Networks & Their Security
advertisement

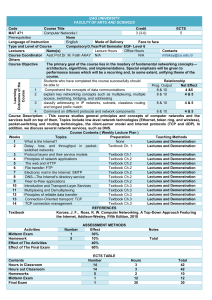
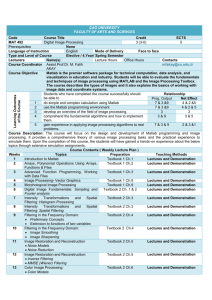
ÇAĞ UNIVERSITY FACULTY OF ARTS AND SCIENCES Learning Outcomes of the Course Code Course Title Credit ECTS MAT 421 Networks & Their Security 3 (3-0) 5 Prerequisites None Language of Instruction Mode of Delivery Face to face English Type and Level of Course Compulsory/ 4.Year/ Fall Semester Lecturers Name(s) Contacts Lecture Hours Office Hours Course Coordinator Assoc.Prof.Dr. M. Fatih mfakay@cu.edu.tr Thu. 9-12 N/A AKAY Others Course Objective This course provides an essential study of computer security issues and methods in networking systems. The aim of the course is to introduce the student to the fundamentals of cryptography and network security. Relationship Students who have completed the course successfully should be able to Net Effect Prog. Output 4&5 1 command on the concepts of data communications 8 &10 5&5 2 explain concepts related to applied cryptography, including 3 & 10 plaintext, ciphertext, symmetric cryptography, asymmetric cryptography, and digital signatures. 5&5 3 outline the requirements and mechanisms for identification and 3 & 10 authentication. 5&5 4 explain the requirements of non-real time security (email 3 & 10 security) and ways to provide privacy, source authentication, message integrity, non-repudiation, proof of submission, proof of delivery, message flow confidentiality, and anonymity. Course Description: This course involves an intense examination of network security defense techniques and countermeasures with defense fundamentals explained in great detail. Topics include Introduction to the Internet, Principles of Cryptography, Message Integrity and End-Point Authentication, Securing E-mail, TCP Connections and Wireless LANs. Course Contents:( Weekly Lecture Plan ) Weeks Topics Preparation Teaching Methods 1 Lectures and Demonstration What Is the Internet? Textbook Ch.1 2 Lectures and Demonstration Delay, Loss, and Throughput in PacketTextbook Ch.1 Switched Networks 3 Lectures and Demonstration Protocol Layers and Their Service Models Textbook Ch.1 4 Lectures and Demonstration Networks Under Attack Textbook Ch.1 5 Lectures and Demonstration History of Computer Networking and the Textbook Ch.1 Internet 6 Lectures and Demonstration What Is Network Security? Textbook Ch.8 7 Lectures and Demonstration Principles of Cryptography Textbook Ch.8 8 Lectures and Demonstration Symmetric Key Cryptography Textbook Ch.8 9 Lectures and Demonstration Public Key Encryption Textbook Ch.8 10 Lectures and Demonstration Message Integrity and End-Point Textbook Ch.8 Authentication 11 Lectures and Demonstration Securing E-mail and TCP Connections: SSL Textbook Ch.8 12 Lectures and Demonstration Network-Layer Security: IPsec and Virtual Textbook Ch.8 Private Networks 13 Lectures and Demonstration Securing Wireless LANs Textbook Ch.8 14 Lectures and Demonstration Operational Security: Firewalls and Intrusion Textbook Ch.8 Detection Systems REFERENCES Textbook Kurose, J.F., Ross, K.W., Computer Networking, A Top-Down Approach Featuring the Internet, Addison-Wesley, Fifth Edition, 2010 Activities Midterm Exam Homework Effect of The Activities Effect of The Final Exam Number 1 10 ASSESSMENT METHODS Effect 30% 10% 40% 60% ECTS TABLE Notes Total Contents Hours in Classroom (Face-to-face) Hours out Classroom Homeworks Midterm Exam Final Exam Number 14 14 10 1 1 Hours 3 3 2 20 25 Total Total / 30 ECTS Credit RECENT PERFORMANCE 2012-2013 FALL SEMESTER MAT421 NETWORKS AND THEIR SECURITY 5 4 3 2 1 0 -1 4 2 1 0 0 0 0 0 1 0 NA FF FD DD DC CC CB BB BA AA Total 42 42 20 20 25 149 =149/30= 4.96 5