(C) Copyright 1991-1993
E N C R Y P T - I T
MaeDae Enterprises
F O R
W I N D O W S
Version 2.xx
Reference Manual
Encryption, decryption, and cryptanalysis program.
Supporting the secure Data Encryption Standard (DES).
Context sensitive help and on-line manual make it easy!
Encrypt-It for Windows is user supported software (Shareware).
If you use it past the initial 15 day evaluation period, you are
required to register it. No exceptions!
Registered Users: Your serial number can be found on the back of
your manual, the distribution disk, or on the registration card.
Encrypt-It for Windows
"Encryption/Decryption/Cryptanalysis -- Fast, Safe, and Easy to
Use"
is published by
MaeDae Enterprises
5430 Murr Road
Peyton, CO 80831-7402 U.S.A.
(719) 683-3860
Published and printed in the United States of America.
Copyright 1991 MaeDae Enterprises as a licensed, unpublished,
proprietary work. All international rights reserved.
Page 1
(C) Copyright 1991-1993
MaeDae Enterprises
The printed Reference Manual and associated registered software
may not be copied, resold, reproduced, disclosed, archived,
transmitted, or transferred in any form, electronic or otherwise,
without the express written permission of MaeDae Enterprises.
You may freely distribute the Shareware version.
REGISTERED USERS: (those who paid and received a serial number)
MaeDae Enterprises hereby grants a "book" license to the original
individual (even if purchased by a company) user of this copy of
Encrypt-It. You may use the program on your computer and make
one backup for storage as long as there is no possibility of use
or residence on more than one machine at any time. Just like two
people cannot read the same book in different locations at the
same time. Every registered copy of Encrypt-It has a unique,
embedded serial number for traceabililty. You may not sell or
give copies of the registered program or printed documentation to
anyone. No exceptions.
Pricing, specifications, and conditions are subject to change
without notice.
Send all registrations and inquiries for site (multiple CPU or
network) licensing to MaeDae Enterprises at the address on the
previous page.
Disclaimer:
MaeDae Enterprises makes NO claims AND offers NO warranties of
any sort with Encrypt-It. MaeDae Enterprises assumes NO
responsibility for any damage resulting from the apparent or
actual use of Encrypt-It (mental or physical). The program
provided is not guaranteed as to merchantability or fitness for
its ultimate use. The user accepts all responsibility for use
and may not resell the program.
IBM PC/XT/AT are registered trademarks of the International
Business Machines Corporation.
Encrypt-It is a trademark of MaeDae Enterprises.
trademarks belong to their respective owners.
Other
Page 2
(C) Copyright 1991-1993
MaeDae Enterprises
PREFACE
ABOUT THIS MANUAL
You will notice that this manual is concise. This is intentional
as we strived to make Encrypt-It the easiest program of its type
to use. We opted to provide an extensive built-in user help
system. Feel free to use this reference manual to install and
get acquainted with the program.
For many of you, this may be your first exposure to Shareware.
To help eliminate possible confusion, we included a short
description of the Shareware marketing concept, explaining what
it is and why it relies on YOU for its survival.
What is Shareware? Shareware is not a kind of software. It is a
revolutionary method of marketing Commercial software. Our
software is Commercial software that we are allowing you to
examine for 15 days before you make the purchase decision. With
traditional marketing methods, you have to purchase Commercial
software from a computer store or through mail order businesses,
then try it out, and hope it does what you want. Shareware
allows you to "try before you buy!"
We rely upon you, the customer, to examine our software. If you
find it useful, please register. Your support is needed for us
to continue to improve our products.
Enough of this verbage. The real fun and learning begin when you
use the program. So, enjoy!
With warmest regards,
The gang at MaeDae Enterprises.
Page 3
(C) Copyright 1991-1993
MaeDae Enterprises
Table of Contents
=================
Page
====
Description
============
5.
What is the Data Encryption Standard (DES)?
5.
What is Encrypt-It?
6.
Hardware Requirements
7.
Installation - the "README.DOC" file.
An overview of its features.
7.
Installation Notes
8.
Getting Started
9.
Tutorial
10.
Additional Features
11.
Troubleshooting
12.
Basic Definitions
13.
Cryptographic Tecnniques
14.
Encrypted Ramblings
Page 4
(C) Copyright 1991-1993
MaeDae Enterprises
WHAT IS THE DATA ENCRYPTION STANDARD (DES)?
===========================================
Most encryption schemes are kept secret. One exception is the
Data Encryption Standard (DES), which was issued by the U.S.
