Full Description - Faculty of Information Technology Multimedia
advertisement
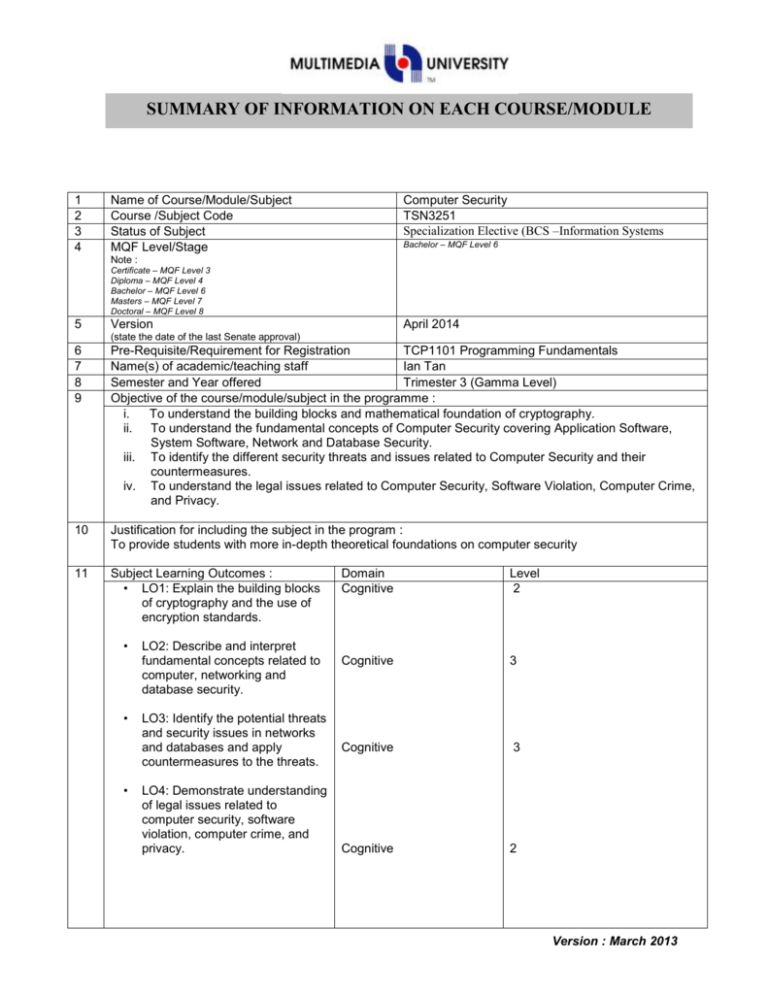
SUMMARY OF INFORMATION ON EACH COURSE/MODULE 1 2 3 4 Name of Course/Module/Subject Course /Subject Code Status of Subject MQF Level/Stage Computer Security TSN3251 Specialization Elective (BCS –Information Systems Bachelor – MQF Level 6 Note : Certificate – MQF Level 3 Diploma – MQF Level 4 Bachelor – MQF Level 6 Masters – MQF Level 7 Doctoral – MQF Level 8 5 Version April 2014 (state the date of the last Senate approval) 6 7 8 9 Pre-Requisite/Requirement for Registration TCP1101 Programming Fundamentals Name(s) of academic/teaching staff Ian Tan Semester and Year offered Trimester 3 (Gamma Level) Objective of the course/module/subject in the programme : i. To understand the building blocks and mathematical foundation of cryptography. ii. To understand the fundamental concepts of Computer Security covering Application Software, System Software, Network and Database Security. iii. To identify the different security threats and issues related to Computer Security and their countermeasures. iv. To understand the legal issues related to Computer Security, Software Violation, Computer Crime, and Privacy. 10 Justification for including the subject in the program : To provide students with more in-depth theoretical foundations on computer security 11 Subject Learning Outcomes : • LO1: Explain the building blocks of cryptography and the use of encryption standards. • • • LO2: Describe and interpret fundamental concepts related to computer, networking and database security. LO3: Identify the potential threats and security issues in networks and databases and apply countermeasures to the threats. LO4: Demonstrate understanding of legal issues related to computer security, software violation, computer crime, and privacy. Domain Cognitive Level 2 Cognitive 3 Cognitive 3 Cognitive 2 Version : March 2013 12 13 14 Mapping of Learning Outcomes to Programme Outcomes : Learning Outcomes PO1 PO2 PO3 PO4 PO5 LO1 LO2 LO3 LO4 Assessment Methods and Types : Method and Type Description/Details Quizzes In class or in lab. Assignment Group assignment Test Written Final Exam Written Details of Subject Topics PO6 PO7 X X PO8 PO9 X X X Percentage 15% 15% 20% 50% Mode of Delivery (eg : Lecture, Tutorial, Workshop, Seminar, etc.) Indicate allocation of SLT (lecture, tutorial, lab) for each subtopic 1. Overview • • • • • • 4 4 0 2 0 2 6 0 2 Classical to modern ciphers (product ciphers). DES as a case study of modern ciphers and attacks on DES. Evolution of modern ciphers, Triple DES and AES. 4. Asymmetric Cryptography • Tutorial 0 Terminology and background, stream and block ciphers. Monoalphabetic substitution and cryptanalysis methods. Polyalphabetic substitution and cryptanalysis methods. Transposition ciphers and cryptanalysis methods. 3. Symmetric Cryptography • • Lab 4 Introduction to computer security. Concept of confidentiality, integrity and availability. Discussion on vulnerabilities, threats, controls. 