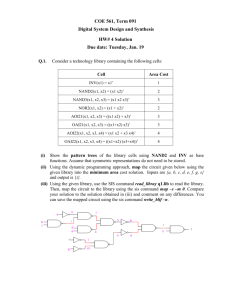
Lattice-Based Cryptography: =1=Short Integer Solution (SIS) and =1
advertisement

Lattice-Based Cryptography:
Short Integer Solution (SIS) and
Learning With Errors (LWE)
Chris Peikert
Georgia Institute of Technology
crypt@b-it 2013
1 / 17
Recall: Lattices
I Full-rank additive subgroup in Zm .
O
2 / 17
Recall: Lattices
I Full-rank additive subgroup in Zm .
I Basis B = (b1 , . . . , bm ) :
m
L(B) = B · Z
=
m
X
b2
(Z · bi )
i=1
b1
O
2 / 17
Recall: Lattices
I Full-rank additive subgroup in Zm .
I Basis B = (b1 , . . . , bm ) :
m
L(B) = B · Z
=
m
X
b1
(Z · bi )
i=1
O
b2
2 / 17
Recall: Lattices
I Full-rank additive subgroup in Zm .
I Basis B = (b1 , . . . , bm ) :
m
L(B) = B · Z
=
m
X
b1
(Z · bi )
i=1
O
b2
(Other representations too . . . )
2 / 17
Recall: Lattices
I Full-rank additive subgroup in Zm .
I Basis B = (b1 , . . . , bm ) :
m
L(B) = B · Z
=
m
X
b1
(Z · bi )
i=1
O
b2
(Other representations too . . . )
Hard Problems
I Find/detect short nonzero lattice vector(s): SVP, GapSVP, SIVP
I Decode under small amount of error: BDD
2 / 17
A Hard Problem: Short Integer Solution
I Znq = n-dimensional vectors modulo q
(e.g., q ≈ n3 )
3 / 17
A Hard Problem: Short Integer Solution
I Znq = n-dimensional vectors modulo q
|
a1
|
|
a2
|
(e.g., q ≈ n3 )
···
|
am
|
∈ Znq
3 / 17
A Hard Problem: Short Integer Solution
I Znq = n-dimensional vectors modulo q
(e.g., q ≈ n3 )
I Goal: find nontrivial small z1 , . . . , zm ∈ Z such that:
|
|
|
|
z1 · a1 + z2 · a2 + · · · + zm · am = 0 ∈ Znq
|
|
|
|
3 / 17
A Hard Problem: Short Integer Solution
I Znq = n-dimensional vectors modulo q
(e.g., q ≈ n3 )
I Goal: find nontrivial short z ∈ Zm such that:
· · · · A · · · ·
z = 0 ∈ Znq
|
{z
}
m
3 / 17
A Hard Problem: Short Integer Solution
I Znq = n-dimensional vectors modulo q
(e.g., q ≈ n3 )
I Goal: find nontrivial short z ∈ Zm such that:
· · · · A · · · ·
z = 0 ∈ Znq
|
{z
}
m
One-Way & Collision-Resistant Hash Function
I Set m > n lg q. Define fA : {0, 1}m → Znq as
fA (x) = Ax.
3 / 17
A Hard Problem: Short Integer Solution
I Znq = n-dimensional vectors modulo q
(e.g., q ≈ n3 )
I Goal: find nontrivial short z ∈ Zm such that:
· · · · A · · · ·
z = 0 ∈ Znq
|
{z
}
m
One-Way & Collision-Resistant Hash Function
I Set m > n lg q. Define fA : {0, 1}m → Znq as
fA (x) = Ax.
I Collision x, x0 ∈ {0, 1}m where Ax = Ax0 . . .
3 / 17
A Hard Problem: Short Integer Solution
I Znq = n-dimensional vectors modulo q
(e.g., q ≈ n3 )
I Goal: find nontrivial short z ∈ Zm such that:
· · · · A · · · ·
z = 0 ∈ Znq
|
{z
}
m
One-Way & Collision-Resistant Hash Function
I Set m > n lg q. Define fA : {0, 1}m → Znq as
fA (x) = Ax.
I Collision x, x0 ∈ {0, 1}m where Ax = Ax0 . . .
. . . yields solution z = x − x0 ∈ {0, ±1}m , of norm kzk ≤
√
m.
3 / 17
Cool!
(but what does this have to do with lattices?)
4 / 17
Cool!
(but what does this have to do with lattices?)
I Parity-check matrix
A = (a1 , . . . , am ) ∈ Zn×m
q
defines the ‘q-ary’ integer lattice
L⊥ (A) = {z ∈ Zm : Az = 0}.
O
4 / 17
Cool!
(but what does this have to do with lattices?)
I Parity-check matrix
(0, q)
A = (a1 , . . . , am ) ∈ Zn×m
q
defines the ‘q-ary’ integer lattice
L⊥ (A) = {z ∈ Zm : Az = 0}.
(q, 0)
O
4 / 17
Cool!
(but what does this have to do with lattices?)
