sender bits
advertisement

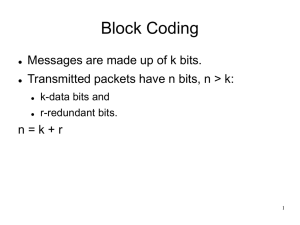
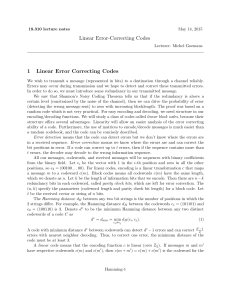
UNIT-4 1. a. Briefly explain coaxial cable and optical fiber with their applications Ans: [Dec 14] Coaxial Cable Coaxial cable (or coax) carries signals of higher frequency ranges than those in twistedpair cable, in part because the two media are constructed quite differently. Instead of having two wires, coax has a central core conductor of solid or stranded wire (usually copper) enclosed in an insulating sheath, which is, in turn, encased in an outer conductor of metal foil, braid, or a combination of the two. The outer metallic wrapping serves both as a shield against noise and as the second conductor, which completes the circuit. This outer conductor is also enclosed in an insulating sheath, and the whole cable is protected by a plastic cover APPLICATIONS Co-axial cable was widely used in analog telephone networks where a single coaxial network could carry 10,000 voice signals • digital transmission were Ethernet LANs Optical fiber A fiber-optic cable is made of glass or plastic and transmits signals in the form of light. To understand optical fiber, we first need to explore several aspects of the nature of light Propagation Modes Current technology supports two modes (multimode and single mode) for propagating light along optical channels, each requiring fiber with different physical characteristics Application • • TV companies uses combination of applications of optical fibers and co-axial cables b Find the bandwidth for a signal transmitting at 12 Mbps for QPSK. The value of d Solution For QPSK, 2 bits is carried by one signal element. This means that r =2. So the signal rate (baud rate) is S =N x (lIr) =6 Mbaud. With a value of d =0, we have B =S =6 MHz. b. What is hamming distance? Explain. [June 15/Dec 14] Ans: Hamming Distance One of the central concepts in coding for error control is the idea of the Hamming distance.The Hamming distance between two words (of the same size) is the number of differences between the corresponding bits. We show the Hamming distance between two words x and y as d(x, y). The Hamming distance can easily be found if wc apply the XOR operation (ffi) on the two words and count the number of Is in theresult. Note that the Hamming distance is a value greater than zero. code in Table 10.3 is also a parity-check code with k =4 and n =5. c. What is CRC? If the generating polynomial for CRC code is X+X+1 and message word is 11110000, determine check bits and coded word. [Dec 14/Dec 15] Cyclic codes are special linear block codes with one extra property. In a cyclic code, if a codeword is cyclically shifted (rotated), the result is another codeword. For example, if 1011000 is a codeword and we cyclically left-shift, then 0110001 is also a codeword. In this case, if we call the bits in the first word ao to a6' and the bits in the second word boto b6, we can shift the bits by using the following: 2. a. find the codeword C(x) for the information D(x) = x3 +1 with a generator polynomial T (x) = X3 +x +1 14] [Dec Ans. Now that we have discussed operations on polynomials, we show the creation of a codeword from a dataword. Figure 10.22 is the polynomial version of Figure 10.15. We can see that the process is shorter. The dataword 1001 is represented as x3 + 1. The divisor 1011 is represented as x3 + x + 1. To find the augmented dataword, we have left-shifted the dataword 3 bits (multiplying by x\ The result is x6 + x3 . Division is straightforward. We divide the first term of the dividend, x6, by the first term of the divisor, x3. The first term of the quotient is then x6/x3, or x3. Then we multiply x3 by the divisor and subtract (according to our previous definition of subtraction) the result from the dividend. The result is x4, with a degree greater than the divisor's degree; we continue to divide until the degree of the remainder is less than the degree of the divisor. It can be seen that the polynomial representation can easily simplify the operation of division in this case, because the two steps involving all-Os divisors are not needed here. (Of course, one could argue that the all-Os divisor step can also be eliminated in binary division.) In a polynomial representation, the divisor is normally referred to as the generator polynomial t(x). b. What is internet checksum? With an example list the steps undertaken by the sender & the receiver for error detection. 14] [Dec Ans. Internet Checksum Traditionally, the Internet has been using a 16-bit checksum. The sender calculates the checksum by following these steps. Sender site: 1. The message is divided into 16-bit words. 2. The value of the checksum word is set to O. 3. All words including the checksum are added ushtg one's complement addition. 4. The sum is complemented and becomes the checksum. 5. The checksum is sent with the data. Receiver site: 1. The message (including checksum) is divided into 16-bit words. 2. All words are added using one's complement addition. 3. The sum is complemented and becomes the new checksum. 4. If the value of checksum is 0, the message is accepted; otherwise, it is rejected. The nature of the checksum (treating words as numbers and adding and complementing them) is well-suited for software implementation. Short programs can be written to calculate the checksum at the receiver site or to check the validity of the message at the receiver site 3. a. Explain error detecting and error correcting in block coding. [June 14] Ans: Error detection Frame or codeword length n = m (data) + r (redundant or check bits). Any data section (length m) is valid (we allow any 0,1 bitstring). Not every codeword (length n) is valid. Make it so that: (no. of valid codewords) is a very small subset of (all possible 0,1 bitstrings of length n) so very unlikely that even large no. of errors will transform it into a valid codeword. Price to pay: Lots of extra check bits (high r). Obviously this works up to some error rate - won't work if no. of errors is large enough (e.g. = n). Error-check says "I will work if less than p errors in this block" Error correction If two codewords are Hamming distance d apart, it will take d one-bit errors to convert one into the other. To detect (but not correct) up to d errors per length n, you need a coding scheme where codewords are at least (d+1) apart in Hamming distance. Then d errors can't change into another legal code, so we know there's been an error. To correct d errors, need codewords (2d+1) apart. Then even with d errors, bitstring will be d away from original and (d+1) away from nearest legal code. Still closest to original. Original can be reconstructed. 3. b. Define Types of Errors in data communication. [June 14/June 15] Ans: Types of Errors: 1.Single-Bit Error: The term single-bit error means that only 1 bit of a given data unit (such as a byte, character, or packet) is changed from 1 to 0 or from 0 to 1.Single-bit errors are the least likely type of error in serial data transmission. 2. Burst Error: The term burst error means that 2 or more bits in the data unit have changed from 1 to 0 or from 0 to 1.The length of the burst is measured from the first corrupted bit to the last corrupted bit. Some bits in between may not have been corrupted. 4. Explain the structure of encoder and decoder of hamming code. [June 15]