National Bureau of Standards. Even the National Security Agency
(NSA) was intimately involved in the development and acceptance
testing of the algorithm.
But, how does it work? DES performs its encryption "magic" by
working on a block of 64 bits of your data using a 64 bit key
(we generate the 64 bit key from the key you supply). Basically,
DES is a substitution cipher. We know this sounds very
technical,
but don't worry, we have hidden all the complexity of DES behind
an
extremely easy to use interface. Our extensive built-in user
help
system makes protecting your data a simple task.
Why did we choose to implement DES? We chose DES because it is a
standard. Its ability to protect your data is well documented.
Our goal is to provide you the best possible software tool for
the protection of your data. We use multiple layers of
encryption, with DES as the final layer of protection for your
data. Because of this approach, we feel your data is protected
far better than using DES by itself.
WHAT IS ENCRYPT-IT?
===================
Encrypt-It is a powerful encryption/decryption package for
Windows
3.x that allows you to:
1. Encrypt any file using Data Encryption Standard encryption,
2. Decrypt the file using a confidental key,
3. Perform encryption and decryption on entire groups of files
in a batch mode,
4. Obtain file statistics (frequency/distribution, mode, mean,
median, and more) to determine how well the file is encrypted
(also to look at other encrypted files),
5. Erase files completely without leaving a trace.
support a government standard file wipe option.
6. And do it all without cryptic commands!
We even
Page 5
(C) Copyright 1991-1993
MaeDae Enterprises
HARDWARE REQUIREMENTS
=====================
1. IBM PC/XT/AT, IBM PS/2, or fully compatible computer capable
of running Windows 3.0 or later.
2.
At least one 5.25" or 3.5" floppy disk drive.
Two floppy
disk
drives or one floppy and a hard disk (300K free space minimum for
the full system) are strongly recommended.
INSTALLATION - README.DOC
=========================
For all installation information see the README.DOC on the main
distribution diskette. You can view the information on-line or
print it out on your printer. README.DOC is constantly updated
to contain the latest information.
P.S. The Shareware version of Encrypt-It is compelete. However,
it is a 15 day trial version. Also, additional product
information screens are added.
Feel free to share ONLY the Shareware version with friends and
potential users of Encrypt-It for 15 day trial/evaluation
purposes only. You may not use the Shareware version on other
machines in order to avoid purchasing additional copies of the
full program. You may not give away any copies or make more than
one copy of the fully operational program for other than archival
purposes. The full version of Encrypt-It has a unique serial
number embedded in each copy for traceability.
Page 6
(C) Copyright 1991-1993
MaeDae Enterprises
IMPORTANT INSTALLATION NOTES:
1. Diskette #1 contains many files in addition to EIW.EXE.
Please make sure these files are all installed in the same
directory when running the program.
2.
If Encrypt-It does not run properly:
A. Your machine may not be 100% IBM PC operating system
compatible or Windows may be installed incorrectly. This
is not always disastrous and a quick call to our phone
support staff may solve your problem.
B. You may have a slightly incompatible Windows video
driver. Usually, updating your driver or re-installing
Windows solves the problem.
C. If you have any memory resident programs or system
drivers, try running without them loaded on your computer.
On some computers, ANSI.SYS is suspect.
3. This manual is designed to give you a general overview and
familiarity with the program. More complete, up-to-date
information is available to you through the extensive built-in
user help (F1) system. When using the more advanced features of
the program, the help screens will guide you through the toughest
questions with ease. As Encrypt-It continues to add more
features, you can be sure that the built in help will give you
the guidance needed. This way everybody wins. We don't spend
money continually revising manuals and charging you higher
prices. You get what you want and deserve: accurate up-to-date
information. So fire up the computer, dig in, and welcome to
Encrypt-It!
Page 7
(C) Copyright 1991-1993
MaeDae Enterprises
GETTING STARTED
===============
After you run EIW.EXE using the file manager, the MAIN MENU will
appear on your screen.
The Main Menu options with descriptions are below.
*File: This menu option provides the basic File Select option
which allows you to select the file(s) you want to work with. It
also provides utilities like File Remove and File Statistics
which allow you to "look" at any file to see how well it is
encrypted.
Note:
You must first select a file before you can work with it.
Grayed menu options will then become dark text indicating you can
now use those options. After you encrypt, decrypt, or remove
files, you will notice the encrypt and decrypt options become
grayed. They are now disabled because you altered the contents of
the directory and it needs to be re-read before you can continue.