I Parity-check matrix
(0, q)
A = (a1 , . . . , am ) ∈ Zn×m
q
defines the ‘q-ary’ integer lattice
L⊥ (A) = {z ∈ Zm : Az = 0}.
I SIS is SVP on random lattices L⊥ (A)!
(q, 0)
O
4 / 17
Cool!
(but what does this have to do with lattices?)
I Parity-check matrix
(0, q)
A = (a1 , . . . , am ) ∈ Zn×m
q
defines the ‘q-ary’ integer lattice
L⊥ (A) = {z ∈ Zm : Az = 0}.
I SIS is SVP on random lattices L⊥ (A)!
I Syndrome u ∈ Znq defines coset
x
(q, 0)
O
L⊥
u (A) = {x : Ax = u},
x 7→ Ax reduces x modulo L⊥ (A).
4 / 17
Cool!
(but what does this have to do with lattices?)
I Parity-check matrix
(0, q)
A = (a1 , . . . , am ) ∈ Zn×m
q
defines the ‘q-ary’ integer lattice
L⊥ (A) = {z ∈ Zm : Az = 0}.
I SIS is SVP on random lattices L⊥ (A)!
(q, 0)
I Syndrome u ∈ Znq defines coset
O
L⊥
u (A) = {x : Ax = u},
x 7→ Ax reduces x modulo L⊥ (A).
Worst-Case/Average-Case Connection
[Ajtai’96,. . . ]
Finding short (kzk ≤ β q) nonzero z ∈ L⊥ (A)
for uniformly random A ∈ Zn×m
q
⇓
solving GapSVPβ √n and SIVPβ √n on any n-dim lattice.
4 / 17
A “Key” Trick
I Generate uniform A with a short solution x (s.t. Ax = 0):
5 / 17
A “Key” Trick
I Generate uniform A with a short solution x (s.t. Ax = 0):
1
Choose Ā ← Zqn×m̄ and x̄ ← {0, 1}
m̄
for (say) m̄ ≥ 2n lg q.
5 / 17
A “Key” Trick
I Generate uniform A with a short solution x (s.t. Ax = 0):
1
2
Choose Ā ← Zqn×m̄ and x̄ ← {0, 1}
Let A = [Ā | −Āx̄] and x =
[ x̄1 ].
m̄
for (say) m̄ ≥ 2n lg q.
(We just reduced −x̄ modulo L⊥ (Ā).)
5 / 17
A “Key” Trick
I Generate uniform A with a short solution x (s.t. Ax = 0):
1
2
Choose Ā ← Zqn×m̄ and x̄ ← {0, 1}
Let A = [Ā | −Āx̄] and x =
[ x̄1 ].
m̄
for (say) m̄ ≥ 2n lg q.
(We just reduced −x̄ modulo L⊥ (Ā).)
I For many short solutions, let A = [Ā | −ĀX̄] and X =
X̄
I
.
5 / 17
A “Key” Trick
I Generate uniform A with a short solution x (s.t. Ax = 0):
1
2
Choose Ā ← Zqn×m̄ and x̄ ← {0, 1}
Let A = [Ā | −Āx̄] and x =
[ x̄1 ].
m̄
for (say) m̄ ≥ 2n lg q.
(We just reduced −x̄ modulo L⊥ (Ā).)
I For many short solutions, let A = [Ā | −ĀX̄] and X =
X̄
I
.
m̄
I Nothing special about {0, 1} : enough entropy suffices (essentially).
5 / 17
A “Key” Trick
I Generate uniform A with a short solution x (s.t. Ax = 0):
1
2
Choose Ā ← Zqn×m̄ and x̄ ← {0, 1}
Let A = [Ā | −Āx̄] and x =
[ x̄1 ].
m̄
for (say) m̄ ≥ 2n lg q.
(We just reduced −x̄ modulo L⊥ (Ā).)
I For many short solutions, let A = [Ā | −ĀX̄] and X =
X̄
I
.
m̄
I Nothing special about {0, 1} : enough entropy suffices (essentially).
‘Leftover Hash’ Lemma
s
I Over choice of Ā and x̄, matrix A = [Ā | −Āx̄] ≈ uniform.
I Proof: family fĀ : {0, 1}m̄ → Znq is pairwise independent;
x̄ has sufficient (min-)entropy.
5 / 17
A “Key” Trick
I Generate uniform A with a short solution x (s.t. Ax = 0):
1
2
Choose Ā ← Zqn×m̄ and x̄ ← {0, 1}
Let A = [Ā | −Āx̄] and x =
[ x̄1 ].
m̄
for (say) m̄ ≥ 2n lg q.
(We just reduced −x̄ modulo L⊥ (Ā).)
I For many short solutions, let A = [Ā | −ĀX̄] and X =
X̄
I
.
m̄
I Nothing special about {0, 1} : enough entropy suffices (essentially).
‘Leftover Hash’ Lemma
s
I Over choice of Ā and x̄, matrix A = [Ā | −Āx̄] ≈ uniform.
I Proof: family fĀ : {0, 1}m̄ → Znq is pairwise independent;
x̄ has sufficient (min-)entropy.
Dirty Little Secret
I This trick — reducing a short vector modulo a lattice — is the
only one-way function used in all of lattice crypto!
