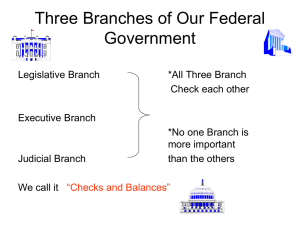
Aff - Millennial Speech & Debate
advertisement

Aff 1AC Plan The United States Supreme Court should hold in American Civil Liberties Union v. Clapper that the collection of metadata by or for the use of the National Security Agency is an unconstitutional violation of the Fourth Amendment to the United States Constitution. Advantage 1 – Democracy Failure of the supreme court to rein in NSA metadata surveillance signals abdication of constitutional scrutiny and loss of judicial independence McCormack, 2014 (Wayne, E.W. Thode Professor of Law, University of Utah, “U.S. Judicial Independence: Victim in the ‘war on terror,’” Washington & Lee Law Review, Winter, 71 Wash & Lee L. Rev. 305) The battle over NSA surveillance probably has less to do with actual invasions of privacy and more to do with the sense that government decided it can do whatever it wants to do with total impunity. The existence of secret NSA programs is not at all surprising to those who have paid close attention to this issue for the last decade. The fact is that our government was never open or transparent about what it was doing, and we knew it was not. For example, Attorney General Alberto Gonzales in a number of public statements during 2005 and 2006 was always careful to say "the program the President has disclosed" is legal, leaving open the inference that there was much more that had not been disclosed: A word of caution here. This remains a highly classified program. . . . So my remarks today speak only to those activities confirmed publicly by the President, and not to other purported activities described in press reports. These press accounts are in almost every case, in one way or another, misinformed, confusing, or wrong. And unfortunately, they have caused concern over the potential breadth of what the President has actually authorized. n429 Nowhere in the many public statements of the era--all of which are contained on the DOJ website-is there any mention of [*387] the undisclosed activities of the NSA. Naturally we would get "press accounts . . . [that were] misinformed, confusing, or wrong." n430 But we probably got some information that was accurate. What do we know now in 2014? We know that NSA and its affiliated agencies are capable of reading all our e-mail and listening to our phone conversations. n431 Do they do so? They would have us believe they are too busy to bother with us little people. But it is also clear that if the "metadata mining" reveals a pattern of curiosity, then it is a simple matter to reach into the grab bag and pull out everything any particular individual has said for a long period of time. n432 Indeed, some instances of unauthorized snooping into content have been acknowledged and one FISA judge has described the NSA as having repeatedly misrepresented its activities to the court. n433 The FISA Court has approved "programmatic" surveillance by interpreting the word "relevant" n434 to mean basically all electronic communications, which can be monitored for suspicious patterns. n435 "And under the 'reasonable suspicion' standard, there [*388] is no judicial review when someone decides to look into the content of those communications." n436 Frankly, I'm not so sure that privacy of information is really that important, except to the extent that I need to be able to protect my bank accounts from being raided. What makes the NSA dustup more disturbing is the feeling within government that government can act with impunity in the name of "national security." n437 If they can read my e-mails today, can they haul me off to a military brig without judicial approval tomorrow? Oh, wait, they did that already--kept several people locked up for years with total impunity--even tortured with impunity. n438 Recently, two judges have taken a hard look at the NSA activity and disagreed on the merits. n439 At least, these two judges did not yield to the temptation to abdicate judicial independence in the face of the dreaded word "terrorism." n440 G. Standing The U.S. federal courts have a rather mystical, ethereal approach to their "special place" in separation of powers. Part of the mystique is a doctrine called "standing," which I have described elsewhere as part of the "Mythology of Justiciability." n441 The heart of the doctrine is that a person who is not able to show an injury by another person has no claim of right against that [*389] other person. The mystery is why we need to waste barrels of ink and jurisprudential energy on a point basic to all of law--if you haven't harmed me, I don't have a claim against you. n442 Be that as it may, there are two instances in which federal courts have turned blind eyes to what would seem to be palpable injuries, either likely or threatened. These are the cases dealing with the illegal surveillance by the NSA under the heading of the Terrorist Surveillance Program (TSP), n443 and the targeted killing of a U.S. citizen, Anwar al-Aulaqi. n444 1. Have I Been Bugged? A number of lawsuits challenged the NSA program. One suit was brought by the ACLU on behalf of a group of individuals and groups who regularly conducted international telephone and Internet communications for legitimate professional reasons (for example, journalism or the practice of law). n445 A district court in Michigan granted the plaintiffs' request for an injunction, finding that the TSP violated FISA, the First and Fourth Amendments, and the separation of powers doctrine. n446 On appeal, the Sixth Circuit found that the plaintiffs lacked standing to bring the action. n447 They could not show that any particular conversation was intercepted, nor could the plaintiffs claim that any personal interest was harmed by refraining from conversations that might [*390] be monitored. n448 Judge Gilman dissented on the ground that the attorney-plaintiffs had a clear duty to refrain from communicating with clients when those communications were likely to be intercepted, and were thus able to show a cognizable harm from the threat of interception. n449 Speaking to the merits, Judge Gilman argued that the TSP was illegal because "the clear wording of FISA and Title III that these statutes provide the 'exclusive means' for the government to engage in electronic surveillance within the United States for foreign intelligence." n450 At the same time, the Al-Haramain Foundation and two of its lawyers filed a similar action against the government in Oregon district court. n451 Al-Haramain is a Muslim charity designated a "Specially Designated Global Terrorist" by the Treasury Department's Office of Foreign Assets Control, which freezes the organization's assets and makes it illegal for others to do business with it. n452 At one point, the Government inadvertently disclosed a "top secret" document that proved Al-Haramain had been subjected to warrantless surveillance and prompted a further claim for unlawful surveillance. n453 The Government sought to dismiss the case by invoking the state secrets privilege, which the district court rejected on the basis that the existence of the TSP was not a secret, and that "no harm [*391] to the national security would occur if plaintiffs [were] able to prove the general point that they were subject to surveillance as revealed in the Sealed Document," so long as no other information in the document was revealed. n454 The Ninth Circuit granted the Government's request for interlocutory review of the state secrets issue, n455 holding that the public disclosures about the TSP had already made the basic dimensions of the program known and thus the state secrets privilege did not foreclose the lawsuit entirely. n456 Nevertheless, the top-secret document was protected by the privilege, and the plaintiffs would not be allowed to introduce their memory of the document into evidence. n457 Although the court believed that the plaintiffs could not establish standing without the document, the Ninth Circuit remanded the case to the district court to determine whether FISA might preempt the state secrets privilege. n458 On remand, the district court first held that FISA would, in fact, preempt the privilege, but a remedy would be available only on behalf of someone who was an "aggrieved person" under the statute. n459 The plaintiffs were able to rely on public announcements by government officials and publicly available press reports to make a prima facie case, based on nonclassified information, that they were aggrieved persons because of wiretaps and e-mail intercepts [*392] without a court order. n460 After extended recalcitrance by the Government, the district court ordered: Plaintiffs have made out a prima facie case and defendants have foregone multiple opportunities to show that a warrant existed, including specifically rejecting the method created by Congress for this very purpose. Defendants' possession of the exclusive knowledge whether or not a FISA warrant was obtained, moreover, creates such grave equitable concerns that defendants must be deemed estopped from arguing that a warrant might have existed or, conversely, must be deemed to have admitted that no warrant existed. The court now determines [that f]or purposes of this litigation, there was no such warrant for the electronic surveillance of any of plaintiffs. n461 With no genuine issue of material fact, the district court granted summary judgment for the plaintiffs, and it later awarded them about $ 41,000 in damages and over $ 2.5 million in fees and expenses. n462 The entire amount went to the attorney-plaintiffs, as the "[d]istribution of any funds to plaintiff Al-Haramain is impossible because Al-Haramain's assets are blocked as a result of its designation as a SDGT organization." n463 Indeed, the district court acknowledged that "the government had reason to believe that Al-Haramain supported acts of terrorism." n464 In the final episode of this long-running litigation, the Ninth Circuit ruled that the Government enjoyed sovereign immunity from a damage action by the organization. n465 Another large number of lawsuits alleged that telecommunications companies violated their customers' rights by [*393] cooperating and assisting the NSA in surveillance of their phones. n466 The actions were consolidated as part of the multi-district litigation panel in northern California. n467 While these cases were pending in district court, Congress enacted a statutory provision rendering an electronic communications service provider immune from suit if the Attorney General certified that the provider helped the government in intelligence gathering, including assistance in executing the TSP. n468 Based on this provision, the district court dismissed the pending suits against the telecommunications companies. n469 On appeal, the Ninth Circuit affirmed, rejecting a series of constitutional arguments, including several related to the separation of powers doctrine and due process considerations. n470 But in another opinion on the same day, the Ninth Circuit allowed a class action suit to proceed against the Government for what the plaintiffs described as "a communications dragnet of ordinary American citizens." n471 According to the court, the [*394] plaintiffs had standing by alleging a concrete and particularized injury from the collaboration between the government and AT&T at a specific facility in San Francisco. n472 And although the claims "strike . . . at the heart of a major public controversy involving national security and surveillance," the Ninth Circuit refused to characterize the legal issues as political questions, or to impose a heightened standing requirement for government surveillance involving national security interests. n473 Where this case will go now after the Snowden revelations remains to be seen, but at least the Ninth Circuit has shown itself to be the exception in standing up against some of the government abuses. The FISA Amendments Act of 2008 (FAA) n474 continued the authorization of intercepts involving parties outside the United States but stipulated that the government may not conduct electronic surveillance or intercept wire, oral, or electronic communications except pursuant to express statutory authorization (for example, FISA). n475 This statement of exclusive authority should have defused the Executive argument for unfettered discretion, but of course we now have public admissions of massive government gathering of electronic communications data. n476 [*395] The ACLU filed suit against the FAA on behalf of a group of attorneys, journalists, and legal, media, and human rights organizations, arguing that the provision "allows the executive branch sweeping and virtually unregulated authority to monitor the international communications . . . of law-abiding U.S. citizens and residents." n477 The district court granted summary judgment in favor of the government on the basis that the plaintiffs lacked standing to bring the suit. n478 On appeal, a panel of the Second Circuit reversed and remanded, asserting that the plaintiffs had standing based on a reasonable fear that their sensitive international electronic communications were being monitored, requiring them to engage in costly and burdensome measures to protect the confidentiality of communications necessary for their work. n479 In September 2011, the Second Circuit denied rehearing en banc by an equally divided vote. n480 In February 2013, the Supreme Court reversed on standing grounds, agreeing with the Government that the plaintiffs failed to show a realistic threat of imminent injury. n481 Their speculations required assuming that the government would target their communications, that authorization under the statute would be judicially approved, and that government would succeed in acquiring their communications. n482 Moreover, the plaintiffs' choices to make expenditures to prevent interception of confidential communications based on hypothetical future harm [*396] was their own choice and not the direct result of identifiable government action. n483 Of course, now we know the assumptions of the Supreme Court about judicial authorization of intercepts were unfounded because the NSA has been monitoring anything and everything that it chooses to monitor. n484 This set of assumptions was particularly poignant in some of the dissents from the earlier Second Circuit denial of rehearing. n485 One dissent pointed to the FISCR's opinion in In re Directives as offering "a glimpse into the actual world of foreign intelligence targeting," which "appears quite different from the one hypothesized by plaintiffs." n486 [The FISCR] reviewed the actual procedures adopted by the executive to satisfy PAA requirements and found that they in fact afforded "protections above and beyond those specified" in the statute and adequately allayed any particularity or probable cause concerns. . . . Such scrupulous oversight rebuts any general assumptions, unsupported by specific facts, that the executive will instinctively abuse its targeting discretion under the FAA. . . . n487 Now that it is publicly known that the NSA has been routinely gathering information on U.S. residents, the assertion that the statutes "rebut . . . any general assumption, unsupported by specific facts, that the executive will instinctively abuse its targeting discretion" rings extremely hollow. n488 This is not to say that the judges holding that view were knowingly complicit in government misdeeds, but they certainly chose consciously to turn a blind eye when their colleagues were insisting on scrutiny of actual government practices. [*397] 2. Judicial Review of Killing U.S. Citizens The final case that I wish to highlight here is the "targeted killing" of Anwar Al-Aulaqi, a U.S. citizen who expatriated to Yemen and became a major jihadist figure on the Internet. n489 When it was leaked in the press that Anwar al-Aulaqi had been placed on the U.S. government's kill lists, his father Nasser al-Aulaqi filed suit to assert his son's rights to due process. n490 His lawsuit also asserted that the U.S. targeted-killing policy violated the Fourth and Fifth Amendments, as well as treaty and customary international law. n491 While asking for an injunction to stop the government from killing his son, he sought a declaration that the policy was illegal and disclosure of the criteria used to determine whether to target a U.S. citizen. n492 The D.C. District Court started with the observations that this "unique and extraordinary case" presented "[s]tark, and perplexing, questions" such as: "How is it that judicial approval is required when the United States decides to target a U.S. citizen overseas for electronic surveillance, but that, according to the defendants, judicial scrutiny in prohibited when the United States decides to target a U.S. citizen overseas for death?" n493 Yet, the court dismissed the case, holding that Nasser al-Aulaqi lacked standing to bring the constitutional claims on behalf of his son. n494 The court also blindly asserted that there was nothing to prevent Anwar al-Aulaqi from peacefully presenting himself at the U.S. Embassy in Yemen and announcing his wish to vindicate his constitutional rights in court, which, as a matter of domestic [*398] and international law, the U.S. government would have to respect without resorting to violence. n495 Moreover, it was not clear that the father was serving his son's "best interests," understood as acting in accordance with Anwar al-Aulaqi's intentions or wishes. n496 There was no evidence that Nasser al-Aulaqi wanted to vindicate his rights in a U.S. court; to the contrary, his public statements showed disdain for the American legal system, as well as a belief that Muslims were not bound by Western law and it was therefore legitimate to violate U.S. law. n497 Moreover, Nasser al-Aulaqi's claims might have been barred by sovereign immunity, because a suit against the President, Secretary of Defense, and CIA Director was "tantamount to a suit against the United States." n498 In the portion of its opinion most strikingly presenting problems of judicial independence, the court refused to decide this question by exercising its "equitable discretion" to avoid interjecting itself into sensitive issues of foreign affairs and activities by the military and intelligence community. n499 Serious separation-of-powers concerns would be raised by a "judicial attempt to enjoin the President in the performance of his official duties." n500 The same would be true of a court order granting declaratory and injunctive relief against the nation's top military and intelligence advisors regarding the use of force abroad, when such action was (purportedly) authorized by the President himself. n501 [*399] Finally, in a similar vein, the court concluded that the case was a nonjusticiable political question. n502 This doctrine exempts from judicial review those matters that are committed by the U.S. Constitution to the political branches, including the precise issue in this case--the decision to employ military force. n503 According to the court, resolution of the plaintiff's claims would require it to decide: (1) [T]he precise nature and extent of Anwar Al-Aulaqi's affiliation with AQAP; (2) whether AQAP and al Qaeda are so closely linked that the defendants' targeted killing of Anwar Al-Aulaqi in Yemen would come within the United States' current armed conflict with al Qaeda; (3) whether (assuming plaintiff's proffered legal standard applies) n504 Anwar Al-Aulaqi's alleged terrorist activity renders him a "concrete, specific, and imminent threat to life or physical safety . . . ."; and (4) whether there are "means short of lethal force" that the United States could "reasonably" employ to address any threat that Anwar Al-Aulaqi poses to U.S. national security interests. . . . Such determinations, in turn, would require this Court . . . to understand and assess the "capabilities of the [alleged] terrorist operative to carry out a threatened attack, what response would be sufficient to address that threat, possible diplomatic considerations that may bear on such responses, the vulnerability of potential targets that the [alleged] terrorist[] may strike, the availability of military and nonmilitary options, and the risks to military and [*400] nonmilitary personnel in attempting application of non-lethal force." n505 It is truly a mystery why a court should have to decide any of those questions to rule on whether a U.S. citizen abroad has due process or other legal rights before being executed by executive fiat. The judicial function consists of setting out the criteria for the Executive to follow in making those decisions. n506 The court confessed its concern that "there are circumstances in which the Executive's unilateral decision to kill a U.S. citizen overseas is 'constitutionally committed to the political branches' and judicially unreviewable" but nonetheless concluded that it was barred from adjudicating the merits of the case. n507 The United States then used aerial unmanned aircraft (drones) to execute not just Anwar but also his son Abdulrahman and a colleague, Samir Khan. n508 In July 2012, the ACLU filed a new suit on behalf of the families of all three, arguing that the killings violated the Fourth Amendment's ban on unreasonable seizures, the Fifth Amendment's right to due process, and the Bill of Attainder Clause. n509 In addition, the ACLU filed a FOIA request and subsequent legal action seeking records related to legal authority and factual basis for the targeted killing of the three individuals. n510 In a masterly display of the various doctrines considered in this Article, on December 14, 2012, DOJ filed a motion to dismiss the damage action on the grounds of lack of standing, political question, qualified immunity, failure to state a claim under due [*401] process, and Executive freedom from the Bill of Attainder Clause. n511 V. Conclusion The "head in the sand" attitude of the U.S. Judiciary in the past decade is a rather dismal record that does not fit the high standard for judicial independence on which the American public has come to rely. Many authors have discussed these cases from the perspective of the civil rights and liberties of the individual. n512 What I have attempted to do here is sketch out how the undue deference to the Executive in "time of crisis" has undermined the independent role of the Judiciary. Torture, executive detentions, illegal surveillance, and now killing of U.S. citizens, have escaped judicial review under a variety of excuses. n513 To be clear, many of the people against whom these abuses have been levied are, or were, very dangerous if not evil individuals. Khalid Sheikh Muhamed and Anwar al-Aulaqi should not be allowed to roam free to kill innocent civilians. But hundreds of years of history show that there are ways of dealing with such people within the limits of restrained government without resort to the hubris and indignity of unreviewed Executive discretion. The turning of blind eyes by many, albeit not all, federal judges is a chapter of this history that will weigh heavily against us in the future. [*402] No judge wants to feel responsible for the deaths of innocents. But direct responsibility for death lies with those who contribute to the act. Meanwhile, the judge has an ethical responsibility for abuses by government of which the Judiciary is a part. To illustrate the threat, one federal judge resigned from the secret FISA Court in "protest because the Bush administration was bypassing the court on warrantless wiretaps." n514 To be fair, his public statement before Congress included the thought that the judges were independent but not making fully informed decisions. n515 It makes sense that this courageous judge (who also ruled against the Government in a major Guantanamo case n516) would extol the independence of the federal Judiciary, but perhaps those of us outside the club can be forgiven for seriously challenging his assessment. Meanwhile, critics are voicing the belief that recent appointments to the FISA Court will be even more deferential to the Executive. n517 To repeat, there is nothing "new" in the killing of innocents for religious or political vengeance. n518 This violence has always been with us and unfortunately will continue despite our best efforts to curb it. Pleas for Executive carte blanche power are exactly what judicial independence was developed to avoid, and what many statements in various declarations of human rights are all about. The way of unreviewed Executive discretion is the way of tyranny. The US has transitioned into authoritarianism – surveillance power coupled with the absence of judicial review eviscerates any possibility of democratic modeling Turley, 2012 (Jonathan, Shapiro professor of public interest law at George Washington University, “10 reasons the U.S. is no longer the land of the free,” http://jonathanturley.org/2012/01/15/10-reasonsthe-u-s-is-no-longer-the-land-of-the-free/) Below is today’s column in the Sunday Washington Post. The column addresses how the continued rollbacks on civil liberties in the United States conflicts with the view of the country as the land of the free. If we are going to adopt Chinese legal principles, we should at least have the integrity to adopt one Chinese proverb: “The beginning of wisdom is to call things by their right names.” We seem as a country to be in denial as to the implications of these laws and policies. Whether we are viewed as a free country with authoritarian inclinations or an authoritarian nation with free aspirations (or some other hybrid definition), we are clearly not what we once were. [Update: in addition to the column below, a later column in the Washington Post explores more closely the loss of free speech rights in the West]. Every year, the State Department issues reports on individual rights in other countries, monitoring the passage of restrictive laws and regulations around the world. Iran, for example, has been criticized for denying fair public trials and limiting privacy, while Russia has been taken to task for undermining due process. Other countries have been condemned for the use of secret evidence and torture. Even as we pass judgment on countries we consider unfree, Americans remain confident that any definition of a free nation must include their own — the land of free. Yet, the laws and practices of the land should shake that confidence. In the decade since Sept. 11, 2001, this country has comprehensively reduced civil liberties in the name of an expanded security state. The most recent example of this was the National Defense Authorization Act, signed Dec. 31, which allows for the indefinite detention of citizens. At what point does the reduction of individual rights in our country change how we define ourselves? While each new national security power Washington has embraced was controversial when enacted, they operate in isolation. They form a mosaic of powers under which our country could be considered, at least in part, authoritarian. Americans often proclaim our nation as a symbol of freedom to the world while dismissing nations such as Cuba and China as categorically unfree. Yet, objectively, are often discussed in isolation. But they don’t we may be only half right. Those countries do lack basic individual rights such as due process, placing them outside any reasonable definition of “free,” but the United States now has much more in common with such regimes than anyone may like to admit. These countries also have constitutions that purport to guarantee freedoms and rights. But their governments have broad discretion in denying those rights and few real avenues for challenges by citizens — precisely the problem with the new laws in this country. The list of powers acquired by the U.S. government since 9/11 puts us in rather troubling company. Assassination of U.S. citizens President Obama has claimed, as President George W. Bush did before him, the right to order the killing of any citizen considered a terrorist or an abettor of terrorism. Last year, he approved the killing of U.S. citizen Anwar al-Awlaqi and another citizen under this claimed inherent authority. Last month, administration officials affirmed that power, stating that the president can order the assassination of any citizen whom he considers allied with terrorists. (Nations such as Nigeria, Iran and Syria have been routinely criticized for extrajudicial killings of enemies of the state.) Indefinite detention Under the law signed last month, terrorism suspects are to be held by the military; the president also has the authority to indefinitely detain citizens accused of terrorism. While Sen. Carl Levin insisted the bill followed existing law “whatever the law is,” the Senate specifically rejected an amendment that would exempt citizens and the Administration has opposed efforts to challenge such authority in federal court. The Administration continues to claim the right to strip citizens of legal protections based on its sole discretion. (China recently codified a more limited detention law for its citizens, while countries such as Cambodia have been singled out by the United States for “prolonged detention.”) Arbitrary justice The president now decides whether a person will receive a trial in the federal courts or in a military tribunal, a system that has been ridiculed around the world for lacking basic due process protections. Bush claimed this authority in 2001, and Obama has continued the practice. (Egypt and China have been denounced for maintaining separate military justice systems for selected defendants, including civilians.) Warrantless searches The president may now order warrantless surveillance, including a new capability to force companies and organizations to turn over information on citizens’ finances, communications and associations. Bush acquired this sweeping power under the Patriot Act in 2001, and in 2011, Obama extended the power, including searches of everything from business documents to library records. The government can use “national security letters” to demand, without probable cause, that organizations turn over information on citizens — and order them not to reveal the disclosure to the affected party. (Saudi Arabia and Pakistan operate under laws that allow the government to engage in widespread discretionary surveillance.) Secret evidence The government now routinely uses secret evidence to detain individuals and employs secret evidence in federal and military courts. It also forces the dismissal of cases against the United States by simply filing declarations that the cases would make the government reveal classified information that would harm national security — a claim made in a variety of privacy lawsuits and largely accepted by federal judges without question. Even legal opinions, cited as the basis for the government’s actions under the Bush and Obama administrations, have been classified. This allows the government to claim secret legal arguments to support secret proceedings using secret evidence. In addition, some cases never make it to court at all. The federal courts routinely deny constitutional challenges to policies and programs under a narrow definition of standing to bring a case. War crimes The world clamored for prosecutions of those responsible for waterboarding terrorism suspects during the Bush administration, but the Obama administration said in 2009 that it would not allow CIA employees to be investigated or prosecuted for such actions. This gutted not just treaty obligations but the Nuremberg principles of international law. When courts in countries such as Spain moved to investigate Bush officials for war crimes, the Obama administration reportedly urged foreign officials not to allow such cases to proceed, despite the fact that the United States has long claimed the same authority with regard to alleged war criminals in other countries. (Various nations have resisted investigations of officials accused of war crimes and torture. Some, such as Serbia and Chile, eventually relented to comply with international law; countries that have denied independent investigations include Iran, Syria and China.) Secret court The government has increased its use of the secret Foreign Intelligence Surveillance Court, which has expanded its secret warrants to include individuals deemed to be aiding or abetting hostile foreign governments or organizations. In 2011, Obama renewed these powers, including allowing secret searches of individuals who are not part of an identifiable terrorist group. The administration has asserted the right to ignore congressional limits on such surveillance. (Pakistan places national security surveillance under the unchecked powers of the military or intelligence services.) Immunity from judicial review Like the Bush administration, the Obama administration has successfully pushed for immunity for companies that assist in warrantless surveillance of citizens, blocking the ability of citizens to challenge the violation of privacy. (Similarly, China has maintained sweeping immunity claims both inside and outside the country and routinely blocks lawsuits against private companies.) Continual monitoring of citizens The Obama administration has successfully defended its claim that it can use GPS devices to monitor every move of targeted citizens without securing any court order or review. It is not defending the power before the Supreme Court — a power described by Justice Anthony Kennedy as “Orwellian.” (Saudi Arabia has installed massive public surveillance systems, while Cuba is notorious for active monitoring of selected citizens.) Extraordinary renditions The government now has the ability to transfer both citizens and noncitizens to another country under a system known as extraordinary rendition, which has been denounced as using other countries, such as Syria, Saudi Arabia, Egypt and Pakistan, to torture suspects. The Obama administration says it is not continuing the abuses of this practice under Bush, but it insists on the unfettered right to order such transfers — including the possible transfer of U.S. citizens. These new laws have come with an infusion of money into an expanded security system on the state and federal levels, including more public surveillance cameras, tens of thousands of security personnel and a massive expansion of a terrorist-chasing bureaucracy. Some politicians shrug and say these increased powers are merely a response to the times we live in. Thus, Sen. Lindsey Graham (R-S.C.) could declare in an interview last spring without objection that “free speech is a great idea, but we’re in a war.” Of course, terrorism will never “surrender” and end this particular “war.” Other politicians rationalize that, while such powers may exist, it really comes down to how they are used. This is a common response by liberals who cannot bring themselves to denounce Obama as they did Bush. Sen. Carl Levin (D-Mich.), for instance, has insisted that Congress is not making any decision on indefinite detention: “That is a decision which we leave where it belongs — in the executive branch.” And in a signing statement with the defense authorization bill, Obama said he does not intend to use the latest power to indefinitely imprison citizens. Yet, he still accepted the power as a sort of regretful autocrat. An authoritarian nation is defined not just by the use of authoritarian powers, but by the ability to use them. If a president can take away your freedom or your life on his own authority, all rights become little more than a discretionary grant subject to executive will. The framers lived under autocratic rule and understood this danger better than we do. James Madison famously warned that we needed a system that did not depend on the good intentions or motivations of our rulers: “If men were angels, no government would be necessary.” Benjamin Franklin was more direct. In 1787, a Mrs. Powel confronted Franklin after the signing of the Constitution and asked, “Well, Doctor, what have we got — a republic or a monarchy?” His response was a bit chilling: “A republic, Madam, if you can keep it.” Since 9/11, we have created the very government the framers feared: a government with sweeping and largely unchecked powers resting on the hope that they will be used wisely. The USA Freedom Act attempted reform, but it only institutionalizes NSA spying; it can’t solve the advantage Zeese, 2015 (Kevin, lawyer and privacy advocate, “Modest changes to US patrit act left major problems unresolved,” RT, June 1, http://rt.com/op-edge/263861-patriot-act-surveillance-snowden-usa/) Kevin Zeese: [Yesterday] the Senate basically decided to go forward with the USA Freedom Act, which will make some modest changes to the Patriot Act. The main change will be that the metadata will no longer be stored by the federal government or the NSA, rather it will be stored by the telephone companies, and then if the NSA wants to get access, they have to apply, and get a warrant from a judge to do so. So that is an improvement on a portion of the Patriot Act. We still have a major problem in the US of massive NSA snooping, and that’s really left unresolved. I supported Rand Paul’s effort, the Republican from Kentucky, to try to stop the Patriot Act from being renewed, and real rethinking of how we deal with this kind of intelligence gathering in the US and around the world; it is not just snooping in the US, but around the world as well. Unfortunately, I think the Senate is going to go forward with a modest change, a slight improvement. I guess you can look at that in two ways: it is a slight improvement, it is the first time the Patriot Act has lost any power, but it does also institutionalize the practice of this kind of snooping and provides now a new way of handling it and it combines corporate and government working together, which is always dangerous in the US. Supreme court action is key to restore global democracy – judicial independence is internationally modeled and checks authoritarianism caused by rising executive power Flaherty, 2008 (Martin S., Co-Director for International Law and Justice, Leitner Family Professor in International Human Rights, Fordham Law School; visiting Professor, Woodrow Wilson School of Public and International Affairs, Princeton University, “Globalization and Executive power,” Internationall Human rights Colloquium at Georgetown Law, Spring, http://www.law.georgetown.edu/internationalhrcolloquium/documents/GEPLRev.doc) That “old-time” separation of powers should be enough to turn back any trend toward deference. The balance of this essay, however, offers one more which is at once more original and potentially the most powerful. Call this separation of powers in a global context – or “global separation of powers” for short. The premise is straightforward. It assumes, first, that globalization generally has resulted in a net gain in power not for judiciaries, but for the “political” branches – and above all for executives – within domestic legal systems. In other words, the growth of globalized transnational government networks has yielded an imbalance among the three (to four) Such an imbalance, among other things, poses a significant and growing threat for the protection of individual rights by domestic courts, whether on the basis of international or national norms. Yet is separation of powers analysis helps identify the problem, it also suggests the solution. If globalization has comparatively empowered executives in particular, it follows that fostering – rather than prohibiting – judicial globalization provides a parallel approach to help restore the balance. In this way, judicial separation of powers justifies judicial borrowing on both non-democratic and non-democratic grounds. From a non-democratic perspective, transnational judicial dialogue with reference to international law and parallel comparative questions gives major branches of government in separation of powers terms. national judiciaries a unique expertise on once aspect of foreign affairs, and so is a further exception to the usual presumption that the judiciary is the least qualified branch of government for the purposes of foreign affairs. More important, from a democratic point of view, restoring the balance that separation of powers seeks promotes self-government to the extent that separation of powers is itself seen as a predicate for any well-ordered form of democratic selfgovernment. Constitutional liberalism and respect for civil liberties is key to achieve democratic peace Tarzi, 2007 (Shah M., L. Morgan Chair of International Affairs, “Democratic peace, illiberal democracy, and conflict behavior,” International Journal on World Peace, Vol. XXIV, No. 4, December) The proposition that mature, stable "constitutionally liberal" democratic republics do not go to . war with each other is compelling. or dyadic peace, is ^his type of democracy implies also widespread in "constitutional liberalism," which, as international relations. Eareed Zakada has aptly stated, refers to "the tradition, deep in Western history, that seeks to protect an individual's autonomy and dignity against coercion, whatever the source—state, church, or society."^ A glance at Western democracies in North America and Western Europe today would have one readily conclude that mature "constitutional liberal" democracies are highly unlikely to initiate war with each other. The overwhelming majority of democracies today, however, can be characterized as young democracies, in most instances even as protodemocratic regimes, semi-democracies, or "illiberal democracies."^ This essay offers preliminary observations on the importance of the profound analytical and evidentiary divide between the mature "liberal constitutional" democracy and the other types. While war between liberal democracies is rare or less likely, electoral democracy does not necessarily lead to "liberal constitutionalism," and therefore it does not follow that these are as unlikely to engage in confiict with other democratic regimes. Without paying due attention to this divide, there is the danger that the rich body of empirical research may become a justification rather than an explanation for the mutual democratic pacifism thesis. This essay highlights the theoretical basis of democratic peace theory and the evidence offered to support the causal logic. Accordingly, the next section will refiect on the key normative and institutional explanations in support of this theory and present selective samples of empirical findings that buttress the causal link. Next, this article underscores some of the shortcomings of democratic peace and examine the challenges to the theory, including that posed by the realist critique. Thereaft:er, the study draws attention to several interpretive examples to illuminate the aforementioned propositions. The ultimate goal is to generate overall hypotheses that take into account the different types of democracies referenced above and thus present opportunity for additional systematic studies. THE DYADIC PATHWAY TO DEMOCRATIC PEACE There are two widelyoffered explanations regarding the causal logic for democratic war behavior and democratic peace. The normative explanation stresses the role of democratic political culture and shared democratic values and norms. Accordingly, common values, including respect for individual freedom, human rights, civil liberties, due process, and related broader shared beliefs about representative government are vital for explaining known facts regarding democratic behavior. According to William Dixon, one vital shared norm is the "normative guideline of bounded competition," that is, political leaders recognize the legitimacy of competing values and interests and are experienced in its exercise when international disputes involve democracies. "In situations where both parties to a dispute are democracies, not only do both sides subscribe to these norms, the leaders of botii are fully cognizant that bounded competition is the norm, both for themselves and for their opponents.'" Several authors, noted scholar Bruce Russet among them, emphasize tiic role of pacific settlement of disputes, reliance on negotiation, arriving at mutually acceptable compromise, and other elements of the democratic political culture. These attributes shape approaches to political dispute resolution amongst democratic states.'" Russet in particular notes the relevance of the norm of peaceful conflict resolution amongst democracies. This is a nineteenth century social norm that found application and confirmation in the World War II and Cold War alliances among Western democracies." Finally, a modern version of the classical Kantian formulation argues that a combination of factors such as the commitment of democratic governments to human rights, citizens' abhorrence of violence, the fact that citizens bear the cost of war, and the ability of citizens to constrain political leaders, together make it difficult for democratic governments to engage in war with other democracies.'