ANATOMY OF AN ATTACK:
The Internet of Things (IoT) - The Hidden Danger Exposed
RESEARCH by TrapX Labs
Authored By:
TrapX Labs - A Division of TrapX Security, Inc.
March 6, 2015
Page _ 2
TABLE OF
CONTENTS
ABOUT ANATOMY OF AN ATTACK
3
EXECUTIVE SUMMARY
4
THE INTERNET OF THINGS
The IoT Supply Chain
Three Tiers of Risk
IoT Trends for the Future
5
5
7
8
THE NEST® THERMOSTAT HACK
9
11
11
13
Getting Root Access to NEST and Establishing the Tool Chain
Address Resolution Protocol (ARP) Spoofing with Capturing
Coding Details
RECOMMENDATIONS AND FINDINGS
15
INTRODUCING DECEPTIONGRID™
16
DeceptionGrid - Breaking the Intrusion Kill Chain
DeceptionGrid Technology
DeceptionGrid Differentiation
DeceptionGrid Benefits
ABOUT
About TrapX Labs
About TrapX Security, Inc.
FIND OUT MORE – DOWNLOAD DECEPTIONGRID
TrapX Security // www.trapx.com
16
17
18
18
20
20
20
21
Page _ 3
ABOUT ANATOMY OF
AN ATTACK
The Anatomy of an Attack (AOA) Series highlights the results of our research into
current or potential critical information security issues. The AOA series are
publications of TrapX Laboratories. The mission of TrapX Labs is to conduct critical
cybersecurity experimentation, analysis and investigation and to bring the benefits
back to the community at large through AOA publications and rapid ethical
compliance disclosures to manufacturers and related parties.
The TrapX Labs knowledge base benefits significantly from information on advanced
malware events shared with us by the TrapX Security Operations Center (TSOC).
Uniquely this TSOC threat analysis includes very deep intelligence on advanced
persistent threats (APTs) and Zero Day Events.
TrapX Security // www.trapx.com
Page _ 4
EXECUTIVE
SUMMARY
This AOA overviews our continued research into the Internet of Things (IoT). The
Internet of Things is the network of physical devices that contain embedded
technology which enable varying degrees of communication, command and control.
These devices may allow the ability to sense and/or interact with their internal
operations or even the external environment. Any single IoT device, without adequate
security, can present a serious threat to the networks to which they are connected. We
share our forward view of the impending escalation in IoT cyber-attacks and the risks
these pose to corporate, government and personal security. We also highlight IoT
trends and present our view of new attack vectors for continued research.
TrapX Labs recommend specific defensive measures and security best practices to
both to consumers of IoT devices as well as Original Equipment Manufacturers
(OEMs) in the supply chain. OEMs may buy IoT devices for integration within their
product lines or may source components which are acquired from overseas
manufacturers. We are concerned that the manufacturers of IoT devices at all points
in the supply chain do not seem to have the economic incentives to provide initial
cyber security support or ongoing support including the regular integration of
software and/or hardware updates. We share our recommendations and identify the
three tiers of risk we have discovered.
This AOA also shares our specific research into the NEST Learning Thermostat™
attack vector presented at the BlackHat® 2014 conference as a specific instance of IoT
risk. Our research validates and confirms several key findings. First, that while the
NEST device demonstrates relatively robust security compared to most other IoT
devices, the attack vectors presented at BlackHat® enabled us to completely
compromise the device within our Advanced Test Bed Facility (ATBF). Further, for
real world validation, we took this NEST device outside of our ATBF and had it
installed by technicians within a participant’s home network. Our lab “Black Hat”
penetration team was easily able to demonstrate compromise of the entire home
network using the NEST as an initial point of attack. This exploitation included
access to files on personal laptops and, perhaps more serious, to the corporate laptop
which this individual had brought home. We were able to access significant personal
data including the data collected by the NEST device which included when the
participant was home, as well as when they were not home.