5 / 17
Another Hard Problem: Learning With Errors
[Regev’05]
I As before, dimension n and modulus q ≥ 2
6 / 17
Another Hard Problem: Learning With Errors
[Regev’05]
I As before, dimension n and modulus q ≥ 2
I Search: find s ∈ Znq given ‘noisy random inner products’
a1 ← Znq , b1 = hs , a1 i + e1
a2 ← Znq , b2 = hs , a2 i + e2
..
.
6 / 17
Another Hard Problem: Learning With Errors
[Regev’05]
I As before, dimension n and modulus q ≥ 2, error rate α 1
I Search: find s ∈ Znq given ‘noisy random inner products’
a1 ← Znq , b1 = hs , a1 i + e1
a2 ← Znq , b2 = hs , a2 i + e2
..
.
Errors ei ← χ = Gaussian over Z, width αq.
αq >
√
n
6 / 17
Another Hard Problem: Learning With Errors
[Regev’05]
I As before, dimension n and modulus q ≥ 2, error rate α 1
I Search: find s ∈ Znq given ‘noisy random inner products’
|
|
A = a1 · · · am , bt = st A + et
|
|
Errors ei ← χ = Gaussian over Z, width αq.
αq >
√
n
6 / 17
Another Hard Problem: Learning With Errors
[Regev’05]
I As before, dimension n and modulus q ≥ 2, error rate α 1
I Search: find s ∈ Znq given ‘noisy random inner products’
|
|
A = a1 · · · am , bt = st A + et
|
|
Errors ei ← χ = Gaussian over Z, width αq.
αq >
√
n
I Decision: distinguish (A, bt = st A + et ) from uniform (A, bt ).
6 / 17
Another Hard Problem: Learning With Errors
[Regev’05]
I As before, dimension n and modulus q ≥ 2, error rate α 1
I Search: find s ∈ Znq given ‘noisy random inner products’
|
|
A = a1 · · · am , bt = st A + et
|
|
Errors ei ← χ = Gaussian over Z, width αq.
αq >
√
n
I Decision: distinguish (A, bt = st A + et ) from uniform (A, bt ).
I Foundation for a huge amount of crypto
[R’05,PW’08,GPV’08,PVW’08,CDMW’08,AGV’09,ACPS’09,CHKP’10,ABB’10a,ABB’10b,GKV’10,BV’11,BGV’12,. . . ]
6 / 17
LWE as a Lattice Problem
· · · · A · · · · ∈ Zn×m
q
|
{z
m
,
bt = st A + et
vs.
b ← Zm
q
}
I Lattice interpretation:
L(A) = {zt ≡ st A mod q}
b
b
Finding s, e: BDD on L(A)!
Distinguishing b vs. b: decision-BDD.
7 / 17
LWE as a Lattice Problem
· · · · A · · · · ∈ Zn×m
q
|
{z
m
,
bt = st A + et
vs.
b ← Zm
q
}
I Lattice interpretation:
L(A) = {zt ≡ st A mod q}
b
b
Finding s, e: BDD on L(A)!
Distinguishing b vs. b: decision-BDD.
I Also enjoys worst-case hardness [R’05,P’09]
. . . but results are more subtle.
7 / 17
Overview of LWE Hardness
GapSVP,
SIVP
≤
quantum
[R’05]
search-LWE ≤ decision-LWE ≤ crypto
≤
GapSVP
[BFKL’94,R’05,
P’09,. . . ]
classical
n
(q ≥ 2 )
[P’09]
I Dim-modulus tradeoff [BLPRS’13]: e.g., n, q = 2n for n2 , q = poly(n).
√
I Why error αq > n?