^ This form of institution-building is the only way to prevent democratization from causing instability and war Owen, 2005 (John M., Associate Professor of Politics at the University of Virginia, “Iraq and the Democratic peace,” Foreign Affairs, Vol. 84, No. 6) The theory, which originated in the work of the eighteenth-century philosopher Immanuel Kant and was refined in the 1970s and 1980s by several researchers working independently, has, since the 1990s, been one of the hottest research areas in international relations. Although some skeptics remain and no one agrees about why exactly it works, most academics now share the belief that democracies have indeed made a separate peace. What is more, much research suggests that they are also unusually likely to sign and honor international agreements and to become economically interdependent. The administrations of Presidents George H.W. Bush and Bill Clinton made frequent appeals to the theory in public, and it seems to have informed their support for democratization in former communist lands and in Haiti. The current Bush administration, however, has gone much further in its faith in the idea, betting the farm that the theory holds and will help Washington achieve a peaceful, stable, and prosperous Muslim world as, over time, Iraq's neighbors, following Iraq's example, democratize. The United States' real motives for attacking Iraq may have been complex, but "regime change"-the replacement of Saddam Hussein's gruesome tyranny with a democracy-was central to Washington's rhetoric by the time it began bombing Baghdad in March 2003. Why has a president who set his defining policy around one of political science's crown jewels come in for so much venom from the same academics who endorse the idea? After all, a host of peer-reviewed journal articles have implicitly supported the president's claim that a democratic Iraq would not threaten the United States or Israel, develop weapons of mass destruction, or sponsor terrorism. Are professors simply perpetual critics who refuse to take responsibility for the consequences of their ideas? Or does Bush hatred trump social science? The Bush administration's desire to break with its predecessors and alter the authoritarian status quo in the Middle East was admirable. But the White House got its science wrong, or at least not completely right: the democratic peace theory does not dictate that the United States can or should remake Iraq into a democracy. In Electing to Fight: Why Emerging Democracies Go to War, the veteran political scientists Edward Mansfield and Jack Snyder make two critical points. Not only is turning authoritarian countries into democracies extremely difficult, much more so than the administration seems to have anticipated. The Middle East could also become a much more dangerous place if Washington and the rest of the world settle for a merely semi-democratic regime in Baghdad. Such an Iraq, Mansfield and Snyder imply, would be uncommonly likely to start wars--a bull in the Middle Eastern china shop. Unfortunately, such an Iraq may also be just what we are likely to end up with. ILLIBERAL DEMOCRACIES At first glance, the realists' critique of the Iraq war is easier to understand than that of the democratic peace theorists. Indeed, realism--which holds that a country's type of government has no systematic effects on its foreign policy--is enjoying a revival in Washington these days, precisely because of the war. According to the realists, the best way to have dealt with Saddam would have been not to overthrow him but to use coercive bargaining: to have threatened him with annihilation, for example, if he ever used nuclear weapons. Even the democratic peace theory, however, does not necessarily prescribe the use of force to transform despotisms such as Iraq into democracies. Indeed, by itself, the argument that democracies do not fight one another does not have any practical implications for the foreign policymaker. It needs an additional or minor premise, such as "the United States can make Iraq into a democracy at an acceptable cost." And it is precisely this minor premise about which the academy has been skeptical. No scholarly consensus exists on how countries become democratic, and the literature is equally murky on the costs to the United States of trying to force them to be free. This last part of the puzzle is even more complicated than it first appears. Enter Mansfield and Snyder, who have been contributing to the democratic peace debate for a decade. Their thesis, first published in 1995, is that although mature democracies do not fight one another, democratizing states--those in transition from authoritarianism to democracy-do, and are even more prone to war than authoritarian regimes. Now, in Electing to Fight, the authors have refined their argument. As they outline in the book, not only are "incomplete democratizing" states--those that develop democratic institutions in the wrong order--unlikely ever to complete the transition to democracy; they are also especially bellicose. According to Mansfield and Snyder, in countries that have recently started to hold free elections but that lack the proper mechanisms for accountability (institutions such as an independent judiciary, civilian control of the military, and protections for opposition parties and the press), politicians have incentives to pursue policies that make it more likely that their countries will start wars. In such places, politicians know they can mobilize support by demanding territory or other spoils from foreign countries and by nurturing grievances against outsiders. As a result, they push for extraordinarily belligerent policies. Even states that develop democratic institutions in the right order--adopting the rule of law before holding elections-are very aggressive in the early years of their transitions, although they are less so than the first group and more likely to eventually turn into full democracies. Of course, politicians in mature democracies are also often tempted to use nationalism and xenophobic rhetoric to buttress their domestic power. In such cases, however, they are usually restrained by institutionalized mechanisms of accountability. Knowing that if they lead the country into a military defeat or quagmire they may be punished at the next election, politicians in such states are less likely to advocate a risky war. In democratizing states, by contrast, politicians know that they are insulated from the impact of bad policies: if a war goes badly, for example, they can declare a state of emergency, suspend elections, censor the press, and so on. Politicians in such states also tend to fear their militaries, which often crave foreign enemies and will overthrow civilian governments that do not share their goals. Combined, these factors can make the temptation to attack another state irresistible. Mansfield and Snyder present both quantitative and case-study support for their theory. Using rigorous statistical methods, the authors show that since 1815, democratizing states have indeed been more prone to start wars than either democracies or authoritarian regimes. Categorizing transitions according to whether they ended in full democracies (as in the U.S. case) or in partial ones (as in Germany in 1871-1918 or Pakistan throughout its history), the authors find that in the early years of democratic transitions, partial democracies--especially those that get their institutions in the wrong order--are indeed significantly more likely to initiate wars. Mansfield and Snyder then provide several succinct stories of democratizing states that did in fact go to war, such as the France of Napoleon III (1852-70), Serbia between 1877 and 1914, Ethiopia and Eritrea between 1998 and 2000, and Pakistan from 1947 to the present. In most of these cases, the authors find what they expect: in these democratizing states, domestic political competition was intense. Politicians, wing for power, appeased domestic hard-liners by resorting to nationalistic appeals that vilified foreigners, and these policies often led to wars that were not in the countries' strategic interests. Although their argument would have been strengthened by a few comparative studies of democratizing states avoiding war and of flail democracies and authoritarian states starting wars, Mansfield and Snyder are persuasive. In part this is because they carefully circumscribe their claims. They acknowledge that some cases are "false positives," that is, wars started by states that have wrongly been classified as democratizing, such as the Iran-Iraq War, started by Iraq in 1980. They also answer the most likely objections to their argument. Some skeptics, for example, might counter that Mansfield and Snyder get the causality reversed: it is war or the threat of it that prevents states from becoming mature democracies. Others might argue that democratizing states become involved in more wars simply because their internal instability tempts foreign states to attack them--in other words, that democratizers are more sinned against than sinning. Analyzing data from 1816 through 1992, Mansfield and Snyder put paid to these alternative explanations. Bad domestic institutions usually precede wars, rather than vice versa, and democratizing states usually do the attacking. Where does Electing to Fight leave realism, the dominant theory of international conflict? The quantitative data support the realist claims that major powers are more likely to go to war than minor ones and that the more equal are the great powers, the more likely are wars among them. But democratization makes war more likely even after one takes these factors into account. Furthermore, the case studies suggest that democratizing states very often lose more than they gain from the wars they begin, which implies that they do not respond to international incentives as rationally as realism would expect. That said, notwithstanding its preference for viewing states from the inside, the Mansfield-Snyder theory is still "realist" in the general sense that it assumes that politicians and other actors are rationally self-interested. Their self-interest simply involves building and maintaining domestic power as well as external security--and sometimes trading some of the latter in order to gain the former. The authors' conclusions for foreign policy are straightforward. The United States and other international actors should continue to promote democracy, but they must strive to help democratizing states implement reforms in the correct order. In particular, popular elections ought not to precede the building of institutions that will check the baleful incentives for politicians to call for war. Mansfield and Snyder are unsparing toward well-intentioned organizations that have pressured authoritarian governments to rush to elections in the past--often with disastrous consequences. As the authors show, for example, it was organizations such as the World Bank and the National Democratic Institute that pushed Burundi and Rwanda to increase popular sovereignty in the early 1990s--pressure that, as Mansfield and Snyder argue, helped set off a chain of events that led to genocide. Acknowledging their intellectual debt to writers such as Samuel Huntington (particularly his 1968 book Political Order in Changing Societies) and Fareed Zakaria, Mansfield and Snyder have written a deeply conservative book. Sounding like Edmund Burke on the French Revolution but substituting statistics and measured prose for rhetorical power, the authors counsel against abruptly empowering people, since premature elections may well usher in domestic upheavals that thrust the state outward against its neighbors. Democracy is key to solve multiple existential risks Diamond, prof of pol sci, 95—prof of political science and sociology, Stanford. Senior research fellow at Hoover. (Larry, Promoting Democracy in the 1990s, http://wwwics.si.edu/subsites/ccpdc/pubs/di/1.html) Nuclear, chemical, and biological weapons continue to proliferate. The very source of life on Earth, the global ecosystem, appears increasingly endangered. Most of these new and unconventional threats to security are associated with or aggravated by the weakness or absence of democracy, with its provisions for legality, accountability, popular sovereignty, and openness. LESSONS OF THE TWENTIETH CENTURY The experience of this century offers important lessons. Countries that govern themselves in a truly democratic fashion do not go to war with one another. They do not aggress against their neighbors to aggrandize themselves or glorify their leaders. Democratic governments do not ethnically "cleanse" their own populations, and they are much less likely to face ethnic insurgency. Democracies do not sponsor terrorism against one another. They do not build weapons of mass destruction to use on or to threaten one another. Democratic countries form more reliable, open, and enduring trading partnerships. In the long run they offer better and more stable climates for investment. They are more environmentally responsible because they must answer to their own citizens, who organize to protest the destruction of their environments. Democracy incrementally reduces the risk of war and systemic harms Rummel, prof of pol sci, 7—BA from U Hawaii and PhD in pol sci from NU. Former prof, Yale and Indiana U. Prof of pol sci, U Hawaii (R.J., 9/7, Why Freedom? Let Me Count the Reasons, http://freedomspeace.blogspot.com/2007/09/why-freedom-let-me-count-reasons.html, AG) Democratically free people do not make war on each other Why? The diverse groups, cross-national bonds, social links, and shared values of democratic peoples sew them together; and shared liberal values dispose them toward peaceful negotiation and compromise with each other. It is as though the people of democratic nations were one society This truth that democracies do not make war on each other provides a solution for eliminating war from the world: globalize democratic freedom Second: The less free the people within any two nations are, the bloodier and more destructive the wars between them; the greater their freedom, the less likely such wars become And third: The more freedom the people of a nation have, the less bloody and destructive their wars What this means is that we do not have to As we promote freedom, as the people of more and more nations gain greater human rights and political liberties, as those people without any freedom become partly free, we will decrease the bloodiness of the world’s wars. We have already seen this in the sharp decrease in world violence with the great increase in the number of democracies. In short: wait for all, or almost all nations to become liberal democracies to reduce the severity of war. Increasing freedom in the world decreases the death toll of its wars. Surely, whatever reduces and then finally ends the scourge of war in our history, without causing a greater evil, must be a moral good. And this is freedom In conclusion, then, we have wondrous human freedom as a moral force for the good. Freedom produces social justice, creates wealth and prosperity, minimizes violence, saves human lives, and is a solution to war. In two words, it creates human security. Moreover, and most important: People should not be free only because it is good for them. They should be free because it is their right as human beings In opposition to freedom is power, its antagonist. While freedom is a right, the power to govern is a privilege granted by a people to those they elect and hold responsible for its use. Too often, however, thugs seize control of a people with their guns and use them to make their power total and absolute. Where freedom produces wealth and prosperity, such absolute power causes impoverishment and famine. Where freedom minimizes internal violence, eliminates genocide and mass murder, and solves the problem of war, such absolute power unleashes internal violence, murders millions, and produces the bloodiest wars. In short, power kills; absolute power kills absolutely. Advantage 2 – Legitimacy NSA metadata collection hurts US soft power – it’s used for propaganda by competitors Arkedis, 2013 (Jim, senior fellow at the Progressive Policy Institute, “PRISM is bad for American soft power,” The Atlantic, June 19, http://www.theatlantic.com/international/archive/2013/06/prism-is-badfor-american-soft-power/277015/) There was a foreign policy angle to Truman's civil rights awakening, too. In the ideological battle pitting democracy against communism, the Soviet Union began to churn out propaganda saying that Jim Crow proved America's inability to live up to its own fundamental values on human rights. The argument was effective, argues Caley Robertson of Colby University: segregation was frustrating the United States' attempts to export democracy during the Cold War. In other words, Jim Crow was damaging America's soft power, defined by Harvard professor Joseph Nye as a country's ability to achieve its aims through attraction rather than coercion. Which brings us to PRISM, the NSA program that collects meta-data from Americans' telephone and online communications. I am a former Department of Defense intelligence analyst. I have never used PRISM, and do not know if it existed during my tenure. However, I have used NSA databases, and became aware of two ironclad truths about the agency: First, its data is a critical intelligence tool; and second, that access to databases by non-NSA intelligence analysts is highly controlled. It's like buying drugs (so I'm told): you need "a guy" on the inside who passes you the goods in the shadows, then disavows any connection to you. In addition to being useful and tightly controlled, PRISM is, of course, legal by the letter of the law. Its existence is primarily justified by the "business records" clause in the PATRIOT Act, and President Obama has argued that the legislation has been authorized by "bipartisan majorities repeatedly," and that "it's important to understand your duly elected representatives have been consistently informed on exactly what we're doing." Salvation from excessive government snooping would seem to lie at the ballot box. Fair enough. But in the immediate wake of September 11, Americans questioned little of what their government would do to keep them safe. Just four months after the attacks in January 2002, Gallup reported that fully half of Americans would support anti-terrorism measures even if they violated civil liberties. Times have changed. As soon as August 2003, Gallup found just 29 percent of Americans were willing to sacrifice civil liberties for security. By 2009, a CBS poll concluded only 41 percent of Americans had even heard or read about the PATRIOT Act, and 45 percent of those believed the law endangered their civil liberties. A Washington Post poll from April 2013--after the Boston marathon attacks but before PRISM's disclosure-- found 48 percent of Americans feared the government would go too far in compromising constitutional rights to investigate terrorism. And following the Edward Snowden leaks, 58 percent were against the government collecting phone records. Not a total reversal, but certainly trending in one direction. This shift has existed in a vacuum of public debate. Prior to the PRISM leaks, the last time domestic government surveillance made headlines was in very late 2005 and early 2006, following revelations that the Bush administration was wiretapping Americans without a warrant. Despite the scandal, the PATRIOT Act was quickly reauthorized by March 2006. The Bush administration did announce the end of warrantless wiretapping in 2007, and he moved the program under jurisdiction of the FISA court , a panel of Supreme Courtappointed judges who approve domestic surveillance requests. To call the FISA court a rubber stamp is an understatement. This year, it has rejected a grand total of 11 warrant requests out of--wait for it--33,996 applications since the Carter administration. The PATRIOT Act's reauthorization wouldn't come up again until 2009. By then, public uproar over warrantless wiretapping had long since receded, and the year's debate played out as a relatively quite inside-baseball scuffle between civil liberties groups and the Hill. When the law came up for its next presidential signature in 2011, it was done quietly by autopen--a device that imitates Obama's John Hancock--from France. Shifting attitudes and quiet reauthorization flies in the face of the standard the president has set for himself. In a 2009 speech at the National Archives, Obama emphasized the importance of the consent of the governed in security affairs, "I believe with every fiber of my being that in the long run we cannot keep this country safe unless we enlist the power of our most fundamental values... My administration will make all information available to the American people so that they can make informed judgments and hold us accountable." The president's inability to live up to this ideal is particularly jarring as he defends PRISM. Following the leaks, he's said he is pushing the intelligence community to release what it can, and rightly insists that the NSA is not listening in on Americans' phone calls. Those are helpful steps, but should have been raised during the National Archives speech just months into his administration, not six months into his second term. Director of National Intelligence James Clapper continues to argue that disclosure of collection methods will give America's enemies a "'playbook' to avoid detection." That's thin gruel. First, America's enemies are already aware of the NSA's extensive electronic surveillance capabilities. That's why Osama Bin Laden and deceased al Qaeda in Iraq leader Abu Musab al Zarqawi used a complex network of couriers rather than electronic communications. It's typical operational security of truly dangerous operatives. Second, Obama stated as recently as late May that the threat from al Qaeda's core operatives has decreased significantly, shifting to less deadly cells scattered throughout the Middle East and North Africa. The lack of public debate, shifting attitudes towards civil liberties, insufficient disclosure, and a decreasing terrorist threat demands that collecting Americans' phone and Internet records must meet the absolute highest bar of public consent. It's a test the Obama administration is failing. This brings us back to Harry Truman and Jim Crow. Even though PRISM is technically legal, the lack of recent public debate and support for aggressive domestic collection is hurting America's soft power. The evidence is rolling in. The China Daily, an Englishlanguage mouthpiece for the Communist Party, is having a field day, pointing out America's hypocrisy as the Soviet Union did with Jim Crow. Chinese dissident artist Ai Wei Wei made the link explicitly, saying "In the Soviet Union before, in China today, and even in the U.S., officials always think what they do is necessary... but the lesson that people should learn from history is the need to limit state power." Even America's allies are uneasy, at best. German Chancellor Angela Merkel grew up in the East German police state and expressed diplomatic "surprise" at the NSA's activities. She vowed to raise the issue with Obama at this week's G8 meetings. The Italian data protection commissioner said the program would "not be legal" in his country. British Foreign Minister William Hague came under fire in Parliament for his government's participation. Unrestrained NSA surveillance undermines US soft power and prevents it from maintaining influence amid shrinking material power gap Quinn, 2013 (Adam, Senior lecturer in international politics at the University of Birmingham in Birmingham, Britain, “NSA revelations threaten Obama’s soft power and America’s global influence,” CSM, October 29, http://www.csmonitor.com/Commentary/Opinion/2013/1029/NSA-revelationsthreaten-Obama-s-soft-power-and-America-s-global-influence) For presidents, like sports-team managers, the tough weeks tend to outnumber the jubilant. But even by the standards of an unforgiving job, Barack Obama could be forgiven for feeling unusually buffeted of late. Many of the blows have come on the domestic front, with the all-consuming stand-off of the government shutdown segueing into frantic efforts to defend and repair the roll-out of Obamacare amid charges of fatal technological incompetence. But if he were tempted to seek solace in the autonomy of foreign policy – as modern presidents have been wont to do – there has been little consolatory triumph to be found. In August and September, he was caught in a mighty tangle over Syria, threatening military strikes over its chemical weapons use before being hamstrung first by Britain’s refusal to join the charge and then by the reluctance of his own Congress. The legacy of that mess continues to work itself out in unpredictable ways, such as increasingly public tensions between the United States and Saudi Arabia, hitherto one of its more solid allies. Though the eventual Russian-orchestrated deal to remove Syria’s chemical weapons was a respectable one given the circumstances, the episode as a whole spoke of an America straining to translate its power into influence, or to maintain, a united front among its friends. Recommended: 3 views on NSA reform Now the rolling scandal over National Security Agency (NSA) surveillance, triggered by the mass leak of secrets by Edward Snowden, has entered another phase of intensity, this time centered on Europe. Revelations that the US tapped the phone of German Chancellor Angela Merkel, operated numerous “listening posts” on European soil, and sucked up vast quantities of communications data from millions of citizens across Europe have broken in the press. Public expressions of displeasure have been forthcoming, including a European Union statement. Taken together, these vignettes of public dissension will be enough to make many ask the question: Is the US losing its influence even over its allies? Is this just a tricky moment for a particular president, or is it a harbinger of a broader trend? 3 views on NSA reform GALLERY Monitor Political Cartoons PHOTOS OF THE DAY Photos of the weekend Global shift First, the necessary caveats: Enduring alliance relationships resemble long marriages, in that the mere presence of moments of strain, or even audible arguments, cannot be taken as evidence of imminent separation. Looking back over the longer-term history of America’s relations with its allies, episodes such as the Vietnam War, the “Euromissile” crisis of the 1980s, and the controversial interventions in the former Yugoslavia in the 1990s demonstrate that sharp differences of opinion and conflicting priorities are no radical, new state of affairs. And however unhappy they may be with their recent treatment, it is not obvious that countries such as Germany, France, or Saudi Arabia have anywhere to go if they did decide the time had come to tout for alternative alliance partners. It is not entirely clear how European annoyance might manifest in ways that have practical importance. It is true the Europeans have it in their power to threaten progress on the Transatlantic Trade and Investment Partnership process, but it is not clear that such an action would harm the US more than Europe itself. In short, even if they are disgruntled, necessity may ultimately prove a sufficient force to help them get over it. The reason present friction between the US and its allies carries greater weight, however, is that it arises in the context of a global shift in power away from the US and its established allies and toward new powers. The prospect of “American decline” in terms of relative international power is the focus of a great deal of debate over both substance and semantics. But the central fact is that even the part of the US’s own intelligence apparatus charged with long-term foresight regards it as established that, within 20 years, the world will have transitioned from the “unipolar” American dominance of the first post-cold war decades to a world in which multiple centers of power must coexist. The center of economic gravity has already shifted markedly toward Asia during the last decade. This certainly does not mean any single new power is about to rise to replace the US as a hegemonic force. Nor does it mean the US will be going anywhere: The scale of its existing advantages across a range of fronts – military, economic, institutional – is sufficiently great that it is assured a prominent place at the table of whatever order may come. What it does mean is that Americans must presently be engaged in thinking carefully about how best to leverage their advantages to retain the maximum possible influence into the future. If they cannot continue to be first among equals in managing the world order, they will wish at least to ensure that order is one that runs in line with their own established preferences. Soft power Many of those who are optimistic about the ability of the US to pull off this project of declining power without declining influence place emphasis on two things: the extent to which the US has soft power due to widespread admiration for its political and cultural values, and the extent to which it has locked in influence through the extent of its existing networks of friends and allies. Even if these advantages cannot arrest America’s decline on harder metrics, if played properly, they can mitigate its consequences and secure an acceptable future. Shoring up support from like-minded countries such as those of Europe ought to be the low-hanging fruit of such an effort. So the current problems do harm on both fronts. It will be difficult to maintain the allure of soft power if global opinion settles on the view that American political discord has rendered its democracy dysfunctional at home, or that its surveillance practices have given rein to the mores of a police state. And it will be harder to preserve American status through the force of its alliances if its politicians' economic irresponsibility (for example, publicly contemplating a default on American national debt) or scandals over surveillance or drone strikes alienate their public or cause their leaders to question the extent to which they really are on the same side as the US. Restoration of judicial enforcement of constitutional norms is key to overall US legitimacy; this solves major power war Knowles, 2009 (Robert, Acting assistant Professor, New York University School of Law, “American Hegemony and the Foreign Affairs Constitution,” Arizona State Law Journal, 41 Ariz. St. L.J. 87, October) International relations scholars are still struggling to define the current era. The U.S.-led international order is unipolar, hegemonic, and, in some ways, imperial. In any event, this order diverges from traditional realist assumptions in important respects. It is unipolar, but stable. It is more hierarchical. The U.S. is not the same as other states; it performs unique functions in the world and has a government open and accessible to foreigners. And the stability and legitimacy of the system depends more on successful functioning of the U.S. government as a whole than it does on balancing alliances crafted by elite statesmen practicing realpolitik. “[W]orld power politics are shaped primarily not by the structure created by interstate anarchy but by the foreign policy developed in Washington.”368 These differences require a new model for assessing the institutional competences of the executive and judicial branches in foreign affairs. One approach would be to adapt an institutional competence model using insights from a major alternative theory of international relations – liberalism. Liberal IR theory generally holds that internal characteristics of states – in particular, the form of government – dictate states behavior, and that democracies do not go to war against one another.369 Liberalists also regard economic interdependence and international institutions as important for maintaining peace and stability in the world.370 Dean Anne-Marie Slaughter has proposed a binary model that distinguishes between liberal, democratic states and non-democratic states.371 Because domestic and foreign issues are “more convergent” among liberal democracies, Slaughter reasons, the courts should decide issues concerning the scope of the political branches’ powers.372 With respect to non-liberal states, the position of the U.S. is more “realist,” and courts should deploy a high level of deference.373 A strength of Dean Slaughter’s binary approach is that it would tend to reduce the uncertainty in foreign affairs adjudication. Professor Nzelibe has criticized this approach because it would put courts in the difficult position of determining which countries are liberal democracies.374 But even if courts are capable of making these determinations, they would still face the same dilemmas adjudicating controversies regarding non-liberal states. Where is the appropriate boundary between foreign affairs and domestic matters? How much discretion should be afforded the executive when individual rights and accountability values are at stake? To resolve these dilemmas, an institutional competence model should be applicable to foreign affairs adjudication across the board. In constructing a new realist model, it is worth recalling that the functional justifications for special deference are aimed at addressing problems of a particular sort of role effectiveness—which allocation of power among the branches will best achieve general governmental effectiveness in foreign affairs. In the 21st Century, America’s global role has changed, and the best means of achieving effectiveness in foreign affairs have changed as well. The international realm remains highly political—if not as much as in the past— but it is American politics that matters most. If the U.S. is truly an empire— and in some respects it is—the problems of imperial management will be far different from the problems of managing relations with one other great power or many great powers. Similarly, the management of hegemony or unipolarity requires a different set of competences. Although American predominance is recognized as a salient fact, there is no consensus among realists about the precise nature of the current international order.375 The hegemonic model I offer here adopts common insights from the three IR frameworks—unipolar, hegemonic, and imperial—described above. First, the “hybrid” hegemonic model assumes that the goal of U.S. foreign affairs should be the preservation of American hegemony, which is more stable, more peaceful, and better for America’s security and prosperity, than the alternatives. If the United States were to withdraw from its global leadership role, no other nation would be capable of taking its place.376 The result would be radical instability and a greater risk of major war.377 In addition, the United States would no longer benefit from the public goods it had formerly produced; as the largest consumer, it would suffer the most. Second, the hegemonic model assumes that American hegemony is unusually stable and durable.378 As noted above, other nations have many incentives to continue to tolerate the current order.379 And although other nations or groups of nations—China, the European Union, and India are often mentioned—may eventually overtake the United States in certain areas, such as manufacturing, the U.S. will remain dominant in most measures of capability for decades to come. In 2025, the U.S. economy is projected to be twice the size of China’s.380 The U.S. accounted for half of the world’s military spending in 2007 and holds enormous advantages in defense technology that far outstrip would-be competitors.381 Predictions of American decline are not new, and they have thus far proved premature.382 Third, the hegemonic model assumes that preservation of American hegemony depends not just on power, but legitimacy.383 All three IR frameworks for describing predominant states—although unipolarity less than hegemony or empire—suggest that legitimacy is crucial to the stability and durability of the system. Although empires and predominant states in unipolar systems can conceivably maintain their position through the use of force, this is much more likely to exhaust the resources of the predominant state and to lead to counter-balancing or the loss of control.384 Legitimacy as a method of maintaining predominance is far more efficient. The hegemonic model generally values courts’ institutional competences more than the anarchic realist model. The courts’ strengths in offering a stable interpretation of the law, relative insulation from political pressure, and power to bestow legitimacy are important for realizing the functional constitutional goal of effective U.S. foreign policy . This means that courts’ treatment of deference in foreign affairs will, in most respects, resemble its treatment of domestic affairs. Given the amorphous quality of foreign affairs deference, this “domestication” reduces uncertainty. The increasing boundary problems caused by the proliferation of treaties and the infiltration of domestic law by foreign affairs issues are lessened by reducing the deference gap. And the dilemma caused by the need to weigh different functional considerations—liberty, accountability, and effectiveness—against one another is made less intractable because it becomes part of the same project that the courts constantly grapple with in adjudicating domestic disputes. Wars from US hegemonic decline spread globally and go nuclear Kagan 7 (Robert, Senior Associate at the Carnegie Endowment for International Peace, “End of Dreams, Return of History” Policy Review, http://www.hoover.org/publications/policyreview/8552512.html#n10) This is a good thing, and it should continue to be a primary goal of American foreign policy to perpetuate this relatively benign international configuration of power. The unipolar order with the United States as the predominant power is unavoidably riddled with flaws and contradictions. It inspires fears and jealousies. The United States is not immune to error, like all other nations, and because of its size and importance in the international system those errors are magnified and take on greater significance than the errors of less powerful nations. Compared to the ideal Kantian international order, in which all the world's powers would be peaceloving equals, conducting themselves wisely, prudently, and in strict obeisance to international law, the unipolar system is both dangerous and unjust. Compared to any plausible alternative in the real world, however, it is relatively stable and less likely to produce a major war between great powers. It is also comparatively benevolent, from a liberal perspective, for it is more conducive to the principles of economic and political liberalism that Americans and many others value. American predominance does not stand in the way of progress toward a better world, therefore. It stands in the way of regression toward a more dangerous world. The choice is not between an American-dominated order and a world that looks like the European Union. The future international order will be shaped by those who have the power to shape it. The leaders of a post-American world will not meet in Brussels but in Beijing, Moscow, and Washington. The return of great powers and great games If the world is marked by the persistence of unipolarity, it is nevertheless also being shaped by the reemergence of competitive national ambitions of the kind that have shaped human affairs from time immemorial. During the Cold War, this historical tendency of great powers to jostle with one another for status and influence as well as for wealth and power was largely suppressed by the two superpowers and their rigid bipolar order. Since the end of the Cold War, the United States has not been powerful enough, and probably could never be powerful enough, to suppress by itself the normal ambitions of nations. This does not mean the world has returned to multipolarity, since none of the large powers is in range of competing with the superpower for global influence. Nevertheless, several large powers are now competing for regional predominance, both with the United States and with each other. National ambition drives China's foreign policy today, and the Chinese are powerfully motivated to return their nation to what they regard as its traditional position as the preeminent power in East Asia. although it is tempered by prudence and the desire to appear as unthreatening as possible to the rest of the world, They do not share a European, postmodern view that power is passé; hence their now two-decades-long military buildup and modernization. Like the Americans, they believe power, including military power, is a good thing to have and that it is better to have more of it than less. Perhaps more significant is the Chinese perception, also shared by Americans, that status and honor, Japan, meanwhile, which in the past could have been counted as an aspiring postmodern power -- with its pacifist constitution and low defense spending -- now appears embarked on a more traditional national course. Partly this is in reaction to the rising power of China and concerns about North Korea's nuclear weapons. But it is also driven by Japan's own national ambition to be a leader in East Asia or at least not and not just wealth and security, are important for a nation. to play second fiddle or "little brother" to China. China and Japan are now in a competitive quest with each trying to augment its own status and power and to prevent the other 's rise to predominance, and this competition has a military and strategic as well as an economic and political component. Their competition is such that a nation like South Korea, with a long unhappy history as a pawn between the two powers, is once again worrying both about a "greater China" and about the return of Japanese nationalism. As Aaron Friedberg commented, the East Asian Russian foreign policy, too, looks more like something from the nineteenth century. It is being driven by a typical, and typically Russian, blend of national resentment and ambition. A postmodern future looks more like Europe's past than its present. But it also looks like Asia's past. Russia simply seeking integration into the new European order, the Russia of Andrei Kozyrev, would not be troubled by the eastward enlargement of the EU and NATO, would not insist on predominant influence over its "near abroad," and would not use its natural resources as means of gaining geopolitical leverage and enhancing Russia 's international status in an attempt to regain the lost glories of the Soviet empire and Peter the Great. But Russia, like China and Japan, is moved by more traditional great-power considerations, including the pursuit of those valuable if intangible national interests: honor and respect. Although Russian leaders complain about threats to their security from NATO and the United States, the Russian sense of insecurity has more to do with resentment and national identity than with plausible external military threats. 16 Russia's complaint today is not with this or that weapons system. It is the entire postCold War settlement of the 1990s that Russia resents and wants to revise. But that does not make insecurity less a factor in Russia 's relations with the world; indeed, it makes finding India's regional ambitions are more muted, or are focused most intently on Pakistan, but it is clearly engaged in competition with China for dominance in the Indian Ocean and sees itself, correctly, as an emerging great power on the world scene. In the compromise with the Russians all the more difficult. One could add others to this list of great powers with traditional rather than postmodern aspirations. Middle East there is Iran, which mingles religious fervor with a historical sense of superiority and leadership in its region. 17 Its nuclear program is as much about the desire for regional hegemony as about defending Iranian territory from attack by the United States. Even the European Union, in its way, expresses a pan-European national ambition to play a significant role in the world, and it has become the vehicle for channeling German, French, and British ambitions in what Europeans regard as a safe supranational direction. Europeans seek honor and respect, too, but of a postmodern variety. The honor they seek is to occupy the moral high ground in the world, to exercise moral authority, to wield political and economic influence as an antidote to militarism, to be the keeper of the global conscience, and to be recognized and admired by others for playing this role. Islam is not a nation, but many Muslims express a kind of religious nationalism, and the leaders of radical Islam, including al Qaeda, do seek to establish a theocratic nation or confederation of nations that would encompass a wide swath of the Middle East and beyond. Like national movements elsewhere, Islamists have a yearning for respect, including self-respect, and a desire for honor. Their national identity has been molded in defiance against stronger and often oppressive outside powers, and also by memories of ancient superiority over those same powers. China had its "century of humiliation." Islamists have more than a century of humiliation to look back on, a humiliation of which Israel has become the living symbol, which is partly why even Muslims who are neither radical nor fundamentalist proffer their sympathy and even their support to violent extremists who can turn the tables on the dominant liberal West, and particularly on a dominant America which implanted and still feeds the Israeli cancer in their midst. Finally, there is the United States itself. As a matter of national policy stretching back across numerous administrations, Democratic and Republican, liberal and conservative, Americans have insisted on preserving regional predominance in East Asia; the Middle East; the Western Hemisphere; until recently, Europe; and now, increasingly, Central Asia. This was its goal after the Second World War, and since the end of the Cold War, beginning with the first Bush administration and continuing through the Clinton years, the United States did Even as it maintains its position as the predominant global power, it is also engaged in hegemonic competitions in these regions with China in East and Central Asia, with Iran in the Middle East and Central Asia, and with Russia in Eastern Europe, Central Asia, and the Caucasus. The United States, too, is more of a traditional than a postmodern power, and though Americans are loath to acknowledge it, they not retract but expanded its influence eastward across Europe and into the Middle East, Central Asia, and the Caucasus. generally prefer their global place as "No. 1" and are equally loath to relinquish it. Once having entered a region, whether for practical or idealistic reasons, they are remarkably slow to withdraw from it until they believe they have substantially transformed it in their own image. They profess indifference to the world and claim they just want to be left alone even as they seek daily to shape the behavior of billions of people around the globe. The jostling for status and influence among these ambitious nations and would-be nations is a second defining feature of the Nationalism in all its forms is back, if it ever went away, and so is international competition for power, influence, honor, and status. American predominance prevents these rivalries from intensifying -- its regional as well as its global predominance. Were the United States to diminish its influence in the regions where it is currently the strongest power, the other nations would settle disputes as great and lesser powers have done in the past: sometimes through diplomacy and accommodation but often through confrontation and wars of varying scope, intensity, and destructiveness. One novel aspect of such a multipolar world is that most of these powers would possess nuclear weapons. That could make wars between them less likely, or it could simply make them more catastrophic. It is easy but also dangerous to underestimate the role the United States plays in providing a measure of stability in the world even as it new post-Cold War international system. also disrupts stability. For instance, the United States is the dominant naval power everywhere, such that other nations cannot compete with it even in their home waters. They either happily or grudgingly allow the United States Navy to be the guarantor of international waterways and trade routes, of international access to markets and raw materials such as oil. Even when the United States engages in a war, it is able to play its role as guardian of the waterways. In a more genuinely multipolar world, however, it would not. Nations would compete for naval Conflict between nations would involve struggles on the oceans as well as on land. Armed embargos, of the kind used in World War I and other major conflicts, would disrupt trade flows in a way that is now impossible. Such order as exists in the world rests not merely on the goodwill of peoples but on a foundation dominance at least in their own regions and possibly beyond. provided by American power. Even the European Union, that great geopolitical miracle, owes its founding to American power, for without it the European nations after World War ii would Europe's stability depends on the guarantee, however distant and one hopes unnecessary, that the U nited S tates could step in to check any dangerous development on the continent. In a genuinely multipolar world, that would not be possible without renewing the danger of world war. People who believe greater equality among nations would be preferable to the present American predominance often succumb to a basic logical fallacy. They believe the never have felt secure enough to reintegrate Germany. Most Europeans recoil at the thought, but even today order the world enjoys today exists independently of American power. They imagine that in a world where American power was diminished, the aspects of international order that they like would remain in place. But that 's not the way it works. International order does not rest on ideas and institutions. It is shaped by configurations of power. The international order we know today reflects the distribution of power in the world since World War ii, and especially since the end of the Cold War. A different configuration of power, a multipolar world in which the poles were Russia, China, the United States, India, and Europe, would produce its own kind of order, with different rules and norms reflecting the interests of the powerful states that would have a hand in shaping it. Would that international order be an improvement? Perhaps for Beijing and Moscow it would. But it is doubtful that it would suit the tastes of enlightenment liberals in the Even under the umbrella of unipolarity, regional conflicts involving the large powers may erupt. War could erupt between China and Taiwan and draw in both the United States and Japan. War could erupt between Russia and Georgia, forcing the United States and its European allies to decide whether to intervene or suffer the consequences of a Russian victory. Conflict between India and Pakistan remains possible, as does conflict between Iran and Israel or other Middle Eastern states. These, too, could draw in other great powers, including the United States. Such conflicts may be unavoidable no matter what policies the United States pursues. But they are more likely to erupt if the U nited S tates weakens or withdraws from its positions of regional dominance. This is especially true in East Asia, where most nations agree that a reliable American power has a stabilizing and pacific effect on the region. That is certainly the view of most United States and Europe. The current order, of course, is not only far from perfect but also offers no guarantee against major conflict among the world's great powers. of China 's neighbors. But even China, which seeks gradually to supplant the United States as the dominant power in the region, faces the dilemma that an American withdrawal could unleash In Europe, too, the departure of the U nited S tates from the scene -- even if it remained the world's most powerful nation -- could be destabilizing. It could tempt Russia to an even more overbearing and potentially forceful approach to unruly nations on its periphery. Although some realist theorists seem to imagine that the disappearance of the Soviet Union put an end to the an ambitious, independent, nationalist Japan. possibility of confrontation between Russia and the West, and therefore to the need for a permanent American role in Europe, history suggests that conflicts in Europe involving Russia are If the United States withdrew from Europe -- if it adopted what some call a strategy of "offshore balancing" -- this could in time increase the likelihood of conflict involving Russia and its near neighbors, which could in turn draw the United States back in under unfavorable circumstances. It is also optimistic to imagine that a retrenchment of the American position in the Middle East and the assumption of a more passive, "offshore" role would lead to greater stability there. The vital interest the United States has in access to oil and the role it plays in keeping access possible even without Soviet communism. open to other nations in Europe and Asia make it unlikely that American leaders could or would stand back and hope for the best while the powers in the region battle it out. Nor would a more "even-handed" policy toward Israel, which some see as the magic key to unlocking peace, stability, and comity in the Middle East, obviate the need to come to Israel 's aid if its security became threatened. That commitment, paired with the American commitment to protect strategic oil supplies for most of the world, practically ensures a heavy American military presence in the In the Middle East, competition for influence among powers both inside and outside the region has raged for at least two centuries. The rise of Islamic fundamentalism doesn't change this. It only adds a new and more threatening dimension to the competition, which neither a sudden end to the conflict between Israel and the Palestinians nor an immediate American withdrawal from Iraq would change. The alternative to American pre dominance in the region is not balance and peace. It is further competition. The region and the states within it remain relatively weak. A diminution of American influence would not be followed by a diminution of other external influences. One could expect deeper involvement by both China and Russia, if only to secure their interests. 