RSA Encryption and Decryption in C/C++ using Miracl
advertisement
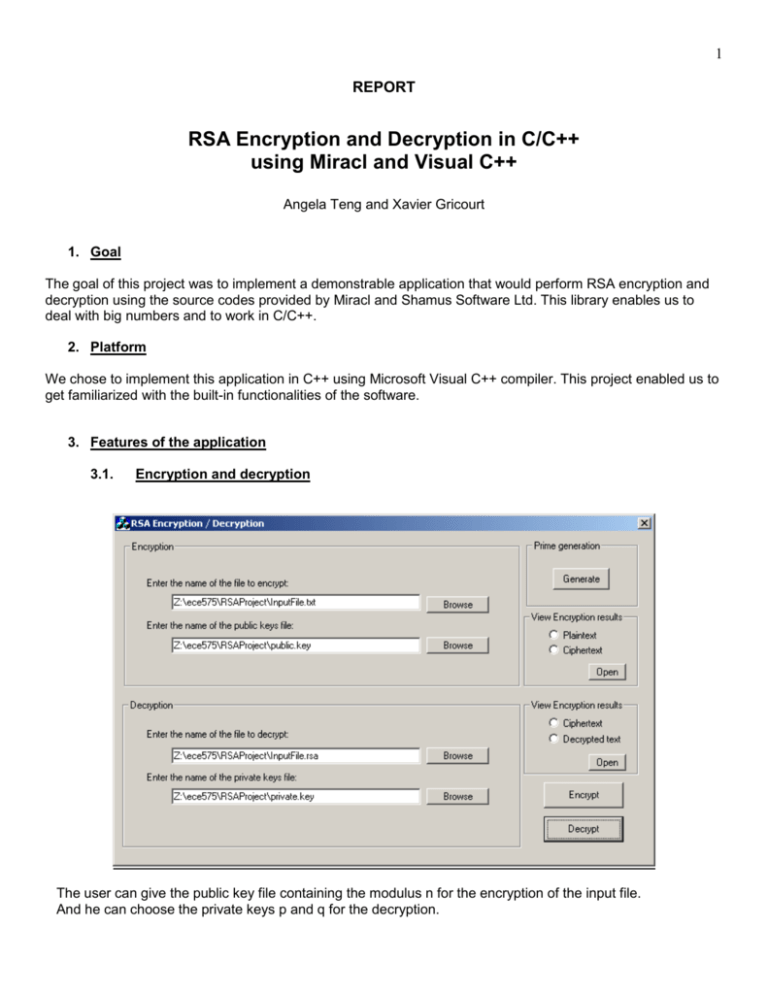
1 REPORT RSA Encryption and Decryption in C/C++ using Miracl and Visual C++ Angela Teng and Xavier Gricourt 1. Goal The goal of this project was to implement a demonstrable application that would perform RSA encryption and decryption using the source codes provided by Miracl and Shamus Software Ltd. This library enables us to deal with big numbers and to work in C/C++. 2. Platform We chose to implement this application in C++ using Microsoft Visual C++ compiler. This project enabled us to get familiarized with the built-in functionalities of the software. 3. Features of the application 3.1. Encryption and decryption The user can give the public key file containing the modulus n for the encryption of the input file. And he can choose the private keys p and q for the decryption. 2 Plaintext from the Input File Ciphertext The decrypted text is the same as the plaintext above. 3.2. Key generation By clicking on the button generate, the user can randomly generate the public and private keys files suitable for an encryption exponent e =3. The basic code provided by Miracl enabled us to implement this secondary application. We know that it might be fastidious for the user to look for correct primes by himself. The size of each prime has to be between 128 and 1024 bits and the seeds are between 0 and 9. If the user doesn't choose a name for the output files, the application will set the names to respectively "defaultpublic.key" and "defaultprivate.key". The application closes after use. If the user starts encryption or decryption after the button will be desactivated. 3 4. Problems Miracl is quite complex to understand and to use for those who are not familiarized with it, but it is very powerful. The problem with RSA encryption and decryption is that it can take a large amount of time. The larger the primes and the message are, the more time it takes. That's why for efficiency reason, we chose to fix the encryption exponent e to 3, like Miracl documentation proposed. We are not pretending the RSA algorithm is then secure. An improvement could be made to the application by enabling the user to choose e, along with p and q. The application will bug if the keys aren't correct. 5. The RSA Algorithm Encryption First, let’s assume we are at Bob’s side, as the computation of the program is too long for a big encryption exponent e, we have set e = 3. Then, the program has to generate 2 primes p and q such that gcd(e,(p-1)(q-1))=1. Bob choose p and q and the application computes n = p*q. We now assume that we are at Alice’s side. She only knows Bob's public keys. The program computes c = me (mod n) and put the result in a file .rsa. The message in the input file might be bigger than the modulus. So the program divides the message into blocks so that the length of each block is not bigger than n. Each block is then encrypted following the RSA algorithm. n and e are kept in a “public.key” file and p and q in a “private.key” file. Decryption We are back at Bob’s side, the program reads the ciphertext c = me (mod n) (which was sent by Alice). This function extracts p and q from the “private.key” file and n and e from the “public.key” file. Then, it computes d with d*e=1 (mod (p-1)(q-1)) using the Chinese remainder theorem. Finally it computes m=cd (mod n) by blocks and we get the original message.