F
Required by worst-case hardness proofs
F
There’s an exp((αq)2 )-time attack! [AG’11]
8 / 17
SIS versus LWE
SIS
LWE
Az = 0, ‘short’ z 6= 0
(A, bt = st A + et ) vs. (A, bt )
9 / 17
SIS versus LWE
SIS
LWE
Az = 0, ‘short’ z 6= 0
(A, bt = st A + et ) vs. (A, bt )
I ‘Computational’ (search)
problem a la factoring, CDH
9 / 17
SIS versus LWE
SIS
LWE
Az = 0, ‘short’ z 6= 0
(A, bt = st A + et ) vs. (A, bt )
I ‘Computational’ (search)
problem a la factoring, CDH
I ‘Decisional’ problem a la QR,
DCR, DDH
9 / 17
SIS versus LWE
SIS
LWE
Az = 0, ‘short’ z 6= 0
(A, bt = st A + et ) vs. (A, bt )
I ‘Computational’ (search)
problem a la factoring, CDH
I ‘Decisional’ problem a la QR,
DCR, DDH
I Many valid solutions z
9 / 17
SIS versus LWE
SIS
LWE
Az = 0, ‘short’ z 6= 0
(A, bt = st A + et ) vs. (A, bt )
I ‘Computational’ (search)
problem a la factoring, CDH
I ‘Decisional’ problem a la QR,
DCR, DDH
I Many valid solutions z
I Unique solution s, e
9 / 17
SIS versus LWE
SIS
LWE
Az = 0, ‘short’ z 6= 0
(A, bt = st A + et ) vs. (A, bt )
I ‘Computational’ (search)
problem a la factoring, CDH
I ‘Decisional’ problem a la QR,
DCR, DDH
I Many valid solutions z
I Unique solution s, e
I LWE ≤ SIS: if Az = 0, then
bt z = et z is small, but
bt z is ‘well-spread’
9 / 17
SIS versus LWE
SIS
LWE
Az = 0, ‘short’ z 6= 0
(A, bt = st A + et ) vs. (A, bt )
I ‘Computational’ (search)
problem a la factoring, CDH
I ‘Decisional’ problem a la QR,
DCR, DDH
I Many valid solutions z
I Unique solution s, e
I LWE ≤ SIS: if Az = 0, then
bt z = et z is small, but
bt z is ‘well-spread’
I SIS ≤ LWE quantumly [R’05]
9 / 17
SIS versus LWE
SIS
LWE
Az = 0, ‘short’ z 6= 0
(A, bt = st A + et ) vs. (A, bt )
I ‘Computational’ (search)
problem a la factoring, CDH
I ‘Decisional’ problem a la QR,
DCR, DDH
I Many valid solutions z
I Unique solution s, e
I LWE ≤ SIS: if Az = 0, then
bt z = et z is small, but
bt z is ‘well-spread’
I SIS ≤ LWE quantumly [R’05]
I Applications: OWF / CRHF,
signatures, ID schemes
9 / 17
SIS versus LWE
SIS
LWE
Az = 0, ‘short’ z 6= 0
(A, bt = st A + et ) vs. (A, bt )
I ‘Computational’ (search)
problem a la factoring, CDH
I ‘Decisional’ problem a la QR,
DCR, DDH
I Many valid solutions z
I Unique solution s, e
I LWE ≤ SIS: if Az = 0, then
bt z = et z is small, but
bt z is ‘well-spread’
I SIS ≤ LWE quantumly [R’05]
I Applications: OWF / CRHF,
signatures, ID schemes
‘minicrypt’
9 / 17
SIS versus LWE
SIS
LWE
Az = 0, ‘short’ z 6= 0
(A, bt = st A + et ) vs. (A, bt )
I ‘Computational’ (search)
problem a la factoring, CDH
I ‘Decisional’ problem a la QR,
DCR, DDH
I Many valid solutions z
I Unique solution s, e
I LWE ≤ SIS: if Az = 0, then
bt z = et z is small, but
bt z is ‘well-spread’
I SIS ≤ LWE quantumly [R’05]
I Applications: OWF / CRHF,
signatures, ID schemes
I Applications: PKE, OT,
ID-based encryption, FHE, . . .
‘minicrypt’
9 / 17
SIS versus LWE
SIS
LWE
Az = 0, ‘short’ z 6= 0
(A, bt = st A + et ) vs. (A, bt )
I ‘Computational’ (search)
problem a la factoring, CDH
I ‘Decisional’ problem a la QR,
DCR, DDH
I Many valid solutions z
I Unique solution s, e
I LWE ≤ SIS: if Az = 0, then
bt z = et z is small, but
bt z is ‘well-spread’
I SIS ≤ LWE quantumly [R’05]
I Applications: OWF / CRHF,
signatures, ID schemes
I Applications: PKE, OT,
ID-based encryption, FHE, . . .
‘minicrypt’
‘CRYPTOMANIA’
9 / 17
SIS versus LWE
SIS
LWE
Az = 0, ‘short’ z 6= 0
(A, bt = st A + et ) vs. (A, bt )
Average-case SVP:
Average-case BDD:
L⊥ (A) = {z ∈ Zm : Az = 0}
L(A) = {zt ≡ st A mod q}
(0, q)
(q, 0)
O
10 / 17
Warm-Up: Simple Properties of LWE
1
Check a candidate solution s0 ∈ Znq :
test if all b − hs0 , ai small.
If s0 6= s, then b − hs0 , ai = hs − s0 , ai + e is ‘well-spread’ in Zq .
2
Shift the secret by any t ∈ Znq : given (a, b = hs, ai + e), output
a , b0 = b + ht, ai
= hs + t, ai + e.
Random t’s (with fresh samples) ⇒ random self-reduction.
Lets us amplify success probabilities (both search & decision):
non-negl on uniform s ← Znq
3
=⇒
≈ 1 on any s ∈ Znq
Multiple secrets: (a, b1 ≈ hs1 , ai, . . . , bt ≈ hst , ai) vs. (a, b1 , . . . , bt ).
Simple hybrid argument, since a’s are public.
11 / 17
Warm-Up: Simple Properties of LWE
1
Check a candidate solution s0 ∈ Znq :
test if all b − hs0 , ai small.
If s0 6= s, then b − hs0 , ai = hs − s0 , ai + e is ‘well-spread’ in Zq .
2
Shift the secret by any t ∈ Znq : given (a, b = hs, ai + e), output
a , b0 = b + ht, ai
= hs + t, ai + e.
