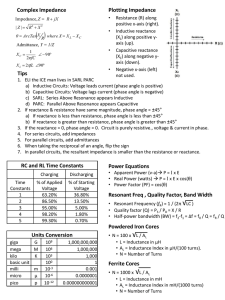
Building on Reactance Theory to Explain and Predict When IT
advertisement

Building on Reactance Theory to Explain and Predict When IT Security Policies and Controls Can Backfire and Cause Malicious End-User Behavior Paul Benjamin Lowry, Ph.D. IS Ph.D. Preparation Program Coordinator, Information Systems Department, Brigham Young University Danny Bakker Matthew Ehle Joseph Gridley Britton Kowalk Scott McCown MISM and Ph.D. Preparation students, Information Systems Department, Brigham Young University Status of manuscript: This is a work-in-process (in design / data-collection phase; will be further along by the time of the conference) that is being conducted as part of the IS Ph.D. preparation program at Brigham Young University. Research questions: Do some IT controls end up being counter-productive because they go too far in restricting freedoms that employees consider to be personally important? Can Reactance Theory be a helpful theory on which we can predict which kind of IT security control will be effective in the workplace and which will not be? Theory and Theoretical Model: We believe that Reactance Theory can be an effective theoretical model that can help predict which kinds of IT security controls will be productive or counter-productive in a work environment. Reactance Theory explains that every person has a set of free behaviors that they value, and that they will experience reactance whenever any of those behaviors is eliminated or threatened with elimination (Brehm, 1966). The importance of freedom for a given behavior “is a direct function of the unique instrumental value which that behavior has for the satisfaction of needs, multiplied by the actual or potential maximum magnitude of those needs. By unique is meant that no other behavior in the individual’s repertoire of behaviors would satisfy the same need or set of needs” (Brehm 1966, pp. 4-5). Reactance is “a motivational state directed toward the re-establishment of the threatened or eliminated freedom” (Brehm 1966, p. 15). The creation of reactance by a highly restrictive IT policy could be highly detrimental because Reactance Theory would indicate that there could be policies that would actually encourage users to work against the policy. Our study tries to further establish what kind of policies would backfire from underlying reactance. We further development Reactance Theory by considering some important and recent theoretical extensions by Dillard and Shen (2005) and Quick and Do (2009). Specially, we add concepts of anger and controlling language, and the idea of the “boomerang effect” that comes from reactance. “Boomerang effects arise whenever an individual restores his or her freedoms by expressing motivation to perform the threatened or eliminated behavior. Related boomerang effects occur whenever an individual does not exercise the threatened or eliminated freedom but instead performs a related admonished activity. Vicarious boomerang effects happen whenever an individual associates with others who perform the threatened or eliminated freedom” (Quick & Kim 2009, p. 769). Anger is negative affect that occurs as a result of reactance, and can result in detrimental organizational behaviors (Dillard and Shen, 2005). Controlling language is the use of “forceful language that explicitly pressures or attempts to control audiences into message conformity” (Quick and Kim 2009, p. 767). Controlling language—regardless of actual freedom loss—has been shown to be a factor in reducing perceived freedom and increasing reactance. Our theoretical model is depicted as follows: Approach: Aside from conducting a preliminary pilot test, our data collection approach will be three-fold: (1) we will conduct an online factorial survey of approximately 250 working professionals (commissioned by a market research firm) that will provide each participant with a series of 15 randomized vignettes that will manipulate the IVs in our model—focusing on different kinds of IT policies that can cause perceived loss of freedom (e.g., password policies, surfing policies, software monitoring, tiered-IT policies, encryption policies, laptop policies, etc.). Such factorial surveys are highly effective in indicating which IV manipulations will be most effective for impacting the DVs. (2) Based on the most effective manipulations from the online factorial survey, we will conduct an online experiment of approximately 500 working professionals (commissioned by a market research firm) that will provide each participant one descriptive vignette designed to carefully manipulate the IVs (focusing on loss / gain of freedom), and we will ask them about their intention to comply to the tiered-IT policy they were given. From this we will construct a PLS SEM model to test our underlying model. (3) We will conduct an online survey of approximately 1000 working professionals (commissioned by a market research firm) where we ask them to describe their freedoms, organizational use of controlling language, importance of freedoms, etc., and ask them to describe their current intention to follow their given IT security policies. This will further be used to test the generalizability of the theory to current working conditions. This will also be analyzed with a PLS SEM model. Expected contributions: The unique contribution of this study is to bring a new theory into the IS security realm (Reactance Theory) that can explain and predict which IT security policies are going to cause negative reactance by employees and under which contextual conditions. This is particularly useful because if Reactance Theory holds, there will be some common IT policies that can backfire to where not only will employees not intend to comply with them, they may do the opposite of the policy to regain their freedoms. From the results practitioners can come to know what magnitude of reactance to expect from their employees that are limited by policies, as well as whether or not it is a good idea to allow employees to regain freedoms through company provisions based on certain criteria.