Ethics Report
advertisement

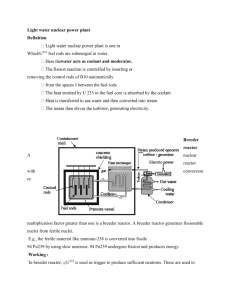
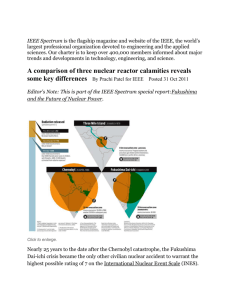
Assignmnt#5 – Ethics Report & Presentation (5%) GROUP 15 This assignment is designed to enhance your understanding the ethical issue involved in the practice of Engineering. For the case assigned to you, critically examine the case from the following points of view: 1. What are the circumstances of this disaster? 2. What key ethical principles were involved? 3. How could this disaster have been avoided? 4. What actions could you have taken if you were part of the project in question? 5. What are the ethical issues that may be involved in your own project? 6. What steps would you take to make sure there will be no disasters involving your project? Circumstances of the Disaster There are several differing reports on the actual events surrounding Chernobyl; however they all agree that there are several main factors that contributed to the explosion. The first being the overall design of the reactor. Chernobyl was an RMBK reactor, meaning that it had a positive void coefficient. These types of reactors are prone to excessive steam generation at lower power levels, which can lead to spikes in heat. Since the explosion occurred during a test of the lower power capabilities of the reactor, this was quickly identified as the main mechanism of the explosion. Of course, this explosion never would have occurred had the reactor been operating normally. The test that was being run was inherently dangerous, as it was designed to see if the reactor could sustain its own cooling systems in the event of a power failure. There was a delay between the time the system lost power and the time when the backup generators could provide enough power to maintain the cooling systems. Effectively the engineers were placing the reactor into a risky state, where the certainty of the cooling systems was unknown. This leads to another point of failure in the accident. Many of the reports indicate that the staff who was supposed to be in charge of the test had left for the day, yet the test was still run. This left the testing procedure to be watched over by the night shift, who demonstrated a lack of knowledge regarding the characteristics of the reactor, namely its positive void coefficient. In the end, all of these factors led to two massive explosions, scattering the radioactive fuel from the reactor across the surrounding countryside. Much of this radioactive material was also carried by the wind across Europe, where it was detected by other reactors, causing temporary panic from operators that their personal reactors were leaking. Key Ethical Principles Involved With the incident and Chernobyl the big ethical violation from the National Society of Professional Engineers(NSPE) Code of Ethics for Engineers that was broken, was the first principle from the first ethic under the Fundamental Canons section: Hold paramount the safety, health, and welfare of the public. Not only did the control rods have an inadequate design, but the reactor had a positive void coefficient characteristic (it can become unstable at low power and may experience a rapid, uncontrolled power increase) , and a violation of operating regulations as well as the station staff not having knowledge of the reactor, this when compiled with its non-routine operation that helped cause the accident led to one of the most well known if not greatest engineering disasters in the world. How chernobly could been avoided Chernobyl was not a nuclear disaster. It was not triggered by natural disaster. The rest why Chernobyl occurred was because of poor training, lack of safety measures, lack of planning. If the personal was well trained this wouldn’t of happened. The personal chose not to continue with the test that was being conducted. If they were trained well they would of continued to test and realize something was wrong. If the government was not pressuring the company to get more results it would of helped for this not to cut corners. If the company also planned better, the government would not pressure them as much on the deadline as well. Lastly it could have been prevent if it was designed better. It was not design the best way which caused the disasters. Considerations to Avoid Ethical Liability in the Chernobyl Disaster Given the time elapsed since the incident, the relatively primitive technology involved in the plant's design, and the difficulty in understanding exactly what transpired due to the overwhelmingly secretive policies under Soviet administration, it is difficult to point fingers and say exactly where decisions could have been made differently to ideally eliminate ethical problems surrounding the Chernobyl meltdown and surrounding response. Primary avenues of improvement are found in communication, response planning, and overall more knowledge provided about principles involved in the reactor's operation under all (not just nominal) conditions. During the reactor tests that led up to the explosions that blew open a reactor core, some of the results were anomalous and rather than abort the test or fundamentally alter the procedures according to known information, the decision was made to press on with the testing (until, at the last minute, a shutdown from extreme reactor temperatures was initiated and triggered the events of the explosion). Had all involved personnel dutifully reported meticulous information about their instrument readings, it is possible that conclusions could have been drawn as to what was happening in the reactor and what might be done to prevent catastrophe. Whether or not this could have been done, the administration at the plant was not fully educated on the