TrapX Security // www.trapx.com
Page _ 5
THE INTERNET
OF THINGS
As noted earlier, the Internet of Things is the network of physical devices that contain
embedded technology which enable varying degrees of communication, command and
control. Consider that the number of IoT devices will grow to over 26 billion units
installed by the year 2020. This is almost a 30-fold increase from the 900 million
installed in 2009.1 For contrast, this number shows a growth rate and an installed
base much larger than that of smartphones, tablets and personal computers. By
2020 those devices will reach about 7.3 billion units.1
“The vast majority of IoT devices provide a wide
open door to advanced persistent threats and
other sophisticated malware. Cyber security
must be designed into these products initially.
Without this design and implementation, these
devices will present a huge potential risk to
your organization, your employees, your
business partners and your customers.”
Moshe Ben Simon
Vice President and Founder, TrapX Security
General Manager, TrapX Labs
Costs for IoT enablement will fall to well under $1 by 2020.1 This is very compelling
price point for manufacturers. These attractive prices contribute, in part, to the
integration of IoT connectivity even before any strategy for enabling security is
designed or delivered. Manufacturing, healthcare, insurance and many other
industries will all be heavy consumers of IoT connectivity. Yet the industries
producing these devices are far less aware and capable of preventing cyber disruption
than even the personal computer or networking industries.
The IoT Supply Chain
At every level of manufacture and design, the manufacturers involved with IoT are
obsessed with cost cutting and minimal design footprints. The design chain for
electronic components like IoT usually includes 2 or even 3 tiers of manufacturer,
1
Gartner Group. “Forecast: The Internet of Things, Worldwide 2013.” http://www.gartner.com
TrapX Security // www.trapx.com
Page _ 6
each integrating their products with the products of their suppliers. Unless their
customer specifies it, or unless the regulatory environment requires it for compliance,
additional features for cyber security will not go into the product.
IoT Supply Chain
CHIP LEVEL & SW KIT
ASSEMBLY LEVEL MODULE WITH
SW FOR INTERNET COMMUNICATION
FINAL PRODUCT:
BLOOD GAS ANALYZER
Copyright 2015 TrapX Security, inc.
We also found that many manufacturers that would enable the integration of IoT are
absolutely not aligning component level product designs with relevant security
standards. Many of them see this as important at the system level, for the final
integrated product, but not at their level. It must be driven by “the final customer in
the supply chain … the one that delivers the television set to the consumer.”
There are many important design standards for security that could be part of your
manufacturer best practices. These include ISO 27001/ 27002, NIST 800 or ISA/IEC62443. Yet even these standards do not completely protect you against the leading
edge of modern malware. Technologies such as DeceptionGrid™ exist because
modern malware, advanced persistent threats (APTs) and new Zero Day Exploits are
often able to circumvent and avoid other cyber defense technologies and the best
practices associated with them.
IoT devices, when used to anchor a malware attack, can expose your organization to
several major attack vectors. These can include man-in-the-middle, hidden
surveillance functions, remote code execution, weak password exploit and hardware
reverse engineering. Advanced malware just needs one entry point, think of it as
“patient zero” and then this anchor point can be used repeatedly to launch attacks to
everything connected to that network.
The list of devices that will add connectivity through the IoT is fairly large. The list of
potential devices includes everything you can imagine from DVD players, television
sets, wireless connected wearables, baby monitors, home automation hubs,
refrigerators, washing machines, dryers, microwave ovens, home alarm systems,
photo frames, MP3 players and gas station pumps. We’re not even considering the
impact of devices like the Apple® watch. Many of the manufacturers that make these
devices intend to buy the IoT connectivity in pre-assembled small modules that may
include hardware, mounting, chips and connectivity.
Consider that implications of the announcements that Google may be working with
various automakers to connect cars to Android®. Imagine that you can lock your
vehicle, unlock it, monitor critical vehicle functions or even start the engine from your
Android® phone or desktop computer.
Medical devices are an area of high connectivity and hence high concern for the IoT.
TrapX Security // www.trapx.com
Page _ 7
Many devices are already connected today and may include blood gas analyzers,
computerized tomography machines, colonoscopy test systems, stent insertion
monitors, and insulin pumps right up to pacemakers.
The risks for IoT medical devices and the hospitals that use them are so significant.