18 And one could also expect the more powerful states of the region, particularly Iran, to expand and fill the vacuum. It is region, both on the seas and on the ground. The subtraction of American power from any region would not end conflict but would simply change the equation. doubtful that any American administration would voluntarily take actions that could shift the balance of power in the Middle East further toward Russia, China, or Iran. The world hasn 't changed that much. An American withdrawal from Iraq will not return things to "normal" or to a new kind of stability in the region. It will produce a new instability, one likely to draw the United States back in again. The alternative to American regional predominance in the Middle East and elsewhere is not a new regional stability. In an era of burgeoning nationalism, the future is likely to be one of intensified competition among nations and nationalist movements. Difficult as it may be to extend American predominance into the future, no one should imagine that a reduction of American power or a retraction of American influence and global involvement will provide an easier path. Legitimacy independently solves multiple existential risks – key to global cooperation on security and the environment Stanley, security prof, 7 (Elizabeth Stanley, Ph.D. is an Assistant Professor of Security Studies in the Edmund A. Walsh School of Foreign Service and the Department of Government, 7 “International Perceptions of US Nuclear Policy” Sandia Report, http://www.prod.sandia.gov/cgi-bin/techlib/access-control.pl/2007/070903.pdf) How important is soft power, anyway? Given its vast conventional military power, does the United States even need soft power? Some analysts argue that US military predominance is both possible and desirable over the long term, and thus soft power is not important. But a growing consensus disagrees. These analysts argue that soft power is critical for four reasons. First, soft power is invaluable for keeping potential adversaries from gaining international support, for “winning the peace” in Afghanistan and Iraq, and for convincing moderates to refrain from supporting extremist terrorist groups. Second, soft power helps influence neutral and developing states to support US global leadership. Third, soft power is also important for convincing allies and partners to share the international security burden.14 Finally, and perhaps most importantly, given the increasing interdependence and globalization of the world system, soft power is critical for addressing most security threats the United States faces today. Most global security threats are impossible to be countered by a single state alone. Terrorism, weapons of mass destruction (WMD) proliferation, failed and failing states, conflicts over access to resources, are not confined to any one state. In addition, disease, demographic shifts, environmental degradation and global warming will have negative security implications as well.15 All of these potential threats share four traits: (1) they are best addressed proactively, rather than after they develop into full-blown crises; (2) they require multi-lateral approaches, often under the umbrella of an international institution; (3) they are not candidates for a quick fix, but rather require multi-year, or multi-decade solutions; and, (4) they are “wicked” problems. Given these four traits, soft power is critical for helping to secure the international, multi-lateral cooperation that will be necessary to address such threats effectively. Independently, excessive national security deference causes WMD terrorism and extinction – courts are key to stop it Knowles, 2010 (Robert, Visiting assistant professor of Chicago-Kent college of law, “Responses to the ten questions,” William Mitchell Law Review, 36 Wm. Mitchell L. Rev. 5061) Second, unipolarity increases the power of the U.S. executive branch, which faces fewer external constraints than it would in a world with several great powers balancing one another militarily.3 This became especially apparent with America's post-9/11 detention policies. At one time, the executive branch faced much more exogenous pressure from other great powers to comply with international law in the treatment of captured enemies. If the United States strayed too far from established norms, it would risk retaliation upon its own soldiers or other sanctions from powerful rivals. Today, there are few such constraints: enemies such as al Qaeda are not great powers in the traditional sense and are not likely to obey international law anyway. Instead, the danger is that American rule-breaking will undermine the legitimacy of U.S. leadership. America's military predominance enables it to set the rules of the game. When the United States breaks its own rules, it loses legitimacy. With U.S. legitimacy at stake, it follows that courts should be more, not less, active in national security cases. Courts are widely regarded as rule-based institutions, rather than political institutions, that can ensure that the political branches do not shortcircuit processes for changing the law or act to violate fundamental constitutional principles. The approval of courts lends legitimacy to government action. When other nations see the United States following the law, they are more likely to acquiesce in U.S. leadership. This makes this task of providing global public goods-such as fighting terrorism-easier for the United States. As the largest public-goods consumer, the United States benefits the most from perceptions of its own legitimacy. Legitimacy becomes especially important in view of declining U.S. influence relative to other powers. The world may not be multi-polar today, but it could be by mid-century. America's enormous military advantage will decrease over time, and its reduced share of global economic output will give it less ability to throw its weight around. Although the costs for the United States of disregarding international legal norms may seem worth it now, those costs will increase from year-to-year. To the extent that international institutionsincluding frameworks of international law-provide some "stickiness," the United States is better off investing its own legitimacy in these institutions now, while it has maximum influence. If the United States leaves its imprint on international law and institutions, they will be less costly for the United States to comply with in the future and much more costly for a rising rival, such as China, to ignore. Nonetheless, there are some who argue that we are already living in a multi-polar world, and that rogue states and terrorist groups like al Qaeda are our true rivals. Advances in technology will-if they do not already-enable terrorists or rogue states to deploy small nuclear and biological weapons to threaten American cities, making up in sheer mayhem what they lack in armies and navies. A nuclear explosion in a large metropolitan area-such as New York-has the potential to change life as we know it. In this sense, al Qaeda can be viewed as an existential threat. 9 However, the capacity for small groups to leverage extremism into great destruction does not alter the fundamental structure of geopolitics. Not all existential threats are the same. A nuclear device would be just as dangerous in the hands of a domestic group or a lone wolf as it would be in the hands of al Qaeda. It would be a mistake to assume that these new threats are best pursued by giving the executive branch greater deference. In fact, the dangers from terrorism make even clearer the need to adhere to established principles. The United States will occupy a global leadership role for decades to come. Successful management of global crises-including a catastrophic terrorist attack-lies not in counterbalancing rivals, but in better management of the international system. The United States cannot hope to tackle large-scale global problems-terrorism especially-if the rest of the world loses confidence in American leadership. The best way for courts to help carry out this task is to ensure that the political branches adhere to the rule of law. Judicial enforcement of constitutional principles are key to US soft power and solving terrorism Sidhu, 2011 (Dawinder S., attorney with a primary focus on the intersection of individual liberties and national security, “Judicial Review as Soft Power: How the courts can help us win the post-9/11 conflict,” National Security Law Brief, Volume 1, Number 1, http://digitalcommons.wcl.american.edu/cgi/viewcontent.cgi?article=1003&context=nslb) There can be little doubt that military victory overseas, at present, stands beyond the grasp of American’s long and powerful arm.22 Perhaps even more sobering is the fact that even if the United States was faring better on the military front, such success would be insuffi cient to prevail in the war. As the 9/11 Commission noted, al Qaeda “represents an ideological movement, not a fi nite group of people,” akin to a “decentralized force.”23 The American strategy, however, appears to be one based on warfare. Judge Richard A. Posner observed that “we have no strategy for defeating them, only fi ghting them.”24 President Obama’s foreign policy objectives in the war have been considered to be “exclusively military” and, on that score, the war “is not going well.”25 Put differently, the American efforts appear to be limited in scope and disappointing in that narrow subset of possible action against transnational terrorism. These facts are beyond dispute—in committing the terrorist atrocities on 9/11, al Qaeda provoked the United States into a war in Afghanistan that was expanded to Iraq. These confl icts are being waged primarily on the military arena, and the achievement of American goals in both arenas has been frustrated despite years of effort, billions of dollars, and the lives of many American soldiers. What can we do differently? What other instruments are available to the United States such that defeating—not just capably fi ghting—the terrorists may be a closer prospect? Specifi cally, how can American law be an advantage to our national security? This Article seeks to answer these questions. In this Article, I will argue that the American response to Islamic terrorist factions must move outside the military sphere in which battles are fought between arms and men to a more conceptual contest for hearts and minds, where the ammunition in this abstract war will be fundamental American principles, particularly a constitutional commitment to the rule of law, and where advancements in the war will be based on incrementally increased attraction to America. This approach will speak to one’s will and conscience in an effort to secure a more lasting respite from the ongoing struggles that have no foreseeable end in sight, have been attended by suffering and sorrow, and have claimed a growing number of victims on all sides.26 Part I will distinguish between “hard power,” which generally constitutes the ability to attain favorable foreign policy outcomes by way of military force or economic coercion, and “soft power,” defi ned as the ability to achieve those outcomes by way of attraction.27 Though soft power generally is thought to include a nation’s values, social norms, and culture, academic studies have not fully demonstrated that a nation’s legal dimensions—specifi cally its legal institutions and adherence to the rule of law—are also a form of soft power.28 This part will attempt to make this showing, citing to aspects of the American constitutional design that may be attractive to people of other communities, including Muslims.29 The legal principles established by the Framers and enshrined in the Constitution are a source of attraction only if we have meaningfully adhered to them in practice. Part II will posit that the Supreme Court’s robust evaluation of cases in the wartime context suggests that the nation has been faithful to the rule of law even in times of national stress. As support, this part will provide examples of cases involving challenges to the American response to wars both before and after 9/11, the discussion of which will exhibit American respect for the rule of law. While the substantive results of some of these cases may be particularly pleasing to Muslims, for instance the extension of habeas protections to detainees in Guantánamo,30 this part will make clear that it is the legal process—not substantive victories for one side or against the government—which is the true source of American legal soft power. If it is the case that the law may be an element of soft power conceptually and that the use of the legal process has refl ected this principle in practice, the conclusion argues that it would benefi t American national security for others in the world to be made aware of the American constitutional framework and the judiciary’s activities related to the war. Such information would make it more likely that other nations and peoples, especially moderate Muslims, will be attracted to American interests. This Article thus reaches a conclusion that may seem counterintuitive—that the judicial branch, in the performance of its constitutional duty of judicial review, furthers American national security and foreign policy objectives even when it may happen to strike down executive or legislative arguments for expanded war powers to prosecute the current war on terror and even though the executive and legislature constitute the foreign policy branches of the federal government. In other words, a “loss” for the executive or legislature, may be considered, in truth, a reaffi rmation of our constitutional system and therefore a victory for the entire nation in the neglected but necessary post-9/11 war of ideas.31 As such, it is the central contention of this Article that the judicial branch is a repository of American soft power and thus a useful tool in the post-9/11 conflict. Advantage 3 – Privacy Court ruling on NSA metadata collection is the key to all privacy rights – upholding the program ensures chilling effect Barnett, 2015 (Randy, Carmack Waterhouse Professor of Legal Theory, Georgetown University Law Center; director, Georgetown Center for the Constitution, “Why the NSA data seizures are unconstitutional,” Harvard Journal of Law & Public Policy, Vol. 38, No. 1) Although the only surveillance program that has been challenged thus far concerns phone records,8 the principle offered to support this data seizure applies as well to all other business records of our dealings, including our credit card transactions. Indeed, in upholding the constitutionality of the program, Judge William Pauley of the Southern District of New York cited cases that held that "an individual has no constitutionally protected expectation of privacy" in bank records, records given to an accountant, subscriber information provided to an internet service provider, and information from a home computer that is transmitted over the Internet or by email.9 Imagine the chilling effect on liberty if everyone knew that the government is in possession of all this data about their private transactions on its super computers. The relationship between the citizens of the United States and their supposed agents or servants in government would be fundamentally reversed, turning We the People into mere subjects of our rulers. So there is a lot more at stake here than just this particular bulk data seizure program. With the challenge to the Affordable Care Act, we not only wanted to stop Obamacare from being implemented—which sadly we failed to do—we also wanted to defeat the limitless constitutional arguments that were being offered in its defense. In this effort, I am pleased to say we succeeded.10 Now, we need to think very hard about whether these blanket data seizure programs comport with the Fourth Amendment before, not after, the government decides it needs to seize data about every facet of our personal lives. Judicial ruling against Clapper is key to protect all electronic communication Adbo, 2014 (Alex, staff attorney in the ACLU’s speech, privacy, and Technology Project, “Is dragnet surveillance constitutional?” Jurist, March 26, http://jurist.org/hotline/2014/03/alex-abdo-nsa-cellsurveillance.php) Ever since Edward Snowden exposed the National Security Agency's (NSA) sweeping surveillance of US citizens and residents, our country has been engaged in a historic debate about privacy in the digital age. The centerpiece of that debate is a question that has the potential to shape the meaning of privacy in this country for decades to come: does the Constitution permit the NSA to collect the phone records of millions of innocent Americans every single day? The government thinks so, based on a US Supreme Court case from 1979 called Smith v. Maryland. Given the importance of that case to the ongoing debate, it's worth asking whether Smith actually answers the question raised by the NSA's unprecedented surveillance program. The question is important in part because it reflects a fundamental shift in the way that the intelligence agencies do their business: from targeted collection to bulk collection. However it is critical for yet another reason: at stake are not just our phone records, but every digital track we leave as we browse the internet, communicate with loved ones, or even just carry around our increasingly nosy phones. Should the NSA have access to all of that information every single day about every single American? Within a week of the disclosure of the NSA's phone-records program, the ACLU and others filed lawsuits challenging the program. Most recently, Senator Rand Paul joined the fray with a class action on behalf of all Americans. The challenges differ in various ways, but central to each is the key question of whether the Supreme Court effectively approved the dragnet collection of our phone records in Smith. Two federal judges have already issued dueling opinions on that question. One—Judge Richard J. Leon—declared what is perhaps intuitive to many: that bulk collection of the records of innocent Americans likely violates the Constitution, Smith notwithstanding. The other—Judge William H. Pauley III—countered that the phone-records program is unquestionably constitutional under Smith. So which is it? Does Smith justify the NSA's dragnet collection of every American's phone records (and perhaps every American's bank records, credit-card statements, and internet and email records)? The answer is "no." Here's why. In Michael Lee Smith Smith, the Baltimore police suspected that was making threatening and obscene phone calls to a woman he had robbed days earlier. To confirm their suspicions, they asked Smith's telephone company to install a "pen register" on his line to record the numbers he dialed. After just a few days, the pen register confirmed that, sure enough, Smith was the culprit. He was convicted, he appealed, and the Supreme Court for the first time faced the question of whether the warrantless use of a pen register on a criminal suspect violated the Constitution. The Supreme Court held that it did not, because—in the court's estimation—individuals do not expect privacy in the telephone numbers that they dial. That's what the Supreme Court held: that an individual had no expectation of privacy in the numbers that he dialed over the course of several days. Here's what the court did not hold: that the government may, therefore, record the phone numbers that every American dials for all time. The distinction is important. It confirms one predicate of Leon's ruling, that Smith does not—in the words (PDF) of the Foreign Intelligence Surveillance Court—"squarely control" the legality of the NSA's program. In other words, the Supreme Court simply has not decided whether the mass, suspicionless collection of millions of innocent Americans' phone records is constitutional. Of course, even the government concedes that the Supreme Court has not actually answered the precise question that the NSA's phone-records program raises. What it argues, instead, is that if you have no right to privacy in your phone records for a few days, you have no right to privacy in your phone records for five years. That is to say, the government argues that zero plus zero equals zero. Sounds reasonable, right? The problem is that our constitutional right to privacy is not a mathematical equation. Just as grains of sand piled up eventually form a mountain, so too can the accumulation of seemingly insignificant privacy invasions eventually trigger the Constitution's protections. The Supreme Court has made that clear on several occasions. Take the case of United States v. Knotts from 1983, which involved the use of a beeper to track the car of a suspected manufacturer of illicit drugs. Based in part on Smith, the Supreme Court held that the warrantless tracking of a suspect as he moves in public does not violate the Constitution, because Americans do not expect their public movements to remain private. Here's the critical part: the court made clear that its ruling on the tracking of a single person's location for a short period of time could not be mathematically converted into a formula for pervasive surveillance: [I]f such dragnet-type law enforcement practices ... should eventually occur, there will be time enough then to determine whether different constitutional principles may be applicable. In other words, dragnet surveillance is different. When it comes to privacy, zero plus zero does not always equal zero. And that makes sense. When you share bits and pieces of your private life with others, that's not the same as sharing everything with everyone all at once. If that logic sounds familiar, it's because the government uses precisely the same logic when it argues that seemingly innocuous details in classified reports cannot be disclosed lest they be combined into a "mosaic" that reveals far more than the sum of their parts. The Supreme Court confirmed this understanding of our privacy—that the mosaic is often more revealing than the individual tiles—just a few years ago in the landmark case United States v. Jones (PDF). In that case, five justices in two concurring opinions rejected the government's argument that the pervasive tracking of an individual's location in public is no different than the isolated beeper-tracking in Knotts. Some have argued that the Jones concurrences were just that: concurrences and not a majority opinion. However, that's beside the point. The five justices in Jones only confirmed what the Supreme Court made clear in 1983 in Knotts. If there were any doubt about that, you would only need to look to the appellate decision in Jones, which the Supreme Court eventually upheld. In that case (United States v. Maynard), the United States Court of Appeals D.C. Circuit (the very same court that will hear the government's appeal from Leon's ruling) held that cases like Smith and Knotts are relevant to the question of dragnet surveillance, but do not actually answer the question. In short, the constitutionality of the NSA's mass tracking of our phone calls is an open question, at least insofar as Supreme Court precedent is concerned. The real question is the one that has now divided the courts: whether dragnet surveillance is a simple extension of Smith or rather a radical departure from our values and from our Constitution. The answer to that question should be straightforward: the Constitution protects us from dragnet surveillance. Fourth amendment ruling is key to solve tech competitiveness and internet fracturing Dolan, 2013 (Ed, economist and educator with a Ph.D. from Yale University, “The fourth amendment and the economic spillover from NSA surveillance to e-commerce,” August 5, http://www.economonitor.com/dolanecon/2013/08/05/the-fourth-amendment-and-the-economicspillover-from-nsa-surveillance-to-e-commerce/) Violation of an inherent right is wrong in itself, whether or not the victim can prove actual damages. Still, as the founders knew, exposure to unreasonable searches and seizures can do real economic harm. That remains true today, as we can see from the case of e-commerce. The web has been abuzz with commentary on the effects of NSA surveillance on e-commerce. Consider, for example, an interesting exchange that began last week when Lynne Kiesling of Northwestern University posted a brief item on her blog, The Knowledge Problem. She began by noting that NSA surveillance is “much in the nature of the ‘general warrants’ that were the whole reason the authors of the Bill of Rights put the Fourth Amendment in there in the first place,” and then added: Make no mistake: this deep and broad US government surveillance diminishes trust not just in the federal government (as if there is any general trust in the federal government any more), but also in Internet companies — communications companies, ISPs, Apple, Google, Yahoo, Amazon, and so on. The economic implications of the deep and broad US government surveillance are profound. How much economic activity on the Internet will leave those companies? Will government surveillance be able to access substitutes for these companies in other countries, if substitutes come into being? Isn’t this going to cause the commercial Internet to shrink? The federal government may not have intended to stifle the role of the Internet as an economic value-creating commercial platform, but that consequence is almost certain. Kiesling’s contribution was reposted to Reddit, where a reader going by the screen name of Mkawick submitted this comment (slightly abbreviated here, with some acronyms spelled out in full): Working for a small company who does business by selling small games, we have recently added a new networking component to allow people to chat while in game, make purchases online, etc. We use highly sanitized data so that even if someone captures our entire database, putting it back together is nigh impossible. So recently we talked about moving our server to Amazon because of bandwidth and latency. But now with revelations of NSA, Amazon is no longer a viable option. We instead decided to host everything internally, behind pix, expand our infrastructure, and avoid the compromises that are sure to come as a result of the NSA backdoors that are ubiquitous. Every two days there is a new reveal from the NSA that they are invading users’ privacy even more or that they have some new back door previously unknown. Is my company an outlier… probably. However, I know other startups that are also gnashing their teeth similarly and opting to not use Amazon or Google because of that. Add to that Apple’s vulnerability revealed last week (the developer site was compromised and possibly all developer info was stolen) and going to the Cloud is not even a good idea anymore. . . . Add to this the fact that most growth in the economy starts with small companies (depending on how you do the numbers), and if a lot more small companies are opting to take the more “secure” route and avoid Amazon because of the NSA, then this means that the NSA is in effect creating a new market. Already, new secure email systems are popping up (hushmail.com), secure chat (tox.im), and docs and on and on. These NSA revelations are having a profound impact, and the older companies like Google (15 years old) and Yahoo (only 18 years old now) are going to struggle being shackled to US Government bureaucracy and the NSA. In other words, the long slide away from being able to do business has already started for these well-established companies. Even Microsoft (especially them) admitted putting backdoors into Windows, and last week, I began REALLY using linux … which I have only been tinkering with for 15 years now. In the same vein, John Naughton, writes in The Guardian that The days of the internet as a truly global network are numbered. It was always a possibility that the system would eventually be Balkanized, i.e. divided into a number of geographical or jurisdiction-determined subnets as societies such as China, Russia, Iran and other Islamic states decided that they needed to control how their citizens communicated. Now, Balkanization is a certainty. Commenting on the Naughton article, James Fallows of The Atlantic adds that Because of what the U.S. government assumed it could do with information it had the technological ability to intercept, American companies and American interests are sure to suffer in their efforts to shape and benefit from the Internet’s continued growth. American companies, because no foreigners will believe these firms can guarantee security from U.S. government surveillance American interests, because the United States has gravely compromised its plausibility as world-wide administrator of the Internet’s standards and advocate for its open, above-politics goals. . . . The real threat from terrorism has never been the damage it does directly, even through attacks as horrific as those on 9/11. The more serious threat comes from the overreaction, the collective insanity or the simple loss of perspective, that an attack evokes. Our government’s ambition to do everything possible to keep us “safe” has put us at jeopardy in other ways. The bottom line The bottom line is that the founders of our republic not only stood on solider moral ground than our present leaders, but they were also savvier about the practical reasons for insisting on observance of fundamental rights to life, liberty, and property. They did not insert a national security exception in the fourth amendment, or elsewhere in the Bill of Rights, not just because to do so would have been cowardly, but also because it would have been stupid to give the government that much rope. Our current spymasters are not that smart. They have tunnel vision: Get the bad guys at any cost, regardless of the constitution and regardless of the collateral damage. We saw that mentality in action a couple of years ago when the CIA sent an agent with cover as a polio vaccination worker to gather DNA samples at Bin Laden’s compound in Pakistan. When revealed, the ruse stoked Pakistani paranoia about vaccinations, already at a troubling level, to a fever pitch. They didn’t have to do it. It is highly unlikely that the choice of a different cover for the agent would have tipped the scales enough to let Bin Laden go free. What is certain, though, is that thousands of Pakistani kids will go unvaccinated, some of whom will die of polio or live a life of disability. Either our security folks didn’t think about those consequences, or more likely, they just didn’t care. Saving kids from polio is not their mandate, nor, they seem to think, is protecting the integrity of e-commerce. Some reader will object, of course, that Congress has authorized everything that NSA is doing. To the shame of our Congress, there is some truth in that. The real question, though, is whether the law under which NSA claims to act complies with the fourth amendment. Loss of technological leadership causes great power war Taylor, 04 [Mark, Professor of Political Science – Massachusetts Institute of Technology, “The Politics of Technological Change: International Relations versus Domestic Institutions”, 4-1, http://www.scribd.com/doc/46554792/Taylor] Technological innovation is of central importance to the study of international relations (IR), affecting almost every aspect of the sub-field. 2 First and foremost, a nation’s technological capability has a significant effect on its economic growth, industrial might, and military prowess; therefore relative national technological capabilities necessarily influence the balance of power between states, and hence have a role in calculations of war and alliance formation. Second, technology and innovative capacity also determine a nation’s trade profile, affecting which products it will import and export, as well as where multinational corporations will base their production facilities. 3 Third, insofar as innovation-driven economic growth both attracts investment and produces surplus capital, a nation’s technological ability will also affect international financial flows and who has power over them. 4 Thus, in broad theoretical terms, technological change is important to the study of IR because of its overall implications for both the relative and absolute power of states. And if theory alone does not convince, then history also tells us that nations on the technological ascent generally experience a corresponding and dramatic change in their global stature and influence, such as Britain during the first industrial revolution, the United States and Germany during the second industrial revolution, and Japan during Conversely, great powers which fail to maintain their place at the technological frontier generally drift and fade from influence on international scene. 6 This is not to suggest that technological innovation alone determines international politics, but rather that shifts in both relative and absolute technological capability have a major impact on i nternational r elations, and therefore need to be better understood by IR scholars. Indeed, the importance of technological innovation to international relations is seldom disputed by IR theorists. the twentieth century. 5 Technology is rarely the sole or overriding causal variable in any given IR theory, but a broad overview of the major theoretical debates reveals the ubiquity of technological causality. For example, from Waltz to Posen, almost all Realists have a place for technology in their explanations of international politics. 7 At the very least, they describe it as an essential part of the distribution of material capabilities technology is the very cornerstone of great power domination, and its transfer the main vehicle by which war and change occur in world politics . 8 Jervis tells us that the balance of offensive and defensive military technology affects the incentives for war. 9 Walt agrees, arguing that technological change can alter a state’s aggregate power, and thereby affect both alliance formation and the international balance of threats. 10 Liberals across nations, or an indirect source of military doctrine. And for some, like Gilpin quoted above, are less directly concerned with technological change, but they must admit that by raising or lowering the costs of using force, technological progress affects the rational attractiveness of international cooperation and regimes. 11 Technology also lowers information & transactions costs and thus increases the applicability of international institutions, a cornerstone of Liberal IR theory. 12 And in fostering flows of trade, finance, and information, technological change can lead to Keohane’s interdependence 13 or Thomas Friedman et al’s globalization. 14 Meanwhile, over at the “third debate”, Constructivists cover the causal spectrum on the issue, from Katzenstein’s “cultural norms” which shape security concerns and thereby affect technological innovation; 15 to Wendt’s “stripped down technological determinism” in which technology inevitably drives nations to form a world state. 16 However most Constructivists seem to favor Wendt, arguing that new technology changes people’s identities within society, and sometimes even creates new cross-national constituencies, thereby affecting international politics. 17 Of course, Marxists tend to see technology as determining all social relations and the entire course of history, though they describe mankind’s major fault lines as running between economic classes rather than nation-states. 18 Finally, Buzan & Little remind us that without advances in the technologies of transportation, communication, production, and war, international systems would not exist in the first place It escalates Paone, 09 [Chuck, 66th Air Base Wing Public Affairs for the US Air Force, 8-10-09, “Technology convergence could prevent war, futurist says,” http://www.af.mil/news/story.asp?id=123162500] The convergence of "exponentially advancing technologies" will form a "super-intelligence" so formidable that it could avert war, according to one of the world's leading futurists. Dr. James Canton, CEO and chairman of the Institute for Global Futures, a San Francisco-based think tank, is author of the book "The Extreme Future" and an adviser to leading companies, the military and other government agencies. He is consistently listed among the world's leading speakers and has presented to diverse audiences around the globe. He will address the Air Force Command and Control Intelligence, Survelliance and Reconnaissance Symposium, which will be held Sept. 28 through 30 at the MGM Grand Hotel at Foxwoods in Ledyard, Conn., joining Air Force Chief of Staff Gen. Norton Schwartz and a bevy of other The superiority of convergent technologies will prevent war," Doctor Canton said, claiming their power would present an overwhelming deterrent to potential adversaries. While saying that the U.S. will build these super systems faster and better than other nations, he acknowledged government and industry speakers. He offered a sneak preview of his symposium presentation and answered various questions about the future of technology and warfare in early August. " that a new arms race is already under way. "It will be a new MAD for the 21st century," he said, referring to the Cold War-era acronym for Mutually Assured Destruction, the idea that a nuclear first strike would trigger an rational nation states, considering this imminent technology explosion, will see the futility of nation-on-nation warfare in the near future. Plus there's the "socio-economic linking of the global market system." "The fundamental macroeconomics on the planet favor peace, security, capitalism and equally deadly response. It's commonly held that this knowledge has essentially prevented any rational state from launching a nuclear attack. Likewise, Doctor Canton said he believes prosperity," he said. Doctor Canton projects that nations, including those not currently allied, will work together in using these smart technologies to prevent non-state actors from engaging in disruptive and deadly acts. Doctor Canton and his team study and predict many things, but their main area of expertise -- and the one in which he's personally most interested -- is advanced and emerging technology. "I see that as the key catalyst of strategic change on the planet, and it will be for the next 100 years," he said. He focuses on six specific technology areas: "nano, bio, IT, neuro, quantum and robotics;" those he expects to converge in so powerful a way. Within the information technology arena, Doctor Canton said systems must create "meaningful data," which can be validated and acted upon. "Knowledge engineering for the analyst and the warfighter is a critical competency that we need to get our arms around," he said. "Having an avalanche of data is not going to be helpful." Having the right data is. "There's no way for As a futurist, the human operator to look at an infinite number of data streams and extract meaning," he said. "The question then is: How do we augment the human user with advanced artificial intelligence, better software presentation and better visual frameworks, to create a system that is situationally aware and can provide decision options for the human operator, faster than the human being can?" He said he believes the answers can often be found already in what he calls 'edge cultures.' "I would look outside of the military. What are they doing in video games? What are they doing in healthcare? What about the financial industry?" Doctor Canton said he believes more sophisticated artificial intelligence applications will transform business, warfare and life in general. Many of these are already embedded in systems or products, he says, even if people don't know it. that Economic crisis is the most likely cause of great power conflict Nader Elhefnawy 11, Professor of English at the University of Miami, writer on IR published in peerreviewed journals including International Security, Astropolitics, and Survival, Spring 2011, “Twenty Years After the Cold War: A Strategic Survey,” Parameters, The U.S. Army War College Quarterly, http://strategicstudiesinstitute.army.mil/pubs/parameters/Articles/2011spring/Ehlefnawy.pdf Relative calm has prevailed among the great powers since the demise of the Soviet Union. Large-scale warfare remains a possibility, but by and large interstate war has been confined to the margins of the international system, and limited in its intensity, with the operational realities of the world’s major armed forces characterized by alternative missions. Neoliberal globalization has been robust but economically problematic, characterized by slow growth, financial instability, and other factors contributing to social and political stress. East Asia, and especially China, constituted the principal exception to the slow growth characterizing these decades. East Asia has massively increased its share of world manufacturing, exports, and exchange reserves, while at the same time the EU expanded and consolidated the continent’s resources, with some “game-changing” implications (like the euro). Additionally, rising commodity prices have resulted in booms among resource exporters, particularly energy exporters, which have also permitted these nations to enjoy greater political leverage.¶ As a result, while the United States remains in a class of its own with regard to military power, and its large national market, there have been some substantial shifts in economic power from the United States and Japan to other actors over the past two decades. This is particularly true of China, the EU, and a select number of energy exporters, resulting in a more complex and diffuse distribution of power. At the same time the relationships of the major powers are less defined by concerns related to traditional, state-centered threats than at any time since the nineteenth century, if not earlier. While these may not be the traditional threats, they do present an unprecedented array of non-traditional security concerns in areas like energy, the environment, and finance , and physical threats presented by non-state actors, such as international terrorism and high-seas piracy. Despite these mounting threats, cooperation has consistently fallen short of the levels hoped for in the early 1990s.¶ Many of the current trends seem likely to continue through the foreseeable future. The interaction of the crises of the past several years (especially in energy and international finance) combined with long-mounting stresses in the global economy (slow growth, debt, ecological pressure) all raise the possibility of changes in some areas of development, particularly if these changes impact the world’s three principal loci of economic power: China, the European Union, and the United States. China may continue to grow rapidly, though perhaps less so as it matures, and begins to pursue goals beyond the mere maximizing of GDP. Even if the EU’s attempts at integration and expansion recede (as is plausible), Europe as a whole is likely to remain powerful, even if that power is less extensive and well-organized.¶ Meanwhile the US position is not unlike what the “declinists” of the 1980s and early 1990s anticipated. The most significant direct challenges to the United States some twenty years after the Cold War are not military, but economic: deindustrialization, balance of payments problems, debt, and surviving inside an ever-more integrated global economy and strained ecosystem. Relations among the great powers may yet grow more intense, but economic crisis seems the most likely cause of any future conflict, with the less traditional dimensions of security presenting the most realistic obstacles to the United States’ freedom of action if such events ever do materialize. Extinction Richard N. Haass 13, President of the Council on Foreign Relations, 4/30/13, “The World Without America,” http://www.project-syndicate.org/commentary/repairing-the-roots-of-american-power-byrichard-n--haass The most critical threat facing the United States now and for the foreseeable future is not a rising China, a reckless North Korea, a nuclear Iran, modern terrorism, or climate change. Although all of these constitute potential or actual threats, the biggest challenges facing the US are its burgeoning debt, crumbling infrastructure, second-rate primary and secondary schools, outdated immigration system, and slow economic growth – in short, the domestic foundations of American power. Readers in other countries may be Let me posit a radical idea: tempted to react to this judgment with a dose of schadenfreude, finding more than a little satisfaction in America’s difficulties. Such a response should not be surprising. The US and those representing it have been guilty of hubris (the US may often be the indispensable nation, but it would be better if others pointed this out), and examples of inconsistency between America’s practices and its principles understandably provoke charges of hypocrisy. When America does not adhere to the principles that it preaches to others, it breeds resentment. But, like most America’s failure to deal with its internal challenges would come at a steep price. Indeed, the rest of the world’s stake in American success is nearly as large as that of the US itself. Part of the reason is economic. The US economy still accounts for about one-quarter of global output. If US growth accelerates, America’s capacity to consume other countries’ goods and services will increase, thereby boosting growth around the world. At a time when Europe is drifting and Asia is slowing, only the US (or, more broadly, North America) has the potential to drive global economic recovery. The US remains a unique source of innovation. Most of the world’s citizens communicate with mobile devices based on temptations, the urge to gloat at America’s imperfections and struggles ought to be resisted. People around the globe should be careful what they wish for. technology developed in Silicon Valley; likewise, the Internet was made in America. More recently, new technologies developed in the US greatly increase the ability to extract oil and natural gas from underground formations. This technology is now making its way around the globe, allowing other societies to increase their energy production and decrease both their reliance on costly imports and their carbon emissions. The US is also an invaluable source of ideas. Its world-class universities educate a significant percentage of future world leaders. More the US has long been a leading example of what market economies and democratic politics can accomplish. People and governments around the world are far more likely to become more open if the American model is perceived to be succeeding. Finally, the world faces many serious challenges, ranging from the need to halt the spread of weapons of mass destruction, fight climate change, and maintain a functioning world economic order that promotes trade and investment to regulating practices in cyberspace, improving global health, and preventing armed conflicts. These problems will not simply go away or sort themselves out. While Adam Smith’s “invisible hand” may ensure the success of free markets, it is powerless in the world of geopolitics . Order requires the visible hand of leadership to formulate and realize global responses to global challenges. Don’t fundamentally, get me wrong: None of this is meant to suggest that the US can deal effectively with the world’s problems on its own. Unilateralism rarely works. It is not just that the US lacks the means; the multilateralism is much easier to advocate than to design and implement. Right now there is only one candidate for this role: the US. No other country has the necessary combination of capability and outlook. This brings me back to the argument that the US must put its house in order – economically, physically, socially, and politically – if it is to have the resources needed to promote order in the world . Everyone should hope that it does: The alternative to a world led by the US is not a world led by China, Europe, Russia, Japan, India, or any other country, but rather a world that is not led at all. Such a world would almost certainly be characterized by chronic crisis and conflict. That would be bad not just for Americans, but for the vast majority of the planet’s inhabitants. very nature of contemporary global problems suggests that only collective responses stand a good chance of succeeding. But Failure to curtail NSA surveillance causes internet fracturing and undermines the global structure Meinrath, 2013 (Sascha, vice president of the New America Foundation and director of the Open Technology Institute, “the future of the Internet: Balkanization and Borders,” October 11, http://ideas.time.com/2013/10/11/the-future-of-the-internet-balkanization-and-borders/) Brazilian President Dilma Rouseff’s recent indictment of the United States’ cyberspying practices has profound global repercussions for the U.S vision of a borderless, open Internet. What makes this backlash especially potent and lamentable is that it is being fueled not by democracies that oppose American ideals, but rather by allies that resent Washington’s betrayal of its own overarchingly positive vision. Advertisement Rouseff’s offensive to change Internet governance follows reports that the National Security Agency’s watchful eye could see as far as her Palácio do Planalto in Brasília. According to leaked documents, the United States has been surveilling Rousseff’s email, intercepting internal government communications, and spying on the country’s national oil company. After canceling an official visit to meet with President Obama in Washington, Rousseff took to the podium at the U.N.’s General Assembly to call on other countries to disconnect from U.S. Internet hegemony and develop their own sovereign Internet and governance structures. Rousseff’s move could lead to a powerful chorus—one that would transform the Internet of the future from a global commons to a fractured patchwork severely limited by the political boundaries on a map. Brazil is one of a handful of countries—including Indonesia, Turkey, and India—that have wavered in the debate over whether to develop an international framework to govern the Internet, one that would replace the role that the United States has played as chief Internet steward. Traditionally, that debate has featured America in the role as champion of a free and open Internet, one that guarantees the right of all people to freely express themselves. Arguing against that ideal: repressive regimes that have sought to limit connectivity and access to information. The NSA’s actions have shifted that debate, alienating key Internet-freedom allies and emboldening some of the most repressive regimes on the planet. Think of it as an emerging coalition between countries that object to how the United States is going about upholding its avowed principles for a free Internet, and countries that have objected to those avowed principles all along. Our close allies in the European Union, for instance, are now considering revoking datasharing agreements with the United States and requiring American website providers to prominently warn Europeans that their data is subject to U.S. government surveillance. Meanwhile, repressive regimes like Iran, Syria, and China are wresting control of information over their networks, poisoning popular applications and services, and undermining the foundations for the Internet’s open, interconnected structure. NSA misdeeds undoubtedly further embolden these regimes to do as they please. The motivations of those nations questioning America’s de facto control over the global Internet may vary, but their responses are all pointing in the same troubling direction: toward a Balkanized Internet. Today, the Internet is in danger of becoming like the European train system, where varying voltage and 20 different types of signaling technologies force operators to stop and switch systems or even to another locomotive, resulting in delays, inefficiencies, and higher costs. Netizens would fall under a complex array of different jurisdictions imposing conflicting mandates and conferring conflicting rights. And much as different signaling hampers the movement of people and the trade of physical goods, an Internet within such a complex jurisdictional structure would certainly hamper modern economic activity. The NSA has opened a Pandora’s box that treats “citizens” and “foreigners” differently (even defining both groups in myriad different ways). Its rules also impose geo-locational-based jurisdictional mandates (based upon the route of your Internet traffic or the location of the data services and databases you use). They also include requirements based upon ownership; the location of a company’s headquarters may lead to surveillance mandates covering services and infrastructure in other countries. This creates tremendous technical challenges for startups and entrepreneurs—who will have to overcome impossible compatibility hurdles just to get up and running—stifling innovation at a moment when we need greater economic momentum, not dead weight. Already, a German citizen accessing a New York City data center via a Chinese fiber line may find her data covered by an array of conflicting legal requirements requiring privacy and active surveillance at the same time. Fracturing the Internet undermines Internet freedom as well. The basic principle at the heart of Article 19 of the Universal Declaration of Human Rights—protecting the right to freedom of opinion, expression, and the opportunity to participate in the information society—is at risk. Brazil may not be pressing to assert control over everything online or censor its own people, or spy on them, but plenty of other countries with darker motives are cheering Brazil on. The U.S. has done a disservice to all people already living and working under repressive regimes by creating a new international norm that massive-scale surveillance is acceptable. As others adopt the U.S. model, particularly in areas where movements for fundamental freedoms are burgeoning and fighting against oppression, there will be even less access to basic communications, hampering the ability to interact online outside of the regime’s control and censorship. Furthermore, the NSA has made a remarkably myopic tradeoff—overreaching its legal authorities for a slight boost in signals intelligence today that will lead to massive problems in response. Even before all the recent revelations of NSA misbehavior, the United States was already facing calls for a more “democratic” global system of Internet regulation that gave other countries more say in setting rules. Now, for the sake of a free Internet, it is imperative for Washington