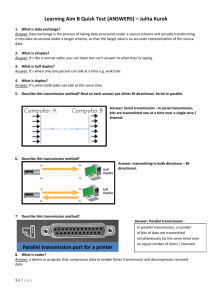
DOC Version - University of South Australia
advertisement

Evaluation of users’ perspective on VoIP’s security vulnerabilities A thesis submitted in partial fulfillment of the requirements for the degree of Master of Science (Computer and Information Science) By Alireza Heravi Supervisors: Professor Jill Slay Dr Sameera Mubarak July 2011 School of Computer and Information Science Mawson Lakes Campus University of South Australia Abstract Voice over Internet protocol (VoIP) is a relatively new technology, representing a major new trend in telecommunications and an alternative to traditional phone systems. The lower cost and greater flexibility of VoIP are the key drivers that are making it widely acceptable. VoIP refers to the transmission of voice conversations over IP-based networks. On the sending side, a VoIP system converts voice, which is an analog signal, into a digital signal, splits it into packets and transports it over IP networks. Conversely, on the receiving side, the digitized voice data is reassembled and decoded. VoIP, like other technologies, introduces both opportunities and security risks. VoIP uses IP networks and therefore inherits their vulnerabilities. Adding voice traffic to IP networks complicates security issues and introduces a range of vulnerabilities. A VoIP system may face either an exclusive attack or an attack to the underlying IP network. To retain a secure VoIP system, both IP network and the VoIP-specific security issues must be addressed. It cannot be assumed that VoIP systems will remain secure if they are plugged into a secure IP network. For this reason VoIP systems require additional security controls. The significance of security and privacy in VoIP communications are well known, and many studies mostly from the technical perspective have been published. However to date, no known research has been conducted to evaluate users’ perspectives on these issues. In light of this scarcity, this thesis aims to evaluate users’ awareness of VoIP security vulnerabilities, and their attitudes towards privacy in VoIP communications. I Declaration I declare that this thesis does not, to the best of my knowledge and belief, incorporate without acknowledgment any material previously submitted for a degree or diploma in any university, or contain any materials previously published or written by another person except where due reference is made in the text. Alireza Heravi 12 June 2011 II Acknowledgments During working on this thesis, I was being assisted and supported either directly or indirectly. Either way, each and every one’s contribution has been of immense help. I thank them dearly for their time and effort. In particular, I wish to express my gratitude to Professor Jill Slay and Dr Sameera Mubarak, my thesis supervisors, for their persistence and support. I truly appreciate their input, help and support. I also must thank my mother and my sister in law, Dr Siavoush Kahkeshan, for their support and my dearest friend, behdad, for encouraging me. III Table of Contents Chapter 1- Introduction ......................................................................................................... 1 1-1 Overview..................................................................................................................................2 1-2 Background ..............................................................................................................................2 1-3 Purpose of this study ................................................................................................................3 1-4 Aims of this thesis ....................................................................................................................3 1-5 Research question ....................................................................................................................4 1-6 Significance of this study...........................................................................................................4 1-7 Summary of thesis chapters ......................................................................................................5 Chapter 2- Literature Review ................................................................................................. 6 2-1 Overview..................................................................................................................................7 2-2 Groundwork of VoIP .................................................................................................................7 2-2-1 Telephony system ........................................................................................................................ 7 2-2-2 The Internet ................................................................................................................................. 8 2-3 VoIP Architecture .....................................................................................................................9 2-3-1 PSTN versus VoIP ......................................................................................................................... 9 2-3-2 VoIP implementation ................................................................................................................. 10 2-3-2-1 PC-to-PC.............................................................................................................................. 10 2-3-2-2 PC-to-Phone/ Phone-to-PC................................................................................................. 11 2-3-2-3 Phone to Phone .................................................................................................................. 13 2-4 VoIP Technology ..................................................................................................................... 14 2-4-1 Signaling..................................................................................................................................... 15 2-4-2 Encoding/Decoding.................................................................................................................... 16 2-4-3 Transport ................................................................................................................................... 17 2-4-3-1 Bandwidth efficiency .......................................................................................................... 20 2-4-4 Gateway ..................................................................................................................................... 