The United States Food and Drug Administration2 (FDA) has already issued guidance
in 2013 for securing wireless medical devices. Medical device manufacturers are
advised to address wireless safety and security issues very early in the device design,
through the development process, release and lifetime maintenance and then to the
end of the device’s life cycle. The FDA regulations (21 CFR 820) mandate that medical
device manufacturers take very significant steps when they incorporate wireless
technology into a medical device. This includes risk analysis, procedures and controls,
failure reports, corrective actions, and much more.
Beyond the FDA regulatory environment, the Health Insurance Portability and
Accountability Act (HIPAA) will also apply. Violation of the integrity of many of these
devices exposes Protected Health Information (PHI) data, defined under HIPAA
which may put a hospital or healthcare organization at serious risk for data breaches
and subsequent financial penalties.
Three Tiers of Risk
The first tier is one which affects laptop computers, networking devices, phones and
many other devices including IoT. This tier includes modules, chips or software
intentionally seeded with preinstalled malicious software. So what appears to be a
standard commercial product includes either hardware, firmware or software based
malware. TrapX Security’s publication of Zombie Zero in 2014 illustrated one such
incident of this type of technical attack. Microsoft® investigated this in 2012 and
found that many of the laptops and desktops with counterfeit copies of Windows XP
or 7 had a piece of malware called Nitol.A. Nitol.A established command and control
to external parties as soon as the computer was connected to the internet. This
allowed the laptops to be used for a variety of purposes the most basic of which was to
exfiltrate data loaded by the unsuspecting user. IoT presents a multitude of
opportunities to place malware in the subassemblies and software used to support IoT
connectivity. This malware is very hard to detect once it is designed into the IoT
components.
Other examples of integration at the chip or hardware level immediately translate to
the larger risk opportunity with IoT. In 2012 Cambridge researcher Sergie
Skorobogatov found that backdoors were deliberately built into military grade chips.3
These military grade chips were supposed to be much more secure than other
commercial grade chips. These backdoors were not done in firmware – but
implemented in the silicon so there was no available fix other than replacement of the
physical chip. Sergie and his co-workers were able to find and exploit this within a
period of two weeks. The possibilities for standard commercial grade chipsets are
significant.
The second tier is one where physical devices and software are compromised and then
placed back into circulation. Certainly this is one of our concerns with respect to the
NEST Hack and more. Hackers can buy and return both new and used equipment.
Each placement malware offers a very high probability of a successful breach. Home
networks almost have no defense for this type of attack. Once infected, the attacker
has an unlimited run of your assets. Even if discovered and removed from a laptop or
server, the initial point of entry in the NEST remains and can be used to launch
another attack.
2
Radio Frequency Wireless Technology in Medical Devices, Guidance for Industry and Food and Drug Administration
Staff, Doument issued on August 15, 2013
3
Business Insider, Robert Johnson, May 29, 2012, Cambridge Scientist Defends Claim That US Military Chips Made
In China Have 'Backdoors', Read more: http://www.businessinsider.com/sergei-skorobogatov-defends-backdoorclaims-2012-5#ixzz3TeM7ustb
TrapX Security // www.trapx.com
Page _ 8
The third tier is that offered by the exposed network port of an IoT device as a
relatively unprotected internet device. These ports generally allow access to
management functions and control functions almost without any protection.
IoT Trends for the Future
Massive IoT growth is certain in the near future. This present’s great potential
rewards for all of us but with this comes considerable risks. IT organizations must be
ready to manage a much broader set of technology that includes wearable devices,
sensors and new technology we cannot predict today. Enterprise security teams will
need to review and change policies to address these new risks on an enterprise wide
basis. Every new sensor provides a big increase in opportunity, risk and complexity
when connected to major enterprise infrastructure software systems.
There are other trends that IoT brings that will impact security significantly:
• The next few years are very big years for actual implementation driven by cost
reductions and compelling business case value. We will go from prototypes to
production. We will see in the market embedded systems in cars, wearable devices
and much more. Most of these early explosions in IoT implementation will
absolutely not have adequate security.
• IPv6 is truly required for IoT to expand. The market has not fully embraced IPv6
and likely won’t for another 12 to 24 months.
• IoT applications will now integrate data from these devices into many applications,
including business applications that have no connections to these data sources
today. The more connections to these insecure devices, the more opportunities for
compromise.