to move fast to restore a belief that America is a trustworthy Internet steward. It’s time for bold leadership to defend our core principles. Reforms need to go far beyond pro-forma reviews carried out by intelligence and administration insiders. There are precedents for the United States’ exercising restraint in order to advance larger interests. As a country, we agreed to stop atmospheric testing of nuclear weapons, not to stockpile or deploy chemical weapons, and not to militarize outer space. There must be a cyberspace equivalent of this restraint—a restoration of balance that prioritizes civil rights, not surveillance, as vital to (inter)national security. Is the benefit of spying on Brazil’s oil company worth the cost of antagonizing the people of our hemisphere’s second-largest democracy and giving China and Russia the moral high ground in debates over how people around the world should access information? Do we really want a world where this behavior is normalized and where it’s acceptable for every country to surveil and hack indiscriminately? The answer to that question seems pretty clear. Today we need bold reforms from Washington—we need to curtail our unhealthy addiction to surveillance and covert hacking. Only by being radically transparent about the scope of current activities and ceasing activities that transgress national norms will we regain global trust and shift the rather bleak trajectory we are currently on. Free Internet failure causes extinction Eagleman 10 [David Eagleman is a neuroscientist at Baylor College of Medicine, where he directs the Laboratory for Perception and Action and the Initiative on Neuroscience and Law and author of Sum (Canongate). Nov. 9, 2010, “ Six ways the internet will save civilization,” http://www.wired.co.uk/magazine/archive/2010/12/start/apocalypse-no] Many great civilizations have fallen, leaving nothing but cracked ruins and scattered genetics. Usually this results from: natural disasters, resource depletion, economic meltdown, disease, poor information flow and corruption. But we’re luckier than our predecessors because we command a technology that no one else possessed: a rapid communication network that finds its highest expression in the internet. I propose that there are six ways in which the net has vastly reduced the threat of societal collapse. Epidemics can be deflected by telepresence One of our more dire prospects for collapse is an infectiousdisease epidemic. Viral and bacterial epidemics precipitated the fall of the Golden Age of Athens, the Roman Empire and most of the empires of the Native Americans. The internet can be our key to survival because the ability to work telepresently can inhibit microbial transmission by reducing human-to-human contact. In the face of an otherwise devastating epidemic, businesses can keep supply chains running with the maximum number of employees working from home. This can reduce host density below the tipping point required for an epidemic. If we are well prepared when an epidemic arrives, we can fluidly shift into a self-quarantined society in which microbes fail due to host scarcity. Whatever the social ills of isolation, they are worse for the microbes than for us. The internet will predict natural disasters We are witnessing the downfall of slow central control in the media: news stories are increasingly becoming user-generated nets of up-to-the-minute information. During the recent California wildfires,locals went to the TV stations to learn whether their neighbourhoods were in danger. But the news stations appeared most concerned with the fate of celebrity mansions, so Californians changed their tack: they uploaded geotagged mobile-phone pictures, updated Facebook statuses and tweeted. The balance tipped: the internet carried news about the fire more quickly and accurately than any news station could. In this grass-roots, decentralised scheme, there were embedded reporters on every block, and the news shockwave kept ahead of the fire. This head start could provide the extra hours that save us. If the Pompeiians had had the internet in 79AD, they could have easily marched 10km to safety, well ahead of the pyroclastic flow from Mount Vesuvius. If the Indian Ocean had the Pacific’s networked tsunami-warning system, South-East Asia would look quite different today. Discoveries are retained and shared Historically, critical information has required constant rediscovery. Collections of learning -- from the library at Alexandria to the entire Minoan civilisation -- have fallen to the bonfires of invaders or the wrecking ball of natural disaster. Knowledge is hard won but easily lost. And information that survives often does not spread. Consider smallpox inoculation: this was under way in India, China and Africa centuries before it made its way to Europe. By the time the idea reached North America, native civilisations who needed it had already collapsed. The net solved the problem. New discoveries catch on immediately; information spreads widely. is In this way, societies can optimally ratchet up, using the latest bricks of knowledge in their fortification against risk. Tyranny mitigated Censorship of ideas was a familiar spectre in the last century, with state-approved news outlets ruling the press, airwaves and copying machines in the USSR, Romania, Cuba, China, Iraq and elsewhere. In many cases, such as Lysenko’s agricultural despotism in the USSR, it directly contributed to the collapse of the nation. Historically, a more successful strategy has been to confront free speech with free speech -and the internet allows this in a natural way. It democratises the flow of information by offering access to the newspapers of the world, the photographers of every nation, the bloggers of every political stripe. Some posts are full of doctoring and dishonesty whereas others strive for independence and impartiality -- but all are available to us to sift through. Given the attempts by some governments to build firewalls, it’s clear that this benefit of the net requires constant vigilance. Human capital is vastly increased Crowdsourcing brings people together to solve problems. Yet far fewer than one per cent of the world’s population is involved. We need expand human capital. Most of the world not have access to the education afforded a small minority. For every Albert Einstein, Yo-Yo Ma or Barack Obama who has educational opportunities, uncountable others do not. This squandering of talent translates into reduced economic output and a smaller pool of problem solvers. The net opens the gates education to anyone with a computer. A motivated teen anywhere on the planet can walk through the world’s knowledge -- from the webs of Wikipedia to the curriculum of MIT’s OpenCourseWare. The new human capital will serve us well when we confront existential threats we’ve never imagined before. Energy expenditure is reduced Societal collapse can often be understood in terms of an energy budget:when energy spend outweighs energy return, collapse ensues. This has taken the form of deforestation or soil erosion;currently, the worry involves fossil-fuel depletion. The internet addresses the energy problem with a natural ease. Consider the massive energy savings inherent in the shift from paper to electrons -- as seen in the transition from the post to email.Ecommerce reduces the need to drive long distances to purchase products. Delivery trucks are more eco-friendly than individuals driving around, not least because of tight packaging and optimisation algorithms for driving routes. Of course, there are energy costs to the banks of computers that underpin the internet -- but these costs are less than the wood, coal and oil that would be expended for the same quantity of information flow. The tangle of events that triggers societal collapse can be complex, and there are several threats the net does not address. But vast, networked communication can be an antidote to several of the most deadly diseases threatening civilization. The next time your coworker laments internet addiction, the banality of tweeting or the decline of face-to-face conversation, you may want to suggest that the net may just be the technology that saves us. Democracy Advantage Uniqueness – Democraccy Global democracy is declining Mead, 2014 (Sir Walter Russell, professor of foreign affairs and humanities at Bard College and editor at large of the American Interest, “A strategy to Counter Democracy’s global retreat,” January 31, The Wall Street Journal, http://www.jackmillercenter.org/walter-russell-mead-world-needs-cheaptranslations-locke-et-al/) In Thailand, the streets are filled with demonstrators demanding the replacement of an elected government with an appointed council. In Egypt, the largest and most important Arab country, the 2011 revolution and much-ballyhooed “transition to democracy” ended in a military coup. President Obama’s lead-from-behind approach to Libya has ushered in anarchy, and Pakistan’s transition from one democratically elected set of powerless and corrupt politicians to another, widely cheered in Washington, has had no discernible positive impact on anything whatsoever. A democratically elected government in Hungary is flirting with fascists. Meantime, political reforms in Burma led to waves of religious violence against that country’s Muslim minority. And in Ukraine, protesters face off against a corrupt, elected government aligned withVladimir Putin. According to Freedom House’s 2014 Freedom in the World Report, 2013 was the eighth year in a row in which freedom lost ground. Yet the decade of freedom’s retreat was also a decade of unprecedented effort on the part of governments and nonprofit organizations to help freedom thrive. Between 2006 and 2012, the U.S. government alone spent $18.6 billion on democracy promotion, partly because of stepped up efforts in Afghanistan and the Middle East. This is a substantially higher rate of spending than during the post-Cold War years, when the former Warsaw Pact states were moving toward democracy. The gloomy prospects for democratic self-government in many parts of the world should not come as a surprise. Building democracy took generations in much of the Atlantic world, and most revolutions didn’t succeed in establishing stable democratic regimes. Some, like the Hungarians’ in 1848 and again in 1956, failed to hold power and were overthrown. Others, like the French and Russian Revolutions, gained power only to install dictatorships worse than the ones they overthrew. The South American revolutions against Spain, like many anti-colonial movements in the 20th century, succeeded against the imperial power—but then failed to build stable, democratic governments in its place. Egypt’s transition didn’t fail because Egypt’s democrats didn’t attend enough conferences on democracy building. It failed because the weight of their nation’s history, economics, religion and culture was too heavy for the relative handful of true democrats to lift. This should be a sobering lesson. While breakthroughs can sometimes occur, the construction of open, democratic systems in many countries around the world is likely to be slower and harder than many of us thought. Yes Modeling Supreme court is internationally modelled Kersch, 2004 (Ken L., Assistant Professor of Politics at Princeton University, “The 'Globalized Judiciary' and the Rule of Law,” The good Society, 13.3) The contemporary revival of globalist utopianism is distinctive from its 1940s precedessor in a crucial respect: it post-dates the U.S. Supreme Court's Brown v. Board of Education (1954) decision and the judge-led "rights revolution" it inaugurated. This revolution was closely followed, and proved highly influential around the world, inspiring many countries to accept the radical empowerment of their judiciaries at the expense of democratically elected legislatures. Whereas the traditional, post-war study of comparative constitutionalism was aimed at scholars and constitutional drafters, today comparative constitutionalists are speaking chiefly to lawyers and judges. Brown, the proliferation of litigation advocacy groups it inspired, and the rise of public law litigation, reversed the traditional progressive suspicion of judges as the (anti-democratic) handmaiden of economic elites and helped create the modern identification of judicial power with progress, civil liberties, and civil rights. The rise of Kantian legal theory, in turn, which envisaged the judge as the heroic tribune of universal morality, reinforced the moral authority - and, hence, political power - of the For various reasons, foreign judges, post-1989, found the judicialized American politics increasingly attractive as a model. The U.S. Supreme Court, the European Court of Justice ("ECJ") duly noted, had helped to nationalize American politics by gradually negotiating away key aspects of the sovereignty of the American states. Nations newly emerging from dictatorships, and countries paralyzed by legislative and executive sclerosis knew that the Warren Court (1953-1969) had broken the southern stranglehold on Congress in the name of unimpeachable national goals. Cognizant of this American success story, they turned optimistically to courts to break their own policy deadlocks and advance the causes of civil liberties and human rights. Unlike their American counterparts, however, these judges were not able to defend their assertiveness by appealing to a centuries-old tradition anchoring judicial review in constitutional popular sovereignty. Instead — and crucially — they anchored their claims to political power in their participation, as fellow professionals, in a global project involving the identification and protection of human rights, the stewardship of the "new" international law, and the technical improvement of the quality of constitutional reasoning generally through transnational professional consultation. For judges in nations that were not so long ago living in isolation and tyranny, drawing a demonstrable connection to a worldwide project involving a movement toward "global governance" became a key source of judicial legitimacy. For them, put otherwise, the process of "judicial globalization" was itself the sine qua non of the construction of judicial legitimacy. A feedback loop soon developed. After decades of sustained battering at home, which included major intellectual assaults on [End Page 18] their use of the doctrines of substantive due process and substantive equal protection to justify their assertiveness, American judges - and a wide array of political activists and legal academics interested in the aggrandizement of American judicial power - began to see the opportunities in connecting themselves to this worldwide movement by tapping in to its freshened wellsprings of legitimacy. The currently intense interest of scholars in the doings of judges worldwide is a direct outgrowth of this process. judge, and inflated his governing pretensions worldwide. Courts globally will model the CP and the new mechanism of treaty interpretation Kersch, 2004 (Ken L., Assistant Professor of Politics at Princeton University, “The 'Globalized Judiciary' and the Rule of Law,” The good Society, 13.3) Scholars of the emerging globalized judiciary have described a process that looks very much like that of bureaucratic formation at work amongst judges around the world. In charting the development of transnational judicial networks and support structures, Anne-Marie Slaughter, Andrew S. Tulumello, and Stepan Wood have suggested that "a wide range of possibilities exist for strengthening formal and informal links between international and domestic institutions in ways that blur the distinction between international and domestic law ...."7 As this process develops, she and her co-authors add, "it is possible that domestic institutions will become more interested in and receptive to their counterpart international institutions as they begin to perform the same functions horizontally rather then vertically." And, indeed, this is precisely what they observe happening amongst judges. "Domestic judges, at least in the United States," they add, "are beginning to articulate their responsibility to 'help the world's legal systems work together, in harmony, rather than at cross purposes.' Such cooperation includes not only procedural mechanisms of deference and collaboration, but also substantive evaluation of the degree of convergence between domestic and foreign law."8 This cooperation has been made possible by "a deep sense of participation in a common global enterprise of judging." "It [involves]," Slaughter asserts, "a vision of a global community of law, established not by the World Court in the Hague, but by national courts working together around the world."9 "Constitutional cross-fertilization," as Slaughter calls its, is a crucial part of this trend. Yes Modeling – SOP Plan spills over to affect separation of powers internationally – courts are globalized and share doctrine Flaherty, 2008 (Martin S., Co-Director for International Law and Justice, Leitner Family Professor in International Human Rights, Fordham Law School; visiting Professor, Woodrow Wilson School of Public and International Affairs, Princeton University, “Globalization and Executive power,” Internationall Human rights Colloquium at Georgetown Law, Spring, http://www.law.georgetown.edu/internationalhrcolloquium/documents/GEPLRev.doc) For the purposes of present analysis, however, by far the most important aspects of judicial globalization involve national courts use of comparative materials and international law – above all international human rights law. Ostensibly new and controversial in the United States, these aspects of globalization are familiar in most other jurisdictions. As noted, national, supreme, and appellate courts have with apparent frequency cited to comparable case law in other jurisdictions as at least persuasive authority to resolve domestic constitutional issues.108 Likewise, such courts also cite with increasing frequency the human rights jurisprudence of such transnational tribunals as the European Court of Human Rights and its Inter-American counterpart.109 In spectacular fashion, the House of Lords has recently been doing both.110 Likewise, the still-recent South African Constitution famously requires judges interpreting its Bill of Rights to consult international law and while expressly allowing them to consult “foreign,” i.e. So marked is the phenomenon that several comparative constitutional law casebooks that highlight such borrowing have carved out a significant market niche, even in the U.S. 112 It follows that in all these comparative law.111 ways the global interaction of judges strengthens their hands within their respective countries. In both theory and in the substance of these interactions, the bolstering of judiciaries generally works toward a greater protection of individual and minority rights. But while leading authorities view judicial globalization as outpacing its legislative counterpart, so too do they describe a world in which executive and regulatory interaction outpaces them all . To this extent, judicial globalization helps identify a problem yet also suggests a solution. The problem, simply, is that transgovernmental globalization taken as a whole draws power to national executive branches and away from rights-protecting judiciaries. Against this problem, the solution becomes fostering the judicial side of the phenomenon, particularly with regard to the use of comparative and international materials. US separation of powers spills over globally and prevents tyranny Flaherty, 2008 (Martin S., Co-Director for International Law and Justice, Leitner Family Professor in International Human Rights, Fordham Law School; visiting Professor, Woodrow Wilson School of Public and International Affairs, Princeton University, “Globalization and Executive power,” Internationall Human rights Colloquium at Georgetown Law, Spring, http://www.law.georgetown.edu/internationalhrcolloquium/documents/GEPLRev.doc) Alexander Hamilton, among the United States’ most cosmopolitan Founders, famously declared that, “[t]he truth is, after all the declamations we have heard, that the Constitution is itself, in every rational sense, and to every useful purpose, a Bill of Rights.”1 Among other things, this Hamilton had in mind separation of powers, including and especially an independent judiciary armed with judicial review. As his then alter-ego, James Madison, even more famously declared, “The accumulation of all powers, legislative, executive, and judiciary, in the same hands . . . may justly be pronounced the very definition of tyranny.” Then as now separation of powers has global implications. In the 18th century, Hamilton and his peers wrestled with the doctrine’s likely effects in foreign affairs as in domestic matters. An enhanced national legislature would now, for example, take the lead in regulating international trade. A stronger executive would better safeguard national security. An independent judiciary would help enforce the law of nations and so keep the republic at peace. Two hundred years later, the doctrine no longer simply has effects beyond U.S. borders, but transcends borders altogether . Most obviously, the doctrine has migrated abroad. Early on, nations around the world adopted some version of the U.S. separation of powers conceptions in modeling their own constitutions, a phenomenon that only accelerated with the decline of colonialism after World War II.3 Though usually overlooked, elements of the doctrine also inform key aspects of international human rights law, such as treaty provisions calling for legislative implementation of fundamental freedoms or mandating the protection of those freedoms by independent judicial bodies.4 JI Solves Democracy Judicial independence key to democracy John Ferejohn Carolyn S.G. Munro Professor of Political Science and Senior Fellow of the Hoover Institution, Stanford University. Visiting Professor of Law and Politics, New York University School of Law. “ INDEPENDENT JUDGES, DEPENDENT JUDICIARY: EXPLAINING JUDICIAL INDEPENDENCE” 72 S. Cal. L. Rev. 353 January / March, 19 99 What is the purpose of judicial independence in a constitutional democracy? In principle, judicial independence furthers three distinct values. First, a high degree of judicial independence seems a necessary condition for the maintenance of the rule of law - ensuring that everyone is subject to the same publicly communicated general legal rules. This concern suggests the necessity of making sure that powerful people - particularly elected officials - cannot manipulate legal proceedings to their advantage. Secondly, in a constitutional government, only those laws that are constitutionally legitimate ought to be enforced, and courts must be able to do much of the work in deciding which laws survive this test. Thus, there is a need to ensure that courts are sufficiently independent to overturn congressional statutes that subvert these values. Finally, in a democracy, it is important that constitutionally legitimate laws be given full effect. The worry here is that officials in the executive branch, or the cur [*367] rent legislature itself, may interfere in the enforcement of statutes enacted by previous legislatures without bothering to go through procedural formalities. In the interest of democracy, courts must have sufficient autonomy to resist the temptations to give too much deference to current holders of economic or political power. JI Good – Illiberal Backsliding Re-invigorated judicial independence sends a global signal- it's the only way to liberalize democratizing states. The Center for Justice and Accountability ’04 (Amici Curiae in support of petitioners in Al Odah et al. v USA, "Brief of the Center for Justice and Accountability, the International League for Human Rights, and Individual Advocates for the Independence of the Judiciary in Emerging Democracies," 3-10, http://www.jenner.com/files/tbl_s69NewsDocumentOrder/FileUpload500/82/AmiciCuriae_Center_for_ Justice_Int_League_Human_Rights_Adv_For_Indep_Judiciary2.PDF) Many of the newly independent governments that have proliferated over the past five decades have adopted these ideals. They have emerged from a variety of less-than-free contexts, including the end of European colonial rule in the 1950's and 1960's, the end of the Cold War and the breakup of the former Soviet Union in the late 1980's and 1990's, the disintegration of Yugoslavia, and the continuing turmoil in parts of Africa, Latin America and southern Asia. Some countries have successfully transitioned to stable and democratic forms of government that protect individual freedoms and human rights by means of judicial review by a strong and independent judiciary. Others have suffered the rise of tyrannical and oppressive rulers who consolidated their hold on power in part by diminishing or abolishing the role of the judiciary. And still others hang in the balance, struggling against the onslaught of tyrants to establish stable, democratic governments. In their attempts to shed their tyrannical pasts and to ensure the protection of individual rights, emerging democracies have consistently looked to the United States and its Constitution in fashioning frameworks that safeguard the independence of their judiciaries . See Ran Hirschl, The Political Origins of Judicial Empowerment through Constitutionalization: Lessons from Four Constitutional Revolutions, 25 Law & Soc. Inquiry 91, 92 (2000) (stating that of the “[m]any countries . . . [that] have engaged in fundamental constitutional reform over the past three decades,” nearly all adopted “a bill of rights and establishe[d] some form of active judicial review”). Establishing judicial review by a strong and independent judiciary is a critical step in stabilizing and protecting these new democracies. See Christopher M. Larkins, Judicial Independence and Democratization: A Theoretical and Conceptual Analysis, 44 Am. J. Comp. L. 605, 605-06 (1996) (describing the judicial branch as having "a uniquely important role" in transitional countries, not only to "mediate conflicts between political actors but also [to] prevent the arbitrary exercise of government power; see also Daniel C. Prefontaine and Joanne Lee, The Rule of Law and the Independence of the Judiciary, International Centre for Criminal Law Reform and Criminal Justice Policy (1998) ("There is increasing acknowledgment that an independent judiciary is the key to upholding the rule of law in a free society . . . . Most countries in transition from dictatorships and/or statist economies recognize the need to create a more stable system of governance, based on the rule of law."), available at http://www.icclr.law.ubc.ca/Publications/Reports/RuleofLaw. pdf (last visited Jan. 8, 2004). Although the precise form of government differs among countries, “they ultimately constitute variations within, not from, the American model of constitutionalism . . . [a] specific set of fundamental rights and liberties has the status of supreme law, is entrenched against amendment or repeal . . . and is enforced by an independent court . . . .” Stephen Gardbaum, The New Commonwealth Model of Constitutionalism, 49 Am. J. Comp. L. 707, 718 (2001). This phenomenon became most notable worldwide after World War II when certain countries, such as Germany, Italy, and Japan, embraced independent judiciaries following their bitter experiences under totalitarian regimes. See id. at 714- 15; see also United States v. Then, 56 F.3d 464, 469 (2d Cir. 1995) (Calabresi, J., concurring) (“Since World War II, many countries have adopted forms of judicial review, which — though different from ours in many particulars — unmistakably draw their origin and inspiration from American constitutional theory and practice. See generally Mauro Cappelletti, The Judicial Process in Comparative Perspective (Oxford: Clarendon Press, 1989).”). It is a trend that continues to this day. It bears mention that the United States has consistently affirmed and encouraged the establishment of independent judiciaries in emerging democracies. In September 2000, President Clinton observed that "[w]ithout the rule of law, elections simply offer a choice of dictators. . . . America's experience should be put to use to advance the rule of law, where democracy's roots are looking for room and strength to grow." Remarks at Georgetown University Law School, 36 Weekly Comp. Pres. Doc. 2218 (September 26, 2000), available at http://clinton6.nara.gov/2000/09/2000-09-26- remarks-bypresident-at-georgetown-international-lawcenter. html. The United States acts on these principles in part through the assistance it provides to developing nations. For example, the United States requires that any country seeking assistance through the Millenium Challenge Account, a development assistance program instituted in 2002, must demonstrate, among other criteria, an "adherence to the rule of law." The White House noted that the rule of law is one of the "essential conditions for successful development" of these countries. See http://www.whitehouse.gov/infocus/developingnations (last visited Jan. 8, 2004).12 Illiberal majoritarian transitions cause genocide and war Fareed Zakaria, PhD Poli Sci @ Harvard, Managing Editor of Foreign Affairs, 1997 (http://www.fareedzakaria.com/ ARTICLES/other/democracy.html) Lang's embarrassment highlights two common, and often mistaken, assumptions -- that the forces of democracy are the forces of ethnic harmony and of peace. Neither is necessarily true. Mature liberal democracies can usually accommodate ethnic divisions without violence or terror and live in peace with other liberal democracies. But without a background in constitutional liberalism, the introduction of democracy in divided societies has actually fomented nationalism, ethnic conflict, and even war. The spate of elections held immediately after the collapse of communism were won in the Soviet Union and Yugoslavia by nationalist separatists and resulted in the breakup of those countries. This was not in and of itself bad, since those countries had been bound together by force. But the rapid secessions, without guarantees, institutions, or political power for the many minorities living within the new countries, have caused spirals of rebellion, repression, and, in places like Bosnia, Azerbaijan, and Georgia, war. Elections require that politicians compete for peoples' votes. In societies without strong traditions of multiethnic groups or assimilation, it is easiest to organize support along racial, ethnic, or religious lines. Once an ethnic group is in power, it tends to exclude other ethnic groups. Compromise seems impossible; one can bargain on material issues like housing, hospitals, and handouts, but how does one split the difference on a national religion? Political competition that is so divisive can rapidly degenerate into violence. Opposition movements, armed rebellions, and coups in Africa have often been directed against ethnically based regimes, many of which came to power through elections. Surveying the breakdown of African and Asian democracies in the 1960s, two scholars concluded that democracy "is simply not viable in an environment of intense ethnic preferences." Recent studies, particularly of Africa and Central Asia, have confirmed this pessimism. A distinguished expert on ethnic conflict, Donald Horowitz, concluded, "In the face of this rather dismal account . . . of the concrete failures of democracy in divided societies . . . one is tempted to throw up one's hands. What is the point of holding elections if all they do in the end is to substitute a Bemba-dominated regime for a Nyanja regime in Zambia, the two equally narrow, or a southern regime for a northern one in Benin, neither incorporating the other half of the state?" Over the past decade, one of the most spirited debates among scholars of international relations concerns the "democratic peace" -- the assertion that no two modern democracies have gone to war with each other. The debate raises interesting substantive questions (does the American Civil War count? do nuclear weapons better explain the peace?) and even the statistical findings have raised interesting dissents. (As the scholar David Spiro points out, given the small number of both democracies and wars over the last two hundred years, sheer chance might explain the absence of war between democracies. No member of his family has ever won the lottery, yet few offer explanations for this impressive correlation.) But even if the statistics are correct, what explains them? Kant, the original proponent of the democratic peace, contended that in democracies, those who pay for wars -- that is, the public -- make the decisions, so they are understandably cautious. But that claim suggests that democracies are more pacific than other states. Actually they are more warlike, going to war more often and with greater intensity than most states. It is only with other democracies that the peace holds. When divining the cause behind this correlation, one thing becomes clear: the democratic peace is actually the liberal peace. Writing in the eighteenth century, Kant believed that democracies were tyrannical, and he specifically excluded them from his conception of "republican" governments, which lived in a zone of peace. Republicanism, for Kant, meant a separation of powers, checks and balances, the rule of law, protection of individual rights, and some level of representation in government (though nothing close to universal suffrage). Kant's other explanations for the "perpetual peace" between republics are all closely linked to their constitutional and liberal character: a mutual respect for the rights of each other's citizens, a system of checks and balances assuring that no single leader can drag his country into war , and classical liberal economic policies -- most importantly, free trade -- which create an interdependence that makes war costly and cooperation useful. Michael Doyle, th leading scholar on the subject, confirms in his 1997 book Ways of War and Peace that without constitutional liberalism, democracy itself has no peace-inducing qualities: Kant distrusted unfettered, democratic majoritarianism, and his argument offers no support for a claim that all participatory polities -- democracies -- should be peaceful, either in general or between fellow democracies. Many participatory polities have been non-liberal. For two thousand years before the modern age, popular rule was widely associated with aggressiveness (by Thucydides) or imperial success (by Machiavelli) . . . The decisive preference of [the] median voter might well include "ethnic cleansing" against other democratic polities. The distinction between liberal and illiberal democracies sheds light on another striking statistical correlation. Political scientists Jack Snyder and Edward Mansfield contend, using an impressive data set, that over the last 200 years democratizing states went to war significantly more often than either stable autocracies or liberal democracies. In countries not grounded in constitutional liberalism, the rise of democracy often brings with it hyper-nationalism and war-mongering. When the political system is opened up, diverse groups with incompatible interests gain access to power and press their demands. Political and military leaders, who are often embattled remnants of the old authoritarian order, realize that to succeed that they must rally the masses behind a national cause. The result is invariably aggressive rhetoric and policies, which often drag countries into confrontation and war. Noteworthy examples range from Napoleon III's France, Wilhelmine Germany, and Taisho Japan to those in today's newspapers, like Armenia and Azerbaijan and Milosevic's Serbia. The democratic peace, it turns out, has little to do with democracy. Illiberalism – Backsliding Now The vast majority of democracies are illiberal and young – only a risk of transitional conflicts now Tarzi 7 (Shah, Professor of Economic Affairs @ Bradley, Democratic Peace, Illiberal Democracy and Conflict Behavior, International Journal on World Peace, vol 24) The proposition that mature, stable "constitutionally liberal" democratic republics do not go to war with each other is compelling. This type of democracy implies "constitutional liberalism," which, as Fareed Zakaria has aptly stated, refers to "the tradition, deep in Western history, that seeks to protect an individual's autonomy and dignity against coercion, whatever the source--state, church, or society." (7) A glance at Western democracies in North America and Western Europe today would have one readily conclude that mature "constitutional liberal" democracies are highly unlikely to initiate war with each other. The overwhelming majority of democracies today, however, can be characterized as young democracies, in most instances even as proto-democratic regimes, semi-democracies, or "illiberal democracies." (8) This essay offers preliminary observations on the importance of the profound analytical and evidentiary divide between the mature "liberal constitutional" democracy and the other types. While war between liberal democracies is rare or less likely, electoral democracy does not necessarily lead to "liberal constitutionalism," and therefore it does not follow that these are as unlikely to engage in conflict with other democratic regimes. Without paying due attention to this divide, there is the danger that the rich body of empirical research may become a justification rather than an explanation for the mutual democratic pacifism thesis. Democratic backsliding now Beinart 7 (Peter, Senior fellow at the Council on Foreign Relations, Time.com: Is Freedom Failing?, http://www.time.com/time/magazine/article/0,9171,1619543,00.html) That was then. But when Nigerians went to the polls again last month, democracy lost. In an orgy of ballot-box stuffing and violence, punctuated by an attempted truck bombing of the electoral-commission headquarters, the ruling party won what some observers thought was the most fraudulent election ever in Nigeria--which is saying something. Once again, Nigeria is catching a wave. From Bangladesh to Thailand to Russia, political freedom is in retreat. In a book due out this fall, Hoover Institution political scientist Larry Diamond notes that "we have entered a period of global democratic recession." What happened? Iraq, for one. The U.S.'s war on terrorism was always a mixed blessing for democracy. President Bush says spreading freedom is key to preventing future terrorist attacks, but his own policies have made reform much harder. For Middle East dictators who equate democratization with chaos, Iraq has been a godsend. With anarchy threatening to engulf the region, the U.S. now needs dictators like Egypt's Hosni Mubarak and Saudi Arabia's King Abdullah more than they need us, which leaves us little leverage to push reform. When Secretary of State Condoleezza Rice went to Cairo in June 2005, she made Egyptian democracy the centerpiece of her trip. By the time Defense Secretary Robert Gates went there last month, he refused to discuss the topic at all. Then there's oil. As Thomas Friedman has noted, the price of crude and the tide of freedom tend to move in opposite directions. Before 9/11, the price per bbl. fluctuated between $20 and $30. Now it hovers between $50 and $65. And that's not likely to change anytime soon, given rising demand from China and India. That gives oil-producing autocracies such as Russia, Iran, Venezuela, Sudan and now Nigeria more money to crush or buy off internal dissent. And it makes it easier for them to win friends and influence people around the world. A decade ago, authoritarian governments were largely on the defensive. Today Venezuela's Hugo Chávez is cloning himself in Bolivia and Ecuador. And Iran is on the verge of dominating the Middle East. For democracy's future, these are real problems. But there's an even bigger one: democracy is not improving people's lives. In Bangladesh, among the most corrupt countries in the world, many were thrilled when the military seized power in January. By most accounts, Russians like how Vladimir Putin has ruled. And though Chávez is one of Latin America's least democratic leaders, he's also one of the most popular. In many countries that have embraced democracy since the cold war's end, free elections haven't reduced corruption, violence or poverty. When generals topple democratic governments or when autocrats like Putin or Chávez strangle them from within, they usually do so in the name of honest government and meat for dinner. And for people who have gone years without either, that sounds pretty good. Illiberalism – Liberal Democ = Stable Liberal democracies are peaceful Danilovic and Clare, associate professor of political science at the University at Buffalo and visiting assistant professor of political science at the University of Illinois at Urbana-Champaign, 2007 (Vesna and Joe, American Journal of Political Science, April, InterScience Online) It has been commonplace to identify the democratic peace research with the Kantian tradition, yet the main emphasis in this research is on the representative nature of electoral democratic institutions while largely ignoring the liberal elements of Kant's "republic" as a source of international peace. Like political theorists and Kantian scholars, we show that the respect for civil liberties and the rule of law— that is, liberal constitutionalism—represent even more fundamental elements of Kantian republicanism than procedural democratic institutions. While it is plausible to expect democracy and liberalism to be correlated, they are nevertheless theoretically and empirically distinct, and our reexamination of Kant's theory of the domestic sources for peace as well as our empirical analysis validate such a distinction. Consider, for example, the recent rise of new regimes, which are not merely transitional, but are rather being consolidated as "competitive" or "electoral" autocracies (Levitsky and Way 2002) or "illiberal democracies" (Zakaria 1997). These prima facie pass as democracies, yet do not score as high on the criteria of liberal constitutionalism. Our study shows that it would be erroneous, and certainly inconsistent with Kant's political theory, to conflate their external relations with liberal democracies simply because they share similar procedural institutions. Thus, when critics point to some conflicts such as that between Peru and Ecuador in the 1990s (e.g., Gates, Knutsen, and Moses 1996) as disputes that defy the democratic peace argument, our study shows that these are not necessarily disputes between liberal states (the cited conflict was actually between Fujimori's illiberal democracy and Ecuador's liberal state). This then reconfirms Kant's original penchant for civil liberties and rule of law as domestic solutions for peace. We first revisit Kant's notion of republic to delineate its constitutive elements—civil liberties and the rule of law, separation of powers, and representative governance—and show how all three are essential for Kant's reasoning behind the "liberal peace." Secondly, unlike previous studies that associate Kant's original argument with either the monadic claim that liberal states are peaceful in general, or dyadic ("separate peace") explanations for the democratic peace, we show that either expectation is consistent with his theory. Thirdly, we point to several levels of explanations concerning domestic sources for peace in Kant's writings, which are based on his dual understanding of motivations behind human actions—both moral and self-interested. This in turn means that, if we are to draw strictly from Kant, there are theoretical justifications for both norm-based and interest-based accounts for the democratic peace. Finally, we depart from the previous international relations literature that associates Kant's theory only with international peace and instead demonstrate that it is consistent with his theory to expect the decline in both international and civil wars with the rise of liberalism. We derive several propositions from our discussion of Kant's approach to liberalism and peace, which are then tested quantitatively. Our results reinforce the need for a careful differentiation between liberal constitutionalism and democratic representation as two related but also distinct aspects of what is referred to as "liberal democracy." We find evidence for both monadic and dyadic expectations for the liberal peace, and the results are more robust when based on the measures for liberalism rather than procedural democracy. Our results for domestic ("civil") peace point even to the opposite pattern. Only liberal states experience less civil wars than any other type of regime. On the other hand, if the states are measured on a strictly democratic scale—regardless of their respect for civil liberties—they are in fact more vulnerable to civil wars than are autocracies. We draw important theoretical implications from these findings. Ultimately, besides the theoretical contribution to the Kantian studies of peace, our analysis validates the caution about the peaceful expectations from the current rise of "new democracies," many of which turn out to be semi- or illiberal societies with different conflict propensities than established liberal democracies. Studies prove that liberal democracy solves both international and civil peace. Danilovic and Clare, associate professor of political science at the University at Buffalo and visiting assistant professor of political science at the University of Illinois at Urbana-Champaign, 2007 (Vesna and Joe, American Journal of Political Science, April, InterScience Online) In our study, we addressed theoretical and empirical gaps in the Kantian tradition in international relations. Our focus was on domestic sources of conflict in Kant's theory, and we showed that, although democracy is consistent with Kantian thinking, the most essential elements of his "republic" concern the protection of civil liberties, the separation of powers, and the rule of law as barriers to arbitrary rule. Our interpretation of Kant's republicanism is in agreement with Kantian political theorists (e.g., Ellis 2005; Rosen 1993), yet liberal governance has routinely been subordinated to electoral democracy in the democratic peace studies. The distinction we draw between procedural democratic rule and liberal governance is relevant both theoretically and empirically. Once we unpack Kant's republic in terms of constitutional liberal governance, we can uncover several levels of his reasoning behind the domestic sources for peace which were largely obscured in the previous studies. Not only do we find that monadic and dyadic views are consistent with Kant's theory, but also that both normative and interest-based explanations for international peace can equally draw on Kant as their theoretical precursor. We further demonstrate that, if we are to fully understand all constitutive elements of his republicanism, we can additionally infer that the Kantian legacy is related to a liberal civil peace as well. Though one of our primary goals was to provide a theoretical contribution to the Kantian tradition in international relations, we also examined its empirical validation. The results of our empirical analysis strongly support all hypotheses inferred from our reexamination of Kantian legacy. While the results are mixed for the "democratic peace"— international and domestic alike—the findings are robust and consistent with our theoretical expectations concerning the impact of constitutional liberalism on both international and civil "liberal peace." The compelling evidence in this study validates Doyle's (2005) recent response to the critics of democratic peace, especially those questioning its historical validity (e.g., Farber and Gowa 1995; Rosato 2003), that the verdict is still out as previous empirical studies have not incorporated "the principles of liberal individualism"—the heart of Kant's republic. As Doyle points out, while these might "evolve" with "democratic institutions,""we cannot be sure of this" (2005, 466), and thus the theory needs additional testing that separately codes a liberal component. We precisely provide such an analysis, casting doubt on the critics' rejection of liberal peace on the grounds of empirical invalidity , though our analytical aim extends well beyond this empirical task. Finally, our study is particularly relevant today. In the last "wave" of democratization, many states that are commonly categorized as democracies continue to have questionable records concerning the protection of individual freedoms, civil rights, and the rule of law against arbitrary rulings or policy implementations. Indeed, as our descriptive analysis indicates, there is a substantial group of states that fit into the category of semiliberal democracies. As comparative politics scholars point out, these are not transitional regimes, but rather consolidated systems that elude previous classifications, which typically conflate the liberal and democratic regime dimensions. Like comparativists, but from a very different—that is, Kantian—angle, we also caution against conflating liberal democracies and "hybrid regimes." At the same time, we have gone a step further to show the implications of analyses for conflict behavior. Our empirical analysis validates the caution against quick conclusions about the peaceful prospects for these new regimes. As demonstrated in our study, if the spread of democracy is indeed going to lead to international and domestic peace, it must be simultaneous with the full development of what was at the heart of Kant's republicanism, that is, constitutional liberal governance. JI Good – A/T Accountability Ending deference increases overall government accountability Knowles, 2009 (Robert, Acting assistant Professor, New York University School of Law, “American Hegemony and the Foreign Affairs Constitution,” Arizona State Law Journal, 41 Ariz. St. L.J. 87, October) The accountability justification generally overstates the degree to which courts are insulated from politics.286 On the domestic front, Supreme Court appointments have become an increasingly prominent issue in presidential elections, at least since Roe v. Wade and the nominations of Robert Bork and Clarence Thomas.287 Although foreign affairs have not played much of a role in these debates thus far, this is almost certainly due to the courts’ generally deferential approach to foreign relations controversies. When the courts have been bolder, such as in the three Guantánamo cases, they have captured the attention of policy-makers and the public, creating issues for presidential campaigns.288 Moreover, accountability cuts both ways. It is a core purpose of the separation of powers.289 The courts can serve an important information-forcing role that assists the People in holding the executive branch accountable for foreign affairs decisions, many of which are shrouded in secrecy.290 Court cases require the government to articulate clearly the rationales for its policies and the procedures through which those policies were enacted. Habeas corpus forces federal officers to justify their detention of individuals whose imprisonment would otherwise remain unscrutinized.291 In any event, assuming that the courts are relatively less accountable than the political branches, this aspect of the