Copyright 2014 Compliance Education Institute, LLC 800.310.5580
advertisement
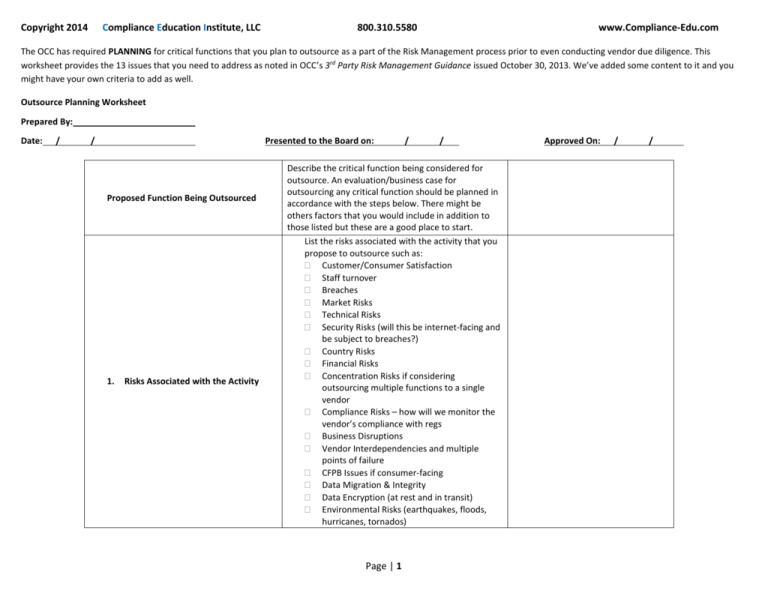
Copyright 2014 Compliance Education Institute, LLC 800.310.5580 www.Compliance-Edu.com The OCC has required PLANNING for critical functions that you plan to outsource as a part of the Risk Management process prior to even conducting vendor due diligence. This worksheet provides the 13 issues that you need to address as noted in OCC’s 3rd Party Risk Management Guidance issued October 30, 2013. We’ve added some content to it and you might have your own criteria to add as well. Outsource Planning Worksheet Prepared By: Date: / / Presented to the Board on: Proposed Function Being Outsourced 1. Risks Associated with the Activity / / Describe the critical function being considered for outsource. An evaluation/business case for outsourcing any critical function should be planned in accordance with the steps below. There might be others factors that you would include in addition to those listed but these are a good place to start. List the risks associated with the activity that you propose to outsource such as: Customer/Consumer Satisfaction Staff turnover Breaches Market Risks Technical Risks Security Risks (will this be internet-facing and be subject to breaches?) Country Risks Financial Risks Concentration Risks if considering outsourcing multiple functions to a single vendor Compliance Risks – how will we monitor the vendor’s compliance with regs Business Disruptions Vendor Interdependencies and multiple points of failure CFPB Issues if consumer-facing Data Migration & Integrity Data Encryption (at rest and in transit) Environmental Risks (earthquakes, floods, hurricanes, tornados) Page | 1 Approved On: / / Copyright 2014 Compliance Education Institute, LLC 800.310.5580 Discuss how the arrangement aligns with the bank’s overall strategic goals, objectives, and risk appetite such as: 2. Strategic Purpose of the Relationship Reduce Headcount Improve Operational Cost Efficiencies Reduce Costs (list the type) Introduce New Capabilities to gain competitive advantage Technology Advantages Reduce Internal Infrastructure Consolidate Vendors Fill gap where expertise is lacking Assess the complexity of the arrangement such as: 3. Assess The Complexity of the Arrangement Volume anticipated (if applicable) Will a vendor likely require subcontractors? Will foreign-based support (call center, application development, help desk) be required? Systems Complexity Financial Complexity Compliance Complexity – are there numerous regs from multiple agencies to comply with Legal Complexity: state, Federal and possible country rules that must be complied with Technical: what technology will be required by the institution Vendor Monitoring: what will the nature of monitoring of the vendor look like (reviews of DR tests, policy reviews, audits and reports, insurance coverage, bond, financial reporting, performance monitoring, etc.) Page | 2 www.Compliance-Edu.com Copyright 2014 Compliance Education Institute, LLC 800.310.5580 Conduct a cost-benefit analysis that spans the term a projected relationship in order to determine the Total Cost of Ownership vs the Cost of the Outsource. First consider the current cost to the institution: 4. Determine whether the financial benefits outweigh the estimated costs to control risks Staffing costs along with adjustments for salary increases over the term that the function would be outsourced Current Software/Hardware maintenance fees Supplies cost Cost of technology controls currently in place that could be possibly eliminated Then consider the following as a comparison: estimated direct contractual costs estimated indirect costs to augment or alter bank processes and systems to accommodate the outsourced function staffing to properly manage the third-party relationship cost to adjust or terminate existing contracts Review the institution's list of strategic initiatives in order to determine where there might be conflict, overlap or synergy. Initiatives might include: 5. Consider how the third-party relationship could affect the institution's other strategic initiatives large technology projects organizational changes mergers acquisitions divestitures Present issues to the Board to resolve any conflict/overlap based upon priority, risk and benefit. Page | 3 www.Compliance-Edu.com Copyright 2014 Compliance Education