TrapX Security // www.trapx.com
Page _ 9
THE NEST®
THERMOSTAT HACK
One of the Internet of Thing hacks that were made visible recently was based upon
analysis of the Nest thermostat. The Nest thermostat is an Internet of Things (IoT)
home automation device that controls the temperature in your home or business.
Nest does this by learning your schedule and observing how you adjust the
temperature. Nest can adjusts its operations and it can also be controlled from a
mobile device such as your iPhone®. Nest automation is significant – it starts
learning about you and your home almost the first moment it is installed and
activated. It tracks when you are present in your home, and when you are out.
First visible in 2010, the NEST devices have been proved to be a huge success. In
January 2014 Google announced that it would spend $3.2 billion in cash to acquire
the entire company. Subsequent to the Google acquisition, Nest has in turn acquired
DropCam for roughly $555 million. All of this creates a huge web of IoT technology
which connects you and your personal information with the internet. Imagine that
information about your presence, or lack of presence, in your house is acquired on a
constant basis, stored and is potentially accessible.
At the Blackhat® conference in 2014 in Las Vegas, Nevada the NEST thermostat was
presented as a use case for an Internet of Things (IoT) hacking attack. At the time the
researchers from the University of Central Florida demonstrated how their attack
vectors worked. If an attacker can get physical access to the device, then in fairly
short order the device could be compromised. Once the backdoor is installed, the
compromised NEST can be used to penetrate and compromise other devices on the
network. Certainly, when hacked, it can be used to spy directly on the owner. The
TrapX Security // www.trapx.com
Page _ 10
DropCam acquisition makes this even more interesting given the much larger amount
of personal data. Of course, the passcodes to access your home wireless network are
in the NEST visible and unencrypted and therefore easily compromised as well.
Of course, since antivirus and other security software does not run on the NEST
device, there is no easy way to diagnose it. Traditional avenues such as producing a
full memory dump and submitting that to a cyber-security expert are not normally
achieved by the average homeowner or small business owner options.
In our Automated Test Bed Facility (ATBF) we took the NEST unit apart and did a
complete analysis of the components and potential entry points. We found an ARM
processor, controllers, memory and much more. Most important was easy access
to the mini-USB port. This access to the mini-USB port was essential to
implementing our chosen attack - this was our hardware open back door.
To be clear, the NEST device implemented PKCS #7 which is the Cryptographic
Message Syntax Standard from RSA Laboratories. This is definitely very good from a
security perspective. PKCS #7 defines a general syntax for messages that include
cryptographic enhancements such as digital signatures and encryption. The Public
Key Cryptography Standards (PKCS) is a group of public-key cryptography standards
created by RSA Security Inc. The company published the standards to promote the use
of the cryptography techniques to which they had intellectual property (patents). This
has also been adopted by the IETF.
TrapX Security // www.trapx.com
Page _ 11
“Make no mistake – the NEST® Thermostat is a
well-designed and relatively secure IoT device.
The problem is that the hackers are moving
faster, with more intensity and with more
funding. We are losing an undeclared cyber
war even before most of us recognize that this
war has already started. This requires far
greater investment in cyber security and a
change in strategy as we go forward with IoT.”
Moshe Ben Simon
Vice President and Founder, TrapX Security
General Manager, TrapX Labs
Getting Root Access to NEST and Establishing
the Tool Chain
The Mini USB port gave us the necessary root access to the NEST operating system.
We found that root access allows minimal attack vectors such as “SSH Reverse
Tunnel” but still the operating system was reasonably well hardened and did not
make it easy to run hacking tools.
The NEST device uses the ARMv7 platform and was missing standard libraries so it
was challenging to develop the hacking tools. We had to cross compile multi-threaded
GCC and Binutils for the ARMv7 platform. The hack also required that we fix some 32
bit atomics intrinsic in the GSS version to allow proper execution of atomic
instructions. Further, we compiled a number of missing standard libraries for tool
chain, including LIBstdc++ and libz.
