1. Which of the following is correct with respect to customers
advertisement

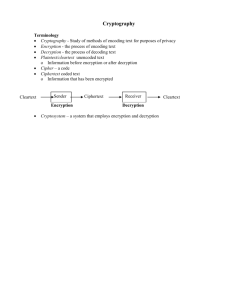
1. Which of the following is correct with respect to customers providing highly personal information across the Internet through electronic commerce transactions? (a) If a transaction is encrypted, any unauthorized parties intercepting the transaction will take ten or more years to decrypt the information. (b) Transactions are relatively secure between the consumer and a company's Web site if the data is encrypted. (c) It is impossible for anybody to see the transaction on the Internet except for the intended Web site conducting the transaction. (d) Customers should never provide charge card information when asked to complete an electronic commerce transaction. Correct answer is (b) Your score on this question is: 0.00 Feedback: See section 6.2 of the course notes. 2. Which of the following reasons is (are) valid for why "iCarnegie" is a bad password? I. II. III. It is a word from the dictionary. It does not contain numbers and symbols. It is the name of an institution. (a) II and III (b) I, II, and III (c) I and II only (d) I and III only Correct answer is (a) Your score on this question is: 0.00 Feedback: See section 6.2.3, subsection "Strong Passwords," in the course notes. 3. How does a receiver of an encrypted message verify that the message originated from the sender? (a) The receiver compares the message hashed with the sender's signature. (b) The receiver compares the received message with the sender's signature. (c) The receiver compares the message hashed with the decrypted signature of the sender. (d) The receiver compares the message with the decrypted signature of the sender. Correct answer is (c) Your score on this question is: 8.33 Feedback: See section 6.2.3, subsection "Digital Signatures," in the course notes. 4. A certificate authority associates a specific _____ with the entity requesting the certificate. (a) digital signature (b) private key (c) password (d) public key Correct answer is (d) Your score on this question is: 8.33 Feedback: See section 6.2.3, subsection "Digital Certificates and Certificate Authorities," in the course notes. 5. With respect to public key encryption, which of the following is true of a server's public key when transferring data across the Internet to a client computer? (a) It is used by client computers when transferring encrypted data from that particular server. (b) It is not a very secure method of encryption, because every computer is aware of a recipient's public key value and can decrypt the data. (c) It is used by the server to decrypt information sent by a client. (d) All clients and servers use the same public key when transferring encrypted data on the Internet. Correct answer is (a) Your score on this question is: 0.00 Feedback: See section 6.2.1 of the course notes. 6. With respect to public key encryption, which of the following is true of a server's private key when transferring data across the Internet from a client computer? (a) It is used by all clients when transferring encrypted data to that server. (b) The sender and receiver both use the private key to encrypt and decrypt a data message sent between them. (c) It is used only by the server to decrypt information received from a client. (d) It is not a very secure method of encryption, because every computer is aware of the recipient's private key. Correct answer is (c) Your score on this question is: 0.00 Feedback: See section 6.2.1 of the course notes. 7. Which of the following comparisons between public-key encryption schemes and private-key encryption schemes is true? (a) It is easier to decrypt data using private-key encryption schemes than public-key encryption schemes. (b) Private-key encryption schemes are more secure than public-key encryption schemes. (c) It takes longer to transmit encrypted data using private-key encryption schemes than public-key encryption schemes. (d) Public-key encryption schemes involve more computations than private-key encryption schemes. Correct answer is (d) Your score on this question is: 8.33 Feedback: See section 6.2.1, subsection "Hybrid Encryption Schemes," in the course notes. 8. Which of the following is (are) true about encryption of data? I. Given the high speed and low cost CPUs available, even the most complex encrypted data is not entirely safe for a long period of time. II. The more bits in the key of the encryption algorithm, the harder it is to break the encryption. III. In public key encryption, the sender and the receiver of encrypted data both use the same key value to encrypt and decrypt the data. (a) I and III only (b) II and III only (c) I, II, and III (d) I and II only Correct answer is (d) Your score on this question is: 8.33 Feedback: See section 6.2.1 of the course notes. 9. To encrypt a message using public-key encryption scheme, which of the following must be done? (a) Encrypt the message using the receiver's private key. (b) Encrypt the message using the sender's private key. (c) Encrypt the message using the sender's public key. (d) Encrypt the message using the receiver's public key. Correct answer is (d) Your score on this question is: 0.00 Feedback: See section 6.2.1, subsection "Public Key Encryption Scheme," in the course notes. 10. With respect to security on the Internet, what is the purpose of digital signatures? (a) To encrypt mail messages (b) To verify the identity of a message sender (c) To request receipts for all sent messages (d) To post anonymous messages to bulletin boards Correct answer is (b) Your score on this question is: 8.33 Feedback: See section 6.2.3 of the course notes. 11. Which of the following statements is (are) true about smart cards? I. II. They are vulnerable to Internet attacks. They can encrypt data. (a) None (b) I only (c) I and II (d) II only Correct answer is (d) Your score on this question is: 8.33 Feedback: See section 6.2.3, subsection "Smart Cards," in the course notes. 12. Encryption is used to (a) archive system files (b) save storage space (c) protect privacy by encoding data (d) store data files in a vault Correct answer is (c) Your score on this question is: 8.33 Feedback: See section 6.2.1 of the course notes. Go to top of assessment.