LN_SE5
advertisement

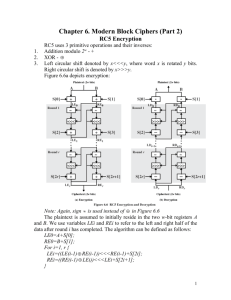
Security Engineering Ross Anderson Wiley, 2001 CH 6 – Distributed A bigger issue than this chapter allows for coverage. We’ll just poke at it a bit. Underlying cryptography (should be)/is mathematics in the form of number theory plus key exchange. Key exchange is touch on here and in chapter 2. Hard to do right but “key enabling technology for protecting distributed systems” [Ross]. Cryptography – designing ciphers Cryptanalysis – breaking ciphers Cryptology – both + use of the ciphers Need to know (jargon) – plaintext, ciphertext, cryptographic primitives, block ciphers, stream ciphers, hash functions, shared key, symmetric key, public key, private key, asymmetric key, digital signature, substitution cipher, transposition cipher (these latter two may be algorithmic or dictionary based Cryptanalysis of simple ciphers usually based on alphabetic use frequency distribution of single, or more characters in plaintext One-Time Pad – key as long as plaintext, never repeated, in its bare form fails to protect message integrity, other than that is close to being a perfect cipher as possible, subject to pad exhaustion, has synchronization problem, extremely simple (low execution overhead but high storage overhead) Stream cipher - usually hardware (gate minimization), block ciphers software (flexibility) Block cipher – want small changes in input to “diffuse” through output, longer block lengths usually better One-way functions – used to protect integrity and authenticity of messages (hash functions and message authenticity codes) Properties of random functions – one-wayness (can’t determine input given output and can’t find a given (“desired”) output when input unknown, hard to find collisions BRM-2/12/2016 CST 554 Lecture Notes (Ch 5) SE-1 Security Engineering Ross Anderson Wiley, 2001 Random generators for stream ciphers – short input long output used to encrypt a plaintext stream, like one-time pad never reused Block cipher – input and output the same size, output (cipher text) is a permutation of input, function is invertible, subject to chosen plaintext, chosen cipher text, chosen plaintext/cihertext, related key attacks with success depending on how innovative the elf is, idea is to forge a message or recover key (and then see plaintext) Digital signature – idea is to add redundant data that can only be created by one entity but verified (using a function expressly for that) by any entity, deterministic (always the same sig, most) or randomized Simple cipher block (Ross’s ECB) given sufficient ciphertext “patterns show through” allowing cut-and-paste. Good for small plaintext but longer or repeated partial texts decryptable/hackable Cipher block chaining (CBC) – uses IV & the output of one block as (part of, xor) input to succeeding block Output feedback (OFB) – turns block cipher into stream cipher, uses IV & encrypts repeatedly then xor Both CBC & OFB have integrity protection issues Cipher feedback – self synchronizing MAC – message authentication code, encrypt using CBC but throw away all but the last N bits or hash fcn Hash functions from block ciphers – feed forward, must withstand chosen key attack MD5 – 128 bit, SHA1 (key optional) – 160 bit (256 & 512 available) Good for MACs, timestamping Key updating – update key periodically (hash hash) (backward security) Autokeying – uptate key by hashing with old messages, too (forward security) Asymmetric cryptographic primitives – factoring, discrete logarithms Key exchange – 5.7.2.2 intro to many varieties, ditto digital signatures 5.7.2.3 and certification and certification authorities in 5.7.4 – in all of these understand how & when use is appropriate for use later in semester BRM-2/12/2016 CST 554 Lecture Notes (Ch 5) SE-2