Address Resolution Protocol (ARP) Spoofing with
Capturing
At that point, we wrote a basic ARP spoofing application to spoof the ARP address for
the gateway without appropriate routing as the first version of our test. ARP Spoofing
is a type of attack in which a bad actor sends falsified ARP (Address Resolution
Protocol) messages over a local area network. This results in the linking of an
attacker’s MAC address with the IP address of a legitimate computer or server on the
network. This can cause all traffic meant for that IP address to be sent to the attacker
instead.
TrapX Security // www.trapx.com
Page _ 12
Think of it as sitting in the middle of a two party conversation, listening to
everything and capturing the data transmitted between the two parties whenever you
want and without detection.
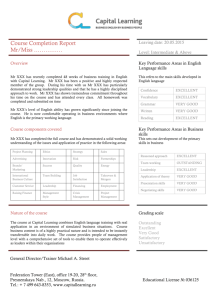
ARP Spoofing
USER B / ADDRESS C
NEST® THERMOSTAT
USER C / ADDRESS C
USER A / ADDRESS A
Switch
DI
ED
•NEST® Hack Established
command and control
•User “A” messages addressed
to user “C” are re-routed by
modified addresses secretly
to Attackers
•Attacker looks like address
A to user C
•Attacker looks like address
C to user A
VE
RT
RT
VE
ARP
SPOOFING
ATTACK
ED
DI
Router
Internet
ATTACKER
Copyright 2015 TrapX Security, inc.
In order to write the ARP spoofing application we use two main libraries: LibCrafter
and LibPcap. It is definitely a difficult task to port all the code for these libraries to the
platform in question and cross-compile it.
TrapX Security // www.trapx.com
Page _ 13
To complete the hack we developed a multi-threaded C++ application on top of
Libcrafter and the LibPcap API’s. Prior to creating an ARP spoofing object by using
the LibCrafter API’s, we set up IPv4 forwarding. Then we initialized both of these
processes to begin the appropriate host spoofing execution. This supported both the
single and netmask based host spoofing (CLI args). Next we created a sniffer object
and used this to filter all the IP traffic before processing it through the callback chain
(callback depth was one for now). We then saved all of these packets from that host in
a capture file whose name was CLI arg. Of course, we had to provide all the proper
interrupt handling and related housekeeping. Upon gathering the SIGINT data, we
then free all of the memory, unlink the files in use, reset the IP forwarding and try to
fix all of the ARP entries before exiting.
So you can see the attack scenario clearly: Install the compromised NEST device and
connect to a target network; run ARP spoof against the local PC, capture all of the
traffic and save it to a pcap file, and then extract from the pcap file user names and
passwords for FTP service. The NEST hack allows you to completely compromise the
security of the network. Once the entry point with the NEST device was in place, we
were then able to compromise just about everything within that network.
Coding Details
For those of you that are interested, we take the level of detail about our coding a bit
further:
• Initialize the global context for handling appropriate hosts and the interface to
spoof, context = arp_spoofing_context (gw_router, victim_net, iface).
• We then obtain the MAC id of our interface and prepare to send the replies to the
victim net with that of routers mac (we obtain routers mac by ARP broadcasts
request).
• On receiving the ARP resolution request, we then prepare the ARP response from
the victim and send back the response and initialize a thread to handle the
subsequent requests from that client.
• Inside arp_spoof_handler, we pass through all the packets from the particular
host, dissect the packet, push the new MAC layer to be forwarded to gw_net, push
back rest of the layers (IP, TCP, Application) and forward the packet.
• This is done using raw TCP/IP sockets using appropriate parameters.
Then we need to capture the packets:
• The first step is to initialize the global context for capturing packets using Berkeley
Packet Filter (BPF).
• Inside the capture handler, we create the file and save the file pointer in static file
handler and then write the global capture header in the file (little or big-endian,
frame type, etc.).
• For each new packet we receive, we simply get called back for the appropriately
filtered packets.
• Appropriately filtered packets are then dissected to extract certain layers and
critical information. We then have to create a packet header for every packet and
write it to the file along with the packet data.
Here are some views of our code in execution:
TrapX Security // www.trapx.com
Page _ 14
PUTTY Code
root@02AA01AC351407FJ# LD_LIBRARY_PATH ./arp_spoof.o -h
usage: ./ ./arp_spoof.o <interface> <gatewaiy ip> <host_to_spoof_> <name of capture file>
ex:
./ ./arp_spoof.o eth0 10.1.1.1 10.1.1.4 arp_poison.pcap
root@02AA01AC351407FJ# []
Copyright 2015 TrapX Security, inc.