Random t’s (with fresh samples) ⇒ random self-reduction.
Lets us amplify success probabilities (both search & decision):
non-negl on uniform s ← Znq
3
=⇒
≈ 1 on any s ∈ Znq
Multiple secrets: (a, b1 ≈ hs1 , ai, . . . , bt ≈ hst , ai) vs. (a, b1 , . . . , bt ).
Simple hybrid argument, since a’s are public.
11 / 17
Warm-Up: Simple Properties of LWE
1
Check a candidate solution s0 ∈ Znq :
test if all b − hs0 , ai small.
If s0 6= s, then b − hs0 , ai = hs − s0 , ai + e is ‘well-spread’ in Zq .
2
Shift the secret by any t ∈ Znq : given (a, b = hs, ai + e), output
a , b0 = b + ht, ai
= hs + t, ai + e.
Random t’s (with fresh samples) ⇒ random self-reduction.
Lets us amplify success probabilities (both search & decision):
non-negl on uniform s ← Znq
3
=⇒
≈ 1 on any s ∈ Znq
Multiple secrets: (a, b1 ≈ hs1 , ai, . . . , bt ≈ hst , ai) vs. (a, b1 , . . . , bt ).
Simple hybrid argument, since a’s are public.
11 / 17
Warm-Up: Simple Properties of LWE
1
Check a candidate solution s0 ∈ Znq :
test if all b − hs0 , ai small.
If s0 6= s, then b − hs0 , ai = hs − s0 , ai + e is ‘well-spread’ in Zq .
2
Shift the secret by any t ∈ Znq : given (a, b = hs, ai + e), output
a , b0 = b + ht, ai
= hs + t, ai + e.
Random t’s (with fresh samples) ⇒ random self-reduction.
Lets us amplify success probabilities (both search & decision):
non-negl on uniform s ← Znq
3
=⇒
≈ 1 on any s ∈ Znq
Multiple secrets: (a, b1 ≈ hs1 , ai, . . . , bt ≈ hst , ai) vs. (a, b1 , . . . , bt ).
Simple hybrid argument, since a’s are public.
11 / 17
Warm-Up: Simple Properties of LWE
1
Check a candidate solution s0 ∈ Znq :
test if all b − hs0 , ai small.
If s0 6= s, then b − hs0 , ai = hs − s0 , ai + e is ‘well-spread’ in Zq .
2
Shift the secret by any t ∈ Znq : given (a, b = hs, ai + e), output
a , b0 = b + ht, ai
= hs + t, ai + e.
Random t’s (with fresh samples) ⇒ random self-reduction.
Lets us amplify success probabilities (both search & decision):
non-negl on uniform s ← Znq
3
=⇒
≈ 1 on any s ∈ Znq
Multiple secrets: (a, b1 ≈ hs1 , ai, . . . , bt ≈ hst , ai) vs. (a, b1 , . . . , bt ).
Simple hybrid argument, since a’s are public.
11 / 17
Warm-Up: Simple Properties of LWE
1
Check a candidate solution s0 ∈ Znq :
test if all b − hs0 , ai small.
If s0 6= s, then b − hs0 , ai = hs − s0 , ai + e is ‘well-spread’ in Zq .
2
Shift the secret by any t ∈ Znq : given (a, b = hs, ai + e), output
a , b0 = b + ht, ai
= hs + t, ai + e.
Random t’s (with fresh samples) ⇒ random self-reduction.
Lets us amplify success probabilities (both search & decision):
non-negl on uniform s ← Znq
3
=⇒
≈ 1 on any s ∈ Znq
Multiple secrets: (a, b1 ≈ hs1 , ai, . . . , bt ≈ hst , ai) vs. (a, b1 , . . . , bt ).
Simple hybrid argument, since a’s are public.
11 / 17
Warm-Up: Simple Properties of LWE
1
Check a candidate solution s0 ∈ Znq :
test if all b − hs0 , ai small.
If s0 6= s, then b − hs0 , ai = hs − s0 , ai + e is ‘well-spread’ in Zq .
2
Shift the secret by any t ∈ Znq : given (a, b = hs, ai + e), output
a , b0 = b + ht, ai
= hs + t, ai + e.
Random t’s (with fresh samples) ⇒ random self-reduction.
Lets us amplify success probabilities (both search & decision):
non-negl on uniform s ← Znq
3
=⇒
≈ 1 on any s ∈ Znq
Multiple secrets: (a, b1 ≈ hs1 , ai, . . . , bt ≈ hst , ai) vs. (a, b1 , . . . , bt ).
Simple hybrid argument, since a’s are public.
11 / 17
Search/Decision Equivalence
[BFKL’94,R’05]
I Suppose D solves decision-LWE: it perfectly∗ distinguishes between
pairs (a, b = hs, ai + e) and (a, b).
12 / 17
Search/Decision Equivalence
[BFKL’94,R’05]
I Suppose D solves decision-LWE: it perfectly∗ distinguishes between
pairs (a, b = hs, ai + e) and (a, b).
We want to solve search-LWE: given pairs (a, b), find s.