constitutional regime is accepted in the domestic context. Why should foreign affairs require faster and easier accountability ? Ultimately, the one-voice arguments for special deference— for uniformity, accountability, and avoiding embarrassment—must be grounded in assumptions about the peculiar requirements of managing a great power’s foreign policy in an anarchic world. These are considerations of realpolitik, which I discuss in the next subpart. JI Good – A/T Courts Not Transparent Turn – court opacity is key to deliberation and democracy Peters, 2000 (Christopher J., Assistant Professor of Law, Wayne state University Law School, “Assessing the new judicial minimalism,” Columbia Law review, 100 Colum. L. Rev. 1454, October) Deliberation is not necessarily promoted by transparency; indeed, it is frequently hindered by it. This is a point that Sunstein himself has made quite powerfully in the past. In The Partial Constitution, Sunstein sides with Madison against Jefferson in favor of the closing of the Constitutional Convention in 1787: On Madison's view, it was best "to sit with closed doors, because opinions were so various and at first so crude that it was necessary they should be long debated before any uniform system of opinion could be formed. Meantime the minds of the members were changing, and much was to be gained by a yielding and accommodating spirit... By secret discussion no man felt himself obliged to retain his opinions any longer than he was satisfied of their propriety and truth, and was open to the force of argument." n187 Indeed, the Federalists thought that opacity was necessary for true democratic deliberation. They distrusted open public discussion and, as James Martin has written, "believed that the public interactions and debates that are a part of any democracy should take place via the representative mechanisms that operate through the legal institutions of the state." n188 The relationship between the opacity and the quality of deliberation recently surfaced in the debate over whether the Senate, sitting as a court of impeachment in the trial of President Clinton, should deliberate publicly or behind closed doors. Some, like Iowa Senator Tom Harkin, opposed deliberations in "secret session" and argued that opening the debate "would send an important message. The public has a right to know how the Senate reaches its final decision on the removal or acquittal of the President." n189 Others, like Alabama Senator Richard Shelby, held a different view: "I think we explain[] to our constituents how we're going to vote as we vote and afterwards... But I believe that the deliberations ought to be like every jury in America, they ought to be behind closed [*1497] doors where we can be candid...." n190 In the end, those advocating open-door deliberations failed to achieve the two-thirds majority necessary to waive the Senate rule requiring secret debate. n191 Madison, Senator Shelby, and Sunstein himself have recognized that the glare of the public spotlight is not conducive to the candidness and openmindedness necessary to true deliberation. This is so for the same reasons that support representative rather than direct democracy: Public opinion may be raw, "based on inadequate information and on popular passions that are insufficiently influenced by reason-giving and understanding of context." n192 Exposing important decisions, and the processes of making them, to instantaneous and continuous public scrutiny threatens to infect representative democracy with the sorts of emotional, knee-jerk tendencies it was designed to avoid. n193 This is especially so when the decisions to be made involve not simply policy issues, but questions of individual rights against the majority. Writing of the dangers of referenda in the affirmative action context, Sunstein notes the risk that "outcomes will not be based on a careful assessment of facts and values, but instead on crude 'we-they' thinking." n194 This point can be generalized across all decisions involving individual rights. Questions of individual rights are inherently "we-they" affairs: The majoritarian "we" is pitted against the individual or minority "they." True deliberation about such questions - decisionmaking characterized by reason-giving, openness to opposing arguments, consideration of various relevant perspectives, and willingness to compromise - is made difficult from the start in the political system, where the ultimate decisionmakers, the citizens, by definition have something to gain or to lose. Deliberation is made all the more difficult when representatives are constantly bombarded, through public opinion polls and the ever-more-massive media, by the self-interests they are supposed to be filtering. n195 [*1498] The increasing transparency of politics stands in stark contrast to the opaque process of adjudicative decisionmaking. Only very rarely, as in the O.J. Simpson case, does the actual process of adjudication attract significant public attention. What publicity adjudication does draw invariably goes to the trial process, not to the appellate process, where law is made. Appellate court and Supreme Court proceedings are not televised, and only the results of those proceedings tend to receive publicity (and then only when they decide high-profile issues). And of course the actual deliberations of appellate courts invariably take place behind closed doors. It is true, and important, that the tools of Supreme Court deliberation - briefs filed by the parties, and transcripts or recordings of oral arguments - and the results of that deliberation - written opinions - usually are made public, more frequently and quickly than ever these days. But these sources only confirm the extent to which adjudication is meticulously deliberative. Legal briefs, oral arguments, and court opinions, unlike arguments made in the political realm, typically eschew entreaties to "public opinion" or "the public interest," instead replacing them with arguments based on the interpretation of legal authorities. Briefs, arguments, and opinions also typically address the reasoning both for and against the results they espouse. They are not allowed to be "supported by self-interest or force" n196 or to rely on "'naked preferences.'" n197 They are models of "reason-giving in the public domain." n198 The quoted phrases in the previous paragraph are taken from Sunstein's description of "deliberative democracy" in One Case at a Time. Remarkably, though, they describe the everyday adjudicative process much more accurately than they describe the everyday political process. n199 This is because the adjudicative process is, in these important ways, far more "deliberative" than politics typically can be. Part of the reason for this is the much- maligned isolationism of the law - its insulation from worldly affairs, its persistent formalism, its self-referential reliance only on appropriately pedigreed authorities. n200 Law in our system takes place behind [*1499] closed doors, away from the public spotlight and with little regard for it. And this opacity may work to the judiciary's advantage in attracting public trust; a recent survey indicates that the public has more "respect" for the Supreme Court than for the political branches. n201 It is strange, then, that Sunstein sees judicial review primarily as a tool for increasing the deliberativeness of the political branches. Much of the point of judicial review is that it is more deliberative than the political process, and thus better constituted to produce decisions that require deliberation above all else. As I explain in the next section, the adjudicative brand of deliberation does not lend itself to many kinds of decisionmaking that the political branches are good at. But it does lend itself to decisionmaking about individual rights - when they exist, what they look like, how far they ultimately extend. Decisions about individual rights are particularly poorly made in the spotlight, where they can be distorted by the very pressures that rights are meant to stand against. They are better made by courts, which can, in the current phrase, "fly under the radar" of public scrutiny. A/T Democracy Resilient Backsliding into illiberalism and authoritarianism is possible Pillar, 2012 (Paul R., “What America can learn from Hungary’s backsliding democracy,” The Atlantic, January 20, http://www.theatlantic.com/international/archive/2012/01/what-america-can-learn-fromhungarys-backsliding-democracy/251701/) This affair shows how even a country where liberal democratic principles seem to have been firmly established (and in this case a country that until now has been a member in good standing of the club of advanced democracies known as the European Union) may back away from consistent application of those principles. Democratization and liberalization are not necessarily one-way processes. To realize this goes against the tendency to think of them as a one-way process. Perhaps some of this tendency comes from interpretations of Francis Fukuyama's end-of-history idea. Perhaps we should remember the ideas of an earlier big-think political philosopher, Plato, about how different forms of government degenerate into other forms. Democracy, as Plato saw it, was not the end state of this process. It was the penultimate state, degenerating into tyranny. Plato's progression of political forms has not matched subsequent history very well, but it provides some food for thought about different possible types of political transformation. We see the common one-way view of political change in much current political thought and interpretations of current events. The Arab Spring, for example, is usually regarded as a push in the direction of greater democracy as long as the process doesn't get hijacked by those nasty Islamists. Apostles of regime change presume that destabilizing any undemocratic regime will result in a new political system that is freer and more democratic, even though that is not necessarily the case. And there is smugness about the endurance of democratic values in our own political system. The Democracy ReportWhat is going on in Hungary suggests that we should not be so smug. Some of what is involved in Hungary's creeping authoritarianism has echoes in American politics. There is the use of brute legislative force or outright coercion to get one's way, even if this in effect means a compromise of democratic values. And there is a hubristic belief that it is so important for one's own party or movement to be in power that this takes precedence over all other interpretations of the national interest. Viktor Orban has a soulmate of sorts in Mitch McConnell when the latter says his top priority is to defeat the president of the opposing party. Plan Solves Democracy NSA domestic surveillance undermines democracy and individual rights – reassertion of independent judiciary key Hafez, 2013 (Jonathan, Associate Professor of Law at Seton Hall Law School, “how NSA surveillance endangers the fourth amendment,” Constitution Daily, August 13, http://blog.constitutioncenter.org/2013/08/how-nsa-surveillance-endangers-the-fourth-amendment/) The Fourth Amendment provides a bulwark against this type of dragnet surveillance. Before searching Americans’ private communications, the Fourth Amendment requires that the government demonstrate probable cause or individualized suspicion. The Fourth Amendment also interposes an independent judiciary between the government and its citizenry—requiring that the government obtain a warrant by making this individualized showing before a federal judge. Review by a neutral and independent decisionmaker is crucial to the Madisonian system of checks and balances, designed to prevent government overreaching and safeguard individual freedoms. The NSA surveillance programs undermine these protections, threatening to render them a dead letter for all “foreign intelligence information”—a category broadly defined to include information not only about terrorism, but also about intelligence activities, national defense, and even the “foreign affairs” of the United States. Further, given the lax standards the NSA uses to determine whether prospective surveillance targets are foreigners abroad, errors are inevitable. This means that the NSA is likely collecting the content of purely domestic communications as well. In 1978, Congress established a special court—known as the Foreign Intelligence Surveillance Court (FISC)—to review requests for national security surveillance. But, at best, the FISC is merely providing review of the overall surveillance programs conducted under the FAA, and not individual requests for information. Moreover, no FISC ruling explaining its legal analysis of the FAA or “about the target” searches of Americans’ cross-border communications has been disclosed to the public. The secrecy that shrouds the FISC’s decisions heightens the risk to the Fourth Amendment, as even the reasoning used to justify massive government surveillance remains secret. The impact of NSA surveillance is deep and far-reaching. Vacuuming up Americans’ communications undermines basic principles of privacy. It also chills the communications and discourse essential to a democratic society and fundamentally alters the citizenry’s relation with its government. The NSA’s widespread, suspicionless surveillance of Americans’ private communications will not only impact the work of journalists, lawyers, and others who frequently communicate with people abroad. It will also affect the conduct of ordinary citizens, now fearful of visiting a controversial website or discussing a particular topic via email. Over time, the vibrant exchange of ideas essential to democracy will diminish and trust in the government will erode. At the same time, the government will be emboldened to justify further incursions on individual liberty in name of protecting the United States from terrorism or other threats. Courts Key to Democracy Independent judiciary and rule of law key to democracy – prevents arbitrary exercise of political power Reenock et al, 2013 (Christopher, Florida State University, Jeffrey K. Staton, Emory University, Marius Radean, Florida State University, “Legal institutions and Democratic survival,” The Journal of Politics, Vol. 75, No. 2, April) Institutional systems designed to limit arbitrary state power, when they are effective, address the kind of monitoring and coordination problems that Przeworski’s leaders confront. By an effective institutional system that limits arbitrary state power, we have in mind a cluster of two classes of elements (themselves collections of many attributes), which scholars have proposed as useful to the creation of credible commitments. One is a set of rules that define the limits of state power (e.g., North 1991). These typically include formal constitutional rules, e.g. prohibitions on the impairment of contracts, due process guarantees, equal protection rights, etc. But they can also include unwritten norms or more typically statutory rules governing standing, the freedom of access to information, etc., and even elements of judicial doctrine that ensure things like the ‘‘reasonableness’’ of government actions. Importantly, although neoinstitutional scholars largely agree that state constraint is promoted by rules, there is little consensus over the precise bundle of rules necessary for an effective system, much less over the precise way of expressing these rules. Even scholars seeking to ‘‘unbundle’’ rules are typically not successful in laying out precisely which rules, in combination with which others, are necessary or suffi- cient to ensure credible commitments (Acemoglu and Johnson 2005). Indeed, it seems highly likely that the perfect bundle of formal rules is likely to be contextually dependent. The reason is that if they are going to set behavioral incentives correctly, they must reflect shared understandings about the real limits of state authority, and these understandings can manifest in a variety of ways (Weingast 1997). The bottom line is that while formal limits on the state must exist, they are unlikely to manifest identically in every context. The second element of an effective institutional system consists of independent mechanisms for applying and enforcing rules in particular contexts. An effective system thus includes people who serve on courts, labor boards, and bodies for alternative dispute resolution, and who are willing to provide judgments that are independent of current government preferences. This is not to say that an effective institutional system need bind state practices in every context. Judges, for example, may be ignored on occasion (e.g., Vanberg 2005). What is critical for an effective system is that when violations are observed, they are declared. Such institutional systems attempt to limit arbitrary state power in a variety of dimensions. In the context of the Przeworski model, an institutional system for the protection of property rights is particularly salient. As Acemoglu and Johnson write, the key feature of these institutions is that: [T]hey are intimately linked to the distribution of political power in society because they regulate the relationship between ordinary private citizens and the politicians or elites with access to political power. When property rights institutions fail to constrain those who control the state, it is not possible to circumvent the ensuing problems by writing alternative contracts to prevent future expropriation, because the state, with its monopoly of legitimate violence, is the ultimate arbiter of contracts. (2005, 951) We will focus largely on this kind of institutional system here, recognizing that the argument can be generalized beyond property rights. In understanding how institutions might influence the monitoring and coordination problems of Przeworski’s (2005) model, we are benefited by the fact that two extant models of law (Carrubba 2005; Weingast 1997) are directly on point. Carrubba considers a game in which players confront an informational challenge that complicates their ability to monitor cooperative agreements. Weingast considers a game in which citizens confront a coordination problem, the solution to which is necessary in order to keep the state from violating fundamental limits on its power. The institutional solutions the authors propose do not exhaust all elements of a complete property rights system, the examples (a judicial dispute resolution function and a set of constitutional rules) are critical components of such a system and the mechanisms proposed are easily extended to a complete system. We consider each in turn. Monitoring. Carrubba’s model is essentially an infinitely repeated prisoner’s dilemma,7 in which the players do not observe period-specific costs of cooperation paid by their opponents. In some periods, mutual cooperation is efficient, whereas in other periods it is not (2005, 672). Carrubba considers an equilibrium in which the players wish to punish non-cooperative behavior only when cooperation would have been mutually beneficial. The problem is that they do not observe the nature of a defection perfectly; and, in the absence of this information, parties are forced to use punishment strategies that result in conflict. These strategies successfully prevent opponents from violating agreements opportunistically but they ensure conflict when agreements are violated for good reasons (i.e., when mutual cooperation would be inefficient). Carrubba argues that the judiciary can serve as a monitor of cooperative agreements and eliminate costly conflicts. It does so by offering strategic declarations on the nature of alleged breaches, declaring a violation only when cooperation would have been mutually beneficial. The implications of this kind of judging is that the parties are permitted to ignore their obligations when mutual cooperation would be inefficient and incentivized to cooperate when it would be efficient.8 By so doing, courts help manage cooperative agreements, agreements like the parties implicitly strike in Przeworski’s model. There are two important caveats. To serve this informational function, judges must be returning decisions that are not simply reflections of either party’s desire. Otherwise, the information revealed would not be credible. Second, judicial monitoring will not induce mutual cooperation in all contexts. As in the Przeworski model, there are some contexts in which a set of cooperative strategies simply cannot be sustained in equilibrium, regardless of the monitoring provided by a court (2005, 673–77). Coordination. Weingast reminds us that monitoring alone cannot solve the leader’s commitment problem. Leaders must believe that they will be punished for ignoring declarations about having violated a limit on power. To hold such beliefs, leaders must perceive that people will mobilize to punish a violation and that this depends on the resolution of a significant coordination problem. If individuals cannot coordinate, they will not be able to enforce limits on the state, the result of which will be that democratic regimes will violate limits on their authority. Weingast suggests that constitutions can serve as focal points, selecting equilibria in which individuals successfully mobilize to redress transgressions from among the set of possible solutions. Although this kind of formal constitutional mechanism is plausible, Weingast’s argument applies to nonconstitutional limits on authority, as well as to the entities that formally recognize violations, e.g., courts. This is to say that judicial decisions finding a violation can serve as a focal point for social coordination. Yet again, it is important to remember that this mechanism works only if rules or the bodies that enforce them actually can create focal points. That is, they must work in practice. To have such an effect courts and other enforcement bodies ought to be at least minimally independent of the parties they regulate. Without independence, it is unclear how they would communicate credibly that a fundamental regime rule had been violated. This mechanism also will be limited by the underlying structure of democratic compromises. If the conditions for compromise are not met, there will be no fundamental limits on state authority to enforce and thus no losing party constituents to coordinate. In summary, systems of institutions facilitate political order by helping competing political coalitions enforce their own bargains. Specifically, they solve a leader’s commitment problem in three ways: (1) by helping to identify violations, (2) by helping to sort out reasonable violations from unreasonable violations, and (3) by helping to coordinate group actions in the event of an unreasonable violation. Legitimacy Advantage Link/Solvency Deference on the NSA destroys judicial independence and legitimacy Buttar, 2013 (Shahid, executive director of the Bill of Rights defense Committee, “Dueling judicial rulings on NSA spying, and why they don’t matter,” December 30, Bill of Rights Defense Committee, http://www.bordc.org/blog/dueling-judicial-rulings-nsa-spying-and-why-they-dont-matter) Two weeks ago, US District Judge Richard Leon rightly described the NSA’s domestic spying operations as an “indiscriminate and arbitrary invasion.” He ruled in favor of a preliminary injunction against the programs, and stayed his ruling pending appeals that could go on for years. Last Friday, Judge William Pauley opined that the NSA’s program does not violate the Fourth Amendment, prompting outrage among observers who understand either the NSA’s programs, or the role of courts, better than Judge Pauley. His decision reflects a disturbing judicial deference to executive spin, and undermines not only constitutional rights, but also judicial independence. Why Judge Pauley’s ruling is silly: what congressional oversight? We've known for some time of executive officials of lying to Congress about the NSA's domestic dragnet. Yet Judge Pauley’s deferential opinion states that the NSAs domestic spying programs have been subjected to rigorous oversight by all three branches of government. That is simply and demonstrably false: multiple members of Congress have publicly complained that they were kept in the dark, and even those few who were exposed to the programs through their roles on oversight committees have posed tough questions, only to hear lies in response. Several members of Congress have gone so far as to seek the prosecution of the Director of National Intelligence for deliberately misleading Congress about the scope, extent, and scale of NSA spying —which, even after the litany of revelations this year, remain unknown to the public, press, and Congress. Among the members of Congress seeking to curtail NSA powers are the original authors of the PATRIOT Act themselves, who claim that they never intended their signature legislative achievement to be abused as it has been over the past decade. Yet Judge Pauley relied on congressional approval of the programs. Why Judge Pauley’s ruling is silly: effectiveness? really? Judge Pauley also predicated his decision on the supposed effectiveness of the NSA’s programs, which the president's own review board rejected a week before the judge released his poorly reasoned opinion. Even to whatever extent the programs were proven effective -- which they have not been -- that issue would be well outside the judicial scope of inquiry. The Fourth Amendment requires searches and seizures to be justified with a specific warrant. In this context, the crucial jurisprudential question is whether or not NSA collection of telephony metadata counts as conducting a “search” or “seizure.” Why Judge Pauley’s ruling is silly: what’s a search? In 1979 -- over 30 years ago, well before the rise of anything even remotely resembling the Internet -- the Supreme Court held that capturing telephony metadata did not constitute a search when the government pursued a specific target, for whom authorities had a basis for individual suspicion, in the context of a particular investigation. None of those limiting principles apply to cases challenging the NSA's spying programs, yet judge Pauley -- like the NSA -- preposterously presents Smith v Maryland as a basis for the legality of tapping the back end of the entire phone system and Internet. At the end of the day, there could not be a more wanton violation of the Fourth Amendment than the NSA's domestic dragnet. Judge Leon, appointed by the president responsible for initiating the programs in the first place, understood that. Stepping back At stake, in addition to the vitality of privacy, and the opportunity for dissent in America, is the independence — and legitimacy — of our judiciary. Each of these ingredients are required for our democracy to be healthy. The fact that the NSA continues to wage a decade-long assault on the American people using our own tax dollars is a clear sign that it is not. The dueling judicial rulings are ultimately a distraction, however, as Congress is poised to take action much more quickly to resolve the current controversy. Having said that, despite the mounting controversy and escalating momentum in Congress for dramatic restrictions on NSA powers, whatever emerges from the current legislative process is likely to remain inadequate, as most agencies involved in domestic spying have yet to draw any sustained public or congressional attention. A/T Courts Not Perceived Courts are internationally perceived Feldman, 2008 (Noah, Law professor at Harvard University and adjunct senior fellow at the Council on Foreign Relaitons, “When judges make foreign policy,” September 28, NYT, http://www.nytimes.com/2008/09/28/magazine/28lawt.html?_r=3&oref=slogin&ref=magazine&pagewanted=print) This problem has many dimensions. It includes mundane practical questions, like what force the United States should give to the law of the sea. It includes more symbolic questions, like whether high-ranking American officials can be held accountable for crimes against international law. And it includes questions of momentous consequence, like whether international law should be treated as law in the United States; what rights, if any, noncitizens have to come before American courts or tribunals; whether the protections of the Geneva Conventions apply to people that the U.S. government accuses of being terrorists; and whether the U.S. Supreme Court should consider the decisions of foreign or international tribunals when it interprets the Constitution. In recent years, two prominent schools of thought have emerged to answer these questions. One view, closely associated with the Bush administration, begins with the observation that law, in the age of modern liberal democracy, derives its legitimacy from being enacted by elected representatives of the people. From this standpoint, the Constitution is seen as facing inward, toward the Americans who made it, toward their rights and their security. For the most part, that is, the rights the Constitution provides are for citizens and provided only within the borders of the country. By these lights, any interpretation of the Constitution that restricts the nation’s security or sovereignty — for example, by extending constitutional rights to noncitizens encountered on battlefields overseas — is misguided and even dangerous. In the words of the conservative legal scholars Eric Posner and Jack Goldsmith (who is himself a former member of the Bush administration), the Constitution “was designed to create a more perfect domestic order, and its foreign relations mechanisms were crafted to enhance U.S. welfare.” A competing view, championed mostly by liberals, defines the rule of law differently: law is conceived not as a quintessentially national phenomenon but rather as a global ideal. The liberal position readily concedes that the Constitution specifies the law for the United States but stresses that a fuller, more complete conception of law demands that American law be pictured alongside international law and other (legitimate) national constitutions. The U.S. Constitution, on this cosmopolitan view, faces outward. It is a paradigm of the rule of law: rights similar to those it confers on Americans should protect all people everywhere, so that no one falls outside the reach of some legitimate legal order. What is most important about our Constitution, liberals stress, is not that it provides The Supreme Court, whose new term begins Oct. 6, has become a battleground for these two worldviews. In the last term, which ended in June, the justices gave expression to both visions. In two cases in particular — one high-profile, the other largely overlooked — the justices divided into roughly two blocs, representing the “inward” and “outward” looking conceptions of the Constitution, with Justice Anthony Kennedy voting rights for us but that its vision of freedom ought to apply universally. with liberals in one case and conservatives in the other. The Supreme Court is on the verge of several retirements; how the justices will address This may seem like an odd way of thinking about international affairs. In the coming presidential election, every voter understands that there is a choice to be made between the foreign-policy visions of John McCain and Barack Obama. What is less obvious, but no less important, is that Supreme Court appointments have become a de facto part of American foreign policy. The court , like the State Department and the Pentagon, now makes decisions in cases that directly change and shape our relationship with the world. And as the justices decide these cases, they are doing as much as anyone to shape America’s fortunes in an age of global terror and economic turmoil. critical issues of American foreign policy in the future hangs very much in the balance. JI Solves Hege – A/T Counterbalancing Multiple factors increase perceived legitimacy of US dominance, prevents counterbalancing Knowles, 2009 (Robert, Acting assistant Professor, New York University School of Law, “American Hegemony and the Foreign Affairs Constitution,” Arizona State Law Journal, 41 Ariz. St. L.J. 87, October) Hegemonic orders take on hierarchical characteristics, with the preeminent power having denser political ties with other nations than in a unipolar order.333 Stability in hegemonic orders is maintained in part through security guarantees and trade relationships that result in economic specialization among nations.334 For example, if Nation X’s security is supplied by Hegemon Y, Nation X can de-emphasize military power and focus on economic power. In a hegemonic system, the preeminent state has “the power to shape the rules of international politics according to its own interests.”335 The hegemon, in return, provides public goods for the system as a whole.336 The hegemon possesses not only superior command of military and economic resources but “soft” power, the ability to guide other states’ preferences and interests.337 The durability and stability of hegemonic orders depends on other states’ acceptance of the hegemon’s role. The hegemon’s leadership must be seen as legitimate.338 The United States qualifies as a global hegemon. In many ways, the U.S. acts as a world government.339 It provides public goods for the world, such as security guarantees, the protection of sea lanes, and support for open markets.340 After World War II, the U.S. forged a system of military alliances and transnational economic and political institutions such as the United Nations, NATO, the International Monetary Fund, and the World Bank that remain in place today. The U.S. provides security for allies such as Germany and Japan, maintaining a strong military presence in Asia and Europe.341 Because of its overwhelming military might, the U.S. possesses what amounts to a “quasi-monopoly” on the use of force.342 This prevents other nations from launching wars that would tend to be truly de-stabilizing. Similarly, the United States provides a public good through its efforts to combat terrorism and confront—even through regime change—rogue states.343 The United States also provides a public good through its promulgation and enforcement of international norms. It exercises a dominant influence on the definition of international law because it is the largest “consumer” of such law and the only nation capable of enforcing it on a global scale.344 The U.S. “was the primary driver behind the establishment of the United Nations system and the development of contemporary treaties and institutional regimes to effectuate those treaties in both public and private international law.”345 Moreover, controlling international norms are sometimes embodied in the U.S. Constitution and domestic law rather than in treaties or customary international law. For example, whether terrorist threats will be countered effectively depends “in large part on U.S. law regarding armed conflict, from rules that define the circumstances under which the President can use force to those that define the proper treatment of enemy combatants.”346 These public goods provided by the United States stabilize the system by legitimizing it and decreasing resistance to it. The transnational political and economic institutions created by the United States provide other countries with informal access to policymaking and tend to reduce resistance to American hegemony, encouraging others to “bandwagon” with the U.S. rather than seek to create alternative centers of power.347 American hegemony also coincided with the rise of globalization—the increasing integration and standardization of markets and cultures—which tends to stabilize the global system and reduce conflict.348 The legitimacy of American hegemony is strengthened and sustained by the democratic and accessible nature of the U.S. government. The American constitutional separation of powers is an international public good. The risk that it will hinder the ability of the U.S. to act swiftly, coherently or decisively in foreign affairs is counter-balanced by the benefits it provides in permitting foreigners multiple points of access to the government.349 Foreign nations and citizens lobby Congress and executive branch agencies in the State, Treasury, Defense, and Commerce Departments, where foreign policy is made.350 They use the media to broadcast their point of view in an effort to influence the opinion of decision-makers.351 Because the United States is a nation of immigrants, many American citizens have a specific interest in the fates of particular countries and form “ethnic lobbies” for the purpose of affecting foreign policy.352 The courts, too, are accessible to foreign nations and non-citizens. The Alien Tort Statute is emerging as an important vehicle for adjudicating tort claims among non-citizens in U.S. courts.353 JI Solves Hege Judiciary key to international credibility – less arbitrary than the executive Sullivan, 2008 (Scott M., Assistant Professor of Law, Emerging Scholars Program, The University of Texas School of Law, “Rethinking Treaty Interpretation,” Texas Law Review, 86 Tex. L. Rev. 777, March) c. Promoting Uniformity. - The judicial doctrine of stare decisis and judicial modesty typically lead to very few contenders in legal interpretations. Court decisions, while ultimately vulnerable to changing judicial opinion, are structurally and procedurally more enshrined than executive determinations that are easily discarded from administration to administration or, in certain political circumstances, within an administration. n97 [*798] d. Legitimacy Enhancing. - As demonstrated by the Bush Administration's interpretation of the requirements of the Geneva Conventions, a unilateral executive interpretation of international obligations is often viewed as subjectively biased rather than objectively reached. In contrast, the diverse, politically insulated federal Judiciary fares much better in world opinion polls. n98 Beyond basic popularity, the perception of an independent, structural check on executive power in foreign affairs assists in creating an aura of legitimacy surrounding the implementation of international law. A/T Deference Key to Hege Our link to hege outweighs their turn – strict offensive realism is false, means legitimacy is the biggest internal link, only we access it Knowles, 2009 (Robert, Acting assistant Professor, New York University School of Law, “American Hegemony and the Foreign Affairs Constitution,” Arizona State Law Journal, 41 Ariz. St. L.J. 87, October) Why do foreign affairs demand that the executive branch enjoy unfettered discretion? The courts’ view of their own competence has been shaped by America’s role in the world. There is a deep , if usually unarticulated, connection between the assumed need for special deference and a popular theory of international relations known as realism. Realism depicts an anarchic international realm, populated only by nation-states, and dominated by roughly co-equal great powers carefully balancing one another.6 Executive competences are required to handle this dangerous and unstable external environment.7 This classic realist model of comparative institutional competence seemed appropriate when America was one of several, or even two, great powers. But even then, importing IR realism into constitutional foreign affairs doctrine was a recipe for chaos. Realpolitik teaches that the state must do whatever is necessary to protect itself.8 But how can courts successfully balance this overriding principle against other constitutional values such as the protection of liberty? Moreover, the post-Cold War world has provoked a crisis in realism.9 The United States is a global hegemon. It is unrivaled in its ability to deploy force throughout the globe, and it provides “public goods” for the world – such as the protection of sea lanes – in exchange for broad acceptance of U.S. leadership.10 Although realism predicts counter-balancing, no great power or coalition has yet emerged to challenge America’s predominance. And despite a new round of predictions about American decline, the U.S. is still projected to have by far the largest economy and the largest military for decades to come .11 Political scientists have struggled to define this American-led system, but courts and scholars of constitutional law have largely ignored it.12 Instead, most debates about special deference have simply accepted outmoded classic realist assumptions that became conventional wisdom in the 1930s and 40s. This Article offers a new model for assessing appropriate judicial deference in foreign affairs that takes account of American hegemony. By maintaining consistent interpretation of U.S. and international law over time and providing virtual representation for other nations and non-citizens, U.S. courts bestow legitimacy on the acts of the political branches, provide public goods for the world, and increase America’s soft power – all of which assist in maintaining the stability and legitimacy of the American-led hegemonic order. A/T Executive Key Turn—court interpretation increases executive legitimacy Knowles, 2009 (Robert, Acting assistant Professor, New York University School of Law, “American Hegemony and the Foreign Affairs Constitution,” Arizona State Law Journal, 41 Ariz. St. L.J. 87, October) Professors Posner and Sunstein have argued for exceptional deference on the ground that, unless the executive is the voice of the nation in foreign affairs, other nations will not know whom to hold accountable for foreign policy decisions.412 But the Guantánamo litigation demonstrated that American hegemony has altered this classic assumption as well. The transparent and accessible nature of the U.S. government made it possible for other nations to be informed about the detainee policy and, conceivably, to have a role in changing it. The Kuwaiti government hired American attorneys to represent their citizens held at Guantánamo.413 In the enemy combatant litigation, the government was forced to better articulate its detainee policies, justify the detention of each detainee, and permit attorney visits with the detainees.414 Other nations learned about the treatment of their citizens through the information obtained by attorneys.415 Their argument relies on false realist assumptions – credibility gained from the courts outweighs hard power gained from the executive Knowles, 2009 (Robert, Acting assistant Professor, New York University School of Law, “American Hegemony and the Foreign Affairs Constitution,” Arizona State Law Journal, 41 Ariz. St. L.J. 87, October) The enemy combatant litigation also underscores the extent to which the classic realist assumptions about courts’ legitimacy in foreign affairs have been turned on their head. In an anarchic world, legitimacy derives largely from brute force. The courts have no armies at their disposal and look weak when they issue decisions that cannot be enforced .440 But in a hegemonic system, where governance depends on voluntary acquiescence, the courts have a greater role to play. Rather than hobbling the exercise of foreign policy, the courts are a key form of “soft power .”441 As Justice Kennedy’s majority opinion observed in Boumediene, courts can bestow external legitimacy on the acts of the political branches.442 Acts having a basis in law are almost universally regarded as more legitimate than merely political acts . Most foreign policy experts believe that the Bush Administration’s detention scheme “hurt America’s image and standing in the world.”443 The restoration of habeas corpus in Boumediene may help begin to counter-act this loss of prestige. A/T Executive Key to Speed International relations doesn’t change fast enough for this to be relevant Knowles, 2009 (Robert, Acting assistant Professor, New York University School of Law, “American Hegemony and the Foreign Affairs Constitution,” Arizona State Law Journal, 41 Ariz. St. L.J. 87, October) Since Curtiss-Wright, speed has been recognized as an important executive branch characteristic. The executive branch can reach a uniform interpretation of the law quickly, and the courts are, by comparison, quite slow.299 This is understandable in a world in which subtly-shifting alliances determine the balance of power. And in the age of terrorism, speed remains a crucial component of effective foreign policy. The ace card for defenders of special deference remains the national security emergency . How can we possibly take the risk that the courts will hobble the President’s efforts to protect the United States in a time of crisis?300 It is important to separate the very slender category of true emergencies from the vast category of foreign relations in general. Ninety-nine percent of foreign affairs controversies do not involve the President sending troops abroad or a threatened terrorist attack, and there is very little opportunity for courts to interfere with an executive response to a crisis situation. Courts typically review the legality of presidential decisions years later.301 Most of the “enemy combatants” detained at Guantánamo were captured within a few months of September 11, 2001 and arrived at Guantánamo in early 2002.302 The Supreme Court did not address the detainees’ constitutional right to habeas review until 2008.303 A/T Executive Key to Flexibility Even if this is true, the loss of credibility and predictability from deference outweighs any increased flexibility Knowles, 2009 (Robert, Acting assistant Professor, New York University School of Law, “American Hegemony and the Foreign Affairs Constitution,” Arizona State Law Journal, 41 Ariz. St. L.J. 87, October) The hegemonic model also reduces the need for executive branch flexibility, and the institutional competence terrain shifts toward the courts. The stability of the current U.S.