*Encrypt: Encode or hide the information within a file to make
it unreadable to anyone who doesn't have a special access code
called a key. Just like you can't unlock a lock without a key,
you can't look at an encrypted file without the key. You limit
the number of people who know the key, thereby limiting the
number of people who can access the intelligence within the file,
even if they have access to the file. A key is simply a
combination of letters and numbers. They may or may not have any
conventional meaning. For example, the letters xyz12345 could be
a key.
*Decrypt: Decryption is the opposite of encryption. You use the
same key initially used to encrypt the file and reverse the
process.
Please note we provide two methods of encryption and decryption.
The two methods are our lighter proprietary method and the Data
Encryption Standard (DES) encryption method. DES provides the
more powerful method, but is much slower. Choose the appropriate
method for the level of protection you require. Encrypt-It can't
retrieve the key used to encrypt the file. If you forget the key
you can also forget your file. This is the nature of data
protection. We have no way of helping you recover any lost data
due to a lost key! So be careful!
*ClearKey!: This option clears the encryption/decryption key
from memory. Use of this option is strongly recommended before
you leave Encrypt-It running un-attended. You must protect your
key to prevent someone else from gaining access to your data.
*Options: This menu item provides access to the options
available to you for encryption and decryption. You can set the
level of encryption (DES or proprietary), tell Encrypt-It what to
do with source files after encryption/decryption, etc.
Page 8
(C) Copyright 1991-1993
MaeDae Enterprises
You may choose any of the displayed options by holding down the
Alt key, then pressing the letter which is underlined on the menu
item or by selecting it with the mouse.
TUTORIAL (ENCRYPTING/DECRYPTING A FILE)
=======================================
Now let's do something simple to demonstrate how Encrypt-It
works.
Choose the File menu option. Then pick the Select option from
the menu. A File Select dialog box will appear allowing you to
select one or more files. Choose the first file by double
clicking the mouse on it. Did you notice that the Encrypt and
Decrypt main menu options are now enabled?
Pick the main menu Encrypt Option. A dialog box will appear
asking you several questions. The only one that has to be
answered in this tutorial is the key. Since this is the first
file we've encrypted, the Encryption Key won't contain anything.
The cursor should be on the line prompting you for a key. Choose
an easy to remember key and type it in. Now click on the OK box.
A file will be written in encrypted form using the default key
and default filename shown. The file to be encrypted is broken
into small blocks which can easily be read into your computer's
memory, then encrypted. You have just encrypted your first file.
Did you notice that the Encrypt/Decrypt Options grayed? You just
added a new file to the default directory invalidating the file
list stored in memory. It will stay grayed until you update the
in-memory list through the use of the File Select option.
*** Warning ***
Encrypt-It remembers the last key you used
until you exit the program, or 10 minutes have passed with no
activity on your computer! If you haven't cleared the key, and
it wasn't cleared automatically, it is still available for use by
Encrypt-It in the next operation. This makes it easier for you
but can lead to problems if you walk away from your computer with
Encrypt-It running. Another user could potentially find out the
last key you used by checking the encrypt or decrypt screens. We
recommend you NEVER leave your computer with Encrypt-It running.
Now lets decrypt the file you just encrypted. To decrypt a file
you just reverse the process. You first select the file you just
encrypted using the same steps as for encryption. Look for the
filename created when you encrypted the first file, then select
it with mouse. Now select Decrypt from the main menu and the
Decrypt Files dialog box opens. Use the same key as when you
encrypted the file. The output filename will be extracted from
the header of the encrypted file. You can allow Encrypt-It to
overwrite the original, unencrypted file or choose a new
filename. It's that simple.
Page 9
(C) Copyright 1991-1993
MaeDae Enterprises
ADDITIONAL FEATURES
===================
MULTIPLE FILE OPERATIONS
Use the File Select dialog box to tag multiple files. If
multiple files are tagged, Encrypt-It will prompt you for
confirmation and then work with the entire group of files at one
time. This works for Encrypt, Decrypt, File Remove, and File
Stats.
AUTO FILENAME GENERATION
Encrypt-It will automatically generate a unique destination
filename when you encrypt a file. You have the option to
override this feature for single file operations. We suggest a
tilde (~) as the first character of an encrypted file's
extension. Encrypt-It automatically generates an extension with
a ~ followed by two characters. Your directory is checked for
files and we generate 00-99 and AA-ZZ until we find a unique
unused filename. Most of the time the extension will be a .~00
for the first encrypted file, a .~01 for the second, etc. This
technique allows encrypting groups of files in a batch mode
without your manual input. Using this method we can generate
about 776 unique filenames by working with the file extension and
leaving the main portion of the filename unchanged.