Additional Code
File Edit View Go Capture Analyze Statistics Telephony Tools Internals Help
No.
Time
Source
Protocol
Length
Info
1881
0.000000
192.xxx.x.xx 107.xxx.xxx
Destination
FTP
60
Request: \000\000\000\000\xxx\xxx
1888
0.000000
107.xxx.xxx
192.xxx.x.xx
FTP
374
Response: 2200---welcome to Pure-FTPd [privsep] [TLS]
1889
0.000000
107.xxx.xxx
192.xxx.x.xx
FTP
374
[TCP Retransmission] Response: 220---welcome to Pure-FTPd [privsep] [TLS]
1892
0.000000
192.xxx.x.xx 107.xxx.xxx
FTP
60
[TCP Retransmission] Request: \000\000\000\000\xxx\xxx
1901
0.000000
107.xxx.xxx
192.xxx.x.xx FTP
374
[TCP Retransmission] Response: 220---welcome to Pure-FTPd [privsep] [TLS]
1902
0.000000
107.xxx.xxx
192.xxx.x.xx FTP
374
[TCP Retransmission] Response: 220---welcome to Pure-FTPd [privsep] [TLS]
1903
0.000000
192.xxx.x.xx 107.xxx.xxx
FTP
60
[TCP Retransmission] Request: \000\000\000\000\xxx\xxx
2023
0.000000
192.168.0.26
107.xxx.xxx
FTP
69
[TCP Out-of-Order] Request: User download
2024
0.000000
192.xxx.x.xx
192.xxx.x.xx ICMP
97
Redirect (Redirect for host)
2025
0.000000
192.xxx.x.xx 107.xxx.xxx
FTP
69
[TCP Retransmission] Request: User download
2030
0.000000
107.xxx.xxx
192.xxx.x.xx FTP
60
[TCP ACKed unseen segment] Response: \000\000_%\xxx\xxx
2032
0.000000
107.xxx.xxx
192.xxx.x.xx FTP
95
[TCP Out-of-Order] Response: 331 user download OK. Password Required
2033
0.000000
107.xxx.xxx
192.xxx.x.xx FTP
95
[TCP Retransmission] Response: 331 user download OK. Password Required
2040
0.000000
192.xxx.x.xx 107.xxx.xxx
FTP
60
[TCP ACKed unseen segment] Request: \000\000\000\000\xxx\xxx
2325
0.000000
192.xxx.x.xx 107.xxx.xxx
FTP
69
[TCP Out-of-Order] Request: Pass X X X x!
2326
0.000000
192.xxx.x.xx
97
Redirect (Redirect for host)
2327
0.000000
192.xxx.x.xx 107.xxx.xxx
FTP
69
[TCP Out-of-Order] Request: Pass X X X x!
2332
0.000000
107.xxx.xxx
192.xxx.x.xx FTP
86
[TCP ACKed unseen segment] Response: 230 OK. Current directory is /
2333
0.000000
107.xxx.xxx
192.xxx.x.xx FTP
86
[TCP Retransmission] Response: 230 OK. Current directory is /
2340
0.000000
107.xxx.xxx
107.xxx.xxx
60
Request: \000\000\000\000\000\000
192.xxx.x.xx ICMP
FTP
Copyright 2015 TrapX Security, inc.
TrapX Security // www.trapx.com
Page _ 15
RECOMMENDATIONS
AND FINDINGS
Our review of the security infrastructure of the internet of things (IoT) provided a
considerable wealth of information for us. We have several recommendations and
findings that flow from our assessment of the Internet of Things risks. This is
based upon TrapX Security Lab's (TSL’s) experience, our constant dialog with other
leading security experts on a global basis and our views of current and emerging
trends within the marketplace:
• Do a design review on all of your OEM components, especially those manufactured
overseas. This will take a lot of work but we view it as essential for anyone in the
defense industry and highly desirable for most manufacturers that integrate
electronic components and chips;
• Consider your strategy to rapidly integrate and deploy software fixes and/or
hardware fixes to your end-user customer base, especially if you have a 2 or 3 tier
supply chain;
• Avoid allowing any of these devices to be bootable from a USB port in the
production versions;
• Sign the software – this is a mathematical technique used to validate the
authenticity of the software;
• Run security tests to discover vulnerabilities and help with the design review of
OEM components – we’d recommend use an outside security penetration firm;
• Implement firewalls to resist hacker attacks and only allow specified IP addresses
in or out – every device needs one; and,
• Protect the project management interface from attackers and only allow limited
access to the management server.