25 2-5 Security/privacy ..................................................................................................................... 27 2-5-1 VoIP/PSTN security: a comparison ............................................................................................ 28 2-5-2 VoIP security .............................................................................................................................. 28 2-5-2-1 General VoIP security issues .............................................................................................. 29 IV 2-5-2-2 VoIP providers’ security issues ........................................................................................... 30 2-5-2-3 SIP/H.323 security .............................................................................................................. 32 2-5-2-4 Man-In-The-Middle (MITM) and Denial of Service (DoS)................................................... 33 2-5-2-5 Spam over Internet Telephony........................................................................................... 34 2-5-2-6 Biometric encryption .......................................................................................................... 35 2-5-3 Myths about VoIP security ........................................................................................................ 35 2-5-4 VoIP Threat Taxonomy .............................................................................................................. 37 Chapter 3- Methodology...................................................................................................... 40 3-1 Overview................................................................................................................................ 41 3-2 Approach ............................................................................................................................... 42 3-2-1 Research epistemologies ........................................................................................................... 42 3-2-1-1 Positivist studies ................................................................................................................. 43 3-2-1-2 Interpretation studies ........................................................................................................ 44 3-2-1-3 Critical studies .................................................................................................................... 45 3-2-2 Qualitative or quantitative research ......................................................................................... 46 3-2-1-1 Qualitative research ........................................................................................................... 46 3-2-1-2 Quantitative research ......................................................................................................... 47 3-2-1-3 Triangulation ...................................................................................................................... 48 3-2-1-4 Compare and contrast: quantitative versus qualitative research ...................................... 50 3-2-3 Research reasoning process ...................................................................................................... 52 3-2-3-1 Deductive reasoning ........................................................................................................... 52 3-2-3-2 Inductive reasoning ............................................................................................................ 52 3-2-3-3 Compare and contrast: deductive versus inductive reasoning .......................................... 53 3-3 Sampling ................................................................................................................................ 54 3-4-1 General universe, population and sample ................................................................................ 55 3-4-2 Sampling types........................................................................................................................... 56 3-4-3 The used sampling type ............................................................................................................. 57 3-4-3-1 Simple Random Sampling ................................................................................................... 58 3-4-3-2 Purposive sampling ............................................................................................................ 59 3-4 Data Analysis (Quantitative Data) ........................................................................................... 60 3-4-1 Coding ........................................................................................................................................ 60 V 3-4-2 Relationship between variables ................................................................................................ 61 3-5 Research Ethics....................................................................................................................... 62 3-6 Questionnaire design .............................................................................................................. 63 3-7 Summary................................................................................................................................ 64 Chapter 4- Results ............................................................................................................... 65 4-1 Overview................................................................................................................................ 66 4-2 The survey results................................................................................................................... 66 4-2-1 Background ................................................................................................................................ 67 4-2-1-1 Nationality .......................................................................................................................... 67 4-2-2-2 Average monthly talking time ............................................................................................ 68 4-2-3-3 Average monthly international call time via phone/mobile .............................................. 69 4-2-4-4 Using computers to make calls/voice chat......................................................................... 72 4-2-5-5 Average monthly use of computers to make calls/voice chat ........................................... 