AUTO KEY CLEARING
The key used to encrypt/decrypt files must be kept secret for
your data to remain protected. Encrypt-It has a built-in auto
key clearing feature. Any time you have a key typed in and leave
your computer for 10 minutes with Encrypt-It running unattended,
your key will be automatically cleared. For this feature to
work, you must be at the Encrypt-It main menu.
Page 10
(C) Copyright 1991-1993
MaeDae Enterprises
TROUBLESHOOTING
===============
If Encrypt-It will not run, you may have insufficient memory or
too many memory resident programs. Try running Encrypt-It with
no memory resident programs or allocate a larger swapfile under
Windows. See your Windows User's Guide for help with the
Swapfile program.
If Encrypt-It just stops running and you get an "Unrecoverable
Application Error," you may have incompatible hardware/software.
Try running Encrypt-It in the 386 Enhanced mode (if you have a
386 computer) to see if that corrects the problem.
Occasionally, certain memory resident TSR or "pop-up" programs
conflict with Encrypt-It. In general, there is no problem, but
there are many new programs being written without regard to the
system requirements of other programs that may be running at the
same time. Remove them from memory, and try again. If that
fails, try getting rid of device drivers in your CONFIG.SYS file.
ANSI.SYS is a prime suspect for some not-so-compatible computers.
MISCELLANEOUS
Encrypt-It works closely with your computer's hardware to gain
much of its speed. However, it never directly addresses the
hardware without using standard DOS calls. If you have any
memory resident software that modifies the way DOS works, then
Encrypt-It may not function properly. We strongly recommend that
you remove all memory resident software before running
Encrypt-It.
Page 11
(C) Copyright 1991-1993
MaeDae Enterprises
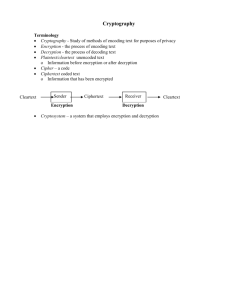
BASIC DEFINITIONS:
==================
The terms used in Encrypt-It may be a little confusing. They are
terms frequently used when discussing cryptography. We have
tried to pick a handful of the most important terms and define
them for you. They are:
Data Encryption Standard (DES) - The Data Encryption Standard was
issued by the U.S. National Bureau of Standards. The National
Security Agency (NSA) was intimately involved in the development
and acceptance testing of the algorithm. DES performs its
encryption by working on a block of 64 bits of your data using a
64 bit key (we generate the 64 bit key from the key you provide).
Basically, DES is a substitution cipher.
Cryptography -- The general study of hiding the meaning of
messages and the general techniques used for the hiding.
Cryptanalysis -- The solving or breaking of codes without any
knowledge of the key.
Cipher -- Any technique, method, or scheme (substitution,
transposition, and XOR) used to encrypt and decrypt text,
without regard to its linguistic structure.
Plaintext -- The unencrypted or totally decrypted readable text.
Ciphertext -- The unintelligible text, after encrypting it.
Encrypting -- The process of encoding/encrypting a plaintext file
to hide the intelligence.
Decrypting -- Decoding an encrypted/ciphertext file.
Key -- The text used to encrypt or decrypt a file. Sometimes
called a code word. Keys can be simple everyday words or very
complex combinations of characters that have no meaning. Some
electronic information services pick your password by combining
two regular words with a character between them. Examples keys:
abc1234, Never:Again, and alsdkfqiaef.
Page 12
(C) Copyright 1991-1993
MaeDae Enterprises
CRYPTOGRAPHIC TECHNIQUES
========================
Cryptographic techniques provide a very cost effective method of
protecting your important data. There are many computer
techniques available today for protecting your sensitive data.
Encrypt-It uses multiple layers of the following four encryption
methods:
1. Transposition - Changes the natural order of data so that a
different for the characters is used. It swaps characters within
a message to place them in a different order based on the
encryption key (text string) you use for encryption. For
example,
"THIS IS A TEST" could become "ISTHA SI TAEST". You will notice
that the characters are the same. However, their order is
totally mixed up or transposed. This process is repeated during
decryption to return the data back to its original state.
2. Substitution - Substitution is one of the simplest encryption
techniques. It creates a new order for the characters. For
example, the order of the text ABCDEFGHIJKLMNOPQRSTUVWXYZ could
be changed to the new order CADMYNZEOFPBQGSRHTUIVWJKXL. The
message "THIS IS A TEST" would then become "IEOU OU C IYUI".
