CENG 362 - Homework 3 Due date: May 23rd Friday 23:55 What to
advertisement
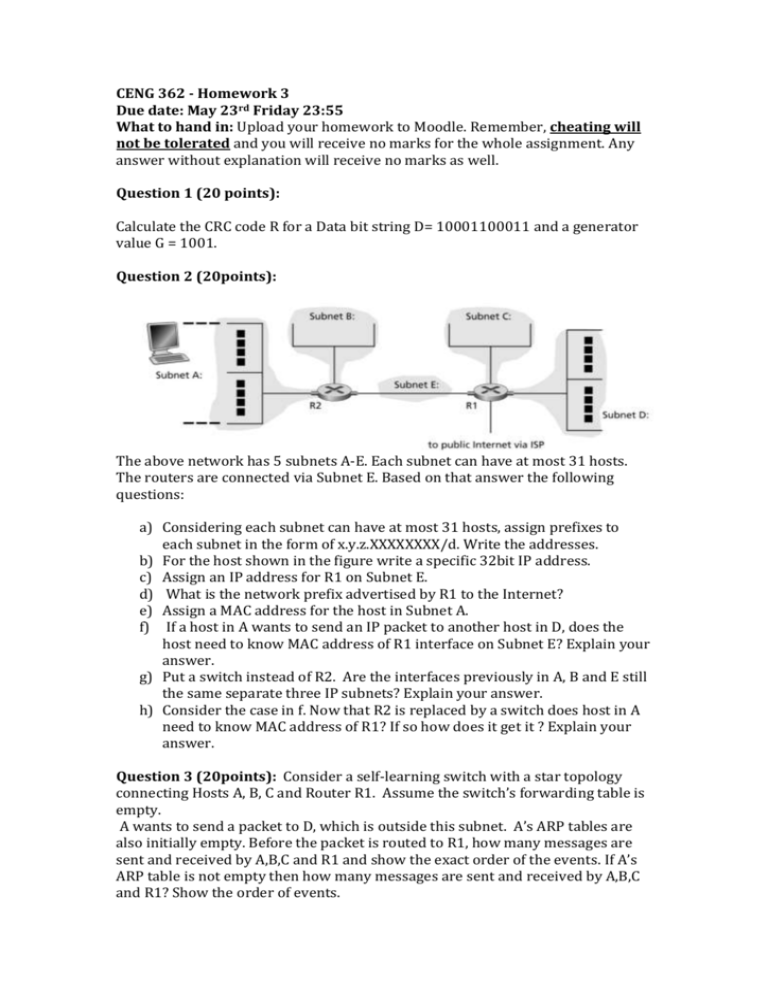
CENG 362 - Homework 3 Due date: May 23rd Friday 23:55 What to hand in: Upload your homework to Moodle. Remember, cheating will not be tolerated and you will receive no marks for the whole assignment. Any answer without explanation will receive no marks as well. Question 1 (20 points): Calculate the CRC code R for a Data bit string D= 10001100011 and a generator value G = 1001. Question 2 (20points): The above network has 5 subnets A-E. Each subnet can have at most 31 hosts. The routers are connected via Subnet E. Based on that answer the following questions: a) Considering each subnet can have at most 31 hosts, assign prefixes to each subnet in the form of x.y.z.XXXXXXXX/d. Write the addresses. b) For the host shown in the figure write a specific 32bit IP address. c) Assign an IP address for R1 on Subnet E. d) What is the network prefix advertised by R1 to the Internet? e) Assign a MAC address for the host in Subnet A. f) If a host in A wants to send an IP packet to another host in D, does the host need to know MAC address of R1 interface on Subnet E? Explain your answer. g) Put a switch instead of R2. Are the interfaces previously in A, B and E still the same separate three IP subnets? Explain your answer. h) Consider the case in f. Now that R2 is replaced by a switch does host in A need to know MAC address of R1? If so how does it get it ? Explain your answer. Question 3 (20points): Consider a self-learning switch with a star topology connecting Hosts A, B, C and Router R1. Assume the switch’s forwarding table is empty. A wants to send a packet to D, which is outside this subnet. A’s ARP tables are also initially empty. Before the packet is routed to R1, how many messages are sent and received by A,B,C and R1 and show the exact order of the events. If A’s ARP table is not empty then how many messages are sent and received by A,B,C and R1? Show the order of events. Question 4 (20points): Consider the RSA algorithm. If p = 7 and q = 13 what are n and z? If e is 17 why is this an acceptable solution, explain? Find d such that ed mod z = 1. Encrypt the message m = 9 using key (n,e). Show all work. Question 5 (20points): Alice wants to send a message to Bob. Bob has already got his certificate signed by CA and sent it to Alice. But Alice does not have a public/private key pair. The hash function used by both parties is H(-). a) Is it possible for Bob to verify that Alice created the message? If so show with a diagram between Bob and Alice on how to achieve it. b) How about confidentiality when sending the message from Alice to Bob? Show a block diagram if so as well.