12 / 17
Search/Decision Equivalence
[BFKL’94,R’05]
I Suppose D solves decision-LWE: it perfectly∗ distinguishes between
pairs (a, b = hs, ai + e) and (a, b).
We want to solve search-LWE: given pairs (a, b), find s.
?
I If q = poly(n) , to find s1 ∈ Zq it suffices to test whether s1 =
0,
because we can shift s1 by 0, 1, . . . , q − 1. Same for s2 , s3 , . . . , sn .
12 / 17
Search/Decision Equivalence
[BFKL’94,R’05]
I Suppose D solves decision-LWE: it perfectly∗ distinguishes between
pairs (a, b = hs, ai + e) and (a, b).
We want to solve search-LWE: given pairs (a, b), find s.
?
I If q = poly(n) , to find s1 ∈ Zq it suffices to test whether s1 =
0,
because we can shift s1 by 0, 1, . . . , q − 1. Same for s2 , s3 , . . . , sn .
The test: for each (a, b), choose fresh r ← Zq . Invoke D on pairs
(a0 = a − (r, 0, . . . , 0) , b).
12 / 17
Search/Decision Equivalence
[BFKL’94,R’05]
I Suppose D solves decision-LWE: it perfectly∗ distinguishes between
pairs (a, b = hs, ai + e) and (a, b).
We want to solve search-LWE: given pairs (a, b), find s.
?
I If q = poly(n) , to find s1 ∈ Zq it suffices to test whether s1 =
0,
because we can shift s1 by 0, 1, . . . , q − 1. Same for s2 , s3 , . . . , sn .
The test: for each (a, b), choose fresh r ← Zq . Invoke D on pairs
(a0 = a − (r, 0, . . . , 0) , b).
I Notice: b = hs, a0 i + s1 · r + e.
12 / 17
Search/Decision Equivalence
[BFKL’94,R’05]
I Suppose D solves decision-LWE: it perfectly∗ distinguishes between
pairs (a, b = hs, ai + e) and (a, b).
We want to solve search-LWE: given pairs (a, b), find s.
?
I If q = poly(n) , to find s1 ∈ Zq it suffices to test whether s1 =
0,
because we can shift s1 by 0, 1, . . . , q − 1. Same for s2 , s3 , . . . , sn .
The test: for each (a, b), choose fresh r ← Zq . Invoke D on pairs
(a0 = a − (r, 0, . . . , 0) , b).
I Notice: b = hs, a0 i + s1 · r + e.
F
If s1 = 0, then b = hs, a0 i + e ⇒ D accepts.
12 / 17
Search/Decision Equivalence
[BFKL’94,R’05]
I Suppose D solves decision-LWE: it perfectly∗ distinguishes between
pairs (a, b = hs, ai + e) and (a, b).
We want to solve search-LWE: given pairs (a, b), find s.
?
I If q = poly(n) , to find s1 ∈ Zq it suffices to test whether s1 =
0,
because we can shift s1 by 0, 1, . . . , q − 1. Same for s2 , s3 , . . . , sn .
The test: for each (a, b), choose fresh r ← Zq . Invoke D on pairs
(a0 = a − (r, 0, . . . , 0) , b).
I Notice: b = hs, a0 i + s1 · r + e.
F
If s1 = 0, then b = hs, a0 i + e ⇒ D accepts.
F
If s1 6= 0 and q prime then b = uniform ⇒ D rejects.
12 / 17
Search/Decision Equivalence
[BFKL’94,R’05]
I Suppose D solves decision-LWE: it perfectly∗ distinguishes between
pairs (a, b = hs, ai + e) and (a, b).
We want to solve search-LWE: given pairs (a, b), find s.
?
I If q = poly(n) , to find s1 ∈ Zq it suffices to test whether s1 =
0,
because we can shift s1 by 0, 1, . . . , q − 1. Same for s2 , s3 , . . . , sn .
The test: for each (a, b), choose fresh r ← Zq . Invoke D on pairs
(a0 = a − (r, 0, . . . , 0) , b).
I Notice: b = hs, a0 i + s1 · r + e.
F
If s1 = 0, then b = hs, a0 i + e ⇒ D accepts.
F
If s1 6= 0 and q prime then b = uniform ⇒ D rejects.
I (Don’t actually need prime q = poly(n) .)
[P’09,ACPS’09,MM’11,MP’12,BGV’12]
12 / 17
Decision-LWE with ‘Short’ Secret
Theorem
[M’01,ACPS’09]
I LWE is no easier if the secret is drawn from the error distribution χn .
13 / 17
Decision-LWE with ‘Short’ Secret
Theorem
[M’01,ACPS’09]
I LWE is no easier if the secret is drawn from the error distribution χn .
(This is called the “Hermite normal form” of LWE.)
13 / 17
Decision-LWE with ‘Short’ Secret
Theorem
[M’01,ACPS’09]
I LWE is no easier if the secret is drawn from the error distribution χn .
(This is called the “Hermite normal form” of LWE.)
I Intuition: finding e ⇔ finding s: take bt − et = st A, solve for s.
13 / 17
Decision-LWE with ‘Short’ Secret
Theorem
[M’01,ACPS’09]
I LWE is no easier if the secret is drawn from the error distribution χn .