73 4-2-6-6 Preferred way to make international calls ......................................................................... 74 4-2-7-7 Preferred service for international calls via land line/mobile ............................................ 77 4-2-8-8 Preferred software for making calls/voice chat ................................................................. 78 4-2-2 Awareness/attitude towards VoIP security/privacy.................................................................. 80 4-2-2-1 Concerned features when making international calls........................................................ 80 4-2-2-2 Comparison of security between international/long distance calls and domestic calls .... 82 4-2-2-3 Privacy concerns when making calls .................................................................................. 83 4-2-2-4 Traditional telephony security versus VoIP security .......................................................... 86 4-2-2-5 Concern about VoIP privacy (eavesdropping) .................................................................... 88 4-2-2-6 Possibility of privacy breaches in VoIP versus traditional telephony ................................. 90 4-2-2-7 Concern about VoIP security .............................................................................................. 90 4-2-2-8 Possibility of privacy/security breaches in VoIP ................................................................. 91 4-2-2-9 Discussing security/privacy issues with service providers ................................................. 92 4-2-2-10 The discussed security/privacy issues with service providers ......................................... 93 4-5 Summary................................................................................................................................ 94 Chapter 5- Discussion .......................................................................................................... 95 5-1 Overview................................................................................................................................ 96 VI 5-2 Discussion of the results and findings ...................................................................................... 96 5-2-1 Background ................................................................................................................................ 96 5-2-1-1 Nationality .......................................................................................................................... 96 5-2-1-2 Average monthly talking time ............................................................................................ 96 5-2-1-3 Average monthly international call time ............................................................................ 98 5-2-1-4 Using computers to make calls/voice chat......................................................................... 99 5-2-1-5 Average monthly use of computer to make calls/voice chat ........................................... 100 5-2-1-6 Preferred way to make international calls ....................................................................... 101 5-2-1-7 Preferred service for international calls via land line/mobile .......................................... 101 5-2-1-8 Preferred software for making calls/voice chat ............................................................... 102 5-2-2 Awareness/attitude towards VoIP security/privacy................................................................ 102 5-2-2-1 Concerned features when making international calls...................................................... 102 5-2-2-2 Comparison of security between international/long distance calls and domestic calls .. 103 5-2-2-3 Privacy concerns when making calls ................................................................................ 103 5-2-2-4 Comparison of VoIP and traditional telephony from privacy/security perspective ........ 104 5-2-2-5 Concern about VoIP privacy (eavesdropping)/security.................................................... 105 5-2-2-6 Discussing security/privacy issues with service providers ............................................... 105 5-3 Limitations ........................................................................................................................... 106 5-4 Further research ................................................................................................................... 106 Chapter 6- Conclusion………….. ........................................................................................... 108 Appendix A – Participant information sheet....................................................................... 112 Appendix B- Recruitment email ......................................................................................... 114 Appendix C – Questionnaire .............................................................................................. 115 References ........................................................................................................................ 119 VII List of Figures Chapter 2 Figure 2-1 VoIP implementation: PC-to-PC ................................................................................................... 11 Figure 2-2 VoIP implementation: PC-to-Phone ............................................................................................. 12 Figure 2-3 VoIP implementation: Phone-to-PC ............................................................................................. 12 Figure 2-4 VoIP implementation: Phone-to-Phone........................................................................................ 13 Figure 2-5 Pure VoIP implementation: IP Phone-to-IP Phone........................................................................ 13 Figure 2-6 Multi-site enterprise VoIP implementation .................................................................................. 14 Figure 2-7 IP header .................................................................................................................................... 17 Figure 2-8 UDP header ................................................................................................................................ 18 Figure 2-9 RTP/UDP/IP packet…….…......…Figure 2-10 RTP/UDP/IP packet ..................................................... 19 Figure 2-11 RTP header ............................................................................................................................... 