-led international system depends on the ability of the U.S. to govern effectively. Effective governance depends on, among other things, predictability.421 G. John Ikenberry analogizes America's hegemonic position to that of a “giant corporation” seeking foreign investors: “The rule of law and the institutions of policy making in a democracy are the political equivalent of corporate transparency and accountability.”422 Stable interpretation of the law bolsters the stability of the system because other nations will know that they can rely on those interpretations and that there will be at least some degree of enforcement by the United States. At the same time, the separation of powers serves the global-governance function by reducing the ability of the executive branch to make “abrupt or aggressive moves toward other states .”423 The Bush Administration’s detainee policy, for all of its virtues and faults, was an exceedingly aggressive departure from existing norms, and was therefore bound to generate intense controversy. It was formulated quickly, by a small group of policy-makers and legal advisors without consulting Congress and over the objections of even some within the executive branch.424 Although the Administration invoked the law of armed conflict to justify its detention of enemy combatants, it did not seem to recognize limits imposed by that law.425 Most significantly, it designed the detention scheme around interrogation rather than incapacitation and excluded the detainees from all legal protections of the Geneva Conventions.426 It declared all detainees at Guantánamo to be “enemy combatants” without establishing a regularized process for making an individual determination for each detainee.427 And when it established the military commissions, also without consulting Congress, the Administration denied defendants important procedural protections.428 In an anarchic world characterized by great power conflict, one could make the argument that the executive branch requires maximum flexibility to defeat the enemy, who may not adhere to international law. Indeed, the precedents relied on most heavily by the Administration in the enemy combatant cases date from the 1930s and 1940s—a period when the international system was radically unstable, and the United States was one of several great powers vying for advantage.429 But during that time, the executive branch faced much more exogenous pressure from other great powers to comply with international law in the treatment of captured enemies. If the United States strayed too far from established norms, it would risk retaliation upon its own soldiers or other consequences from powerful rivals. Today, there are no such constraints: enemies such as al Qaeda are not great powers and are not likely to obey international law anyway. Instead, the danger is that American rule-breaking will set a pattern of rule-breaking for the world, leading to instability .430 America’s military predominance enables it to set the rules of the game. When the U.S. breaks its own rules, it loses legitimacy. A/T Deference Key to Hege Deference not key to hege – Courts won’t be overly intrusive Jonathan Turley, Prof of Law @ George Washington, George Washington Law Review, August 2002 (70 Geo. Wash. L. Rev. 649) The judicial incompetence rationale is hardly compelling in an age of regulation in which courts routinely deal with the most complex and comprehensive issues involving federal agencies. Courts often review actions taken by agencies like the DOE and NASA despite their classified functions and specialized communities. More importantly, there is objectively little reason for courts to be so self-critical and self-doubting when dealing with military matters. There is a mystique of a warrior class that obscures the fact that the legal issues dealt with in military courts are largely conventional criminal matters. If, as suggested in this article, military jurisdiction were reduced to core military functions and violations, the excluded cases where the status of the defendant is merely incidental. Once again, there was an element of truth in the danger of supplanting martial traditions and values with judicial edicts and analysis. This danger, however, was primarily limited to those core areas of discipline and obedience, such as orders violations. This rationale breaks down rapidly as the subjects of individual cases move further from the center of military concerns and into more conventional violations. As will be argued below, a significant reduction in the military justice system can be made without touching on these core areas. n296 A/T Confuses Diplomats Non-unique, confusion inevitable Knowles, 2009 (Robert, Acting assistant Professor, New York University School of Law, “American Hegemony and the Foreign Affairs Constitution,” Arizona State Law Journal, 41 Ariz. St. L.J. 87, October) A related argument, and a justification for the one-voice rationale, is that the United States will be “embarrassed” by conflicting pronouncements from different branches of government. The risk of embarrassment plays a key role in the Curtiss-Wright homily on superior executive competence, and has been frequently mentioned in foreign affairs political question decisions since Baker v. Carr.280 The core of the embarrassment justification is, apparently, that U.S. diplomats will be undermined in their delicate negotiations with other nations because court decisions that conflict with executive branch policy could baffle or even offend foreign officials.281 But it is difficult to argue that foreign dignitaries will fail to understand how the branches of the U.S. government can reach different interpretations of the law. America’s current structure of government has existed for almost 230 years. In the past, “other nations [were] asked to understand our complex constitutional system of checks and balances and we somehow managed to survive as a nation.”282 JI Good – Terrorism Judicial independence key to solve terrorism – provides credibility to government commitments Findley and Young, 2011 (Michael G., Brigham Young University, and Joseph K., American University, “Terorism, Democracy, and Credible commitments,” International Studies Quarterly, Vol. 55) In the context of terrorism, we consider credible commitment problems that groups face in assessing their future relations with the government (Fearon 1995; Lake and Rothchild 1998). Groups in all societies have policy goals, some more extreme than others, along with a variety of possible strategies to achieve those goals. Groups with extreme preferences are likely to opt for violence in pursuit of their goals more often than groups with moderate preferences (Lake 2002), especially when their rights cannot be guaranteed. Groups pursuing extreme policy changes face a strategic dilemma: it is possible that pressing extreme policy change will result in a violent response from the government. Similar to bargaining theories of war, whether the government of a state can provide a credible commitment not to violate rights in the future, and to conduct its behavior through the formal political process, is a salient concern for extremist groups seeking policy change. Whether the group’s policy preferences will be considered might then be secondary to the group’s survival. Some political institutions can mitigate credible commitment problems by binding governments to respect the formal political process and allow diverse opportunities for groups to air their grievances, even when groups pursue extreme policy change. Put otherwise, even in the presence of extremism within the population, institutions can help mitigate the desire to turn to violence. Other institutions (or lack thereof) prevent governments from making this commitment to future restraint credible. When the political institutions do not constrain a government from repressing groups with extreme demands in the future, these same groups then have incentives to act outside of the formal political process. Political institutions are an important part of an explanation of terrorism precisely because different institutions provide distinct strategic incentives for groups to pursue policy change. Both democracies and nondemocracies could have higher or lower levels of terrorism depending on how well their institutional arrangements make government commitments credible. We consider a specific institutional arrangement, whether a state has an independent judiciary, and hypothesize that independent judiciaries make government commitments more credible, thereby providing less incentive for groups to use terrorism. Without independent judiciaries, executives cannot credibly restrain themselves from future violations of rights. Thus, groups seeking to make extreme demands through a formal political process must assess whether the executive will resort to force. An independent judiciary offers some assurances about future government behavior in this situation. We examine this credible commitment hypothesis using a new data set of all domestic and transnational terrorist events in 149 countries from 1970 to 1997 (LaFree and Dugan 2007).2 The results indicate that independent judiciaries decrease the likelihood of terrorism, offering support for the credible commitment hypothesis. We also find that variation in terrorism exists both within and across regime type, although on average democracies have higher levels of terrorism than autocracies. In addition to standard statistical tests and robustness checks, we use matching methods and demonstrate that our results are not dependent on any one model specification (Rosenbaum and Rubin 1983; Ho, Imai, King, and Stuart 2007). Best statistical evidence shows judicial independence solves terrorism Findley and Young, 2011 (Michael G., Brigham Young University, and Joseph K., American University, “Terorism, Democracy, and Credible commitments,” International Studies Quarterly, Vol. 55) The results of our analysis indicate that independent judiciaries have a pacifying effect on domestic terrorism, even controlling for other factors. To be sure the results are not sensitive to certain measures or model specifications, we conducted a series of additional robustness checks consisting of (i) including a lagged dependent variable in the model, (ii) adding the GTD’s 1993 marginal estimates, (iii) including the 1998–2004 data, (iv) employing different measures of domestic and transnational terrorism, (v) including a lagged measure of state violence, (vi) estimating a zero-inflated negative binomial rather than the simple negative binomial, and (vii) using matching methods to reduce dependence on model assumptions. We report the results of the additional analyses in an online web appendix and briefly review the major findings here. Despite Brandt et al. (2000) and Brandt and Williams’s (2001) advice not to use a lagged dependent variable, we checked whether the independent judiciary result is sensitive to the inclusion of the lagged measure of terrorism and find that the independent judiciary result is still statistically significant at the 5% level, although the coefficient attenuates some. We then added the GTD’s marginal estimates for the lost 1993 data and also included the 1998–2004 data in our analyses to lengthen the time in our analysis. In both cases, we find that the independent judiciary result remains negatively related to terrorism and is statistically significant. When we operationalize domestic terrorism differently, the results are qualitatively almost identical. We included a measure of transnational terrorism and found that the results are also similar to domestic terrorism, suggesting that domestic and transnational terrorism may follow similar causal processes. We follow up on this point both in the conclusion and in the appendix, as it is an especially important distinction for terrorism research. We added a measure of state violence, furthermore, to address the possibility that calculated state repression reduces the levels of terrorism, and find that the opposite occurs—the more state violence that occurs, the more frequently dissident terrorism occurs as well. Independent judiciaries continue to be associated with less terrorism, even controlling for state violence. Rather than rely solely on the negative binomial regression model, we estimated the results using a zero-inflated negative binomial and find that our baseline results on independent judiciaries are robust to this change in estimator. Finally, to ensure that our results are not dependent upon the assumptions of any particular model, we pre-process our data using a variety of matching procedures. After matching, we again estimate zero-inflated negative binomial and simple negative binomial models and find that independent judiciaries remain associated with fewer terror events. Conclusion Terrorism is a frequent and persistent form of political behavior in contexts as diverse as Colombia, the United Kingdom, Russia, and Pakistan. We have argued that a common explanation underlies terrorist acts in democracies and authoritarian regimes alike and have emphasized the importance of examining credible commitment problems, an important class of strategic dilemmas (Lake and Rothchild 1998). We argued that certain institutional arrangements, especially an independent judiciary, can help resolve strategic dilemmas between the state and violent opposition. Namely, if an independent judiciary exists, extremists can be less concerned about a strong crackdown by the government in the future. In contrast to many studies that use data on transnational terror to evaluate arguments about state–opposition interactions, we use new data on terrorism throughout the world from 1970 to 1997 that includes domestic events. To show that our results are robust and not dependent on a particular model specification or assumptions embedded in the models, we estimate a series of models using alternative measures of terrorism and credible commitments, different time periods, and also employ matching methods to pre-process our data (Ho et al. 2007). The statistical analyses all provide substantial and robust support for the hypotheses, leading us to conclude that strategic dilemmas, such as commitment problems, are important determinants of terrorist behavior. Because we use the GTD data, we are better able to support claims about the process of domestic terrorism. We did not find substantial differences, however, between the effects of an independent judiciary on domestic and transnational terrorism. It is possible that domestic and transnational terrorism are, in fact, fundamentally similar in this particular context. We would not expect domestic and transnational terrorism to follow similar causal processes, however, because ‘‘[m]ost attacks are domestic and, more importantly, [transnational] attacks are not a representative sample of all terrorist activity’’ (Sa´nchez-Cuenca and De la Calle 2009:37). We suspect that domestic and transnational terrorism are indeed different and contend that the similar finding in our analysis is an artifact of the data and statistical tests. Transnational terrorism data and tests need to be refined in order to accurately understand the relationship between domestic and transnational terrorism. Namely, like other recent transnational terrorism studies, we used the standard country-year unit of analysis. Given that multiple nationalities are involved in transnational terrorism, directed dyads may need to be used instead, especially if the target of the terrorist act is separate from the state where the act occurred (Young and Findley 2010). In this case, information about institutions or other domestic factors in both states is necessary to evaluate arguments concerning transnational terrorism. Future theoretical and empirical work should consider more directly whether there exist differences between international and domestic terrorism. These differences may be applicable in varying contexts such as different samples of states or in unique time periods. If future work finds that meaningful differences do not exist, the large literature on transnational terrorism (for example, Sandler et al. 1983; Li 2005) may not need to set itself aside as a different area of study altogether. If meaningful differences are found, then attention should be focused on understanding the conditions under which this is the case. Our study has implications for several research areas, such as the connection between democracy and terrorism (Li 2005) as well as more general conflict processes. Rationalist explanations for war (e.g., Fearon 1995) suggest that conflict is caused by commitment problems, information problems, and (possibly) issue indivisibilities. Our findings suggest that, at least in the context of terrorism, issue indivisibilities may not be as salient for conflict resolution. If creating institutions, such as independent judiciaries, mitigates conflict, then even indivisible issues like territory can be dealt with. Most importantly, it suggests the need to understand better how government commitments affect the propensity for terrorism as a strategy for change. Both democracies and authoritarian regimes provide a diverse array of incentives for political participation, and further research could be devoted to addressing which of these incentives contributes to credible commitments. Beyond looking at just cross-national variation in terrorism activities, we suspect that a particularly fruitful area of research could address commitment problems at local and regional levels within countries, such as those created by geographic and other local factors. Additionally, variation in party systems and electoral systems within larger states like India (Piazza 2009) could help unpack some of these difficult issues. At the other end, intergovernmental organizations or non-governmental organizations might also be able to contribute to making commitments more credible, which could have the effect of decreasing terrorism throughout the world. Terror – A/T War on Terror Key Even if the war on terror is good, rule of law is key to solve Feldman, 2008 (Noah, Law professor at Harvard University and adjunct senior fellow at the Council on Foreign Relaitons, “When judges make foreign policy,” September 28, NYT, http://www.nytimes.com/2008/09/28/magazine/28lawt.html?_r=3&oref=slogin&ref=magazine&pagewanted=print) So what do we need the Constitution to do for us now? The answer, I think, is that the Constitution must be read to help us remember that while the war on terror continues, we are also still in the midst of a period of rapid globalization . An enduring lesson of the Bush years is the extreme difficulty and cost of doing things by ourselves. We need to build and rebuild alliances — and law has historically been one of our best tools for doing so. In our present precarious situation, it would be a terrible mistake to abandon our historic position of leadership in the global spread of the rule of law. Our leadership matters for reasons both universal and national. Seen from the perspective of the world, the fragmentation of power after the cold war creates new dangers of disorder that need to be mitigated by the sense of regularity and predictability that only the rule of law can provide. Terrorists need to be deterred. Failed states need to be brought under the umbrella of international organizations so they can govern themselves. And economic interdependence demands coordination, so that the collapse of one does not become the collapse of all . Privacy Advantage Tech Internal Link Failure to curtail surveillance undermines technological leadership Zetter, 2014 (Kim, award-winning, senior staff reporter at Wired covering cybercrime, privacy, and security, “Personal privacy is only one of the costs of NSA surveillance,” Wired, July 29, http://www.wired.com/2014/07/the-big-costs-of-nsa-surveillance-that-no-ones-talking-about/) “Too often, we have discussed the National Security Agency’s surveillance programs through the distorting lens of a simplistic ‘security versus privacy’ narrative,” said Danielle Kehl, policy analyst at the Open Technology Institute and primary author of the report. “But if you look closer, the more accurate story is that in the name of security, we’re trading away not only privacy, but also the U.S. tech economy, internet openness, America’s foreign policy interests and cybersecurity.” Over the last year, documents leaked by NSA whistleblower Edward Snowden, have disclosed numerous NSA spy operations that have gone beyond what many considered acceptable surveillance activity. These included infecting the computers of network administrators working for a Belgian telecom in order to undermine the company’s routers and siphon mobile traffic; working with companies to install backdoors in their products or network infrastructure or to devise ways to undermine encryption; intercepting products that U.S. companies send to customers overseas to install spy equipment in them before they reach customers. The Foundation’s report, released today, outlines some of the collateral damage of NSA surveillance in several areas, including: Economic losses to US businesses due to lost sales and declining customer trust. The deterioration of internet security as a result of the NSA stockpiling zero-day vulnerabilities, undermining encryption and installing backdoors in software and hardware products. Undermining the government’s credibility and leadership on “internet freedom” and governance issues such as censorship. Economic Costs to U.S. Business The economic costs of NSA surveillance can be difficult to gauge, given that it can be hard to know when the erosion of a company’s business is due solely to anger over government spying. Sometimes, there is little more than anecdotal evidence to go on. But when the German government, for example, specifically cites NSA surveillance as the reason it canceled a lucrative network contract with Verizon, there is little doubt that U.S. spying policies are having a negative impact on business. “[T]he ties revealed between foreign intelligence agencies and firms in the wake of the U.S. National Security Agency (NSA) affair show that the German government needs a very high level of security for its critical networks,” Germany’s Interior Ministry said in a statement over the canceled contract. Could the German government simply be leveraging the surveillance revelations to get a better contract or to put the US on the defensive in foreign policy negotiations? Sure. That may also be part of the agenda behind data localization proposals in Germany and elsewhere that would force telecoms and internet service providers to route and store the data of their citizens locally, rather than let it pass through the U.S. But, as the report points out, the Germans have not been alone in making business decisions based on NSA spying. Brazil reportedly scuttled a $4.5 billion fighter jet contract with Boeing and gave it to Saab instead. Sources told Bloomberg News “[t]he NSA problem ruined it” for the US defense contractor. Governments aren’t the only ones shunning US businesses. American firms in the cloud computing sector are feeling the pressure as consumers and corporate clients reconsider using third-party storage companies in the U.S. for their data. Companies like Dropbox and Amazon Web Services reportedly have lost business to overseas competitors like Artmotion, a Swiss hosting provider. The CEO of the European firm reported that within a month after the first revelations of NSA spying went public, his company’s business jumped 45 percent. Similarly, 25 percent of respondents in a survey of 300 British and Canadian businesses earlier this year said they were moving their data outside the US as a result of NSA spying. The Information Technology and Innovation Foundation has estimated that repercussions from the spying could cost the U.S. cloud computing industry some $22 to $35 billion over the next few years in lost business. Will the NSA spying revelations have long-term effects? Or will customers return to U.S. companies once the news fades into the background? It’s hard to tell. But German chancellor Angela Merkel has suggested that Europe build a separate permanent internet to keep data local and prevent it from traversing networks the NSA can more easily monitor. Germany also has instituted new data rules that prohibit any company from obtaining a federal contract unless it can guarantee that it will protect data stored in Germany from foreign authorities. These kinds of policies and infrastructure changes tend to remain long after the circumstances that spawned them have passed. Third Party Doctrine Bad Clapper is key to the Fourth amendment – limiting the scope of the third party doctrine is key to restore it Napolitano, 2014 (Andrew P., Senior Judicial Analyst, Fox News Channel, 1998 to present; Distinguished Visiting Professor of Law, Brooklyn Law School, 2013 to present; Judge of the Superior Court of New Jersey, 1987 to 1995, “A legal history of national security law and individual rights in the United States,” NYU Journal of Law & Liberty, 8 NYU J.L. 7 Liberty 396) In American Civil Liberties Union v. Clapper, Judge Pauley reached the opposite conclusion that Judge Leon did, relying on the third party doctrine. The Third Party Doctrine is an outdated rule in Fourth Amendment law which states that once a piece of information or data is given to a third party, like a medical record or a business record including personal data, the owner of that piece of information has no further legitimate privacy interest in that piece [*550] of information. n639 Consequently, Judge Pauly held that "the business records created by Verizon are not "Plaintiffs' call records.' Those records are created and maintained by the telecommunications provider, not the ACLU. Under the Constitution, that distinction is critical because when a person voluntarily conveys information to a third party, he forfeits his right to privacy in the information." n640 When the D.C. and Second Circuits hear the inevitable appeals from these cases, they as well may split or rule against the government. A circuit split over so fundamental a question cannot be ignored by the Supreme Court for long. In United States v. Jones, five justices filed concurring opinions to Justice Antonin Scalia's approach of Fourth Amendment analysis. In light of the massive government intrusion into privacy as of late, Justice Sonia Sotomayor's description of the privacy harms rings ever more true: This approach is ill suited to the digital age, in which people reveal a great deal of information about themselves to third parties in the course of carrying out mundane tasks. People disclose the phone numbers that they dial or text to their cellular providers; the URLs that they visit and the e-mail addresses with which they correspond to their Internet service providers; and the books, groceries, and medications they purchase to online retailers... . I for one doubt that people would accept without complaint the warrantless disclosure to the Government of a list of every Web site they had visited in the last week, or month, or year. But whatever the societal expectations, they can attain constitutionally [*551] protected status only if our Fourth Amendment jurisprudence ceases to treat secrecy as a prerequisite for privacy. n641 While Justice Samuel Alito and the other more liberal justices on the court concurring separately, it is likely the Justices will at least grant certiorari and evaluate the Third Party doctrine as part of their analysis, perhaps even reaching a compromise majority. 6. President Obama's NSA Reforms On January 17, 2014, President Obama introduced a series of NSA spying privacy "reforms" his administration will work towards institutionalizing in the future. These reforms can be succinctly described as too little, too late. The Electronic Frontier Foundation gave the Obama's reforms a 3.5/12 rating when "stacked up against 12 common sense fixes that should be a minimum for reforming NSA surveillance." n642 Obama's reform promise to do the following: "end the bulk collection of domestic phone records "as it currently exists [pursuant to PATRIOT Act Section 215]'" n643; abrogate the use of National Security Letters (gag order records demands) n644; lessening spying on foreigners n645; [*552] and, reforming the FISA court while opposing the deplorable FISA Improvements Act. n646 As the Electronic Frontier Foundation points out, this does nothing to stop the NSA from continuously undermining internet security through breaking encryption and security safeguards. n647 President Obama has not rejected the Third Party Doctrine, nor "embraced meaningful transparency reform." n648 Information obtained can still be used against criminal defendants without showing it to them. n649 And most importantly, the trove of data the government has collected over the last decade isn't going to be destroyed, as it should be; instead, it may be transferred into someone else's custody. In the grand scheme of things, these reforms are meaningless and maintain the hallmarks of a totalitarian government. Conclusion Overall, the historical record we have examined gives a less than satisfactory view of federal regard for civil liberties when it comes to matters of national security. Rights to trial, free speech, privacy, to be secure in one's home, to be free from indefinite detention, to fairness from the government, and many others have been sacrificed in the name of "security;" often for the satisfaction of the majority rather than for an actual national security need. With respect to the three rights specifically addressed in this article, the historical record demonstrates the need for serious and [*553] specific concerns if we are to be a free people. The attacks on the Freedom of Speech, the "oldest" of these constitutional norms, began in 1798, became a nationwide and prominent issue between World War I and the Cold War, and generally were corrected by the Warren Court. As to due process, the battle over the right to a civilian trial is still ongoing, but generally has been expanded since the days of President Lincoln. This battle has also come front and center in the Global War on Terror, with the judicial recognition of the due process rights of non-state actors engaged in combat against American troops. The detention of enemy combatants at Gitmo and other military bases has brought the vitality of military jurisdiction and military commissions to the forefront of jurisprudence in the cases of Hamdan and Padilla, tipping off a continuing disagreement between Congress, and the President, and the Supreme Court. With the right to privacy, however, the historical trend seems to be in the opposite direction. Governmental assaults on privacy began a while ago with less discrete violations, similar to President Adam's pinprick incursions on speech in the late 1790s, but eventually developed into a massive, nationwide, pressing issue because of the extreme and shocking breadth of the government's massive reach. It is probable that the current Supreme Court will arrive at a fundamental and necessary reimagining of the Third Party Doctrine and the Fourth Amendment jurisprudence that permits the sort of twisted executive reasoning described in this work. Justice Sotomayor, who has not shied away from finding constitutional theories to uphold the constitutional excesses of Big Government, recently revealed an inclination to engage in recovering lost privacy protections through this jurisprudence in United States v. Jones: More fundamentally, it may be necessary to reconsider the premise that an individual has no reasonable expectation of privacy in information voluntarily disclosed to third parties. This approach is ill suited to the digital age, in which [*554] people reveal a great deal of information about themselves to third parties in the course of carrying out mundane tasks, [and moreover, the Court should] not assume that all information voluntarily disclosed to some member of the public for a limited purpose is, for that reason alone, disentitled to Fourth Amendment protection. n650 And Justice Scalia himself, who has argued for a textualist reading of the Fourth Amendment - that is, it only protects persons, houses, papers, and effects - paused poignantly and emitted a "gotcha" smile when asked recently in public if a computer chip in a cell phone or a desktop is an "effect" under the Fourth Amendment. n651 Is the postman entitled to read your mail just because you gave him a letter to deliver? Is Verizon entitled to listen to your telephone conversations and tell the feds what it heard just because you used its equipment to conduct them? Can Google tell the feds all you have emailed just because you used Google's servers? Could the Fourth Amendment possibly permit this? While the court has shown a willingness to intervene and is poised to make substantial strides in the area of privacy protections, there is still a significant chance the law could go the other way; yet the law's reasonable expectation standard lets your neighbors sacrifice your freedom. Clapper is key for the supreme court to reexamine the third party disclosure doctrine. Third party doctrine eviscerates the constitutional protection of privacy Geverd, 2015 (Timothy, Law clerk for the Honorable B. Avant Edenfield, United States District Court for the Southern District of Georgia, “Bulk telephony metadata collection and the fourth amendment: the case for revisiting the Third-party disclosure doctrine in the Digital age,” The John Marshall Journal of Information Technology & Privacy Law, Winter, 31 J. Marshall J. Info. Tech. & Privacy L. 191, http://repository.jmls.edu/cgi/viewcontent.cgi?article=1759&context=jitpl) On June 5, 2013, Glenn Greenwald of The Guardian reported on leaked National Security Agency (“NSA”) documents revealing that the Agency was “collecting the telephone records of millions of US customers. . . under a top secret order issued in April.”2 On June 9, 2013, The Guardian released the identity of the source of the NSA leaks as Edward Snowden.3 Snowden, claiming that the NSA surveillance programs “pose[] „an existential threat to democracy,‟”4 leaked the top secret documents in order “„ . . . to inform the public as to that which is done in their name and that which is done against them‟”—i.e., government use of dragnet surveillance to destroy “basic liberties.”5 Snowden recently appeared by videoconference at the South by Southwest Conference in Austin, Texas.6 When asked if he would leak the details of the NSA surveillance programs again if given the chance, Snowden responded, “„Absolutely yes,” and added “that he „took an oath to support and defend the Constitution and [he] saw the Constitution . . . being violated on a massive scale.‟”7 However, it is far from clear that the NSA‟s surveillance programs do indeed violate the Constitution under current Fourth Amendment principles. Despite the Fourth Amendment‟s guarantee that “[t]he right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated,”8 the United States Supreme Court “consistently has held that a person has no legitimate expectation of privacy in information voluntarily turned over to third parties.”9 Thus, information disclosed to third parties falls outside of the protection of the Fourth Amendment. Under this third-party disclosure doctrine, the Court has held that the phone numbers one dials are beyond the scope of Fourth Amendment protection.10 Similarly, lower federal courts have applied the third-party disclosure doctrine to power records produced by utility companies,11 to records kept by Internet Service Providers (“ISPs”), 12 and to credit card information.13 The third-party disclosure doctrine thus clears the way for broad surveillance programs like the ones Edward Snowden leaked, capturing the attention of the American people and the world. Lack of constitutional protection for such information certainly is cause for alarm in today‟s digital world. Simply put, “your privacy is not Fourth Amendment safe” in the digital age.14 For many years, electronic surveillance has been beyond the reach of federal courts, because “[o]nce [information is] disclosed, that is the end of the privacy inquiry, and the result is that privacy protection is lost” regardless of “the circumstances surrounding that disclosure.”15 However, in the wake of the Edward Snowden leaks, federal courts will be forced to consider the continued vitality of the third-party disclosure doctrine in today‟s technological age. 16 Thus far, three United States District Courts have considered the legality of the NSA‟s bulk data collection and have reached conflicting conclusions.17 Three United States Courts of Appeals have since heard oral argument on the constitutionality of the bulk telephony collection program.18 This Article argues that federal courts should seize the opportunity presented by the Snowden leaks to reexamine the continued vitality of the current third-party disclosure doctrine in Fourth Amendment jurisprudence. Specifically, this Article argues that Smith v. Maryland19 simply cannot continue to act as the “North Star” for judges navigating the “Fourth Amendment waters” of the digital age,20 and that instead, Smith should apply more narrowly in the digital age. In so arguing, this Article advocates that courts apply a modified, twostep test to evaluating third-party disclosures rather than applying the traditional binary rubric that courts have drawn from Smith and United States v. Miller21—i.e., if information is disclosed, that information is unprotected. Thus, this Article suggests that courts ask, first, what individuals reasonably expect the scope of their disclosure to be and, second, whether a particular surveillance program is capable of revealing information beyond what those individuals reasonably expected to reveal. If the technology reveals information beyond that which individuals reasonably expected to reveal, then the use of such technology implicates the Fourth Amendment. ACLU v. Clapper Key Supreme court action in Clapper is key to restore privacy protection Brand, 2015 (Jeffrey S., Dean and Professor Emeritus and Chairman of the Center for Law and Global Justice, University of San Francisco School of Law, “Eavesdropping on our founding fathers: how a return to the republic’s core democratic values can help us resolve the surveillance crisis,” Harvard National Security Journal, 6 Harv. Nat’l Sec. J. 1) Most ominously, Section 215 of the Patriot Act expanded the power of the FBI to subpoena "tangible things" if they were believed to be "relevant to an authorized investigation" into international terrorism or foreign intelligence activities. n73 The amendment proved to be a bonanza for the Executive Branch when the FISA Court, in an opinion that remains secret to this day, expanded the definition of "relevance" to include "an entire database of records on millions of people." n74 The Wall Street Journal reported that, according to the FISA Review Court, "the special nature of the national-security and terrorism-prevention cases means 'relevant' can have a broader meaning for those investigations." n75 In 1991, the United States Supreme Court in United States v. R. Enterprises rejected such a broad definition of relevance in criminal cases because it inevitably meant that records of innocent individuals would be included. n76 Ironically, it would be a Democrat, Senator Diane Feinstein (D-CA), who would seek to explain and support the rationale for President George W. Bush's signature legislation: In today's world, things are not so simple. In many cases surveillance will have two key goals--the gathering of foreign intelligence and the gathering of evidence for a criminal prosecution. . . . Rather than forcing law enforcement to decide which purpose is primary . . . this bill strikes a new balance. It will now require that a "significant" purpose of the investigation must be foreign intelligence gathering to proceed with surveillance under FISA. n77 [*20] Post-9/11 history also included a willingness on the part of the Bush Administration to ignore FISA completely if it believed national security so demanded--a tack it took with the institution of the 2002 Terrorist Surveillance Program (TSP) that completely side-stepped FISA. The program was revealed by the New York Times in 2005, and the Bush Administration was forced to admit that TSP violated existing surveillance statutes. n78 By 2008, the perfect storm roiled to a peak when, with overwhelming bipartisan support, Congress passed the FISA Amendments Act (FAA), n79 which eliminated many of the specificity requirements needed to obtain a warrant under the FISA regime in its initial incarnation. Moreover, the FAA for the first time defined an "international wire communication" to include communications where an "end point is in the United States," thereby subjecting U.S. citizens to its reach. n80 The amendment led the Congressional Research Service to conclude that FISA now "provides a mechanism for the domestic acquisition without a court order, of communications that persons in the United States, including citizens, would be a party to. Prior to the enactment of Section 702, such acquisitions would require a court order in all but emergency situations." n81 [*21] Finally, in 2013, the FISA court received an additional layer of insulation from review when the Supreme Court decided Clapper v. Amnesty International. n82 In Clapper, the Court rejected an opportunity to rule on the constitutional merits of many of the post-9/11 changes to FISA by holding that the plaintiffs lacked standing to bring the action. In a 5-4 opinion authored by Justice Alito, the Court held that plaintiffs' fear that they would be subject to surveillance in the future was "too speculative" to establish standing. n83 Ultimately, new laws, amendments to FISA, secret rulings of the FISA court, and Clapper are partially responsible for landing us where we are today--in a surveillance environment in which it is possible for the government to collect data on essentially every phone call made in the United States. In fact, in light of all of these changes, it would be unfair to place all of the blame on the drafters of the original FISA statute for the Act's inability to weather the 9/11 storm and the concurrent technology revolution. Nonetheless, the reality is that even without the Patriot Act, the FAA, and Clapper, FISA was destined to implode because of fundamental flaws in its structure. FISA may have been ambushed by subsequent events but it is not blameless for its own demise. FISA may no longer be recognizable relative to its initial incarnation, but the seeds of its destruction in its original structure surely are and they shed light on the lessons that FISA teaches for the future. It is to those flaws and those lessons that we now turn. Time is of the essence. After the Supreme Court's decision in Clapper, one commentator wrote: "Absent a radical sea change from the courts, or more likely intervention from the Congress, the coffin is slamming shut on the ability of private citizens and civil liberties groups to challenge government counterterrorism policies." n84 That ominous prognosis punctuates the urgency of learning from the past if we are to halt the march toward democracy's extinction, a march led by the very institutions that the Framers created to sustain it. Internet Internal Link NSA surveillance gives countries an excuse to restrict data flows – damages the internet’s viability Giovanetti, 2013 (Tom, president of the Institute for Policy Innovation, “NSA Mass Surveillance Harming the Free Flow of Data,” September 19, http://www.ipi.org/ipi_issues/detail/nsa-masssurveillance-harming-the-free-flow-of-data) The American people have been outraged to find that their ordinary, uneventful communications and ecommerce transactions have been collected, analyzed and stored for future access in a mass surveillance program by the National Security Agency (NSA). But beyond its domestic political impact, the mass surveillance scandal may have far reaching economic consequences that affect the ability of American companies to compete internationally. The free movement of goods and people across borders has long been an element of a free society that contributes to economic growth. Barriers to trade in goods and lawful migration of citizens are rightly seen as creating unnecessary friction and harming economic freedom. But in our new global, digital economy, the free flow of data across borders is equally important. The Internet we have today and the Internet we want in the future depends on the free, unhindered flow of data across national borders. Various countries have long wanted to control digital traffic. Some despotic regimes want to have total control over Internet traffic for obvious reasons, but many other countries see data flows as resources to harness for domestic development purposes. India and Brazil, among others, have advocated “forced localization” policies that would compel data companies to: Build in-country data storage facilities so they are subject to countryspecific regulation and taxation; Share software code and other sensitive design elements with in-country government and industrial players; and Be subject to involuntary technology transfer requirements. This is why cross-border data flow protection has been a key element in recent trade agreements like the Trans Pacific Partnership (TPP) and the emerging Transatlantic Trade and Investment Partnership (TTIP) agreement with the EU. Tragically, the NSA mass surveillance scandal has provided these countries with the excuse they needed to move toward more control, regulation and forced localization of data. This week Dilma Rousseff, the president of Brazil, announced a series of measures aimed at insulating Brazil’s data flows from the United States. Tech Competitiveness Internal Link NSA surveillance undermines tech competitiveness – companies can’t deal with international overregulation Kosner, 2013 (Anthony Wing, “All major tech companies say NSA actions put public trust in internet at risk,” Forbes, December 9, http://www.forbes.com/sites/anthonykosner/2013/12/09/all-major-techcompanies-say-nsa-actions-puts-public-trust-in-internet-at-risk/) America’s biggest tech companies have gone from begging congress for surveillance reform, as Kashmir Hill reported here at the end of October, to taking their case to President Obama and members of Congress directly in an open letter published today. At risk is the public’s trust in the internet itself and all of the economic and cultural benefits it contains. The letter, signed by AOL, Apple, Facebook, Google, LinkedIn, Microsoft, Twitter and Yahoo, urges the U.S. to “take the lead and make reforms that ensure that government surveillance efforts are clearly restricted by law, proportionate to the risks, transparent and subject to independent oversight.” Microsoft’s general counsel, Brad Smith, released a statement asserting that, “People won’t use technology they don’t trust. Governments have put this trust at risk, and governments need to help restore it.” This is a striking development given the varying degree to which these same companies have cooperated and/or collaborated with the NSA’s data collection efforts. Clearly the balance has tipped and America’s tech companies now feel emboldened to call for sweeping reforms even as the Democratic chair of the Senate Intelligence Committee, Dianne Feinstein of California, is sponsoring a bill maintain the security agencies’ right to continue to collect bulk data. The Big-8, with a combined valuation of $1.4 trillion, are trying to convince their billions of users worldwide that they can still trust American tech companies. “For our part,” the open letter reads, “we are focused on keeping user’s data secure — deploying the latest encryption technology to prevent unauthorized surveillance on our networks and by pushing back on government requests to ensure that they are legal and reasonable in scope.” Google, Twitter, Yahoo and Microsoft have all beefed up their internal encryption systems. ”The security of users’ data is critical,” says Google CEO Larry Page, “which is why we’ve invested so much in encryption and fight for transparency around government requests for information.” This may all sound political, but as with most things coming out of Silicon Valley (and Redmond), it is primarily economically motivated. America’s leadership role in consumerfacing internet technology is clearly at risk, as are the benefits of true global connectivity for businesses and individuals. As governments around the world have expressed their displeasure with the Snowden revelations, a thicket of international regulation threatens to choke the global growth of the Internet giants. The Guardian explains that “The eight technology companies also hint at new fears, particularly that competing national responses to the Snowden revelations will not only damage their commercial interests but also lead to a balkanisation of the web as governments try to prevent internet companies from escaping overseas.” The Guardian’s role, particularly, in providing journalistic support for Snowden’s leaked material (more of which is still to come) has made it hard for American tech companies to deny the extent to which their own infrastructure has been compromised and repurposed for the cause of state surveillance. These companies have a mixed track record in terms of their relationship with the NSA, but most have expressed outright anger (and in some case expletives!) as these revelations have rolled out about the degree of their infiltration. CP 2ACs Notes The 2AC blocks are the bare minimum that you need in the 2AC – depending on the specific 1NC you may want to pull cards from the advantage sections of the file into the blocks. 2AC Congress CP 1. Perm – Do both 2. No solvency – a. Courts are key to legitimacy because they are perceived as rulebased institutions – this convinces potential terrorists and rival nations that the US won’t act arbitrarily and prevents counterbalancing; b. Key to democratic modeling – Flaherty evidence says that courts are engaged in international dialogue and supporting independence is the only way to place institutional checks on executive power; c. courts are key to democratic sustainability – electoral and representative democracies are natural unstable and tend toward war-making – courts are the only way to solve democratic peace; d. judicial precedent key to spillover to solve other privacy rights – fourth amendment protection is key to the internet and tech advantage. Current precedent grants undue deference to the executive; only the plan can reverse this trend Hall, 2014 (Jame, former political operative having worked on multiple campaigns, currently journalist for the sleuth journal, “The fourth amendment, NSA and metadata,” Sleuth Journal, June 13, https://www.thesleuthjournal.com/fourth-amendment-nsa-metadata/) Since the post World War II era, the radical shift from the remnants of the former Republic, into a global authority, where the meaning of the law has no correlation to the intent of original constitutional conviction, is undeniable. What was enemy signals interception became complete domestic scrutiny and monitoring. Lost for all practical legal purposes was The Central Meaning of the Fourth Amendment. Tracey Maclin provides a historic account and judicial context on how the constitution was perverted. “The Court’s rational basis model essentially asks whether the police have acted irrationally while intruding upon the Fourth Amendment rights of individuals. The Court’s model rarely requires warrants authorizing searches, disfavors vigorous judicial oversight of police searches, and prefers deference to police procedures as the mode of constitutional decision-making. Most importantly, a rational basis model severely diminishes our rights under the Fourth Amendment. As the private container cases demonstrate, a rational basis model does not subject police searches to vigorous judicial check. In many instances, the police are free to undertake unsupervised and suspicionless searches, even when less intrusive means are available to serve the state’s interests. In other contexts, warrantless searches are permitted when the only justification for such a search is police convenience. In the end, the Court finds that all of these searches are reasonable because they rationally serve legitimate state interests. This degree of deference to police searches is at odds with the central purpose of the Fourth Amendment, which is distrust of discretionary police power. The Fourth Amendment was not inserted in the Bill of Rights so that judges could meekly defer to government intrusions of privacy; rather, the amendment was designed to control such intrusions.” The NSA purports that national security not only encompasses data mining on all citizens, but also allows for effective total immunity from oversight and accountability. This mindset expands the ordinary boundaries of maintaining the peace into a tyrannical police state. The commitment to Open Government and Transparency is as believable as the fairy tale that anyone can become President. Abdication of judicial responsibility is so blatant that the century old decision by Justice William R. Day, Weeks v. United States (1914), U.S. Supreme Court, has no substantive application when the NSA deems that its ECHELON monitoring systems require that a PRISM be kept on everyone person. Also, watch the video, One Year Of Leaks That Turned Surveillance Conspiracy Theory to FACT! “The point of the Fourth Amendment which often is not grasped by zealous officers is not that it denies law enforcement the support of the usual inferences which reasonable men draw from evidence. Its protection consists in requiring that those inferences be drawn by a neutral and detached magistrate, instead of being judged by the officer engaged in the often competitive enterprise of ferreting out crime. Any assumption that evidence sufficient to support a magistrate’s disinterested determination to issue a search warrant will justify the officers in making a search without a warrant would reduce the Amendment to a nullity, and leave the people’s homes secure only in the discretion of police officers. Crime, even in the privacy of one’s own quarters, is, of course, of grave concern to society, and the law allows such crime to be reached on proper showing. The right of officers to thrust themselves into a home is also a grave concern, not only to the individual, but to a society which chooses to dwell in reasonable security and freedom from surveillance. When the right of privacy must reasonably yield to the right of search is, as a rule, to be decided by a judicial officer, not by a policeman or government enforcement agent. There are exceptional circumstances in which, on balancing the need for effective law enforcement against the right of privacy, it may be contended that a magistrate’s warrant for search may be dispensed with. But this is not such a case. No reason is offered for not obtaining a search warrant except the inconvenience to the officers and some slight delay necessary to prepare papers and present the evidence to a magistrate. These are never very convincing reasons and, in these circumstances, certainly are not enough to bypass the constitutional requirement. No suspect was fleeing or likely to take flight. The search was of permanent premises, not of a movable vehicle. No evidence or contraband was threatened with removal or destruction, except perhaps the fumes which we suppose in time will disappear. But they were not capable at any time of being reduced to possession for presentation to court. The evidence of their existence before the search was adequate and the testimony of the officers to that effect would not perish from the delay of getting a warrant. If the officers in this case were excused from the constitutional duty of presenting their evidence to a magistrate, it is difficult to think of a case in which it should be required.” The cyber environment of digital existence does not void the need for probable cause. However, the NSA does not observe such constitutional needs when the personal computer is the depository of your private papers. Other than advancements in technological communications and archiving, the precedent of the “exclusionary rule”, established in this case, is the ubiquitous causality from NSA collection that vacuums up every byte of data, using the presumption that everyone is a criminal. Even if not charged for an offense at this time, the information awaits future prosecutorial discretion. So, when in the case Klayman v. Obama, “On December 16, Richard J. Leon of the Federal District Court for the District of Columbia ruled that the metadata collection program violates the Fourth Amendment”, hopes were high that at least one federal judge had the courage to uphold the constitution. Metadata and the Fourth Amendment then cites that soon thereafter, the weight and magnate of the intelligence snooping force felt the usual letdown, when American Civil Liberties Union v. Clapper was decided. “On December 27, Judge William H. Pauley III came to the opposite conclusion. Contrary to Judge Leon’s belief that the metadata program has not been effective, Judge Pauley argued that the program could potentially have stopped the 9/11 attacks. However, the crux of his determination was that the Smith precedent applies and that no Fourth Amendment claim can be made out for Americans have no reasonable expectation of privacy regarding the metadata related to their phone calls.” Note the bizarre endorsement of this absurdly twisted legal logic that conveniently destroys the intentional importance of preserving essential privacy that corrupt courts want to make conditional. “Among the requirements for a successful Fourth Amendment claim is establishing that a reasonable expectation of privacy was violated. On this point, the most relevant precedent to the metadata cases is 1979’s Smith v. Maryland, in which the U.S. Supreme Court held that individuals have no reasonable expectation of privacy regarding the telephone numbers they call, for that information is freely provided to telephone companies and it is generally known that telephone companies keep this information in their records.” Abolishing the expectation of privacy is not subject to the redefining of what are reasonable restrictions that the government places upon its agencies. The reason why the NSA is so dangerous stems from the total lack of observing that the spying on ordinary citizens is a profound repudiation of basic and inalienable rights of each individual. Such systematic and surreptitious gathering also has No Fourth Amendment right in metadata embedded in posted photo, so say the U.S. Court of Appeals for the Fifth Circuit. Before long, this parade of government inspection and retention will subject even the hermit and the deliberate recluse to a profile third degree. It is a never-ending process until snatching your individual identity is the ultimate outcome. Congressional involvement doesn’t solve constitutional rights – multiple structural incentives Huq, 2012 (Aziz Z., Assistant professor of Law at the University of Chicago Law School, “Structural constitutionalism as counterterrorism,” California Law Review, August, 100 Calif. L. Rev. 887) Second, legislators may be more skeptical about pro-liberty than about pro-security proposals. Error costs on the liberty margin involve harms to discrete, potentially scattered individuals. Errors on the security side are more likely to be widespread, affecting many people and imposing a high political cost. Pro-liberty innovation thus has a greater downside risk at the polls than pro-security innovation. As a result, pro-liberty legislative action is less likely than new pro-security law. A parallel dynamic has played out in the politics of crime control. Elected officials worry about relaxing crime controls and being blamed for high-profile crimes (which affect many electors) more than they [*922] worry about erroneous convictions (which affect few, if any, electors). n182 Consider the impact of the 1988 "Willie Horton" ad run against candidate Michael Dukakis, which implied that the Massachusetts governor's decisions had resulted in 268 first-degree murders. n183 Although the actual number was zero, the ad "substantially raised the public's anxiety about Dukakis." n184 Third, the combination of such legislative risk along with the executive's attitudes to risk may dramatically cabin the domain of feasible coordinated bilateral action by the political branches. Some analysts have argued that presidents attempt to "reduce ... political risk by seeking and obtaining the approval of another government branch." n185 By allying with Congress, the President signals that a given proposal is not the product of idiosyncratic preferences or interest-group capture. n186 Sharing praise as well as blame, presidents dilute both upside and downside risk. As a consequence, they are more willing to engage in risky policies with congressional support. But Congress seeks to avoid proposals with large downside risk. Precisely when the President wants congressional involvement because a proposal is risky, legislators will be slow to act. As a result, counterterrorism policies with some perceived downside risk are not enacted even if they are on balance beneficial. Fourth, when legislators do act, they tend to avoid resolving hard questions. In a political system with "many veto players separated by large ideological distance ... legislation can only be incremental." n187 Multiparty bargaining delimits the possible policy space for solutions. As the complexity, [*923] difficulty, and enactment costs of legislative specificity rise, legislators will tend more and more to delegate decisions rather than to resolve hard questions themselves. n188 Terrorism is a subject matter that is especially prone to legislative delegation because it often entails hard trade-offs. Post-9/11 legislation generally leaves large discretion in executive hands. For example, when fashioning substitutes for habeas corpus, Congress left open both substantive and procedural rules. n189 While pressing for military commissions in 2006 and 2009, Congress also left to the executive branch the discretion to decide in which cases to use such tribunals. The 2008 tinkering with the Foreign Intelligence Surveillance Act also left considerable discretion in executive hands about how surveillance resources would be deployed. n190 Finally, it is worth underscoring that Congress's involvement does not mean that eventual policy will be more sensitive to values such as individual constitutional rights, despite Justice Souter's argument to that effect. n191 At the time that the Court happens to dispose of a case, there is no ex ante reason that subsequent legislative involvement will necessarily moderate executive decisions in ways that favor constitutional rights. Policy outcomes in a vetogate system depend on the relative positions of Congress and the executive. n192 If the Supreme Court rejects a liberty-invading innovation by the executive, the ensuing statutory response will be less invasive of liberty only if Congress is more libertarian than the executive and the courts at the specific time that legislators are called on to act. If the executive is more libertarian than Congress at that instant, by contrast, judicial resetting of the policy framework may well end up producing a less libertarian outcome because it allows Congress to reset policy. Yet there is no ex ante reason to predict that Congress will always be more libertarian than the executive in this fashion. The relative preferences of Congress and the executive depend on the outcomes of recent elections. The "cooling" function Justice Souter predicted is thus a contingent function of transient politics. n193 [*924] In other words, legislative action on terrorism is unlikely to be timely and cannot be assumed to have a dampening effect on executive ardor. It is instead likely to respond erratically to exogenous pressures and to punt hard questions; often, it will be simply unwise. This is hardly the model of Madisonian deliberation assumed by the Separation of Powers. 