(This is called the “Hermite normal form” of LWE.)
I Intuition: finding e ⇔ finding s: take bt − et = st A, solve for s.
Transformation from secret s ∈ Znq to secret ē ← χn :
13 / 17
Decision-LWE with ‘Short’ Secret
Theorem
[M’01,ACPS’09]
I LWE is no easier if the secret is drawn from the error distribution χn .
(This is called the “Hermite normal form” of LWE.)
I Intuition: finding e ⇔ finding s: take bt − et = st A, solve for s.
Transformation from secret s ∈ Znq to secret ē ← χn :
1
t
Draw samples to get (Ā, b̄ = st Ā + ēt ) for square, invertible Ā.
13 / 17
Decision-LWE with ‘Short’ Secret
Theorem
[M’01,ACPS’09]
I LWE is no easier if the secret is drawn from the error distribution χn .
(This is called the “Hermite normal form” of LWE.)
I Intuition: finding e ⇔ finding s: take bt − et = st A, solve for s.
Transformation from secret s ∈ Znq to secret ē ← χn :
t
1
Draw samples to get (Ā, b̄ = st Ā + ēt ) for square, invertible Ā.
2
Transform each additional sample (a, b = hs, ai + e) to
a0 = −Ā
−1
a
,
b0 = b + hb̄, a0 i
13 / 17
Decision-LWE with ‘Short’ Secret
Theorem
[M’01,ACPS’09]
I LWE is no easier if the secret is drawn from the error distribution χn .
(This is called the “Hermite normal form” of LWE.)
I Intuition: finding e ⇔ finding s: take bt − et = st A, solve for s.
Transformation from secret s ∈ Znq to secret ē ← χn :
t
1
Draw samples to get (Ā, b̄ = st Ā + ēt ) for square, invertible Ā.
2
Transform each additional sample (a, b = hs, ai + e) to
a0 = −Ā
−1
a
,
b0 = b + hb̄, a0 i
= hē, a0 i + e.
13 / 17
Decision-LWE with ‘Short’ Secret
Theorem
[M’01,ACPS’09]
I LWE is no easier if the secret is drawn from the error distribution χn .
(This is called the “Hermite normal form” of LWE.)
I Intuition: finding e ⇔ finding s: take bt − et = st A, solve for s.
Transformation from secret s ∈ Znq to secret ē ← χn :
t
1
Draw samples to get (Ā, b̄ = st Ā + ēt ) for square, invertible Ā.
2
Transform each additional sample (a, b = hs, ai + e) to
a0 = −Ā
−1
a
,
b0 = b + hb̄, a0 i
= hē, a0 i + e.
I This maps (a, b) to (a0 , b0 ), so it applies to decision-LWE too.
13 / 17
Public-Key Cryptosystem using LWE
s ← Znq
(Images courtesy xkcd.org)
[Regev’05]
A ← Zn×m
q
14 / 17
Public-Key Cryptosystem using LWE
s ← Znq
[Regev’05]
A ← Zn×m
q
bt = st A + et
(public key)
(Images courtesy xkcd.org)
14 / 17
Public-Key Cryptosystem using LWE
s ← Znq
A ← Zn×m
q
[Regev’05]
x ← {0, 1}m
bt = st A + et
(public key)
u = Ax
(ciphertext ‘preamble’)
(Images courtesy xkcd.org)
14 / 17
Public-Key Cryptosystem using LWE
s ← Znq
[Regev’05]
x ← {0, 1}m
A ← Zn×m
q
bt = st A + et
(public key)
u = Ax
(ciphertext ‘preamble’)
u0 = bt x + bit ·
q
2
(‘payload’)
(Images courtesy xkcd.org)
14 / 17
Public-Key Cryptosystem using LWE
s ← Znq
[Regev’05]
x ← {0, 1}m
A ← Zn×m
q
bt = st A + et
(public key)
u = Ax
(ciphertext ‘preamble’)
u0 − st u ≈
bit · 2q
(Images courtesy xkcd.org)
u0 = bt x + bit ·
q
2
(‘payload’)
14 / 17
Public-Key Cryptosystem using LWE
s ← Znq
[Regev’05]
x ← {0, 1}m
A ← Zn×m
q
bt = st A + et
(public key)
u = Ax
(ciphertext ‘preamble’)
u0 − st u ≈
bit · 2q
u0 = bt x + bit ·
q
2
(‘payload’)
(A, bt ), (u, u0 )
(Images courtesy xkcd.org)
14 / 17
Public-Key Cryptosystem using LWE
s ← Znq
[Regev’05]
x ← {0, 1}m
A ← Zn×m
q
bt = st A + et