19 Figure 2-12 IPv4/UDP/RTP headers (40 bytes) .............................................................................................. 22 Figure 2-13 IPv6/UDP/RTP headers (60 bytes) .............................................................................................. 22 Figure 2-14 IPv4/IPv6/UDP/RTP header compression ................................................................................... 23 Figure 2-15 50% payload efficiency .............................................................................................................. 23 Figure 2-16 VoIP/PSTN gateway................................................................................................................... 26 Chapter 3 Figure 3-1 Overall research process.............................................................................................................. 41 Figure 3- 2 Deductive research reasoning process Figure 3-3 Inductive research reasoning process .............. 53 Figure 3-4 Sampling overlapping entities...................................................................................................... 55 Figure 3-5 Classification of sampling ............................................................................................................ 57 Chapter 4 Figure 4-1 Overall results by country ............................................................................................................ 67 Figure 4-2 Number of Participants by Country .............................................................................................. 67 Figure 4- 3 The main reason for choosing a service for international calls via Land line/mobile ...................... 77 Figure 4- 4 Reason for choosing software for making calls/ voice chat by computer....................................... 79 Figure 4-5 The most concerned feature when making international calls ....................................................... 80 Figure 4- 6 Valid and irrelevant answers....................................................................................................... 91 Figure 4- 7 Valid, invalid and irrelevant answers ........................................................................................... 93 VIII List of Tables Chapter 1 Table 1- 1 summary of thesis chapters ............................................................................................................................. 5 Chapter 2 Table 2- 1 Audio Codecs ..................................................................................................................................................16 Table 2-2 The three myths about VoIP security ...............................................................................................................36 Table 2-3 VOIPSA’s VoIP Security and Privacy Threat Taxonomy – Misrepresentation treat ...........................................37 Table 2- 4 VOIPSA’s VoIP Security and Privacy Threat Taxonomy – various treats...........................................................38 Table 2-5 VOIPSA’s VoIP Security and Privacy Threat Taxonomy – Interruption of Service treat .....................................39 Table 2- 6 VOIPSA’s VoIP Security and Privacy Threat Taxonomy – Other Interruption of Service treat ..........................39 Chapter 3 Table 3-1 The Different axioms between qualitative (naturalist) and quantitative (positivist) research..........................50 Table 3-2 Qualitative and quantitative research compared and contrasted (adapted from Glesen and Peshkin (1992) ..51 Table 3- 3 Definition of group of individuals in this thesis ...............................................................................................55 Table 3- 4 Data Analysis ..................................................................................................................................................61 Chapter 3 Table 4-1 Average monthly talking time ..........................................................................................................................68 Table 4-2 Relationship between talking time and being concern about VoIP privacy (eavesdropping)............................68 Table 4-3 Relationship between talking time and being concern about VoIP security .....................................................69 Table 4- 4 Average monthly international call time .........................................................................................................70 Table 4-5 Relationship between international talking time and being concern about privacy when making calls ...........70 Table 4-6 Relationship between international talking time and being concern about VoIP privacy (eavesdropping) ......71 Table 4-7 Relationship between international talking time and being concern about VoIP security ................................72 Table 4- 8 Usage of computers to make calls/voice chat .................................................................................................72 Table 4-9 Relationship between using computer to make calls/voice chat and possibility of privacy breaches ...............73 Table 4-10 Average monthly use of computer to make calls/voice chat ..........................................................................74 Table 4-11 Preferred way to make international calls .....................................................................................................74 Table 4-12 Relationship between the preferred way to make international calls and participants’ opinion about whether traditional telephony is more secure than VoIP ..................................................................................75 Table 4-13 Relationship between the preferred way to make international calls and participants’ concern about VoIP privacy ......................................................................................................................................................75 Table 4-14 Relationship between the preferred way to make international calls and participants’ concern about VoIP security .....................................................................................................................................................76 Table 4-15 Preferred software for making calls/voice chat .............................................................................................79 Table 4-16 Relationship between the most concerned feature when making international and participants’ concern about VoIP privacy ............................................................................................................................................81 Table 4- 17 Are international/long distance calls less secure than domestic calls? ..........................................................82 IX Table 4-18 relationship between participants’ opinion about whether international/long distance calls are less secure than domestic calls and whether privacy breaches in traditional telephony is more possible or in VoIP ...................................................................................................................................................................83 Table 4- 19 Concern about privacy when making calls/ voice chat (Five-point scale) ......................................................84 Table 4-20 relationship between participants’ concerns about privacy when making calls and participants’ concerns about VoIP privacy ............................................................................................................................................85 Table 4-21 relationship between participants’ concerns about privacy when making calls and participants’ concerns about VoIP security ...........................................................................................................................................86 Table 4-22 Is traditional telephony (land line/mobile) more secure than VoIP? ..............................................................86 Table 4-23 relationship between participants’ opinion about whether traditional telephony is more secure than VoIP and whether privacy breaches in traditional telephony is more possible or in VoIP ..................................87 Table 4-24 Concern about VoIP privacy (eavesdropping) ................................................................................................88 Table 4-25 relationship between participants’ concern about VoIP privacy and VoIP security ........................................89 Table 4-26 Privacy breach is more possible in traditional telephony or VoIP? .................................................................90 Table 4-27 Concerned about VoIP security (Five-point scale) ..........................................................................................91 Table 4-28 Discussing security/privacy issues with telephone/VoIP service provider ......................................................92 Table 4-30 The discussed security/privacy issues with service providers.........................................................................93 X Acronyms ARPANET Advanced Research Projects Agency Network CLASS Custom Local Area Signaling Services codec coder - decoder iLBC Internet Low Bitrate Codec IN Intelligent Network ITU International Telecommunication Union ITU-T International Telecommunication Union - Telecommunication Standardization Sector PCM pulse code modulation POTS Plain Old Telephone Service PSTN Public Switched Telephone Network QoS Quality of Service RTCP Real Time Control Protocol RTP Real-time Transport Protocol SIP Session Initiation Protocol SS7 Signaling System 7 TCP Transmission Control Protocol UDP User Datagram Protocol VDA Voice Activity Detection VoIP Voice over IP XI Chapter 1- Introduction This chapter serves as the introduction to this thesis and reviews the background literature. It is organized as follows: Section 1.1 provides an overview of this chapter Section 1.2 introduces the background of this thesis Section 1.3 states the purpose of this thesis Section 1.4 defines the aims of this thesis Section 1.5 states the research questions which this thesis intends to answer Section 1.6 describes the significance of this thesis Section 1.7 summarizes the chapters of this thesis 1 Chapter 1- Introduction | 1-1 Overview The following section discusses the background of this thesis by introducing a general overview of Voice over Internet Protocol (VoIP) technology and its security and privacy vulnerabilities. First, the purpose and aims of this study are defined. Next, the major research question that this thesis intends to answer is stated, followed by a discussion on the significance of this thesis. Thirdly and finally, a summary of how the following chapters are organized is provided. 1-2 Background For almost a century, person-to-person communication was dominated by Bell’s legacy, the traditional telephony system. Due to recent advances in the Internet since the 1990s, the “Internet Telephony” technology has now enabled person-to-person communication to take place via computer networks on a global scale. VoIP is an umbrella term for the technologies that enable voice to be transmitted over packetswitched IP networks, such as the Internet. VoIP is comprised of a large number of components including, end user equipment (traditional handsets, softphones or PCs and IP phones), end user applications (Skype, X-Lite, Net-Meeting, etc.), call managers, gateways, switches, routers and protocols. The lower cost and greater flexibility that characterize the main advantages of VoIP over the public switched telephone network (PSTN) are mostly related to the method that voice is transmitted. However, this method - the convergence of voice and data in IP networks complicates security issues and introduces new vulnerabilities. VoIP systems are vulnerable to both VoIP-specific attacks and attacks to the underlying IP network. Consequently, VoIP systems require additional security controls. In the literature, VoIP security has been addressed from technical and industrial perspectives. However, no known research to the best of the researcher’s knowledge has evaluated users’ 2 Chapter 1- Introduction | perspectives on VoIP security and privacy vulnerabilities. To bridge this gap, this study seeks to evaluate the users’ awareness and attitude towards privacy and security issues in VoIP communications. The research methodology that was employed to investigate these matters is quantitative and an on-line questionnaire was designed to collect information. 1-3 Purpose of this study The significance of security issues in VoIP communications are well known, and many papers have been published to address VoIP’s security vulnerabilities. To date, however, no known research has been conducted to evaluate users’ perspective on these issues. This study seeks to evaluate users’ awareness of VoIP security vulnerabilities, and their attitude towards privacy in VoIP communications. An on-line questionnaire was designed to collect information in order to investigate this matter. Chapter 3 explains the on-line questionnaire’s approach and how it was designed, while Chapter 4 presents the results of the study. 