TrapX Security // www.trapx.com
Page _ 16
INTRODUCING
DECEPTIONGRID™
Deception technology is a new category of cyber security designed to meet head-on
the threats of malicious software, targeted attacks, zero day exploits and other
sophisticated attacks.
DeceptionGrid automates the deployment of a network of camouflaged malware traps
that are intermingled with your real information technology resources. The traps
appear identical in every way to your real IT assets.
Once malware has penetrated your enterprise, the attackers move laterally to find
high value targets. Just one touch of the DeceptionGrid sets off a high confidence
ALERT. Real-time automation isolates the malware and delivers a comprehensive
assessment directly to your SOC team.
Now the basic pattern of malware deployment and privilege escalation activity is
disrupted. At the first moment of reconnaissance and lateral movement the APT is
identified positively. Automation adds powerful forensics so that your SOC team has
an almost immediate understanding of the nature of the attack. You can begin rapidly
to implement the best path for remediation and removal.
DeceptionGrid – Breaking the Intrusion Kill Chain
The malicious tools the hackers use are constantly changing, yet the underlying
methods used by sophisticated attackers are so predictable that the security
research community has given this multistage chain of events its own name: the
Intrusion Kill Chain. Technology blind spots have prevented most organizations
from detecting, analyzing and disrupting the early and middle stages of the cyber
kill chain. The TrapX DeceptionGrid™ now makes it possible to eliminate these
blind spots by breaking the Kill Chain.
TrapX Security // www.trapx.com
Page _ 17
GOVERNMENT AND
COMMERCIAL ENTERPRISE
Research
Infiltration
Command & Control
Infected IT Asset
BREAKING
THE ATTACKER’S
KILL CHAIN
ALERT
Malware TRAP
Real IT Asset
SANDBOX
ANALYZE
PAYLOAD
Malware TRAP
SCAN & REMEDIATE
ALL HOSTS
Copyright 2015 TrapX Security, inc.
DeceptionGrid Technology
DeceptionGrid has been designed from the beginning to fit efficiently and securely
into MSSP operations. DeceptionGrid includes Malware Trap Sensors and Network
Intelligence Sensors. Our Security Intelligence Management provides Integrated
Event Management and fully automated Forensic Analysis.
This automated analysis enables the SOC to move faster yet at the same time reduce
costs as excess escalation is no longer required. Further, DeceptionGrid’s mechanism
of generating an alert is not based upon a probabilistic event or clustering around
adjustable thresholds. These are very high confidence events. These alerts are directly
generated and triggered by explicit contact with our Malware Trap Sensors.
TrapX Security // www.trapx.com
Page _ 18
Deception Grid TM
DeceptionGrid Differentiation
DeceptionGrid offers several key points of differentiation. These include:
• Real-time detection of malware movement anywhere within the vLan in your
enterprise. Deployment of DeceptionGrid sensors is comprehensive across the
entire enterprise and provides virtually 100% coverage.
• Reduction in the big data problems bringing hundreds to thousands of alerts that
overwhelm the SOC today. Or missing key alerts due to the configuration of alert
thresholds. A TrapXalert is over 99% accurate and immediately actionable.
• Complete analysis of malware, even zero day events, is automated and fast. Your
security operations center has everything they need to take action.
• Automated deployment of your DeceptionGrid for your entire enterprise enables
provision and management on a scale unattainable with legacy deception based
technology such as honeypots.
