Crypto In-Class Exercise
advertisement

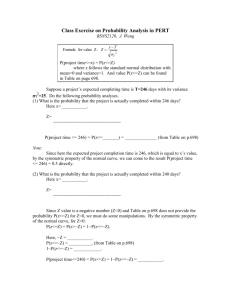
MIS 4850 Systems Security Encryption Exercises April 1, 2015 Student name: ______________________________________________ 1) For their private communications, Bill and Joe use a 16-bit key for symmetric encryption. A cryptanalyst has captured a large amount of ciphertext being sent to Joe. 2.1. What is the maximum number of keys that the cryptanalyst using the correct algorithm will have to try in order to decrypt the ciphertext and crack the key? Answer: 2.2. The cryptanalyst was able to decrypt the cipher and crack the key in 5000 tries. How can you explain this? 2) Computers’ processing power is used to crack encryption keys. Today, the maximum processing speed of microprocessors (based on clock rate and number of circuits) is about 3.5 GHz, and it is increasing by 30% roughly every year. A symmetric session key needs to be, at least, 100 bits long to be considered strong today. It will take processors that have 9 GHz speed to crack such a key. a. How long, in terms of years, it will take until microcomputers are capable of cracking a 100 bit symmetric key. Explain your answer. b. A decision is made to increase the length of a 100-bit symmetric key by one bit. What microprocessor speed will be required to break the key? Explain your answer. c. 533567395 1/2 3) A friend of yours who is running a small business wants to use symmetric encryption for confidentiality to protect communications with his business partners. As a security expert you told him that, given the nature of the transactions and the kind of risk involved, a 112-bit encryption key may be enough to protect the communications. But because he is a high-risk aversion person, he wants to use a 256-bit key. Explain what could be a downside of using a 256-bit key symmetric for encryption where a 112-bit is strong enough to provide protection. 533567395 2/2