Institute, LLC 800.310.5580 6. Consider how the third-party relationship could affect the institution's employees and dual employees (employed by the institution and the vendor) 7. Assess the nature of customer interaction with the third party and the impact the relationship will have on customers. What transition steps are needed to manage the impacts when the activities currently conducted internally are outsourced. Will the outsourced function require employee retraining, headcount reduction, redeployment to other areas of the institution? Will the outsourced function require the vendor's employees to be located on the institution's site? Will there be shared employment of staff as is typical with facilities management outsourcing? Will there be access to or use of confidential or sensitive information? Will there be joint marketing or franchising arrangements Describe the handling of customer complaints, if applicable, and outline plans to manage these impacts. Is customer interaction direct or indirect? If direct, how will the institution monitor that interaction for CFPB compliance and determine customer satisfaction? Will it be through access to reports, complaints, CRM system, surveys sent to customer? Will customer costs be increased/decreased/no impact? Page | 4 www.Compliance-Edu.com Copyright 2014 Compliance Education Institute, LLC 800.310.5580 8. Assess potential information security implications 9. Consider the institution’s contingency plans in the event it needs to transition the activity to another third party or bring it inhouse 10. Assess the extent to which the activities are subject to specific laws and regulations What type of data will the vendor have access to: NPPI, Confidential Data? What media form? Will the vendor view, add, modify, delete, transmit, store, destroy, manage, process, encrypt it? Will the vendor have access to infrastructure? Will the vendor have access to critical applications? Will the vendor have physical access to secure areas of the institution's facilities and, if so, will it be supervised? Will the vendor have access to environmental controls and utilities that might affect the institution's data center? Before the institution even evaluates any vendors, it must have a contingency plan in place in case the vendor has a business disruption or the institution decides that it becomes more strategic to move the service to another vendor or bring the function back in house. That plan should be described here. It could include having alternate providers lined up. A thorough study of the legal and compliance regulations must be conducted so that the institution understands the regulatory issues that both itself and the vendor will be faced with and the capabilities that a vendor must have to ensure compliance. The institution must also have a way in which to monitor the vendor for compliance with all laws and regulations. Privacy Information security Bank Secrecy Act/Anti-Money Laundering (BSA/AML) Fiduciary requirements Page | 5 www.Compliance-Edu.com Copyright 2014 Compliance Education Institute, LLC 11. Consider whether the selection of the third party is consistent with the institution’s broader corporate policies and practices including its diversity policies and practices. 12. Detail how the institution will select, assess, and oversee the third party. 800.310.5580 www.Compliance-Edu.com Does the institution have a policy that commits a percentage of projects to small businesses, minorityowned businesses, etc. and will outsourcing this function help it achieve its goals with respect to its policy? Describe it here and whether the outsource satisfies that policy. This should be covered in the institution's vendor management program and should include policy for conducting: Due Diligence, Risk Assessment Ongoing Monitoring Periodic Review (Financial Review, Performance Review, Contract Compliance, etc.) Review Date: 13. Present to and be approved by the institution’s board of directors when critical activities are involved. The Board MUST review and approve the business case for outsourcing critical functions prior to even searching for vendors and conducting due diligence. Indicate the date that this Planning document has been presented to the Board and any other supervisory committees, executives, etc. Revision Date Approval Date: Approval #1: Approval #2 Approval #3: Page | 6







