File - Routing and Switching

Chapter 2 Routing and Switching Study Guide
Name: DaCota Donnelly
1.
Describe the differences between Half Duplex and Full Duplex communication? Which is preferred and why? Half duplex is when it only goes one way and full duplex is when it goes 100 percent both ways and it is preferred to have full duplex because it is better.
2.
Describe in detail using your own words the switch startup sequence. a.
First, the switch loads a power-on self-test (POST) program stored in ROM. POST checks the CPU subsystem b.
the switch loads the boot loader software. The boot loader is a small program stored in
ROM and is run immediately after POST successfully completes. c.
The boot loader performs low-level CPU initialization. d.
The boot loader initializes the flash file system on the system board. e.
the boot loader locates and loads a default IOS operating system software image into memory and hands control of the switch over to the IOS.
3.
How do you know if the switch booted successfully? The IOS operating system will initializes the interfaces using the cisco IOS
4.
What is the purpose of the mode button on a switch? The mode button is used mainly for password recovery
5.
What do the switchport LEDs indicate a.
No LED- system is off b.
LED is green- the system is operating normally c.
LED alternating between green-amber- there is a link fault d.
LED is amber- it is in standby mode e.
LED blinking amber- the internal power supply in the switch has failed
6.
What type of cable is used in the following configurations: a.
PC to switchport- straight through b.
PC to switchport console port- console cable c.
Switch to switch- cross over d.
Pc to Pc- cross over e.
PC to Routers Ethernet port- straight through f.
Router to Switch- cross over
7.
What is the purpose of configuring the switch management interface?
Because it is very important to do so.
8.
What are the commands to configure a switches management interface from a global config prompt assuming you will use VLAN99 as the management VLAN. interface vlan 99, ip address, shutdown
9.
When is it necessary to configure a switches Default Gateway? What address du you use as the switches default gateway? 172.17.99.1 and once you have it configured.
10.
How do you configure the duplex settings for a switch?
Login using telnet than enable it and than config t, interface f0/? Duplex full
11.
Is it possible for a switch to auto detect what type of cable is attached to it? If so how do you turn on this feature?
Yes it is possible, some switches come with it preinstalled and already on.
12.
List and describe at least 8 SHOW commands that can be used on a switch? a.
Show ip interface brief b.
Show ip ssh c.
Show flash d.
Show vlan e.
Show ip http interface brief f.
Show interface g0/1 g.
Show mac address-table h.
Show interface vlan 99 i.
Show run
13.
List the steps and complete commands to configure SSH on a switch. Why would you configure
SSH.
Enable
Config t
Hostname
Ip domain-name ccna.com
Cypto key generate rsa
1024
End
You would do that so you can provide secure and authentication.
14.
List the 5 common LAN Security Attacks and include the steps that you can use to mitigate them
*MAC Address Flooding- The MAC address table in a switch contains the MAC addresses associated with each physical port and the associated VLAN for each port. When a Layer 2 switch receives a frame, the switch looks in the MAC address table for the destination MAC address. All Catalyst switch models use a MAC address table for Layer 2 switching. As frames arrive on switch ports, the source MAC addresses are recorded in the MAC address table.
*The Telnet protocol is insecure and can be used by an attacker to gain remote access to a Cisco network device. There are tools available that allow an attacker to launch a brute force password-cracking attack against the vty lines on the switch.
* Brute Force Password Attack-The first phase of a brute force password attack starts with the attacker using a list of common passwords and a program designed to try to establish a Telnet session using each word on the dictionary list. If the password is not discovered by the first phase, a second phase begins. In the second phase of a brute force attack, the attacker uses a program that creates sequential character combinations in an attempt to guess the password.
Given enough time, a brute force password attack can crack almost all passwords used.
* Telnet DoS Attack- Telnet can also be used to launch a DoS attack. In a Telnet DoS attack, the attacker exploits a flaw in the Telnet server software running on the switch that renders the
Telnet service unavailable. This sort of attack prevents an administrator from remotely accessing switch management functions.
15.
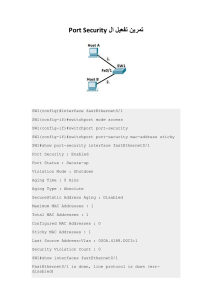
How do you configure switchport port security?
Interface f0/5
Shutdown
Siwtchport port-security
Switchport port-security mac-address ( your mac address)
No shutdown
End
Show port-security interface F0/?
16.
What do the various port security settings mean (Protect, Restrict, Shutdown)?
*Protect – drops packets with unknown source addresses until you remove a sufficient number of secure MAC addresses to drop below the maximum value.
*Restrict- Drops packets with unknown source addresses until you remove a sufficient number of secure MAC addresses to drop below the maximum value and causes the SecurityViolation counter to increment.
*Shutdown- Puts the interface into the error-disabled state immediately and sends an SNMP trap notification.
17.
What is the command to verify port security?
Show port-security interface f0/?
18.
If a port has been disabled how do you reenable?
Enable
Config t
Interface f0/1
No shutdown
End