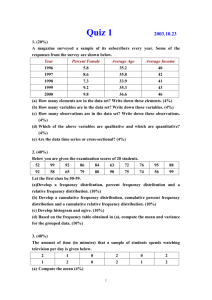
1
1.1 Pairing-based BF primitives
2
3
These are all parameterized algorithms, parameterized by an integer i. From the parameter i we also define
the dual parameter j 3 i to ease exposition.
4
5
These primitives define operations with cryptographic strength defined by reduction to the Bilinear DiffieHellman problem, defined as:
Given group elements P , aQ , bQ , cQ , compute e( P, Q) abc
6
7
8
9
10
11
For more information on this assumption, and the proof that these operations reduce to this problem, see
[Boneh2001.] This system differs from the primitives above in that the identity is encoded into an element
of Gi instead of into Z p . The mapping from a string to an element of Gi , which is typically an elliptic curve
12
For all these operations, the systems parameters are assumed to be defined as:
13
The server secret is defined to be
14
15
group, is more complex than mapping onto an integer in Z p , which is where these primitives get their
name.
s, a random element of Z p
The public parameters are defined to be P (G1 , G2 , G3 , e, Q, R) where
16
G1 , G2 , G3 , e, the system parameters as defined above in Clause 6
17
Q, a generator of G j
18
R, equal to sQ , an element of G j
19
1.1.1 Pairing-based BF: Generation (P-BF-G-i)
20
Input:
21
The parameters P (G1 , G2 , G3 , e, Q, R)
22
The server secret s
23
24
25
An encoded identity M in Gi , typically derived from an identity string
Assumptions: the parameters P describe valid bilinear groups; s is the server secret corresponding to R; and
M is an element of Gi .
26
Output:
27
28
29
30
The derived secret D, an element of Gi
Operation: Use the following steps.
1)
Compute D sM .
2)
Output D.
1
Copyright © <year> IEEE. All rights reserved.
This is an unapproved IEEE Standards Draft, subject to change.
1
2
3
NOTE—The details of encoding identities into values M vary depending on the construction that employs the P-FDH-i
primitives. Not all possible encoding methods will yield secure schemes. Some constructions will include additional
elements in the FDH public key to be used in computing M.
4
1.1.2 Pairing-based BF: Verification (P-BF-V-i)
5
Input:
6
The public parameters P (G1 , G2 , G3 , e, Q, R)
7
An encoded identity M, an element of Gi
8
9
10
The purported generated key D
Assumptions: the parameters P describe valid bilinear groups; D is a BF public key, and thus an element
of Gi ; M is an element Gi ; and D is an element of Gi .
11
Output:
12
13
The value "valid" if D is consistent with M and R and "invalid" otherwise
Operation: Use the following steps.
14
1)
Compute T1 ei ( D, Q) .
15
2)
Compute T2 ei (M , R) .
16
3)
If T1 T2 then output the value "valid," otherwise output the value "invalid."
17
1.1.3 Pairing-based BF: Encryption (P-BF-E-i)
18
Input:
19
The public parameters P (G1 , G2 , G3 , e, Q, R)
20
An encoded identity M, an element of Gi
21
22
A per-message random integer r
Assumptions: the parameters P describe valid bilinear groups.
23
Output:
24
25
A ciphertext E, an element of G j , along with a blinding factor B, an element of G3 .
Operation: Use the following steps.
26
1)
Compute E rQ .
27
2)
Compute B ei (M , R) .
28
3)
Output E and B.
29
NOTE—The blinding factor B is the same as that obtained in P-BF-D, below.
2
Copyright © <year> IEEE. All rights reserved.
This is an unapproved IEEE Standards Draft, subject to change.
1
1.1.4 Pairing-based BF: Decryption (P-BF-D-i)
2
Input:
3
The public parameters P (G1 , G2 , G3 , e, Q, R)
4
A ciphertext C
5
6
7
A generated value D
Assumptions: the parameters P describe valid bilinear groups; C is an element of Gi ; D, an element of G j ,
8
Output:
9
10
is a valid generated value according to P-BF-G-i.
A blinding factor B, an element of G3
Operation: Use the following steps.
11
1)
Compute B ei (C , D) .
12
2)
Output B.
13
14
15
s
NOTE—If both parties follow the algorithms specified, the value B computed here is ei (U , X ) , the same blinding
factor obtained in P-BF-E, above
3
Copyright © <year> IEEE. All rights reserved.
This is an unapproved IEEE Standards Draft, subject to change.