, make sure that there are adequately-sized address blocks available for the larger demands. Also, plan carefully to ensure that the address blocks assigned to the subnet do not overlap. Lecturer : Ahmed M. Al-Saleh & Mouayad Najim Page 28 University of Babylon/College of Information Technology/ Information Network Dept. / First Class / Second Semester/ Subject : Network and Distributed System/ Lecture : 2 In our example, we now allocate blocks of addresses to the four locations as well as the WAN links. With the major blocks allocated, next we subnet any of the locations that require dividing. In our example, we divide the corporate HQ into two networks. Lecturer : Ahmed M. Al-Saleh & Mouayad Najim Page 29 University of Babylon/College of Information Technology/ Information Network Dept. / First Class / Second Semester/ Subject : Network and Distributed System/ Lecture : 2 we will look at addressing from another view. We will consider subnetting based on the number of hosts, including router interfaces and WAN connections. This scenario has the following requirements: • AtlantaHQ 58 host addresses • PerthHQ 26 host addresses • SydneyHQ 10 host addresses • CorpusHQ 10 host addresses • WAN links 2 host addresses (each) When creating an appropriate addressing scheme, always begin with the largest requirement. In this case, the AtlantaHQ, with 58 users, has the largest requirement. Starting with 192.168.15.0, we will need 6 host bits to accommodate the requirement of 58 hosts, this allows 2 additional bits for the network portion. The prefix for this network would be /26 and a subnet mask of 255.255.255.192. Let's begin by subnetting the original address block of 192.168.15.0 /24. Using the Usable hosts = 2^n - 2 formula, we calculate that 6 host bits allow 62 hosts in the subnet. The 62 hosts would meet the required 58 hosts of the AtlantaHQ company router. Address: 192.168.15.0 In Binary: 11000000.10101000.00001111.00000000 Mask: 255.255.255.192/26 Bits in binary : 11111111.11111111.11111111.11000000 Lecturer : Ahmed M. Al-Saleh & Mouayad Najim Page 30 University of Babylon/College of Information Technology/ Information Network Dept. / First Class / Second Semester/ Subject : Network and Distributed System/ Lecture : 2 This tables shows the the Networks IP Addressing for each Corporation after using (VLSM) depeond on the number of Hosts. Lecturer : Ahmed M. Al-Saleh & Mouayad Najim Page 31