2. Elementary Cryptography • Lecture 2 Mathematical foundation in finite field arithmetic, prime numbers and primality tests. Introduction to Public-Key cryptography and usage. RSA as a case study of asymmetric ciphers, timing attacks on RSA and countermeasures against timing attacks. Version : March 2013 5. Program Security • • • • • 15 16 17 2 3 4 0 3 4 0 2 0 0 2 0 2 Security planning, risk analysis & economies of security, security policies & physical security. 10. Legal and Ethical Considerations • 0 Issues: reconnaissance, threats in transit, impersonation, message confidentiality threats, message integrity threats, denial of service. Controls: encryption, firewalls, intrusion setection systems. 9. Security Administration • 2 Memory protection and file access protection. Authentication: passwords, biometrics and multi-modal authentication. 8. Network Security • 0 Introduction to databases security requirements. Inference attacks and countermeasures to inference attacks. 7. Operating System Security • • 4 Securing programs, non-malicious software errors, malicious software (virus, Trojans, etc.) and controls against program threats. 6. Database Security • • 2 Intellectual property: copyrights, patents, trademarks, trade secrets, industrial design. Case study: filing copyrights @ MyIPO. Information and Law. Ethical issues. Total Student Learning Time (SLT) Lecture Tutorials Laboratory/Practical Quiz Assignment Mid Term Test Final Exam Sub Total Total SLT Credit Value Reading Materials : Face to Face Independent Learning 28 8 20 28 8 20 1 2 59 3 12 8 22 101 160/40=4 4 Version : March 2013 Textbook William Stallings and Lawrie Brown, Computer Security: Principles and Practice, Prentice Hall; 2nd edition (November 19, 2011), ISBN-10: 0132775069. Reference Materials Charles P. Pfleeger and Shari Lawrence Pfleeger. Security in Computing, Prentice Hall; 4th edition (October 23, 2006), ISBN-10: 0132390779. William Stallings, Cryptography and Network Security: Principles and Practice, Prentice Hall; 6th edition (March 16, 2013), ISBN-10: 0133354695. Version : March 2013 18 Appendix (to be compiled when submitting the complete syllabus for the programme) : 1. Mission and Vision of the University and Faculty 2. Programme Objectives or Programme Educational Objectives 3. Programme Outcomes (POs) 4. Mapping of POs to the 8 MQF domain 5. Mapping of LOs to the POs 6. Summary of the Bloom’s Taxonomy’s Domain Coverage in all the LOs in the format below : Subject Learning Outcomes Bloom’s Taxonomy Domain (please state the Affective Cognitive Psychomotor learning outcomes) TSN3251 LO1: Explain the building blocks of symmetric cryptography and demonstrate their understanding using encryption standards. LO2: Describe and interpret fundamental concepts related to computer, networking and database security. LO3: Identify the potential threats and security issues in networks and databases and apply countermeasures to the threats. LO4: Demonstrate understanding of legal issues related to computer security, software violation, computer crime, and privacy. 7. Summary of LO to PO measurement 8. Measurement and Tabulation of result for LO achievement 9. Measurement Tabulation of result for PO achievement Mapping Assessment to Learning Outcomes No. Assessment % A1 Lab 10 A2 Assignment 40 A3 Lab Test 30 A4 Term Test 20 LO1 X LO2 LO3 X X X X X X LO4 X X Version : March 2013 Version : March 2013