Apache 2.0 Hardening Guide
advertisement
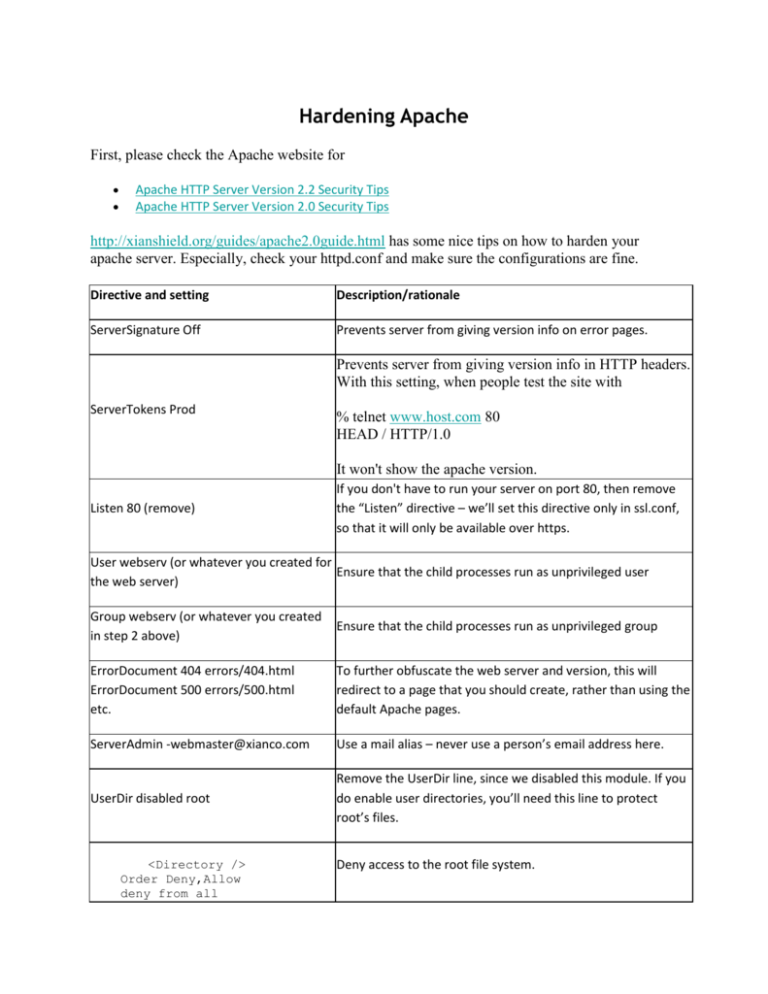
Hardening Apache First, please check the Apache website for Apache HTTP Server Version 2.2 Security Tips Apache HTTP Server Version 2.0 Security Tips http://xianshield.org/guides/apache2.0guide.html has some nice tips on how to harden your apache server. Especially, check your httpd.conf and make sure the configurations are fine. Directive and setting Description/rationale ServerSignature Off Prevents server from giving version info on error pages. Prevents server from giving version info in HTTP headers. With this setting, when people test the site with ServerTokens Prod % telnet www.host.com 80 HEAD / HTTP/1.0 It won't show the apache version. Listen 80 (remove) If you don't have to run your server on port 80, then remove the “Listen” directive – we’ll set this directive only in ssl.conf, so that it will only be available over https. User webserv (or whatever you created for Ensure that the child processes run as unprivileged user the web server) Group webserv (or whatever you created in step 2 above) Ensure that the child processes run as unprivileged group ErrorDocument 404 errors/404.html ErrorDocument 500 errors/500.html etc. To further obfuscate the web server and version, this will redirect to a page that you should create, rather than using the default Apache pages. ServerAdmin -webmaster@xianco.com Use a mail alias – never use a person’s email address here. UserDir disabled root Remove the UserDir line, since we disabled this module. If you do enable user directories, you’ll need this line to protect root’s files. <Directory /> Order Deny,Allow deny from all Deny access to the root file system. TraceEnable off Trace option appears to allow XSS or credential theft. See Cross Site Tracing for details. LimitExcept prevents TRACE from allowing attackers to find a path through cache or proxy servers. <Directory /opt/apache2/htdocs"> <LimitExcept GET POST> deny from all </LimitExcept> The “-“ before any directive disables that option. FollowSymLinks allows a user to navigate outside the doc tree, and Indexes will reveal the contents of any directory in your doc tree. Options -FollowSymLinks Includes -Indexes -MultiViews AllowOverride None Order allow,deny Allow from all </Directory> Includes allows .shtml pages, which use server-side includes (potentially allowing access to the host). If you really need SSI, use IncludesNoExec instead. AddIcon (remove) IndexOptions (remove) AddDescription (remove) ReadmeName (remove) HeaderName (remove) IndexIgnore (remove) Remove all references to these directives, since we disabled the fancy indexing module. Alias /manual (remove) Don’t provide any accessible references to the Apache manual, it gives attackers too much info about your server. AllowOverride None will prevent developers from overriding these specifications in other parts of the doc tree. This article, Secure Installation of Apache Web Server in Linux Exposed, is kinda old, but it still has a lot of values. If you run Apache inside chroot, Using Chroot (in Linux Exposed) is a good read. To check the status of the files and directories in a chroot directory, do the following: # find world writable dir/file root# find /chroot_dir -perm -2 -ls # find suid files root# find /chroot_dir -type f -perm -04000 -ls # find guid files root# find /chroot_dir -type f -perm -02000 -ls Strong Encryption The options below will create an HTTPS server supporting only the SSL v3 and TLSv1 protocols, and only allowing strong cipher suites to be accepted by the web server: SSLProtocol -all +SSLv3 +TLSv1 SSLCipherSuite HIGH Reference: SSL/TLS Strong Encryption: How-To SSL/TLS Strong Encryption: FAQ Apache Chrooted Semantec has a series of articles on this topic: Securing Apache 1.3, Step-by-step Securing Apache 2, Step-by-step Securing PHP, step-by-step Apache with SSL/TLS, step-by-step, Part I Apache with SSL/TLS, step-by-step, Part II Apache with SSL/TLS, step-by-step, Part III 0diggsdigg
![[#MODULES-2756] apache::mod::deflate exec mkdir error](http://s3.studylib.net/store/data/007740364_2-82c5aa7294b9b87bcd9af8c86f942c1c-300x300.png)