Exam 1, In-class Part
advertisement

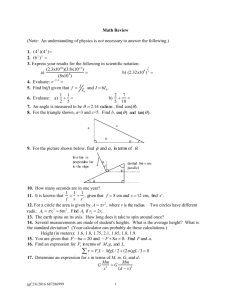
IST 230, Fall 2000 Exam I, In-class Part (60 points) Name Instruction: Most of the following problems require only short answers. No elaborate supporting work is required. Part 1 Basic Math (42 points) Problem 1 Problem 2 Problem 3 Problem 4 Problem 5 Problem 6 Problem 7 Problem 8 Part 2 Applications (18 points) Problem 9 Problem 10 Problem 11 Problem 12 Problem 13 Problem 14 Part 3 Extra Credit (5 points) Problem 15 Problem16 Total Part 1 Basic Math 1. Given two sets X 2, 5, 8 and Y 5, 6, 7, 8. a) Find X Y . b) Find X Y . c) What is the set X Y called? d) What is X Y ? e) What is the set X Y called? f) What is X Y ? g) How many elements are there in the power set P(Y)? h) How many 2-element subsets of Y are there? 2. (0, 1, 1, 0, 1, 1) and (0, 1, 0, 1, 1, 0) Z 26 are two binary vectors of length 6. a) Which two subsets of 1, 2, 3, 4, 5, 6 do the vectors represent? b) Calculate the sum of these two vectors using the binary addition. 3. Give the edge list of the following directed graph. List the edges in lexicographic order. 1 2 5 3 4 4. If a degree sequence of a graph is (1, 1, 1, 2, 2, 3, 4), what does the “Handshake Lemma” tell you about this graph? 5. If a graph has the degree sequence (1, 0, 2, 1), is it connected? 6. Draw an unlabeled tree with the degree sequence (1, 1, 1, 1, 3, 3). 7. According to Cayley’s Theorem, how many labeled 5-node trees are there? 8. A 4, 5, 6, 7. List all elements of the relation R (a, b) A2 : a 1 b in lexicographic order. Part 2 Applications 9. Binary [7,4] Hamming codes are generated with the aid of a three-circle Venn diagram. a) Draw the Venn diagram, label each region by number 1, 2, …, 7, respectively. b) Encode the binary string 0110. c) Decode 1011101. [If there is an error in the code, correct it!] 10. The CD technology uses Eight-to-Fourteen Modulation to translate bytes into codewords. Codes burnt on CDs are binary strings having at least two zeros between any two ones. It also cannot have more than ten consecutive zeros. a) Give one example of such a fourteen-bit codeword. b) Let a k stands for the number of k-bits strings satisfying the requirement that there are at least two zeros between and two ones. This is a Fibonacci numberlike sequence. For k 3 , a k a k 1 a k 3 . a 0 1 , a1 2 , a2 3 , a3 4 , a4 6 , a5 9 , a6 13 Find a7 a8 11. In the discussion of public key encryption, what mathematical concepts are involved? Circle two of the following concepts. Binary strings Fibonacci numbers Large prime numbers Modular arithmetic Permutations Binomial coefficients 12. The mesh topology used in networks is based on which type of graphs? 13. The star topology used in networks is based on which type of graphs? 14. The unit used in multi-dimensional database is called a “cell.” Which of the following concepts are related to a cell? Circle two answers. 2 , K 8 , K 64 , K 8,8 , 8-cube, 64-cube Z 28 , Z 264 , Z 64 , Z 64 Part 3 Extra Credit 15. A Hamiltonian cycle of the 3-cube is marked as follows. Following the path starting at the node labeled 000, write up a non-standard Gray code. 111 110 101 011 100 010 001 000 16. You have to take some socks out of a completely dark room. There are a dozen pairs of socks: Six pairs are white and six pairs are black. You can not tell which sock is which kind when you are in the room. You can take out the room as many socks as you want, as long as there is at least a pair of matching socks. What is the least number of socks you need to take out of the room? Answer and explain. [Hint: Use pigeon hole principle.]