reactor operation to the point where the events of the incident were adequately understood, and it took a thorough investigation after-the-fact to uncover what exactly had transpired. Initial responders to the explosion were normal firefighting crews, and many of them were exposed to extremely dangerous, and even lethal, levels of radiation while struggling to put out chemical fires that they were not equipped to extinguish. More preparedness by the fire teams around the plant - prompted by education from plant officials - could have improved the efficient utilization of these resources in the event of a disaster such as the one that transpired. In general, the plant's designer should have, to be thorough in planning, envisioned all possible abnormal operation conditions of the reactor and designed appropriate procedures for recovery. With the right procedures and training, the reactor crew could easily have stopped things from getting out of control long before the reactor itself exploded. Modern engineering techniques give us the benefit of this clarity in hindsight, just as modern communication systems provide crews with far greater resources to respond to crises in a timely manner, but careful thinking and planning can always go a long way beyond established practices in order to save lives (a lesson not easily learned, and often ignored in favor of political or economic concerns). Ethical Issues in Chernobyl Privacy: Description: Our project goal is aimed at convince and as such we will try to use the methods that best suit the needs of our users. Bluetooth sniffing will allow us to track the Bluetooth ID of the phone without having the students needing to turn the phone on. This is to provide optimal ease of use and helps increase our accuracy, another ethical value we must consider. In addition, due to the amount of hacking and data violation via Bluetooth from other devices, users have developed a distrust of such devices and may attempt to completely turn off the device in order to prevent such hack attempts. However this would invenrtly prevent our device from finding the phone, not regressing for the class. If concerns about the data privacy escalate, features that can turn on passive sniffing could be turned off in the configuration. When the instructor goes though the initial setup of the Smart ID attendance, he will be presented with the option to enable or disable. This could come to include a warranty or a Disclaimer of Use. Accuracy: Our device is claiming superior accuracy and speed at taking attendance. Because of this claim, we must ensure that he professor can depend on the accuracy of our device. These devices could be related to grades or attendance at work and could be held as testimony against another person based off attendance. Our device’s routines and functions must be able to prove the accuracy of the student’s attendance. To ensure that our device is accurate we will provide a confirmation light at each scan to show that the student has been registered for the class. Also, an option in the GUI could allow all missing students to appear in a list for validation. This can provide the Instructor with an extra measure of accuracy in making sure that the information on the screen is accurate. Accuracy is a difficult issue to deal with on some levels because it directly conflicts with our other device goal speed. By taking extra measures to make sure that the accuracy of our devices attendance process is correct, we also increase the amount of time needed to take attendance. However, the benefit of our device is that attendance is not a time critical calculation and can be thoroughly run through after the attendance collecting process. Security: Inside of the SD card will be a log of the Students names associated with the Bluetooth ID of the device they register. If we are going to ask for this information, we must be able to assure to the user that their information is safe and will not be accessible to anyone other then the professor. Because our device is not connected to the Internet or any other type of network, an outside hacking attempt is not possible. Our SD card will be encrypted and won’t allow just any user to take and use. We will encase our device and minimize the need for direction interaction to minimize tampering. Security from the device to the computer will be left for the end user to manage. What steps would you take to make sure our project would not have disasters? In any modern digital communications there are a multitude of vulnerabilities that can be used by hackers to compromise the integrity of you system and users’ information. One advantage that our system has is that all of its processing and storage is done offline on an isolated closed loop system. This prevents our system from being compromised by outside users from remote locations. As with any system there is always going to vulnerabilities that open up a system to compromise and being that our system is completely offline the biggest threat is our data. For this reason our system will be encrypting all user data and only the professor of the class will have access to the system locally. Sources: "Chernobyl." ENGINEERING.com. N.p., n.d. Web. 26 Mar. 2014. <http://www.engineering.com/Library/ArticlesPage/tabid/85/ArticleID/71 /categoryId/7/Chernobyl.aspx>. "The Chernobyl Accident." Public Health England. N.p., n.d. Web. 26 Mar. 2014. <http://www.hpa.org.uk/Topics/Radiation/UnderstandingRadiation/Under standingRadiationTopics/RadiationIncidents/Chernobyl/>. "Decommissioning of Chernobyl Units Approaches." Chernobyl. N.p., n.d. Web. 26 Mar. 2014. < http://www.world-nuclear.org/info/safety-andsecurity/safety-of-plants/chernobyl-accident/>