2AC Clear Statement CP Perm – do both Perm – do the counterplan. The CP still declares a violation of the fourth amendment; it adds additional reasoning to the plan No solvency – the CP still puts congress in control because it can declare its intent to override the fourth amendment. Potential for override means there’s no lasting precedent and no signal of judicial independence Clear statement rules don’t solve – they reduce constitutional rules to arbitrary values Manning, 2010 (John F., Bruce Bromley Professor of Law, Harvard Law School, “Clear statement rules and the constitution,” Columbia Law Review, Vol. 100, No. 2, http://www.law.uchicago.edu/files/files/manning_clearstatement.pdf) This Essay argues that if the legitimacy of constitutionally inspired clear statement rules depends on the plausibility of tracing them meaningfully to the Constitution, that burden cannot be met. Such rules seek to enforce constitutional values in the abstract, standing apart from the constitutional provisions from which they are derived. Indeed, the defining feature of constitutionally inspired clear statement rules is that even when a given interpretation of a statute would not violate the constitutional provision(s) from which the triggering value emanates, that interpretation might still be said to collide with the background value itself. But constitutional values do not, I argue, exist in the abstract. Values such as federalism, nonretroactivity, and the rule of law, do not exist in freestanding form. Rather, like all constitutional values, they find concrete expression in many discrete constitutional provisions, which prescribe the means of implementing the value in question. For example, the Ex Post Facto Clause embodies the value of nonretroactivity but it does so by proscribing the enactment of retroactive criminal penalties.20 Abstracting from that specific proscription to a background value of nonretroactivity, as the Court’s cases do,21 makes nonsense of a constitutionmaking process that determined in what ways and to what degree to proscribe retroactive government conduct. Constitutional penumbras, then, are problematic not because they “expand” the document’s reach, but rather because one cannot meaningfully speak of a constitutional value without reference to the constitutionmakers’ decisions about how to put that value into effect.22 The intuition behind this point is most easily felt from a textualist perspective. Textualism rests centrally upon the idea that all enacted texts, including the Constitution, entail compromise, which inevitably involves difference-splitting decisions about how far and in what ways to carry a value into effect.23 Accordingly, enforcing an abstract “value,” shorn from the implementing provisions that define its scope and limits, risks upsetting whatever compromise produced the text. But the concern about enforcing “values” in the abstract, I submit, holds even if one believes, as many do, that constitutional doctrine generally does and should unfold through common law elaboration (viz. through judge-made doctrine whose details cannot be traced directly to the constitutional text).24 Even given such an understanding, received constitutional doctrine prescribes means—often, quite elaborate means— of protecting the values at stake. Indeed, many such frameworks expressly call upon courts to consider competing values through some specified filter. Within such a doctrinal framework, clear statement rules tend to slight some values relative to others. Put another way, by focusing on one dimension of often complex doctrinal frameworks, clear statement rules do not supplement, but rather risk contradicting, the premises of the Supreme Court’s common law exegesis of the Constitution’s meaning. No solvency and no net benefit – clear statement rules increase intrusion on congress and lead to arbitrary doctrines Manning, 2010 (John F., Bruce Bromley Professor of Law, Harvard Law School, “Clear statement rules and the constitution,” Columbia Law Review, Vol. 100, No. 2, http://www.law.uchicago.edu/files/files/manning_clearstatement.pdf) Critics of clear statement rules have posed three major objections to their use. First, they argue that the practice does not mitigate the countermajoritarian dilemma. Frederick Schauer, for example, argues that, under the canon’s influence, “the Court frequently interprets a statute in ways that its drafters did not anticipate, and, constitutional questions aside, in ways that its drafters may not have preferred.”101 If so, he adds, “it is by no means clear that a strained interpretation of a federal statute that avoids a constitutional question is any less a judicial intrusion than the judicial invalidation on constitutional grounds of a less strained interpretation of the same statute.”102 Second, even if one assumes that aggressive construction is somewhat less intrusive than invalidation, the application of clear statement rules—which of course require no finding of unconstitutionality—may nonetheless accentuate the countermajoritarian difficulty by multiplying the occasions upon which courts act in the teeth of apparent legislative preferences. In this vein, Judge Posner writes that the canon of avoidance “enlarge[s] the already vast reach of constitutional prohibition beyond even the most extravagant modern interpretation of the Constitution—to create a judge-made constitutional ‘penumbra.’”103 Similarly, Professors Eskridge and Frickey have suggested that because clear statement rules purport only to guide statutory interpretation, the Court’s reliance on such rules may actually “provide [it] with a cover for a great deal more countermajoritarain activism, overall, than would open invalidation through judicial review.”104 Third, with respect to subject-specific clear statement rules,105 critics suggest that judges may be willful in picking and choosing which constitutional values to emphasize. In particular, some have complained that the clear statement rules developed since the advent of the Rehnquist Court have tended to favor states’ rights, executive power, and economic interests.106 Or, cast more generally, the critics contend that “[t]he precise way in which a Court deploys substantive canons of statutory construction reflects an underlying ‘ideology,’ or mix of values and strategies that the Court brings to statutory interpretation.”107 They are not, in any sense, “policy neutral.”108 Fourth Amendment Ruling Key Only a constitutional ruling on the NSA solves our advantages Blum, 2015 (Bill, former judge and death penalty defense attorney, “Why the ACLU’s big victory against NSA surveillance falls short,” truthdig, May 12, http://www.truthdig.com/report/item/why_the_aclus_big_victory_against_nsa_surveillance_falls_short _20150512) I don’t like to be a wet blanket, but at the risk of mixing metaphors, I’m going to throw some cold water on the decision last week in American Civil Liberties Union v. Clapper, which held that the National Security Agency’s vast telephone metadata collection program is illegal. While the ruling by the 2nd Circuit Court of Appeals is a clear advance for civil liberties—and the ACLU legal team that engineered it has every right to be proud—the advance, in fact, is modest and incremental. To understand why I’m less enthused than some others, let’s deconstruct what the decision actually said as well as what it didn’t say. The ACLU, in concert with its New York affiliate—the New York Civil Liberties Union—filed the case to have the NSA’s mammoth and indiscriminate surveillance sweeps conducted under Section 215 of the Patriot Act declared unconstitutional. They also sued to have the sweeps invalidated under the terms of the statute itself for exceeding the scope of the statute, and they sought an injunction to stop the sweeps. They succeeded only with their statutory claim. The unanimous 97-page opinion was penned by Judge Gerard Lynch—and joined by Judges Robert Sack and Vernon Broderick with a separate 13-page concurrence by Sack. Both Lynch and Sack are circuit court members, but Broderick is a district court judge designated to sit on the panel. (Appellate courts do this to give lower-court judges experience and to relieve staffing shortages.) All three were appointed to the bench by former President Bill Clinton. But then, so was William H. Pauley III, the U.S. District Court judge for the Southern District of New York whose earlier pro-government order dismissing the case was under appeal. Lynch’s opinion is a model of clarity but also of caution. He begins with a historical overview that takes us back to the bad old days of the early 1970s, when the intelligence agencies of the Nixon era were running roughshod over civil liberties. The Nixonian abuses begat the hearings of the famed select committee on intelligence headed by Sen. Frank Church that resulted in passage of the Foreign Intelligence Surveillance Act (FISA) of 1978 and the creation of the Foreign Intelligence Surveillance Court (FISC) that were designed to curb the abuses. Lynch’s narrative then fast-forwards through the attacks of 9/11 and the enactment of the Patriot Act in 2001. Section 215 of that legislation, together with subsequent revisions and congressional reauthorizations, amended FISA (as codified in 50 United States Code § 1861) to create the Frankenstein monster that is the NSA’s present telephone metadata program. As Lynch notes, Section 215 allows the FBI—on behalf of the NSA—to “make an application [to the FISC] for an order requiring the production of any tangible things (including books, records, papers, documents, and other items) for an investigation to obtain foreign intelligence information not concerning a United States person [meaning, basically, a citizen or lawful resident] or to protect against international terrorism or clandestine activities.” The section requires such applications to include “a statement of facts” showing that there are “reasonable grounds to believe the tangible things sought are relevant to an authorized investigation … to obtain foreign intelligence information. …” Astonishingly, the government has interpreted this language to mean that it can force telecom companies on an ongoing and easily renewable basis to turn over digital records of virtually every phone call made in the country. Such records reveal not only the length of each call but the number on each end of the call and sometimes the location of the callers. And far from acting as a gatekeeper winnowing out frivolous surveillance requests, the FISC—which convenes in secret and whose members are appointed by the Chief Justice of the Supreme Court—has performed as a rubber stamp, approving surveillance applications at a rate exceeding 99 percent. With this framework in place, the NSA has amassed a trove of metadata that it stores for rolling five-year periods, which it can access at any time with specific and detailed searches aimed at individual phone numbers. The key to understanding Lynch’s rejection of the government’s interpretation are the words “relevant” and “authorized investigation” as used in Section 215. Lynch’s discussion of the terms is masterful, but before parsing them, he first had to rebuff two preliminary objections by the Department of Justice—following a long-established litigation script—that the case should be dismissed to avoid an embarrassing ruling on the merits. First, Lynch held that the ACLU plaintiffs, as phone subscribers, had sustained the necessary legal injury to establish standing to sue. Second, he determined that the NSA’s practices may be examined in courts of general jurisdiction rather than solely by the FISC. As a result, he found the ACLU’s lawsuit was not blocked or precluded by any need to maintain state secrecy. Dispensing with the preliminaries, Lynch, to put it tenderly, proceeded to tear the government a proverbial new one, writing: “The records sought are all-encompassing; the government does not even suggest that all of the records sought, or even necessarily any of them, are relevant to any specific defined inquiry.” Exposing the absurdity of the government’s position, he continued: “[T]he government effectively argues that there is only one enormous ‘anti-terrorism investigation’’ and that any records that might ever be of use in developing any aspect of that investigation are relevant to the overall counterterrorism effort.” Lynch concluded that “such an expansive concept of ‘relevance’ is unprecedented and unwarranted.” He found, too, that Congress never intended to endorse such an astounding reading. From there, however, the decision largely fell apart, as Lynch not only refused to rule on the constitutionality of the NSA’s implementation of Section 215 but also declined to order the government to stop its bulk metadata collection program. Instead, he wound up kicking the case back to Pauley on the District Court for further consideration, and inviting Congress to weigh in on whether to redraft and revamp the metadata program before Section 215 is due to expire on June 1. To be fair to Lynch, judges often decline to make constitutional rulings when they can dispose of cases on lesser statutory grounds. Sometimes, however, judges are compelled to issue rulings on both statutory and constitutional bases, depending on the urgency of the matters before them or as a safeguard in the event that their statutory analyses are later found wanting by a higher court. The ACLU’s case plainly was sufficiently urgent to necessitate constitutional adjudication. To be fair again, it’s not as though Lynch ignored the constitutional concerns. In fact, he devoted 12 pages to what he termed the “vexing” Fourth Amendment questions implicated by the NSA’s data sweeps. But after noting the seriousness of the issues, he ducked them, citing a series of old Supreme Court opinions which instruct that individuals have no reasonable expectation of privacy under the Fourth Amendment in information (such as the phone numbers they dial) that they voluntarily turn over to third parties. The cited cases include the decision most frequently invoked by the DOJ to uphold the constitutionality of the NSA’s dragnet surveillance—Smith v. Maryland, a 1979 case that upheld the constitutionality of installing a pen register without a warrant at a telephone company’s office to record the numbers dialed from a criminal suspect’s home. In his concurrence, Sack ventured further, reminding us that one of the core functions of the judiciary is to examine the constitutionality of government actions. He even compared Edward Snowden’s disclosure of the metadata program to those of Daniel Ellsberg, which “gave rise to the legendary ‘Pentagon Papers’ litigation.” Alas, Stack’s views did not command a majority. So where does the 2nd Circuit’s decision leave us? In the absence of any directive halting the NSA’s practices, the practices will continue at least until June 1 and even after that for any “investigations” initiated before that date. Meanwhile, the spotlight is now on Congress, which has three basic options as the June 1 deadline approaches. None, regrettably, would fundamentally alter the landscape of government surveillance. Option No. 1 is to pass the USA Freedom Act, a version of which cleared the House in 2014 but has since stalled in the Senate. If this bill becomes law, telephone metadata would be stored by phone companies rather than the NSA. Intelligence agencies could still access the data, but only with FISC approval upon specific showings of need. As under current law, however, the attorney general could authorize limited data sweeps in an “emergency” for seven days before seeking court endorsement. The act would also make very minor changes to Section 702 of FISA (codified in 50 U.S.C. § 1881a) and the so-called PRISM and “upstream” programs designed under that section to intercept the content of emails and phone calls from terror suspects abroad. Unfortunately, as the NSA has acknowledged, such programs also “incidentally” sweep up the communications of Americans. Additionally, under the act, a panel of amicus curiae (friends of the court) would be established to give “independent” advice to the FISC on privacy matters, and more FISC decisions would be declassified. However, the act would not repeal Executive Order 12333, promulgated by President Reagan in 1981, which empowers intelligence agencies to do nearly everything that they can under Section 702 but without any court oversight. Both President Obama and Hillary Clinton have announced their support for the Freedom Act. Sen. Rand Paul has opposed the Freedom Act, arguing that it doesn’t go far enough to protect privacy interests. Option No. 2 for Congress would be to reject the USA Freedom Act and instead ratify the Patriot Act Reauthorization bill sponsored by Senate Majority Leader Mitch McConnell. The bill would leave the status quo entirely unchanged until December 31, 2020. The third option is for Congress to do nothing. Doing nothing would allow Section 215 to sunset and expire. But as tempting as that choice may seem from a civil liberties perspective, it would actually do little to rein in the NSA. As Harley Geiger of the Center for Democracy and Technology has written on the influential Lawfare blog, the NSA could simply substitute another provision of FISA (50 U.S.C. § 1842) dealing with electronic pen registers and trap devices that would similarly permit it to acquire bulk telephone and email metadata. What we’re involved in, it now seems clear, is a game of move and countermove. What then should our next move be? Politically, what we need at a minimum is an open, ongoing and informed national debate about the pervasive reach, cost, effectiveness and proper limits of government surveillance. Legally, at a minimum, we need judges willing to confront the full constitutional dimensions of whatever actions the legislative and executive branches undertake. A/T Statutory Interpretation Statutory interpretation doesn’t solve – fourth amendment decision is key Nelson, 2015 (Steven, “NSA phone record program illegal, appeals court finds,” US News & World Report, May 7, http://www.usnews.com/news/articles/2015/05/07/nsa-phone-record-program-illegalappeals-court-finds) “I don’t think that Congress alone giving an endorsement to these words would be sufficient under the says. “I think Congress would actually have to say very clearly what it was doing in order to get over that and then the question is whether that would survive [constitutional analysis].” Klayman, who like Cohn and many civil liberties advocates is unconvinced the Section 215-reforming Freedom Act goes far enough, is less pleased. “It was a total cop out,” he says. “We look for the D.C. Circuit to put its foot down and end this unconstitutional, illegal abuse of the surveillance system.” “Who’s to say, now that we’ve seen how the government violates the law, they don’t grab [the data] from Verizon and the other carriers surreptitiously?” he says. “That’s why there needs to be a clear-cut decision saying this is unconstitutional. It’s not a question of this statute or that statute, it’s a violation of the Fourth Amendment.” Klayman says the court’s decision not to issue an injunction to the ACLU, citing pending legislation, “is totally inappropriate, it’s playing politics” – a sentiment likely shared by some supporters of the collection within government. The NSA court’s analysis,” she referred questions about the decision to the White House’s National Security Council. Edward Price, a spokesman for the council, declined to comment directly on the ruling but said President Barack Obama remains supportive of legislation that would alter the collection. Attorney General Loretta Lynch, who oversees the attorneys who defend the NSA program, told a Senate subcommittee Thursday her staff was reviewing the decision and "we are also and have been working with this body and others to look for ways to reauthorize Section 215 in a way that does preserve its efficacy and protect privacy." Obama initially defended the collection but later pivoted and endorsed a new system that would allow the NSA to acquire records as needed from phone companies. Though he oversaw the existing collection with limited congressional input, he declined to make the change without legislation. ACLU Deputy Legal Director Jameel Jaffer, lead counsel on the appeal-winning case, suggested the decision is a larger step toward expanded privacy rights than may at first be appreciated. “This ruling focuses on the phone-records program, but it has far broader significance, because the same defective legal theory that underlies this program underlies many of the government’s other mass-surveillance programs,” Jaffer said in a statement. “The ruling warrants a reconsideration of all of those programs, and it underscores once again the need for truly systemic reform.” DA 2ACs General A/T Impacts Prefer our impacts – structural incentives lead to exaggeration of all threats used to justify NSA surveillance. Giving in to this threat exaggeration causes intelligence arms races that cause their impacts Glennon, 2014 (Michael J., Professor of International Law, Fletcher School of Law and Diplomacy, Tufts University, “National Security and Double Government,” Harvard National Security Journal, 5 Harv. Nat’l Sec. J. 1) The Trumanites' propensity to define security in military and intelligence terms rather than political and diplomatic ones reinforces a powerful structural dynamic. That dynamic can be succinctly stated: Overprotection of national security creates costs that the Trumanite network can externalize; under-protection creates costs that the network must internalize. The resulting incentive structure encourages the exaggeration of existing threats and the creation of imaginary ones. The security programs that emerge are, in economic terms, "sticky down"--easier to grow than to shrink. The Trumanites sacrifice little when disproportionate money or manpower is devoted to security. The operatives that they direct do not [*27] incur trade-off costs. n152 The Trumanites do, however, reap the benefits of that disproportionality--a larger payroll, more personnel, broader authority, and an even lower risk that they will be blamed in the event of a successful attack. n153 Yet Madisonian institutions incur the costs of excessive resources that flow to the Trumanites. The President must submit a budget that includes the needed taxes. Members of Congress must vote for those taxes. A federal agency must collect the taxes. When it comes to picking up the tab, Trumanites are nowhere to be seen. If national security protection is inadequate, on the other hand, the Trumanites are held accountable. They are the experts on whom the Madisonian institutions rely to keep the nation safe. They are the recipients of Madisonian largesse, doled out to ensure that no blame will be cast by voters seeking retribution for a job poorly done. In the event of a catastrophic attack, the buck stops with the Trumanites. No Trumanite craves to be the target of a 9/11 commission following a catastrophic failure. Thus they have, as Jeffrey Rosen put it, an "incentive to exaggerate [*28] risks and pander to public fears" n154 --"an incentive to pass along vague and unconfirmed threats of future violence, in order to protect themselves from criticism" n155 should another attack occur. Indeed, a purely "rational" actor in the Trumanite network might hardly be expected to do anything other than inflate threats. In this way, the domestic political dynamic reinforces the security dilemma familiar to international relations students, the quandary that a nation confronts when, in taking steps to enhance its security, it unintentionally threatens the security of another nation and thus finds its own security threatened when the other nation takes compensatory action. n156 An inexorable and destabilizing arms race is thereby fueled by seemingly rational domestic actors responding to seemingly reasonable threats-threats that they unwittingly helped create. The budget figures, compiled by David Sanger, n157 reflect the incentive structure within which the Trumanite network has emerged and thrives. Over the last decade the defense budget has grown 67% in real terms. n158 It now is 50% higher than it was for an average year during the Cold War n159 --greater than the spending of the next twenty largest military powers combined. n160 During the decade following the 9/11 attacks, the United States spent at least $ 3.3 trillion responding to the attacks. n161 This represents $ 6.6 million for every dollar al Qaeda spent to stage the attacks. n162 It is unclear the extent to which the specific threats at which the Obama national security policy is directed have been inflated; that information is classified, and the handful of Trumanites in a position to [*29] know the truth of the matter can hardly be expected to disclose it. n163 No reliable outside threat assessment is available. Although it is the Madisonians, not the Trumanites, who are expert in assessing the preferences of the public, including public risk tolerance--the Madisonians are the ones who hear out constituents, litigants, and lobbyists--the only way to know whether more insurance is needed is to ask the same Trumanite network that will gladly provide it. If the precise nature of the threatened harm is uncertain, what is not uncertain is the fear of threats, which is essential to the maintenance of the Trumanite network's power--for the fundamental driver of Trumanite power has been emergency, the appearance of threats that must be addressed immediately, without bringing in the Madisonian institutions. "[A]n entire era of crisis in which urgent decisions have been required again and again," n164 in the words of Senator J. William Fulbright, has given rise to the Trumanites' power. Speedy decisions are required that the Madisonian institutions are illequipped to make; the Trumanites have the means at their disposal to act quickly. The perception of threat, crisis, and emergency has been the seminal phenomenon that has created and nurtures America's double government. A/T Terror DA No link – no need for extraordinary process to get necessary records Wyden et al, 2013 (Ron, Mark Udall, and Martin Heinrich, “End the N.S.A. Dragnet, now,” NYT, November 25, http://www.nytimes.com/2013/11/26/opinion/end-the-nsa-dragnet-now.html) Our first priority is to keep Americans safe from the threat of terrorism. If government agencies identify a suspected terrorist, they should absolutely go to the relevant phone companies to get that person’s phone records. But this can be done without collecting the records of millions of law­abiding Americans. We recall Benjamin Franklin’s famous admonition that those who would give up essential liberty in the pursuit of temporary safety will lose both and deserve neither. The usefulness of the bulk collection program has been greatly exaggerated. We have yet to see any proof that it provides real, unique value in protecting national security. In spite of our repeated requests, the N.S.A. has not provided evidence of any instance when the agency used this program to review phone records that could not have been obtained using a regular court order or emergency authorization. A/T Terror DA – TMI NSA surveillance is too broad to be effective; causes abuse and exploitation Schneirer, 2014 (Bruce, contributing writer for The Atlantic and the chief technology officer of the computer-security firm Co3 Systems, “How the NSA threatens national security,” The Atlantic, January 6, http://www.theatlantic.com/technology/archive/2014/01/how-the-nsa-threatens-nationalsecurity/282822/) The NSA's collect-everything mentality is largely a hold-over from the Cold War, when a voyeuristic interest in the Soviet Union was the norm. Still, it is unclear how effective targeted surveillance against "enemy" countries really is. Even when we learn actual secrets, as we did regarding Syria's use of chemical weapons earlier this year, we often can't do anything with the information. Ubiquitous surveillance should have died with the fall of Communism, but it got a new—and even more dangerous—life with the intelligence community's post-9/11 "never again" terrorism mission. This quixotic goal of preventing something from happening forces us to try to know everything that does happen. This pushes the NSA to eavesdrop on online gaming worlds and on every cell phone in the world. But it's a fool's errand; there are simply too many ways to communicate. We have no evidence that any of this surveillance makes us safer. NSA Director General Keith Alexander responded to these stories in June by claiming that he disrupted 54 terrorist plots. In October, he revised that number downward to 13, and then to "one or two." At this point, the only "plot" prevented was that of a San Diego man sending $8,500 to support a Somali militant group. We have been repeatedly told that these surveillance programs would have been able to stop 9/11, yet the NSA didn't detect the Boston bombings—even though one of the two terrorists was on the watch list and the other had a sloppy social media trail. Bulk collection of data and metadata is an ineffective counterterrorism tool. Not only is ubiquitous surveillance ineffective, it is extraordinarily costly. I don't mean just the budgets, which will continue to skyrocket. Or the diplomatic costs, as country after country learns of our surveillance programs against their citizens. I'm also talking about the cost to our society. It breaks so much of what our society has built. It breaks our political systems, as Congress is unable to provide any meaningful oversight and citizens are kept in the dark about what government does. It breaks our legal systems, as laws are ignored or reinterpreted, and people are unable to challenge government actions in court. It breaks our commercial systems, as U.S. computer products and services are no longer trusted worldwide. It breaks our technical systems, as the very protocols of the Internet become untrusted. And it breaks our social systems; the loss of privacy, freedom, and liberty is much more damaging to our society than the occasional act of random violence. And finally, these systems are susceptible to abuse. This is not just a hypothetical problem. Recent history illustrates many episodes where this information was, or would have been, abused: Hoover and his FBI spying, McCarthy, Martin Luther King Jr. and the civil rights movement, anti-war Vietnam protesters, and—more recently—the Occupy movement. Outside the U.S., there are even more extreme examples. Building the surveillance state makes it too easy for people and organizations to slip over the line into abuse. It's not just domestic abuse we have to worry about; it's the rest of the world, too. The more we choose to eavesdrop on the Internet and other communications technologies, the less we are secure from eavesdropping by others. Our choice isn't between a digital world where the NSA can eavesdrop and one where the NSA is prevented from eavesdropping; it's between a digital world that is vulnerable to all attackers, and one that is secure for all users. A/T Terror DA – Trust DA Expansive NSA surveillance ruins public trust Schnier, 2013 (Bruce, contributing writer for The Atlantic and the chief technology officer of the computer-security firm Co3 Systems, “The only way to restore trust in the NSA,” The Atlantic, September 4, http://www.theatlantic.com/politics/archive/2013/09/the-only-way-to-restore-trust-inthe-nsa/279314/) I've recently seen two articles speculating on the NSA's capability, and practice, of spying on members of Congress and other elected officials. The evidence is all circumstantial and smacks of conspiracy thinking -- and I have no idea whether any of it is true or not -- but it's a good illustration of what happens when trust in a public institution fails. The NSA has repeatedly lied about the extent of its spying program. James R. Clapper, the director of national intelligence, has lied about it to Congress. Top-secret documents provided by Edward Snowden, and reported on by the Guardian and other newspapers, repeatedly show that the NSA's surveillance systems are monitoring the communications of American citizens. The DEA has used this information to apprehend drug smugglers, then lied about it in court. The IRS has used this information to find tax cheats, then lied about it. It's even been used to arrest a copyright violator. It seems that every time there is an allegation against the NSA, no matter how outlandish, it turns out to be true. Guardian reporter Glenn Greenwald has been playing this well, dribbling the information out one scandal at a time. It's looking more and more as if the NSA doesn't know what Snowden took. It's hard for someone to lie convincingly if he doesn't know what the opposition actually knows. All of this denying and lying results in us not trusting anything the NSA says, anything the president says about the NSA, or anything companies say about their involvement with the NSA. We know secrecy corrupts, and we see that corruption. There's simply no credibility, and -- the real problem -- no way for us to verify anything these people might say. It's a perfect environment for conspiracy theories to take root: no trust, assuming the worst, no way to verify the facts. Think JFK assassination theories. Think 9/11 conspiracies. Think UFOs. For all we know, the NSA might be spying on elected officials. Edward Snowden said that he had the ability to spy on anyone in the U.S., in real time, from his desk. His remarks were belittled, but it turns out he was right. Public trust key to solve terrorism Perlez and Sciolino, 2007 (Jane and Elaine, “Openness sought in British terror trials,” NYT, May 25, http://www.nytimes.com/2007/05/25/world/europe/25britain.html?_r=0) Mr. Clarke lamented the breakdown in the public’s trust of the police, and the public’s unwillingness to “accept the government’s explanation of the threat” of terrorism. Public criticism that the police were no longer impartial players has hurt their ability to win the confidence of the public. “It is now difficult for the police service, and I suspect others, to express a professional opinion on the subject without being accused of falling on one side or the other in what it seems to me an increasingly wide political divide,” he said. The lack of trust in the police also severely affected the ability to collect important information from the public that could help tip them off to potential plots. The British police obtain most of their intelligence about terrorist planning from classic methods, including electronic surveillance and foreign sources, he said, but very little from local residents. Recent cases in which the police arrested terrorism suspects in Britain, held them for questioning and then released them without charges have created doubts about the integrity of law enforcement, he said. “It is no exaggeration to say the lack of public trust in intelligence is in danger of infecting the relationship between the police and the communities we serve,” he said. A/T “One Voice” – Non-Unique The “one-voice doctrine” is a common justification for judicial deference that says that other branches may not engage in foreign affair Non-unique – Court is interfering in foreign affairs now Moore, 2014 (David, Professor of Law, J. Reuben Clark Law School, Brigham Young University, “Beyond one voice,” Minnesota Law Review, February, 98 Minn. L. Rev. 953) This does not mean "that every case or controversy which touches foreign relations lies beyond judicial cognizance." n33 As noted, just recently in Zivotofsky the Supreme Court concluded that a dispute between the President and Congress regarding the status of Jerusalem as the capital of Israel was justiciable notwithstanding Justice Breyer's one-voice argument to the contrary in dissent. n34 In light of Zivotofsky, the current trajectory is arguably toward a greater judicial role, and thus more voices, in resolving disputes touching on foreign affairs. n35 In harmony with this trend in cases implicating the political question doctrine, the one-voice doctrine leads to lesser shades of deference in other cases. The Zadvydas v. Davis n36 case in the foreign relations area of immigration exemplifies this end of the deference spectrum. The Zadvydas Court implied a statutory limitation on the government's ability to detain aliens who had been ordered removed. n37 In so doing, the Court rejected the government's argument that "a federal habeas court would have to accept the Government's view about whether the implicit statutory limitation is satisfied in a particular case, conducting little or no independent review of the matter." n38 Instead, the Court merely recognized the need to [*965] conduct its review with sensitivity to, among other things, "the Nation's need to "speak with one voice.'" n39 The one-voice doctrine thus extracted only relatively weak deference to the executive's immigration judgments. n40 Moore, 2014 (David, Professor of Law, J. Reuben Clark Law School, Brigham Young University, “Beyond one voice,” Minnesota Law Review, February, 98 Minn. L. Rev. 953) The doctrine is likewise hard to square with case law that recognizes room for the judiciary in foreign affairs. The courts employ a number of doctrines - some generic, some unique to foreign relations law - to police judicial involvement in foreign affairs. Among the generic doctrines are standing, n271 ripeness, n272 [*1008] mootness, n273 personal jurisdiction, n274 forum non conveniens, n275 Chevron deference, n276 and political question. n277 While in many cases these doctrines serve to limit judicial involvement in foreign affairs matters, in other cases they do not. Thus, in its seminal political question opinion, the Court explained that, while there are issues the judiciary will not decide, "it is error to suppose that every case or controversy which touches foreign relations lies beyond judicial cognizance." n278 The Court listed a variety of issues that fit within judicial cognizance, such as whether a treaty preempts particular state laws and whether, in the absence of executive clarity, a foreign war exists that triggers statutes securing U.S. neutrality. n279 The Court's recent opinion in Zivotofsky reaffirmed the judiciary's role over certain [*1009] foreign affairs issues n280 and may signal a retreat from the political question doctrine in foreign affairs. As discussed previously, the question presented was whether Congress could statutorily require the executive to list Israel on the passport of someone born in Jerusalem notwithstanding the President's "power to recognize foreign sovereigns" n281 and the State Department's "longstanding policy of not taking a position on the political status of Jerusalem." n282 The Court rejected the lower courts' dismissal of the case on political question grounds. n283 The judiciary could properly resolve the question. n284 Just as the Court found room for the judiciary in deciding the separation of powers question in Zivotofsky, the Court has asserted a role in policing state action even when the executive is unconcerned about that action. n285 Other foreign affairs doctrines similarly calibrate, rather than eliminate, the judiciary's involvement in foreign affairs. n286 Under the act of state doctrine, U.S. courts "will generally refrain from ... sitting in judgment on ... acts of a governmental character done by a foreign state within its own territory and applicable there." n287 However, if there is clear international law that governs the foreign state's conduct or if the concerns motivating the doctrine are not implicated even though the doctrine technically applies, courts will disregard the doctrine and independently [*1010] assess the legality of the foreign sovereign's acts. n288 Similarly, courts exercise ultimate discretion to decide whether to apply the act of state doctrine when the executive has represented that the doctrine need not apply. n289 Under principles of international comity, courts may abstain from exercising jurisdiction in cases involving the executive, legislative, or judicial acts of foreign states. n290 Pursuant to jurisdiction provided by the Alien Tort Statute, federal courts hear limited claims based on customary international law. n291 Invoking the Charming Betsy [*1011] canon, courts work to interpret federal statutes to avoid infractions of international law unless Congress has manifested intent to violate. n292 Similarly, in applying the presumption against extraterritoriality, courts interpret federal statutes to apply only domestically absent clear evidence of congressional intent to the contrary. n293 And under the range of deference given to the executive in the realm of foreign affairs, courts give more or less weight to the executive's position in foreign affairs cases. n294 The result is that while the courts recognize limits to their participation in foreign affairs matters, n295 those limits fall well short of outright exclusion. Many doctrines recognize a role for the judiciary in foreign relations. The room left for the judiciary results in disagreements between the political branches and the courts. n296 Even recently, the Court has rejected foreign relations-related positions taken by both the President and Congress. For example, in Zivotofsky, the Court rejected the executive's claim that a challenge to the executive's refusal to follow a statute endorsing Jerusalem as the capital of Israel presented a political question. n297 In Medellin v. Texas, the Court concluded that the President lacked unilateral authority to execute an otherwise non-self- [*1012] executing International Court of Justice (ICJ) judgment. n298 And in Boumediene, the Court concluded that Congress had unconstitutionally attempted to deny the writ of habeas corpus to detainees at Guantanamo. n299 In its separation of powers dimensions, then, the one-voice doctrine contends with a practice that involves multiple federal players. Non-unique, the US never speaks with one voice in foreign affairs Knowles, 2009 (Robert, Acting assistant Professor, New York University School of Law, “American Hegemony and the Foreign Affairs Constitution,” Arizona State Law Journal, 41 Ariz. St. L.J. 87, October) The one-voice rationale is in one sense not functionalist at all, but a formal essentialist assertion about the scope of the Constitution’s allocation of powers. To the extent that it is functional, it must rest entirely on other rationales. One of the potential rationales is as follows: because the President is the only unitary, centralized branch of government,274 only the President can truly speak with one voice and is therefore the only branch that can suitably represent a unitary entity in the international arena. But as has been frequently observed, the United States has never strictly spoken “with one voice” in foreign affairs.275 The Constitution’s text allocates foreign affairs powers to both the Congress and the President.276 In practice, Congress has from time to time disagreed with the President, even regarding highly sensitive national security matters.277 And the courts have, from the very beginning, rejected executive branch interpretations of treaties.278 Although the separation of powers has been criticized as interfering with the ability of the United States to form a unified foreign policy, this is the government that the Constitution created.279 The onevoice argument simply does not hold up to scrutiny, at least in its strong form. But there are other rationales for a weaker form—embarrassment and accountability. A/T “One Voice” Speaking with multiple voices isn’t a problem at all Knowles, 2009 (Robert, Acting assistant Professor, New York University School of Law, “American Hegemony and the Foreign Affairs Constitution,” Arizona State Law Journal, 41 Ariz. St. L.J. 87, October) Moreover, it is entirely possible that other nations would be content with conflicting decisions from different branches of the U.S. government. Suppose that the President roundly condemns the offensive court decision and declares the judge to be an “activist.” If the damage done by the court decision was largely dignitary, an angry denouncement from the executive branch may be all that is needed. Past empires relied on multi-vocal signaling to maintain imperial rule.396 But with the advent of globalization, intra-executive branch multi-vocality is much more difficult because advances in communication permit various parts of the “rim” to communicate with one another .397 The American separation-of-powers system provides a way around this problem, allowing the U.S. government to “speak in different voices” at once. A/T Courts Link to Politics Courts don’t link to politics- avoids political fallout Whittington 5 (Keith E., Professor of Politics - Princeton University, "Interpose Your Friendly Hand: Political Supports for the Exercise of Judicial Review by the United States Supreme Court”, The American Political Science Review, Nov., (99)4, p. 583) There are some issues that politicians cannot easily handle. For individual legislators, their constituents may be sharply divided on a given issue or overwhelmingly hostile to a policy that the legislator would nonetheless like to see adopted. Party leaders, including presidents and legislative leaders, must similarly sometimes manage deeply divided or cross-pressured coalitions. When faced with such issues, elected officials may actively seek to turn over controversial political questions to the courts so as to circumvent a paralyzed legislature and avoid the political fallout that would come with taking direct action themselves. As Mark Graber (1993) has detailed in cases such as slavery and abortion, elected officials may prefer judicial resolution of disruptive political issues to direct legislative action, especially when the courts are believed to be sympathetic to the politician's own substantive preferences but even when the attitude of the courts is uncertain or unfavorable (see also, Lovell 2003). Even when politicians do not invite judicial intervention, strategically minded courts will take into account not only the policy preferences of well-positioned policymakers but also the willingness of those potential policymakers to act if doing so means that they must assume responsibility for policy outcomes. For cross-pressured politicians and coalition leaders, shifting blame for controversial decisions to the Court and obscuring their own relationship to those decisions may preserve electoral support and coalition unity without threatening active judicial review (Arnold 1990; Fiorina 1986; Weaver 1986). The conditions for the exercise of judicial review may be relatively favorable when judicial invalidations of legislative policy can be managed to the electoral benefit of most legislators. In the cases considered previously, fractious coalitions produced legislation that presidents and party leaders deplored but were unwilling to block. Divisions within the governing coalition can also prevent legislative action that political leaders want taken, as illustrated in the following case. Courts don’t link to politics- evades electoral consequences Stoutenborough et al. 6 (James, Political Science Dept @ Utah, Reassessing the Impact of Supreme Court Decisions on Public Opinion, Political Research Quarterly, p. 419) In many cases, courts have been empowered by and served the interests of other political actors. While this undermines the countermajoritarian difficulty as an empirical hypothesis, it is not at all reassuring from a democratic perspective. Judicial review can provide an opportunity for elected political actors to evade responsibilities or to pursue policies while evading electoral consequences. Such actions may enhance or enable domination by letting those actors pursue policies that might lead to domination without suffering electoral consequences. The possibility that judicial review can provide another outlet that permits legislators to "run from daylight"85 and effect important policy changes with a minimum of public scrutiny is a serious concern, and may especially contribute to domination by powerful economic elites. An additional concern is that judicial review can have the perverse effect of making legislators less attentive to their constitutional responsibilities, as they may vote for legislation they believe to be unconstitutional under the assumption that the courts will correct their mistake.86 Courts don’t link to politics- shielded from political pressure Ward 9 (Artemus, Professor @ NIU, Political Foundations of Judicial Supremacy, Congress and The Presidency, pg. 119) After the old order has collapse the once- united, new-regime coalition begins to fracture as original commitments are extended to new issues. In chapter 3 Whittington combines Skowronek's articulation and disjunctive categories into the overarching "affiliated" presidencies as both seek to elaborate the regime begun under reconstructive leaders. By this point in the ascendant regime, Bourts are staffed by justices from the dominant ruling coalition via the appointment process - and Whittington spends time on appointment politics here and more fully in chapter 4. Perhaps counter-intuitively, affiliated political actors - including presidents - encourage Courts to exercise vetoes and operate in issue areas of relatively low political salience. Of course, this "activism" is never used against the affiliated president per se. Instead, affiliated Courts correct for the overreaching of those who operate outside the preferred constitutional vision, which are often state and local governments who need to be brought into line with nationally dominant constitutional commitments. Whittington it is easier for affilitated judges, rather than affiliated presidents, to rein in outliers and conduct constitutional maintenance. The latter are saddled with controlling opposition political figures, satisfying short-term political demands, and navigating intraregime gridlock and political thickets. Furthermore, because of their electoral accountability, politicians engage in position-taking, credit-claiming, and blame-avoidance behavior. By contrast, their judicial counterparts are relatively sheltered from political pressures and have more straightforward decisional processes. Activist Courts can take the blame for advancing and legitimizing constitutional commitments that might have electoral costs. In short, a division of labor exists between politicians and explains why judges affiliated with the dominant regime. 