Additional_Review_Notes_VincentBlijleven
advertisement

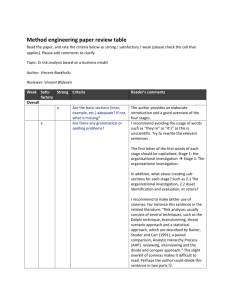
Additional Review Notes Topic: IS risk analysis based on a business model Author: Vincent Boekholtz Reviewer: Vincent Blijleven Introduction - - - - They are both quite well published authors. Are the authors published? I would rewrite this to something akin to: “Both authors have made (significant) contributions to their respective fields of science.” Or: “Both authors are widely cited in their respective domains.” Perhaps it is a good idea to explicitly mention the domain in which this method can be applied. It may seem obvious, but to avoid problems. Inconsistent use of paragraph-structure throughout the paper. Here a white line is used: “published authors. –white space- The Information System (IS) … Make use of indents. This applies to the rest of the document as well. methods which were methods that were so important that, when it malfunctions, it has the potential to cause a so important that when malfunctioning, it could potentially cause a … Because of this the risk analysis Because of this, the risk analysis (still not a nice way to write it, but commas contribute to readability) business model, which can business model that can They introduced The authors introduced (Suh and Han, 2003) (Suh & Han, 2003) Suh and Hand (2003) Hand? through 5 steps through five steps. (Usually, 1-20 is written in letters, and numbers after 20 written in numbers (e.g. one, seventeen, twenty versus 21, 22, 23). When they are assigned When the assets are assigned because it’s of no influence on the purpose of this method (it’s developed I recommend avoiding the usage of words such as “they’re” or “it’s” as this is unscientific. Try to rewrite the relevant sentences. The rest of the needed figures The rest of the required figures Example - Perhaps you could mention the role identified in this method, to know the risk analyst. This was also explicitly asked for in the assignment. Again, to avoid problems . Very good example that contains the most essential elements of the method described. Well done. The first letter of the first words of each stage should be capitalized. Stage 1: the organizational investigation Stage 1: The organizational investigation. What about creating sub-sections for each stage? Such as 2.1 The organizational investigation, 2.2 Asset identification and evaluation, et cetera? According to Stolovitch and Robertson (1998) an effective way to do this, is According to Stolovitch and Robertson (1998), an effective way to address this is to … Literature Review - - - the method they developed the method the authors developed Risk analyses usually consists of several techniques, such as the Delphi technique, brainstorming, threat scenario approach and a statistical approach, which are described by Rainer, Snyder and Carr (1991), a paired comparison, Analytic Hierarchy Process (AHP), reviewing, interviewing and the divide and conquer approach. Split this sentence up in different parts, this is not really fancy to read. They use several of these The authors employ several of the aforementioned techniques … They also agree with The authors also agree with Also “When Stakeholder Perceive Threats and Risks Differently” by Rutkowski, Van de Walle, Van Groenendaal and Pol (2005) use “The IS risk analysis based on a business model” by Suh and Han (2003), not as a comparison, but to adopt their statement that the IS/IT continuity in relation to its processes is of essential importance for the survival of the company. Split this sentence up in two parts. All in all they do support and recommend Suh and Hans (2003) method though. unscientific Process-Deliverable Diagram and Activity & Concept Table - - - Process Deliverable Diagram Process-Deliverable Diagram Make references to the figures and tables in the text. doesn’t mention does not mention which actor carries the activity out, which actor performs/conducts the activity, I recommend not merging the flows between THREAT, ASSET and ANNUAL LOSS EXPECTANCY. The reason for this is as I am not sure whether the cardinalities (1..*, 0..* & 1..*) are always applicable, regardless of whether you e.g. look at ANNUAL LOSS EXPECTANCY from a THREAT or ASSET perspective. I have one question regarding the role, to know the ‘risk analyst’. Considering this is the only role present in this method, perhaps this role could be removed and solely mentioned in the beginning of the third section (PDD), which is what the author has already done. In other words: why include information in the PDD if it doesn’t really make a contribution . I strongly recommend to use either shades of gray or plain white as colours for the table. The blue colour does not really contribute to readability. References - (Suh and Han, 2003) (Suh & Han, 2003) The rest looks really good. The minimal amount of references (10) is given, but suffices for the method described. I am not sure how much related literature is available on this topic as I am not familiar within this domain. Good luck with the final version of your work! (Sorry for several duplicates in this document and the other one).