Chapter 13 - shaieb.net

Chapter 13: Software Architecture
Impact on network defense
Where and how application components should be deployed
Many issues related to placement of components
Software Architecture and Network Defense
The Importance of Software Architecture o Placement
Deciding where to deploy a component is a complicated issue
Many applications do not work properly when their traffic is going through firewalls (Incompatible with NAT).
Some applications needs and defense components often at odds with each other.
Two viewpoints must be considered
If defenses must be weakened, then application should not be used
(emphasis on security).
If the emphasis is on business mission, then security should be flexible. o The Need to Evaluate Application Security
Should be considered from the beginning.
How Software Architecture Affects Network Defense
Firewall and Packet-Filtering Changes o The most common issues involving software architecture and network defense is that of changing firewall rule sets and router ACLs. o Some applications require more that one open port. o Recommendation: Limit which internal hosts can be accessed through those ports.
Internal Application Components o Over the past several years, various protocols have been developed to facilitate communications among distributed application components in network environments regardless of the language. o Two of the best-known architectures are:
DCOM – Distributed Component Object Model
Each process assigned a TCP port
Processes connect to server control manager on port 135 to get the dynamic ports for the process.
It does not work well with NAT.
CORBA – Common Object Request Broker Architecture
Is an industry standard for designing distributed application objects.
Implementation use IIOP (Internet Inter-ORI Protocol)
No fixed port number (different implementation use different ports)
Some IIOP-based applications require two or more channels.
May be tunneled using http.
Known to have problems with NAT.
SOAP – Simple Object Access Port
Part of Microsoft .NET.
Similar functionality as DCOM and IIOP.
Can be tunneled over HTTP.
Problem: Port 80 is intended to carry HTTP traffic. If the trend continues, port 80 traffic will be extremely difficult to monitor and control.
Encryption Connections o Many applications do not encrypt data. o The significance depends on your organization’s security policy. o May be needed if information is sensitive or going through shared networks.
Performance o Firewall and encryption can add considerable delays.
Reliability o The more devices, then less reliable the application will be.
Atypical Operating System o Some applications might require the use of a particular operating system that is no normally used in your environment.
Support issues
Lack of knowledge to secure the OS.
Software Component Placement
Single System Applications o Major decision where to place host. o If the system has external users
You might want to place them on a screened subnet
On internal networks, you could deploy a proxy server for it on a screened subnet.
NOTE: In both cases, external users are connecting to the system on your screened subnet and are unable to initiate a connection to your internal network.
You will need to alter your firewall rules to allow hosts to initiate a connection to only the screened subnet hosts using only the necessary port numbers.
Multitier Applications o It consists of distributed components usually residing in separate systems. o Three Components
User Interface
Middleware component
Database component o Strategy (Regardless of the number of tiers)
Most sensitive component, the most isolated component [the one containing data]
Users should never access data directly. o Recommendations
Place servers containing data on a private network and restrict access to them.
User interface should be place in a screened subnet.
Risk is reduced by keeping each tier on a different machine.
Identifying Potential Software Architecture Issues
Better to be proactive in identifying problems.
Software Evaluation checklist o 8 items page 366-7.
How to Handle an Unsecurable Application o Replace application or modify it (must understand security risks).
Software Testing
Time and time again, application have worked great in a test environment, but fail when deployed in the production environment.
Typically because the two environments are different.
Host Security o The application might have been tested on a server that had not been secured or hardened at all, and it broke in production when it couldn’t perform the same actions on the secured system that it could on the unsecured system. o Moral: Test the application on a server with configurations similar to the production configuration. o Application tested successfully with full admin privileges. o Moral: Consider privilege levels in the design.
Network Configuration and Security o Another problem is that applications are tested without production network security measures in place. o During testing, all the components of the software solution are often on servers on the same subnet, in which firewalls or packet filters are no involved. o Solution: To duplicate the production environment; however, that can be very expensive. o Options
Duplicate only parts of the production network.
Test using the production network.
In this case put the servers in a screened subnet and shield them from everything but test traffic.
NOTE: If application does not work, do not adjust firewall rules on the fly.
Network Defense Design Recommendations
Establishing a network defense that can handle the needs of the applications in a secure manner is important.
Proactive Steps o Choose firewalls and border routers that are sophisticated enough to securely support various types of applications. o It is a good idea to have extra interfaces in your firewalls. o Understand the basics of various areas of security: host, network, application, and database security.
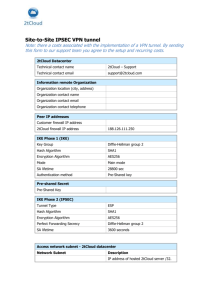
Case Study: Web-Based Online Billing Application
Goal: Is to allow users to view and pay bills online.
Requirements o Must use data in existing billing database. o This is very sensitive, because customers will be providing their credit card or checking account numbers as part of the payment process. o The company is particularly concerned about protecting that information.
PERRY DRAW PICTURE 13.2 DUDE!!!
Figure 13.2
This perimeter network has a firewall that connects two screened subnets with the
Internet and internal network; it also provides NAT capabilities for internal hosts that access the Internet.
Application Description
Web-based user interface
Application server
Database
Deployment Locations
Database should stay in the internal network.
Option 1) Web Interface on existing screened subnet o Interface could be deployed on existing servers.
Potential Problems o The firewall might not be able to handle the protocols used between the web server and the application server. o The data that is passed between the web and application server needs to be encrypted. o External hosts would directly access the webserver.
Option 2) Web Interface and application server on same screened subnet o Use existing o Create new screened subnet
Option 3) All Components on the Internal Network o May need a reverse proxy server on screened subnet to handle requests on behalf of the web-based interface. o If not feasible to use a reverse proxy server, then users could enter your internal network.
Recommendation
Select option number 1 because it is the least resource intensive.
Why o Least-expensive o Least resource intensive o Provides a good level of network security
Lots of examples in Chapter 16,,, good material for the exam….