1999). A/T Reverse Politics – Perm Solves Perm solves the net benefit – only congress and the president get perceived CSM 97(Christian Science Monitor, “Why America Puts Its Supreme Court On Lofty Pedestal,” June 25, Lexis) Today this holds true even more. In one sense, the reason is obvious: With divided government and partisan sniping in Washington, when politicians must create a TV image and constantly raise funds, the scholarly-looking justices seem a refreshing alternative. They come out in black robes from behind red silk curtains, and everyone stands. They ask incisive questions. They disappear. It looks like competence personified. And there's some truth to it. The members of the court don't need to campaign for office every few years. They were selected for life. They don't need speech writers or have to check the polls. The current justices, unlike earlier courts, generally write their own opinions. They are free to dissent, and their rulings are not tied to interest-group pressure. Moreover, as an institution, the court is uniquely constituted. It is not one targetable political persona, as is a single chief executive. Yet it is smaller than a Congress of 535 people. Congress is covered by TV four times as much as the court is. The White House is covered eight times as much, says Lee Epstein of Washington University in St. Louis. The court stands out now because it is not part of Washington's political swamp. The carefully cultivated aloofness of the Supreme Court is, in the Washington scene, almost countercultural in nature. The court's warts don't show. "People don't see the court infighting; it seems more harmonious and less political," says one court-watcher. "With Congress and the White House, we see the blood-letting on the street." Importantly, say scholars, current justices benefit from courageous stands the court took in cases like Brown school desegregation, and the Roe abortion-rights case - when the majority was fragile and the justices felt under great pressure. Those decisions are a main reason the court image is so buffed today. Justices Don't Have to Wade in Washington Swamp A/T Activism = Backlash It is the broad opinion of the Court and Public that affect public popularity, not one particular decision Caldeira and Gibson 92 (Gregory and James, Ann and Darrell Dreher Chair in Political Communication and Policy Thinking at The Ohio State University, “The Etiology of Public Support for the Supreme Court”, American Journal of Political Science, Vol. 36 No. 3, August 1992, JSTOR) For all these reasons, now is an appropriate juncture at which to reexamine the levels, sources, and explanations of public support for the Supreme Court. On the methodological front, we offer an alternative means of thinking about and capturing diffuse support for the Court among the mass public. On the substantive front, we articulate and then test a series of explanations of the etiology of support for the Court. Naturally, we examine the traditional explanations of diffuse support (Murphy, Tanenhaus, and Kastner 1973), but, more important, we introduce and demonstrate the explanatory power of a new set of variables, political values. For the mass public, contrary to previous research, we find no connection between support for specific policies and diffuse support for the Supreme Court. Instead, broad political values—commitment to social order and support for democratic norms—do a good job of predicting attitude toward the Supreme Court . We then consider the important role of “opinion leaders” as supporters of the Supreme Court. In contrast to the mass public, opinion leaders show a greater tendency to link support for the Supreme Court to the satisfaction of specific policy preferences. Finally, we place these results within the context of change by suggesting some of the crucial components of a broader theory of the ebb and flow of support and conclude with speculation on the consequences of attitudes among the mass public and elites for the effective functioning and resilience of the Supreme Court. A/T No Enforcement Other actors will implement the court’s decision regardless of the action Baum 1999 (Lawrence, Prof of Constitutional Law Ohio State University, The Supreme Court p. 22) Acceptance of the Court’s Authority. Policy makers may implement the Supreme Court’s decision even when they have incentives to resist them. One important reason is the Court’s authority as interpreter of the law. Most people believe that the Court’s decisions are authoritative judgments about the law and that there is an obligation to comply with those decisions. Largely as a result the Court’s association with an unpopular policy may help to foster public acceptance of that policy. For the same reason, even officials who are disposed to disobey the courts decisions may choose not to do so. Certainly a policy maker who is indifferent toward a Supreme Court policy will be inclined to go along because of the Court’s authority The executive wont flout court decisions even if they’re controversial. Christina Wells. 2004. Missouri Law Review. 69 Mo. L. Rev. 903] The judicial system is a powerful institution. In the context of resolving constitutional issues, many people, the Court included, believe that the judicial system has the final (and, thus, most powerful) say. 227 To be sure, executive officials, past and present, have asserted that national security matters are particularly within the executive branch's ambit, suggesting that they do not share this view of the Court's legitimacy. 228 Even so, executive officials rarely flout the Court's authority, instead preferring to enlist the Court's support (which the Court often willingly provides). Executive officials might prove more willing to deny the Court's authority if it engaged in more rigorous review of executive decisions regarding national security. However, popular support for the institution of judicial review would likely preclude outright executive defiance 229 and could eventually spur acceptance. This might be especially true if the Court's constitutional standards of review focused more explicitly on decision-making processes, thus avoiding the impression that the Court was substituting its judgment for the executive's. Their evidence only applies to lower courts – Agencies think the Supreme Court’s word is final Michael J. Froehlich, January 1985, The George Washington Law Review, 53 Geo. Wash. L. Rev. 147 Agencies that decline to follow circuit court rulings contend that only the Supreme Court's decisions interpreting statutes and congressional directives are binding on agencies' implementation of national programs. An agency will not necessarily appeal an adverse decision to the Supreme Court, however, or petition Congress to clarify the statute in question, but will simply ignore circuit court precedent in future adjudications within the circuit. Agencies usually follow Richard J. Pierce, Professor of Law, Columbia University, April 1993, Duke Law Journal, 42 Duke L.J. 1170 The opinion concluded that any injury the plaintiff might suffer was not redressable for two reasons. First, because the Department of the Interior was the only agency that was a party to the case, a judicial opinion holding that the Endangered Species Act requires agencies to consult with the Department before funding overseas projects that are likely to have adverse effects on endangered species would bind only the Department and not other agencies. Thus, other federal agencies would be free to ignore the Court's decision if it were to invalidate the Department's rule. That reasoning is inconsistent with precedent. More fundamentally, it ignores the reality that all federal agencies routinely conform their conduct to decisions of the Supreme Court. If the Court were to hold that agencies must consult with the Department of the Interior, the agencies would do so. The opinion itself recognizes that the applicable standard is whether a judicial decision is "likely" to redress the plaintiff's injury. Is the Court seriously suggesting that federal agencies are unlikely to comply with a Supreme Court decision? A/T Legitimacy Turn – Controversial decisions boost legitimacy – positivity bias outweighs and turns any backlash into support Gibson and Caldiera 9 (James L., Professor of Government – Washington University and Fellow – Centre for Comparative and International Politics, and Gregory A., Distinguished University Professor in Political Communications and Policy Thinking – Ohio State University, Citizens, Courts, and Confirmations, http://press.princeton.edu/chapters/s8940.pdf) How is it that the United States Supreme Court avoided any harmful consequences of the election imbroglio? Again, positivity bias. According to this theory, discussed more completely below, anything that causes people to pay attention to courts—even controversies—winds up reinforcing institutional legitimacy through exposure to the legitimizing symbols associated with law and courts. The theory suggests a bias in favor of developing positive feelings for the institution, even during conflicts, and even among losers in such conflicts. While there are many elements to this Gibson, Caldeira, and Spence (2003a) have proffered an answer: the theory of theory, its central prediction is that legal controversies tend to reinforce judicial legitimacy by teaching the lesson that courts are different from the other institutions of the American democracy, and are therefore worthy of respect. No Link – Court overrules all the time, one more decision not key Paul Linton, j.d. loyal university of Chicago, St. Louis public law review. 1993, 13 St. Louis U. Pub. L. Rev. 15 The Court describes this first circumstance as "hypothetical." 272 The distinct impression left by this passage is that decisions of the Supreme Court overruling earlier decisions on matters of constitutional interpretation are rare and thus should not be too readily emulated, lest the "legitimacy" of the Court be called into question. But this impression is wrong. On more than 200 occasions, the Court has overturned previous decisions, and in nearly three-fourths of those cases, the Court overruled because the earlier decision had wrongly interpreted the Constitution . 273 What does this remarkable track re [*75] cord of "judicial correction" mean? At the very least, that the "legitimacy" of the Court is not affeced by its acknowledgement of prior error, even when that error involved an intepretation of the Constitution. Indeed, as in Brown and West Coast Hotel, the Court has often enhanced its credibility by overruling decisions that were wrong when originally decided. One more overruling decision, if otherwise appropriate, could not reasonably be expected to damage that credibility. No Impact – Legitimacy resilient – history proves Gibson and Caldiera 9 (James L., Professor of Government – Washington University and Fellow – Centre for Comparative and International Politics, and Gregory A., Distinguished University Professor in Political Communications and Policy Thinking – Ohio State University, Citizens, Courts, and Confirmations, http://press.princeton.edu/chapters/s8940.pdf) Our contention, however, is that the effects of popular and unpopular decisions are asymmetrical. Popular decisions generate unadulterated support for the Court, just as they do for any institution. But the effects of unpopular decisions are discounted, both by processes of shirking and by association with the legitimizing symbols of judicial power. We acknowledge that the decline of institutional legitimacy could become a nonlinear, cascading process in the sense that as the Court’s reservoir of support becomes shallower, the impact of . 9 unpopular decisions grows. We know of no such cascade in American history, however Our objective in this book is to determine whether politicized confirmation processes can have a delegitimizing effect on the Supreme Court by providing an image of the 9 Court incompatible with the processes undergirding positivity theory. [Continues – To Footnote] In all of our thinking about these processes, we are much influenced by Roosevelt’s attacks on the Supreme Court in the 1930s. If an enormously popular president, stimulated to action by a continuous string of unpopular and crippling Supreme Court decisions, cannot succeed in changing the Court, it is difficult to imagine a scenario in which such attacks would succeed. At the same time, however, Gibson and Caldeira (1992) point to declining support for the Supreme Court among some segments of the African American community from roughly theWarren Court era to the Rehnquist Court, so clearly a diminution of Court support is possible. Gaining a greater understanding of the processes of change in Court support is precisely the objective of this book. Politics – Popular – Tech Tech companies support restrictions on NSA surveillance Kosner, 2013 (Anthony Wing, “All major tech companies say NSA actions put public trust in internet at risk,” Forbes, December 9, http://www.forbes.com/sites/anthonykosner/2013/12/09/all-major-techcompanies-say-nsa-actions-puts-public-trust-in-internet-at-risk/) America’s biggest tech companies have gone from begging congress for surveillance reform, as Kashmir Hill taking their case to President Obama and members of Congress directly in an open letter published today. At risk is the public’s trust in the internet itself and all of the economic and cultural benefits it contains. The letter, signed by AOL, Apple, Facebook, Google, LinkedIn, Microsoft, Twitter and Yahoo, urges the reported here at the end of October, to U.S. to “take the lead and make reforms that ensure that government surveillance efforts are clearly restricted by law, proportionate to the risks, transparent and subject to independent oversight.” Microsoft’s general counsel, Brad Smith, released a statement asserting that, “People won’t use technology they don’t trust. Governments have put this trust at risk, and governments need to help restore it.” This is a striking development given the varying degree to which these same companies have cooperated and/or collaborated with the NSA’s data collection efforts. Clearly the balance has tipped and America’s tech companies now feel emboldened to call for sweeping reforms even as the Democratic chair of the Senate Intelligence Committee, Dianne Feinstein of California, is sponsoring a bill maintain the security agencies’ right to continue to collect bulk data. The Big-8, with a combined valuation of $1.4 trillion, are trying to convince their billions of users worldwide that they can still trust American tech companies. “For our part,” the open letter reads, “we are focused on keeping user’s data secure — deploying the latest encryption technology to prevent unauthorized surveillance on our networks and by pushing back on government requests to ensure that they are legal and reasonable in scope.” Those companies have huge influence Harbert, 2012 (Tam, “Internet giants adopt new lobbying tactics,” IEEE Spectrum, September 27, http://spectrum.ieee.org/telecom/internet/internet-giants-adopt-new-lobbying-tactics) Regardless of which party controls the U.S. government after next month’s elections, Washington’s interest in how Internet companies use customers’ data will continue to grow, and so these tech companies have recognized the need to spend more money on lobbying legislators. Unlike with some other industries, however, their investment is not limited to traditional lobbying methods. They are looking to their users to put pressure on Congress as well. Computer and Internet companies have enlisted elite firms clustered on Washington, D.C.’s K Street in their efforts, according to Bill Allison, editorial director at the Sunlight Foundation, a nonprofit organization that promotes government transparency by putting information online. Google even hired former congresswoman Susan Molinari earlier this year to head its Washington office. The companies have also been inching up their spending. Last year, the computer and Internet industry spent US $127 million on lobbying, up from $123 million in 2010 and $120 million in 2009, according to the Center for Responsive Politics (CRP). Spending is trending up again this year, at least by a few million, based on the $65 million figure for the first six months. The most notable increases, however, are by two of the hottest U.S. Internet companies. Google’s lobbying costs are on track to have nearly quadrupled in the past two years, rising to $9 million in the first half of 2012, according to tallies by the CRP. In fact, last year Google surpassed all other companies in the computer and Internet category, beating the previous top spender—Microsoft—by more than $2 million. Facebook’s spending has also quickly accelerated but is still just a fraction of Google’s. But this year, tech companies also discovered new political muscle when a grassroots campaign rallied Internet users to petition Congress, leading to the defeat of the Stop Online Piracy Act (SOPA). The bill would have required websites and search engines to cut off access to non-U.S sites that the government suspects of copyright infringement. Key Internet companies— including Microsoft, Google, Yahoo, Facebook, and Twitter—opposed SOPA. But what got the most attention were constituent complaints, which were encouraged by Internet rights advocates such as Fight for the Future, Engine Advocacy, and the Center for Democracy and Technology (CDT). The tech companies rode that groundswell of public opinion; Wikipedia blacked out its website in protest. Google weighed in by covering its logo in black. It was a watershed moment, making a huge impression on Congress, Internet firms, and Internet-rights advocates as well. Holmes Wilson, codirector of Fight for the Future, says the organization simply “stumbled across this new tactic,” realizing that it could team up with Internet companies that would then appeal directly to their users. (In truth, there was a similar campaign in 1996.) If these companies “align themselves with the interests of individual users…you have this powerful coalition that can really stand up to any other industry and any other lobbyist,” he says. In fact, in the wake of SOPA, Fight for the Future has formed a new group, called the Internet Defense League, to do just that. “With the Internet Defense League we want to take those tactics that were so successful in defeating SOPA and try to turn those tactics into an ongoing effort and a permanent force for defending the Internet,” says Holmes. Politics – Popular – Public Patel, 2015 (Faiza, “NSA data collection program must end,” Al Jazeera, April 28, http://america.aljazeera.com/opinions/2015/4/senate-republicans-want-to-extend-nsa-datasurveillance.html) Maintaining a database of phone records upends a fundamental premise of the Constitution: The government should intrude on Americans’ private lives only if it has probable cause to suspect criminal activity. While the database doesn’t include recordings of actual conversations, it picks up reams of information about who we call and when. This can be even more revealing of our lives. Calls to the National Rifle Association and the local shooting range show that someone may be a gun owner. Calls to a suicide prevention hotline may tell the government more than it has any right to know about a person’s mental health. Political associations and personal ties are easily revealed. The rationale for the telephone database can be used to collect other types of information as well. The NSA ran an Internet metadata program until 2011 and could well revive it without the public knowing. As we conduct more and more of our lives online, this could allow the government to stockpile information about who we email, which websites we visit and the books and medicines we buy online. Even agencies not concerned with national security are warehousing information. It was recently revealed that for more than two decades starting in 1992, the Drug Enforcement Administration logged virtually all phone calls made from the United States to 116 countries. The people whose calls to family, friends and business associates were picked up weren’t suspected of any crime, and no court was asked for approval. Americans understand the risks these programs pose to their privacy. Several polls have been conducted to gauge people’s attitudes about electronic surveillance. While the results vary somewhat, the clear trend in the last two years is that the public is increasingly uneasy about digital intrusions of unprecedented scale. K Answers Generic K Answer – Civic Engagement Good Education over specific national security policy is key to prevent devolution of government into despotism Glennon, 2014 (Michael J., Professor of International Law, Fletcher School of Law and Diplomacy, Tufts University, “National Security and Double Government,” Harvard National Security Journal, 5 Harv. Nat’l Sec. J. 1) Moreover, as a practical matter, it would be difficult to overcome voter ignorance that is in important respects entirely rational. Consider more closely three of the prerequisites for intelligent participation in governance: minimal intellectual acumen, sound judgment concerning policy alternatives, and an adequate informational base. The first two elements are in many respects already widely present. The fact is that "Joe Six-Pack" is neither unintelligent nor irrational. No one familiar with the rules of American football--surely among the most complicated sports in the world--can doubt the raw intelligence of anyone able to weigh the pros and cons of the nickel defense. Its moral dimensions notwithstanding, the decision whether to run a play-action fake on third-and-two is not a conceptually more difficult question than the decision whether to strike a high-value target located in a car in Yemen with four unidentified companions. Different types of research obviously are required, but neither matter is beyond the intellectual grasp of a person of common intelligence. The moral implications are also, of course, different, but what reason is there to believe that the Trumanites have any greater moral expertise than the average voter? It is often said that the public lacks access to the requisite information. The reality, however, is that all the material needed to make an informed judgment on the wisdom of drone strikes as a general policy--as well as 95% of the other issues the Trumanites confront--is readily available to anyone who can access the internet. One reason that the public does not do so is that, given competing demands on its time, there is no obvious reason to become more informed. National security policy remains the same from one president to the next, whomever one votes for, and even in the most politically accountable of worlds, the public still would necessarily be excluded from sensitive national security deliberations. Why waste time learning about things one cannot affect? n598 A single vote, in any event, has an infinitesimally small chance of determining the outcome of an election. [*109] American voters may not have read Voltaire, but they know that there are gardens to be tended. n599 Theirs is, in key respects, rational ignorance. n600 This is the nub of the negative feedback loop in which the United States is now locked. Resuscitating the Madisonian institutions requires an informed, engaged electorate, but voters have little reason to be informed or engaged if their efforts are for naught--and as they become more uninformed and unengaged, they have all the more reason to continue on that path. The Madisonian institutions thus continue to atrophy, the power of the Trumanite network continues to grow, and the public continues to disengage. VI. Conclusion U.S. national security policy has scarcely changed from the Bush to the Obama Administration. The theory of Walter Bagehot explains why. Bagehot described the emergence in 19th-century Britain of a "disguised republic" consisting of officials who actually exercised governmental power but remained unnoticed by the public, which continued to believe that visible, formal institutions exercised legal authority. n601 Dual institutions of governance, one public and the other concealed, were referred to by Bagehot as "double government." n602 A similar process of bifurcated institutional evolution has occurred in the United States, but in reverse: a network has emerged within the federal government that exercises predominant power with respect to national security matters. It has evolved in response to structural incentives rather than invidious intent, and it consists of the several hundred executive officials who manage the military, intelligence, diplomatic, and law enforcement agencies responsible for protecting the nation's security. These officials are as little disposed to stake out new policies as they are to abandon old ones. They define security more in military and intelligence terms rather than in political or diplomatic ones. [*110] Enough examples exist to persuade the public that the network is subject to judicial, legislative, and executive constraints. This appearance is important to its operation, for the network derives legitimacy from the ostensible authority of the public, constitutional branches of the government. The appearance of accountability is, however, largely an illusion fostered by those institutions' pedigree, ritual, intelligibility, mystery, and superficial harmony with the network's ambitions. The courts, Congress, and even the presidency in reality impose little constraint. Judicial review is negligible; congressional oversight dysfunctional; and presidential control nominal. reform efforts are no more likely to succeed, relying as they must upon those same institutions to restore power to themselves by exercising the very power that they lack. External constraints--public opinion and the press--are insufficient to check it. Both are manipulable, and their vitality Past efforts to revive these institutions have thus fallen flat. Future depends heavily upon the vigor of constitutionally established institutions, which would not have withered had those external constraints had real force. Nor is it likely that any such constraints can be restored through governmental efforts to inculcate greater civic virtue, which would ultimately concentrate power even further. Institutional restoration can come only from an energized body politic. The prevailing incentive structure, however, encourages the public to become less, not more, informed and engaged. To many, inculcated in the hagiography of Madisonian checks and balances and oblivious of the reach of Trumanite power, the response to these realizations will be denial. The image of a double national security government will be shocking. It cannot be right. It sounds of conspiracy, "a state within," and other variations on that theme. "The old notion that our Government is an extrinsic agency," Bagehot wrote, "still rules our imaginations." n603 That the Trumanite network could have emerged in full public view and without invidious intent makes its presence all the more implausible. Its existence challenges all we have been taught. There is, however, little room for shock. The pillars of America's double government have long stood in plain view for all to see. We have learned about significant aspects of what Bagehot described--from some eminent thinkers. Max Weber's work on bureaucracies showed that, left [*111] unchecked, the inexorability of bureaucratization can lead to a "polar night of icy darkness" in which humanitarian values are sacrificed for abstract organizational ends. n604 Friedrich Hayek's work on political organization led him to conclude that "the greatest danger to liberty today comes from the men who are most needed and most powerful in government, namely, the efficient expert administrators exclusively concerned with what they regard as the public good." n605 Eric Fromm's work on social psychology showed how people unconsciously adopt societal norms as their own to avoid anxiety-producing choices, so as to "escape from freedom." n606 Irving Janis's work on group dynamics showed that the greater a group's esprit de corps, "the greater the danger that independent critical thinking will be replaced by groupthink, which is likely to result in irrational and dehumanizing actions directed against out-groups." n607 Michael Reisman's work on jurisprudence has shown how de facto operational codes can quietly arise behind publicly-embraced myth systems, allowing for governmental conduct that is not approved openly by the law. n608 Mills' 1956 work on power elites showed that the centralization of authority among officials who hold a common world view and operate in secrecy can produce a "military metaphysic" directed at maintaining a "permanent war economy." n609 One person familiar with Mills' work was political scientist Malcolm Moos, the presidential speechwriter who five years later wrote President Eisenhower's prophetic warning. n610 "In the councils of government," Eisenhower said, "we must guard against the acquisition of unwarranted influence, whether sought or [*112] unsought, by the military-industrial complex. The potential for the disastrous rise of misplaced power exists and will persist." n611 Bagehot anticipated these risks. Bureaucracy, he wrote, is "the most unimproving and shallow form of government," n612 and the executive that commands it "the most dangerous." n613 "If it is left to itself," he observed, "without a mixture of special and non-special minds," decisional authority "will become technical, self-absorbed, self-multiplying." n614 The net result is responsibility that is neither fixed nor ascertainable but diffused and hidden, n615 with implications that are beyond historical dispute. "The most disastrous decisions in the twentieth century," in Robert Dahl's words, "turned out to be those made by authoritarian leaders freed from democratic restraints." n616 The benefits derived by the United States from double government--enhanced technical expertise, institutional memory and experience, quick-footedness, opaqueness in confronting adversaries, policy stability, and insulation from popular political oscillation and decisional idiosyncrasy--need hardly be recounted. Those benefits, however, have not been cost-free. The price lies in wellknown risks flowing from centralized power, unaccountability, and the short-circuiting of power equilibria. Indeed, in this regard the Framers thought less in terms of risk than certainty. John Adams spoke for many: "The nation which will not adopt an equilibrium of power must adopt a despotism. There is no other alternative." n617 The trivial risk of sudden despotism, of an abrupt turn to a police state or dictatorship installed with coup-like surprise, has created a false [*113] sense of security in the United States. n618 That a strongman of the sort easily visible in history could suddenly burst forth is not a real risk. The risk, rather, is the risk of slowly tightening centralized power, growing and evolving organically beyond public view, increasingly unresponsive to Madisonian checks and balances. Madison wrote, "There are more instances of the abridgment of the freedom of the people by gradual and silent encroachments of those in power than by violent and sudden usurpations." n619 Recent history bears out his insight. Dahl has pointed out that in the 20th century--the century of democracy's great triumph--some seventy democracies collapsed and quietly gave way to authoritarian regimes. n620 That risk correlates with voter ignorance; the term Orwellian has little meaning to a people who have never known anything different, who have scant knowledge of history, civics, or public affairs, and who in any event have likely never heard of George Orwell. "If a nation expects to be ignorant and free, in a state of civilization," Thomas Jefferson wrote, "it expects what never was and never will be." n621 What form of government ultimately will emerge from the United States' experiment with double government is uncertain. The risk is considerable, however, that it will not be a democracy. Courts = Movements – Opaque Courts are key to effective movements – it maintains the opacity necessary for effective deliberation Peters, 2000 (Christopher J., Assistant Professor of Law, Wayne state University Law School, “Assessing the new judicial minimalism,” Columbia Law review, 100 Colum. L. Rev. 1454, October) Deliberation is not necessarily promoted by transparency; indeed, it is frequently hindered by it. This is a point that Sunstein himself has made quite powerfully in the past. In The Partial Constitution, Sunstein sides with Madison against Jefferson in favor of the closing of the Constitutional Convention in 1787: On Madison's view, it was best "to sit with closed doors, because opinions were so various and at first so crude that it was necessary they should be long debated before any uniform system of opinion could be formed. Meantime the minds of the members were changing, and much was to be gained by a yielding and accommodating spirit... By secret discussion no man felt himself obliged to retain his opinions any longer than he was satisfied of their propriety and truth, and was open to the force of argument." n187 Indeed, the Federalists thought that opacity was necessary for true democratic deliberation. They distrusted open public discussion and, as James Martin has written, "believed that the public interactions and debates that are a part of any democracy should take place via the representative mechanisms that operate through the legal institutions of the state." n188 The relationship between the opacity and the quality of deliberation recently surfaced in the debate over whether the Senate, sitting as a court of impeachment in the trial of President Clinton, should deliberate publicly or behind closed doors. Some, like Iowa Senator Tom Harkin, opposed deliberations in "secret session" and argued that opening the debate "would send an important message. The public has a right to know how the Senate reaches its final decision on the removal or acquittal of the President." n189 Others, like Alabama Senator Richard Shelby, held a different view: "I think we explain[] to our constituents how we're going to vote as we vote and afterwards... But I believe that the deliberations ought to be like every jury in America, they ought to be behind closed [*1497] doors where we can be candid...." n190 In the end, those advocating open-door deliberations failed to achieve the two-thirds majority necessary to waive the Senate rule requiring secret debate. n191 Madison, Senator Shelby, and Sunstein himself have recognized that the glare of the public spotlight is not conducive to the candidness and openmindedness necessary to true deliberation. This is so for the same reasons that support representative rather than direct democracy: Public opinion may be raw, "based on inadequate information and on popular passions that are insufficiently influenced by reason-giving and understanding of context." n192 Exposing important decisions, and the processes of making them, to instantaneous and continuous public scrutiny threatens to infect representative democracy with the sorts of emotional, knee-jerk tendencies it was designed to avoid. n193 This is especially so when the decisions to be made involve not simply policy issues, but questions of individual rights against the majority. Writing of the dangers of referenda in the affirmative action context, Sunstein notes the risk that "outcomes will not be based on a careful assessment of facts and values, but instead on crude 'we-they' thinking." n194 This point can be generalized across all decisions involving individual rights. Questions of individual rights are inherently "we-they" affairs: The majoritarian "we" is pitted against the individual or minority "they." True deliberation about such questions - decisionmaking characterized by reason-giving, openness to opposing arguments, consideration of various relevant perspectives, and willingness to compromise - is made difficult from the start in the political system, where the ultimate decisionmakers, the citizens, by definition have something to gain or to lose. Deliberation is made all the more difficult when representatives are constantly bombarded, through public opinion polls and the ever-more-massive media, by the self-interests they are supposed to be filtering. n195 [*1498] The increasing transparency of politics stands in stark contrast to the opaque process of adjudicative decisionmaking. Only very rarely, as in the O.J. Simpson case, does the actual process of adjudication attract significant public attention . What publicity adjudication does draw invariably goes to the trial process, not to the appellate process, where law is made. Appellate court and Supreme Court proceedings are not televised, and only the results of those proceedings tend to receive publicity (and then only when they decide high-profile issues). And of course the actual deliberations of appellate courts invariably take place behind closed doors. It is true, and important, that the tools of Supreme Court deliberation - briefs filed by the parties, and transcripts or recordings of oral arguments - and the results of that deliberation - written opinions - usually are made public, more frequently and quickly than ever these days. But these sources only confirm the extent to which adjudication is meticulously deliberative. Legal briefs, oral arguments, and court opinions, unlike arguments made in the political realm, typically eschew entreaties to "public opinion" or "the public interest," instead replacing them with arguments based on the interpretation of legal authorities. Briefs, arguments, and opinions also typically address the reasoning both for and against the results they espouse. They are not allowed to be "supported by self-interest or force" n196 or to rely on "'naked preferences.'" n197 They are models of "reason-giving in the public domain." n198 The quoted phrases in the previous paragraph are taken from Sunstein's description of "deliberative democracy" in One Case at a Time. Remarkably, though, they describe the everyday adjudicative process much more accurately than they describe the everyday political process. n199 This is because the adjudicative process is, in these important ways, far more "deliberative" than politics typically can be. Part of the reason for this is the much- maligned isolationism of the law - its insulation from worldly affairs, its persistent formalism, its self-referential reliance only on appropriately pedigreed authorities. n200 Law in our system takes place behind [*1499] closed doors, away from the public spotlight and with little regard for it. And this opacity may work to the judiciary's advantage in attracting public trust; a recent survey indicates that the public has more "respect" for the Supreme Court than for the political branches. n201 It is strange, then, that Sunstein sees judicial review primarily as a tool for increasing the deliberativeness of the political branches. Much of the point of judicial review is that it is more deliberative than the political process, and thus better constituted to produce decisions that require deliberation above all else. As I explain in the next section, the adjudicative brand of deliberation does not lend itself to many kinds of decisionmaking that the political branches are good at. But it does lend itself to decisionmaking about individual rights - when they exist, what they look like, how far they ultimately extend. Decisions about individual rights are particularly poorly made in the spotlight, where they can be distorted by the very pressures that rights are meant to stand against. They are better made by courts, which can, in the current phrase, "fly under the radar" of public scrutiny. Courts = Movements – Participation Courts are key to the movement – they allow for active participation in lawmaking Peters, 2000 (Christopher J., Assistant Professor of Law, Wayne state University Law School, “Assessing the new judicial minimalism,” Columbia Law review, 100 Colum. L. Rev. 1454, October) A fact too often overlooked is that these complementary elements - direct participation and indirect participation through representation - are present not just in decisionmaking by the "political" branches of government, but in adjudication as well. Adjudication, even constitutional adjudication, is driven primarily by the participation of the litigants, not by the court itself. n141 One of the litigants (usually acting through counsel) initiates the case, by filing a lawsuit or a criminal prosecution. Each litigant locates relevant facts and determines whether and how to present them to the court . Each litigant identifies relevant legal authorities, synthesizes the facts and authorities into legal arguments, and makes those arguments to the court. When the court - meaning the judge, or panel of judges - makes a decision on the merits, or indeed on procedural matters, that decision typically is responsive to the facts presented and arguments made by the litigants. In most courts, dispositive decisions are memorialized and defended by judges in written opinions, largely to ensure precisely this responsiveness. The role of the judge or judges in all of this remains relatively passive, even under modern rules of procedure and evidence. It consists mostly of rendering a decision that is responsive to the proofs and arguments. To the extent the judge's role extends beyond simply deciding the substantive and procedural issues presented in the case by the litigants, it usually is limited to one or more of three kinds of activities: (1) tending to scheduling and other docket-related matters; n142 (2) narrowing and clarifying the issues that will be contested at trial; n143 and (3) encouraging settlement. n144 Moreover, these activities are primarily the province of trial judges, not of appellate panels. It is thus rather narrowminded to think of adjudication as decisionmaking by judges. Adjudication is decisionmaking by judges and litigants; the boundaries of a judge's or panel's decision are set by the decisions the litigants make with respect to what facts to present, what arguments to [*1482] make, and how to present and make them. It is true, of course, that litigants often complain about judges ignoring what they consider to be important facts or rejecting what they consider to be decisive arguments. Indeed, judges often do this. But judges are subject to criticism when they do this - a point whose significance can hardly be overstated. n145 Judges do not write their opinions without regard for whether they will be perceived as adequately responsive to what the litigants have done and said. Such considerations surely are foremost in their minds. Nor do judges (for the most part) write opinions in which they make up facts, or rely upon evidence not in the record, or rely upon evidence that they themselves have elicited outside the parties' own efforts, or even, in most cases, rely upon legal arguments not urged by one of the parties. n146 Sunstein cheapens somewhat these de facto, institutionalized constraints on the judicial role when he classifies judicial reason-giving as a "norm[] associated with legal craft." n147 Reason-giving is a norm associated with legal (or, more to the point, judicial) craft the way the Hippocratic Oath is a norm associated with medical craft; it is essential to the enterprise. Judicial reason-giving demonstrates whether, and to what degree, a court's decision is responsive to the proofs and arguments presented by the litigants . And responsiveness to the proofs and arguments presented by the litigants is the sine qua non of adjudication . n148 In this sense, judicial reason-giving is even more vital than reason-giving in the political branches, a norm that Sunstein ranks highly . n149 Inadequately responsive legislators can be removed from office through the electoral process; inadequately responsive federal judges cannot be. Norms associated with legal craft are all there is to constrain them. [*1483] Adjudication, then, is a form of government decisionmaking in which those bound by the decision have the opportunity to participate meaningfully - in which the affected parties "are bound by something they helped to make." n150 This should sound familiar, because in this sense adjudication incorporates the democratic ideal of self-government. Litigants bound by a court decision have participated in that decision no less integrally - indeed, more integrally - than have most citizens bound by congressional legislation or administrative rulemaking. The synthesizing presence of a judge in adjudication is no more threatening to the fundamentally participatory nature of the process than is the synthesizing presence of representatives to the process of political legislation. Nor is the judge's presence any more threatening to participation than is the presence of majorities in the legislative chamber or the electorate, who must be convinced to vote a certain way in order for the participation of a particular citizen to be effectual.