This example is simplified for illustration purposes. When
substitution is used within a computer, all 256 possible
characters are used so that it is possible to use the technique
on different types of computer files.
3. Exclusive Or - This is a logic operation used by the computer
to manipulate the data at the bit level. For example, a
character which consists of 10011001 (shown as bits) could be
encrypted with 1101010 to give you 01001100 when the exclusive or
is performed. When either the data or the key contains a 1, the
result is a 1, otherwise it is a 0. To reverse the process, you
exclusive or the encrypted data with the key a second time. This
operation is very easy for computers to perform and is used when
only a minimum of protection is required.
4. Data Encryption Standard (DES) - DES performs its encryption
by working on a block of 64 bits of your data using a 64 bit key
(we generate the 64 bit key from the key you provide). DES makes
a total of 16 passes through each 8 character (64 bit) block of
your data substituting a different character for the one
initially there. As you can guess, DES is practically impossible
to break. To eliminate even that small possibility, cipher block
chaining (CBC) is often used to strengthen DES. CBC provides an
exclusive or encryption layer underneath DES that chains the
encryption of the data from one unencrypted 64 bit block to the
next.
Page 13
(C) Copyright 1991-1993
MaeDae Enterprises
ENCRYPTED RAMBLINGS - SOME GOOD INFORMATION
===========================================
As networks proliferate, the need for data security increases.
The world in the past has largely depended on physical security,
that is safes and locks. Computers, much to everyone's
consternation, are rapidly eroding the possibility of physical
security (wherever a modem is connected to a phone line). Laws
will be passed, but in the final result, honesty depends on good
locks and all the ministrations of legislators and bureaucrats
will have little positive effect on security. Human nature will
win out. The easier it is to get, the more likely it is to be
stolen. Encryption provides part of the answer to the need for
increased security. It will be especially useful in systems that
are open to all users but which have some confidential data.
Instead of complex levels of user verification through passwords,
everyone can get the file but only the people with the key can
decode the information. Encryption in its present state is
cumbersome and time consuming but, faster computers and better
programs can ease this problem. This is where Encrypt-It comes
to the rescue.
Encryption is a fascinating exercise. Encrypt-It implements a
version of Vernham's machine developed at Bell labs in the 1920's
as part of its lite encryption method. The original machine used
Baudot code on a teletype and performed an exclusive or (XOR) on
each character of the message and the key to produce the
encrypted character. The message was decoded by the same machine
in the same manner. The method is considered unbreakable if two
conditions are met. First, the key is longer than the message
and second, the key is only used once, sometimes called a "one
time pad." Typically the files you will be encrypting are much
longer than the key (also much longer than the one we build from
your key) thereby weakening the encryption.
Distribution and maintenance of keys is unworkable in the day-today operation of any communications operation of any size.
Encrypt-It builds a much more complex key in its lite encryption
method from your simple key, in an effort to provide a means to
ease this problem. It creates a one time pad based on your
unique key. Even if you always use the same key, Encrypt-It adds
random information to make the key unique. Most random keys are
not truly random since all random functions are repeatable and
their true randomness is somewhat suspect. What is the solution?
The specter of bigger and faster computers looms in the future to
provide even faster encryption. Thinkers build on the best
thoughts of those preceding them. More powerful computers and
better encryption techniques will eventually provide a good
solution to this problem.
Encrypt-It provides encryption methods that range from the fairly
secure to the very secure. When you choose DES we use the lite
encryption methods as the first layer followed by the secure DES.
This further complicates the process of breaking the code.
Page 14
(C) Copyright 1991-1993
MaeDae Enterprises
The best encryption in the world won't protect your data if you
give away the key. Secure encryption of the data is our job.
The choice of a good key and its protection is your job.
How do you select a good key? Several things should be
considered. The key should not have a lot of repeating
characters. If they have any pattern to the eye they should not
be used. Keys should be kept secure.
Encrypt-It supports keys up to 40 characters in length. We
recommend you use as long a key as practical. Phrases or short
sentences should work well as the key and still be easy to
remember. Spaces may be used in your key, but we recommend not
using spaces at the beginning or end of the key. These spaces
are easily forgotten.
NOTE: If there is any question about the randomness of the
encrypted file, Encrypt-It could be used on it multiple times
using different keys. The true randomness of the key should not
matter since the use of more than one key should make unraveling
very difficult, if not impossible. This process could be
repeated until the paranoia of the person generating the keys was
satisfied.
Page 15