EMAIL ENCRYPTION Guide June 3, 2013 TABLE OF CONTENTS
advertisement

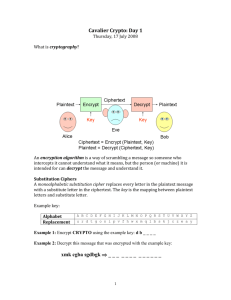
EMAIL ENCRYPTION Guide June 3, 2013 TABLE OF CONTENTS Steps to Create Encryption Public Key ....................................................................................... 3 Installing GPG ........................................................................................................................................... 3 Key Generation Process............................................................................................................................ 4 Update User Settings ................................................................................................................. 6 Decrypting an encrypted file ....................................................................................................... 7 Command Prompt Decryption ................................................................................................................... 7 Explorer Decryption ................................................................................................................................... 8 Page 2 Confidential TRX, Inc. Steps to Create Encryption Public Key The purpose of this document is to provide a quick start guide for individuals wishing to encrypt TravelTrax reports prior to them being transmitted over email. The prerequisites for following this guide are an understanding of public/private key encryption, a copy of GPG installed (can be downloaded from http://www.gnupg.org/), and a TravelTrax account. Installing GPG 1. The installation file for GPG can be obtained at ftp://ftp.gnupg.org/gcrypt/binary/gnupg-w32cli1.4.9.exe. After downloading the installer, run gnupg-w32cli-1.4.9.exe. 2. Follow the on-screen instructions, click Next until the installation has completed, and click Finish to finalize the installation. Page 3 Confidential TRX, Inc. Key Generation Process Below is a screenshot of the key generation process. In most situations, the default values are sufficient. 1. To begin the process, you must execute the following command: Page 4 Confidential TRX, Inc. gpg --gen-key 2. Select what type of key you want to generate. In most cases, the default option (1) DSA and Elgamal is sufficient. 3. When you get to the Real name field, enter the recipient’s real name (or a group name if appropriate). 4. Email address is the email address that will be receiving the reports (for example, if all reports are sent to a distribution list reports@orbitz.com, you would input that address). 5. Comment can be left blank. 6. After confirming your details, you will be required to enter a password to protect your key. Please ensure that you remember this password, as it cannot be recovered if lost. 7. Export the public key to a text file so it can be used within the TravelDashboard user profile. Type the following command: gpg --armor --export email.address@orbitz.com > pubkey.txt (Be sure to input the email address used during the key generation process). 8. This exports your public key to a text file, pubkey.txt. Note that no confirmation is displayed indicating that the process has completed. To confirm that the key has been exported successfully, browse to the file using Notepad or a similar text editor and open it. You have now successfully created a public key that can be used to encrypt email attachments! Page 5 Confidential TRX, Inc. Update User Settings Once you have an encryption key, you need to update your user settings to add the new public key. Follow the instructions below: 1. Log into TRAVELTRAX Web Reporting site. 2. Click on Edit – User Settings. 3. Paste the text from pubkey.txt including -----BEGIN PGP PUBLIC KEY BLOCK----- and ----END PGP PUBLIC KEY BLOCK----- into the Encryption Public Key box. 4. Click Save to complete. Once saved all emailed reports will be sent encrypted using your public key. Page 6 Confidential TRX, Inc. Decrypting an encrypted file Upon receiving an encrypted file, you will notice it has .gpg as a file extension. In the image below, a Credit Card Spend summary report has been sent via email and it was encrypted. To decrypt the file, first save the attachment to an easy to remember location. Command Prompt Decryption The command prompt decryption functionality is included with the basic install of GPG. Other options are available and covered later in this document. Follow these steps to decrypt an encrypted report: 1. Open a command prompt session. 2. Navigate to the location where the file was saved. 3. Input the following command: gpg --output outputfile.zip -- decrypt filename.zip.gpg, outputfile.zip = the desired filename for the decrypted file filename.zip.gpg = the filename of the encrypted file. 4. After entering your password, your file will be decrypted and ready for viewing. Page 7 Confidential TRX, Inc. Explorer Decryption There are also several utilities that allow you to decrypt a file within Windows Explorer itself. One of the most popular is GPGee 1. Go to http://gpgee.excelcia.org/. 2. Download and install GPGee by following the instructions on the website. 3. Configure the GPGee settings by right-clicking on any report file that you saved. You will see a new menu for GPGee (see below). 4. Select Configure. 5. Update the program path to reflect the location that you installed GPG (typically C:\Program Files (86)\GnuPG). 6. Set the public and secret keyring paths. 7. Click Ok and your system is configured to decrypt files. Page 8 Confidential TRX, Inc. 8. To decrypt a file, right click on the encrypted file and select Verify/Decrypt under the GPGee menu. 9. You will be presented with the screen below and required to enter your secret passphrase (the one that you set during the key generation process). 10. After clicking Ok, you will receive a message indicating that the decryption has completed successfully. Page 9 Confidential TRX, Inc.