here
advertisement

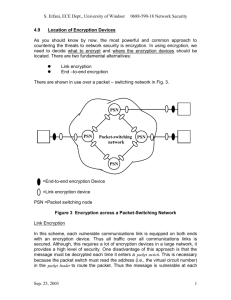
Chapter 13 Multiple Choice and True/False Answer Keys for Parts 1 and 2 Part 1 Check Your Understanding For a quick review to see what you've learned so far, answer the following questions. Visit pearsonhighered.com/techinaction to check your answers. Multiple Choice 1. Which is not a common protocol used on the Internet? a. TCP b. IP c. HTTP d. PGP 2. The large collection of national and international networks that comprises the highest-speed Internet connections is known as the a. TCP/IP pipeline. b. Internet backbone. c. HTTP conduit. d. XML gateway. 3. ISPs are connected to each other at a. Internet exchange points. b. points of presence. c. Internet intersections. d. DNS convergence points. 4. The main suite of Internet protocols used to transmit data is called a. DNS. b. XML. c. HTTP. d. TCP/IP. 5. A _________ takes the place of an IP address because it’s easier for humans to recall than a long string of numbers. a. DNS b. CGI c. domain name d. HTML True–False _____ 1. The Internet is primarily managed by U.S. government agencies. (false) _____ 2. Open system protocols are proprietary. (False) Part 1: Critical Thinking 1. Master of the Internet Now that you know something about how the Internet is managed, how would you improve it? How should the costs of maintaining and improving the Internet be shared among countries? Should there be special treatment given to some information (say, the transfer of medical files to emergency trauma centers) versus other information (chain letters)? Student responses will vary but suggestions may include improved security and privacy; implementation of methods to reduce or eliminate malware, hoaxes, hacking, and other threats; improved access worldwide, etc. Students may suggest different ways of sharing costs between countries – some may believe costs should be shared equally, others may believe that third world countries should receive support from those countries better able to afford it. Students’ opinions regarding giving precedence to Internet traffic based upon content may vary, but they should provide support for their position. 2. The Perfect Packet In packet switching, data is broken up into smaller bundles. How small should a packet be for the best performance? Is it better to have many more, very small packets or just a few packets? How would you decide, and would the answer be the same for all types of information? Student responses will vary. Students should research packet switching to determine what, if any, size limitations exist. Some students may believe that many smaller packets would provide increased security, whereas others may believe that sending fewer large packets will be quicker and more efficient. Students should defend their opinion and provide documentation as appropriate. Part 2 Check Your Understanding For a quick review to see what you've learned so far, answer the following questions. Visit pearsonhighered.com/techinaction to check your answers. Multiple Choice 1. The main use for DHTML is a. creating a secure connection between client and server. b. loading web pages into a browser. c. encrypting e-mail messages. d. making web pages interactive. 2. The protocol used to send e-mail over the Internet is a. HTTP. b. DHTML. c. DNS. d. SMTP. 3. Cascading style sheets allow you to quickly change a. from server-side processing to client-side processing. b. to a more secure transport protocol. c. the rules for applying formatting to an HTML document. d. from HTML to XML. 4. A Java applet is a. downloaded and run in the client browser software. b. executed using JavaScript on the server. c. incredibly fast because it has no load time. d. software that runs exclusively under Mac OS X. 5. MIME is a protocol that is used when you are a. sending a video file to YouTube. b. encrypting an e-mail message. c. executing a CGI script. d. sending an e-mail that has a file attached. True-False _____ 1. The type of encryption most commonly used on the Internet is publickey encryption. (True) _____ 2. HTML5 allows you to create your own tags to describe data, like <shoesize>. (False) Part 2 Critical Thinking 3. Encryption of E-Mail Do you currently encrypt your personal e-mail? When would it be of value? Do you think your school should provide encrypted e-mail for student use? If a stu- dent accused another student of harassment, should the school administrators be allowed to break the encryption? Students should understand both the pros and cons of encrypted e-mail. Discussion should include potential risks which could result from interception of e-mail messages in personal, business, academic or government situations. Additionally, expand the discussion to consider the importance of information security for organizations such as law offices, medical offices, and counseling providers. Students could also report about examples resulting from compromised security in their own experience or by searching online. While differences of opinion can be expected, students should provide support for the conclusions they reach. 4. Breaking Encryption Encryption programs based on 256-bit encryption algorithms are currently considered unbreakable. The U.S. government places restrictions on exports of these encryption products. The government is considering a requirement that all encryption products have a “backdoor” code that would allow government agencies (such as the FBI and CIA) to read encrypted messages. Do you think this backdoor requirement should be implemented? This is a topic with no right answer because it is a clash of security versus privacy, and neither value is inherently superior to the other. When positive values clash, we usually end up saying something like, “…In this situation….” But to do that here we would need restrictions on the use of the back door. How would students react to learning of abuse in the use of a back door key? The government is made up of people and one disgruntled person could post the encryption key—recall wikileaks’ posting of secret government information. Students might consider how an encryption key might be used if it fell into the wrong hands.