(public key)
u = Ax
(ciphertext ‘preamble’)
u0 − st u ≈
bit · 2q
u0 = bt x + bit ·
q
2
(‘payload’)
(A, bt ), (u, u0 )
by LWE
(Images courtesy xkcd.org)
14 / 17
Public-Key Cryptosystem using LWE
s ← Znq
[Regev’05]
x ← {0, 1}m
A ← Zn×m
q
bt = st A + et
(public key)
u = Ax
(ciphertext ‘preamble’)
u0 − st u ≈
bit · 2q
u0 = bt x + bit ·
q
2
(‘payload’)
(A, bt ), (u, u0 )
by LWE and
by LHL when
m ≥ n log q
(Images courtesy xkcd.org)
14 / 17
“Dual” Cryptosystem
x ← {0, 1}m
[GPV’08]
A ← Zn×m
q
15 / 17
“Dual” Cryptosystem
x ← {0, 1}m
[GPV’08]
A ← Zn×m
q
u = Ax
(public key, uniform when m ≥ n log q)
15 / 17
“Dual” Cryptosystem
x ← {0, 1}m
[GPV’08]
A ← Zn×m
q
s ← Znq
u = Ax
(public key, uniform when m ≥ n log q)
bt = st A + et
(ciphertext ‘preamble’)
15 / 17
“Dual” Cryptosystem
[GPV’08]
x ← {0, 1}m
s ← Znq
A ← Zn×m
q
u = Ax
(public key, uniform when m ≥ n log q)
bt = st A + et
(ciphertext ‘preamble’)
b0
= st u + e0 + bit ·
q
2
(‘payload’)
15 / 17
“Dual” Cryptosystem
[GPV’08]
x ← {0, 1}m
s ← Znq
A ← Zn×m
q
u = Ax
(public key, uniform when m ≥ n log q)
bt = st A + et
(ciphertext ‘preamble’)
b0 − bt x ≈
bit · 2q
b0
= st u + e0 + bit ·
q
2
(‘payload’)
15 / 17
“Dual” Cryptosystem
[GPV’08]
x ← {0, 1}m
s ← Znq
A ← Zn×m
q
u = Ax
(public key, uniform when m ≥ n log q)
bt = st A + et
(ciphertext ‘preamble’)
b0 − bt x ≈
bit · 2q
b0
= st u + e0 + bit ·
q
2
(‘payload’)
(A, u), (b, b0 )
15 / 17
“Dual” Cryptosystem
[GPV’08]
x ← {0, 1}m
s ← Znq
A ← Zn×m
q
u = Ax
(public key, uniform when m ≥ n log q)
bt = st A + et
(ciphertext ‘preamble’)
b0 − bt x ≈
bit · 2q
b0
= st u + e0 + bit ·
q
2
(‘payload’)
(A, u), (b, b0 )
by LWE
15 / 17
Most Efficient Cryptosystem
s ← χn
[A’03,LPS’10,LP’11]
A ← Zn×n
q
16 / 17
Most Efficient Cryptosystem
s ← χn
[A’03,LPS’10,LP’11]
A ← Zn×n
q
ut = st A + et
(public key)
16 / 17
Most Efficient Cryptosystem
s ← χn
[A’03,LPS’10,LP’11]
A ← Zn×n
q
r ← χn
ut = st A + et
(public key)
b = Ar + x
(ciphertext ‘preamble’)
16 / 17
Most Efficient Cryptosystem
s ← χn
[A’03,LPS’10,LP’11]
r ← χn
A ← Zn×n
q
ut = st A + et
(public key)
b = Ar + x
(ciphertext ‘preamble’)
b0 = ut r + x0 + bit ·
q
2
(‘payload’)
16 / 17
Most Efficient Cryptosystem
s ← χn
[A’03,LPS’10,LP’11]
r ← χn
A ← Zn×n
q
ut = st A + et
(public key)
b = Ar + x
(ciphertext ‘preamble’)
b0 −st b
≈
bit· 2q
b0 = ut r + x0 + bit ·
q
2
(‘payload’)
16 / 17
Most Efficient Cryptosystem
s ← χn
[A’03,LPS’10,LP’11]
r ← χn
A ← Zn×n
q
ut = st A + et
(public key)
b = Ar + x
(ciphertext ‘preamble’)
b0 −st b
≈
bit· 2q
b0 = ut r + x0 + bit ·
q
2
(‘payload’)
(A, u, b, b0 )
16 / 17
Most Efficient Cryptosystem
s ← χn
[A’03,LPS’10,LP’11]
r ← χn
A ← Zn×n
q
ut = st A + et
(public key)
b = Ar + x
(ciphertext ‘preamble’)
b0 −st b
≈
bit· 2q
b0 = ut r + x0 + bit ·
q
2
(‘payload’)
(A, u, b, b0 )
by LWE (HNF)
16 / 17
Most Efficient Cryptosystem
s ← χn
[A’03,LPS’10,LP’11]
r ← χn
A ← Zn×n
q
ut = st A + et
(public key)
b = Ar + x
(ciphertext ‘preamble’)
b0 −st b
≈
bit· 2q
b0 = ut r + x0 + bit ·
q
2
(‘payload’)
(A, u, b, b0 )
by LWE (HNF)
by LWE (HNF)
16 / 17
Wrapping Up
I Now you know all the basic techniques for working with SIS and LWE.
I We’ve covered a lot: do the exercises to reinforce your understanding!
I Tomorrow: more advanced applications, using “strong trapdoors.”
17 / 17