• Protect all vLans for identified malware, even zero day events, when you find one
instance of a threat within your networks. Our Threat Intelligence Center leverages
our unique defense on a global basis. DeceptionGrid moves rapidly to help
DeceptionGrid Benefits
The benefits of deception technology are very significant. DeceptionGrid is specifically
targeted for the new breed of APT. DeceptionGrid innovation finds sophisticated
malware and zero day events that your existing vendors do not detect. DeceptionGrid
can detect attackers when they move laterally within networks, identify them, and
then help your SOC remediate them rapidly and effectively.
Additional benefits of DeceptionGrid include:
• Shifting the cost and risk to the attacker. DeceptionGrid fundamentally changes
the economics of cyber defense by shifting the cost to the attacker.
• Faster diagnosis and remediation. Advanced real-time forensics and analysis
empowers the security operations center to take immediate action to disrupt all
attacks within the network perimeter.
• Reductions or elimination of economic loss. Better detection reduces the risk of
economic loss due to destruction of enterprise assets, theft of data, and overall
impact to business operations.
TrapX Security // www.trapx.com
Page _ 19
• Deployment of the most powerful class of cyber detection and defense at the lowest
levels of cost. Automated forensics, automated deployment at enterprise levels of
scale and integration with our global threat intelligence center.
• Stronger support for your compliance programs. Reducing or eliminating the
threat from advanced attacks improves organizational ability to comply with PCI,
HIPAA, data breach laws and HIV/AIDS patient data laws and other legislative
requirements on a global basis. Data breaches are expensive and can be reduced or
eliminated with improved detection technology.
• DeceptionGrid is compatible with your existing environments. DeceptionGrid can
integrate with existing operations and defense-in-depth vendor software suites.
TrapX Security // www.trapx.com
Page _ 20
ABOUT
About TrapX Labs
The TrapX Security Labs division was established as an independent research team
within TrapX Security in 2014. Our mission has been clear – to conduct critical
cybersecurity experimentation, analysis and investigation and to bring the benefits
back to the community at large through our publications and our rapid ethical
compliance disclosures to manufacturers and related parties. Since our inception,
TSL has worked to create the next generation of technologies and best practices such
that we can ultimately provide leading resources for the evolution of cyber security.
TrapX Labs division conducts applied research focused on specific cyber threats and
their countermeasures. The TrapX Labs team members develop and apply leading
edge technologies in computing, network architectures, network forensics, malware
analysis, and analysis of commercial hardware and software to solve and understand
the anatomy of these complex attacks. TrapX Lab’s Advanced Test Bed Facility
(ATBF) brings together our researchers with our domain knowledge of current events
which stream from the TrapX Security Operations Center (TSOC). The TSOC provides
a constant feed of new and diverse problems that bring real-world complexity to our
engineers and researchers in real-time.
About TrapX Security, Inc.
TrapX Security is a leader in the delivery of deception based cyber security defense.
Our solutions rapidly detect, analyze and defend against new zero-day and APT
attacks in real-time. DeceptionGrid™ provides automated, highly accurate insight
into malware and malicious activity unseen by other types of cyber defense. We
enable a pro-active security posture, fundamentally changing the economics of cyber
defense by shifting the cost to the attacker. The TrapX Security customer base
includes global 2000 commercial and government customers around the world in
sectors including defense, healthcare, finance, energy, consumer products and other
key industries.
TrapX Security // www.trapx.com
Page _ 21
FIND OUT MORE –
DOWNLOAD DECEPTIONGRID
Come to www.trapx.com and download our FREE proof of concept and trial for
qualifying organizations.
TrapX Security, Inc., 1875 S. Grant St., Suite 570
San Mateo, CA 94402
+1–855–249–4453
www.trapx.com
Download our product: links on the bottom
of our homepage via www.trapx.com
For sales: sales@trapx.com
For partners: partners@trapx.com
For support: support@trapx.com
TrapX, TrapX Security, DeceptionGrid and all logo’s are trademarks or
registered trademarks of TrapX in the United States and in several other
countries.
Cyber Kill Chain is a registered trademark of Lockheed Martin.
NEST, NEST Learning Thermostat™ are trademarks of NEST Labs, Inc.
Other trademarks are the property of their respective owners.
© TrapX Software 2013. All Rights Reserved.
TrapX Security // www.trapx.com