1-4 Aims of this thesis This thesis aims: 1- To explore the users’ perspective on security and privacy issues while using VoIP services to communicate with other people. 2- To study the awareness of VoIP users about security issues and their attitudes towards security-related vulnerabilities. 3 Chapter 1- Introduction | 1-5 Research question This research will address the following question: To what extend are VoIP users aware of VoIP security vulnerabilities and what are their attitudes towards these issues? To answer this question, a number of subsidiary questions will be explored in the following order: 1- What is VoIP? 2- What is VoIP architecture and how could it be implemented? 3- What is VoIP security? 4- What are the sources of VoIP’s security vulnerabilities? 5- What is VoIP security and privacy threat taxonomy? 1-6 Significance of this study The innovative nature of this study lies in the fact that it is examining security vulnerabilities of VoIP from users’ perspective. To the best of the researcher’s knowledge, no such similar academic research has been conducted. 4 Chapter 1- Introduction | 1-7 Summary of thesis chapters The thesis chapters are summarized in Table 1-1. Chapters Summary Chapter 1 The innovative nature of this study lies in the fact that it is examining security vulnerabilities of VoIP from users’ perspective. To the best of the researcher’s knowledge, no such similar academic research has been conducted. Chapter 2 A literature review addresses the purpose and aims of this thesis. VoIP architecture and technology, overview of VoIP security and possible vulnerabilities and users’ perspective on VoIP are discussed. Chapter 3 The research methodology used in this thesis is described in order to answer the research question that has been established. Chapter 4 The results and findings of this study are presented. Chapter 5 A discussion about the results is provided. Chapter 6 Conclusion of this thesis is provided. Table 1- 1 Summary of Thesis Chapters 5 Chapter 1- Introduction | Chapter 2- Literature Review This chapter reviews the existing literature concerning the background to the topic of this thesis. It is organized as follows: Section 2.1 provides an overview of the literature reviewed Section 2.2 introduces the elements which contributed to the emergence of VoIP technology Section 2.3 describes VoIP architecture and compares it to PSTN Section 2.4 describes VoIP technology Section 2.5 provides an overview of VoIP security and introduces possible vulnerabilities and threats to VoIP systems 6 Chapter 2- Literature Review | 2-1 Overview This chapter reviews the studies that are relevant to the purpose and aims of this thesis. The elements which contributed to the emergence of VoIP technology are introduced, followed by a detailed description of VoIP architecture and technology. Furthermore, an overview of VoIP security is presented and possible vulnerabilities and threats to VoIP systems are discussed. 2-2 Groundwork of VoIP Although VoIP systems could be implemented purely based on IP networks, generally they are interconnected to traditional telephony systems and rely on them for delivering voice traffic. In fact, the interoperability of traditional and IP telephony systems significantly contributed to the widespread acceptance of VoIP. The invention of and advances telephony systems and the Internet have provided the foundation of VoIP technology. The evolution of telephony systems and the Internet are discussed in the following sections. 2-2-1 Telephony system ‘Mr. Watson, come here, I want to see you’; this phrase was the first ever transmitted speech over wire and it was sent by Alexander Graham Bell in 1876 (Flood 1976; Brittain 2005). Bell’s work evolved from a scientific curiosity into an essential communication method that has influenced people’s lives ever since. At the early stage, each two-call party devices were connected by a single wire and no dialing was required. Later, the telephone system improved and instead of having physical cables between each end-to-end receiver only one cable was needed to connect users to telephone centers. Operators at telephone centers did the switching between call parties. As further 7 Chapter 2- Literature Review | advances were made in telephony systems, manual switching was replaced by electronic switches. The basic telephone system is called the Plain Old Telephone Service (POTS) and in contrast, the more advanced one which is able to carry both analog and digital traffic is called Public Switched Telephone Network (PSTN)1. During the past decades PSTN developed from a relatively non-complex network to a so-called Intelligent Network (IN). IN is based on a signaling method known as Signaling System 7 (SS7), which enables PSTN to offer Custom Local Area Signaling Services (CLASS) services. Examples of these include “Call blocking” and “Automatic callback” (Davidson et al. 2006). 2-2-2 The Internet On the 29th of October 1969 at 10:30 pm for the first time data was transferred over a packet switched network. The network consisted of two nodes one located at Stanford Research Institute (SRI) and the other one at University of California, Los Angeles (UCLA) connecting with a link at 50kb/s. The researcher’s goal was to type the word “log” at UCLA’s node and SRI’s node added “in” to it in order to create the word “login”. In practice, however, only “l” and “o” were transmitted and then the UCLA’s machine crashed (Kleinrock 2008). Later in that same year (1969) two other nodes - one at University of California at Santa Barbara and the other one at University of Utah - were added to the two previous nodes and formed the first four nodes of what became known as ARPANET (Kleinrock 2008; O'Neill 1995). The above-mentioned research was a part of the Advanced Research Projects Agency Network (ARPANET) deployment. ARPANET, the ancestor of the Internet, was the first operational packet-switched network that was conducted by the Advanced Research Projects Agency 1 In some publications the term general switched telephone network (GSTN) is used to refer to the telephony system. However, PSTN is more common. 8 Chapter 2- Literature Review | (ARPA), established in February 1958 by the US Department of Defense (O'Neill 1995). Lukasik (2010) provides an extensive discussion on why the ARPANET was built. The invention of the World Wide Web (commonly known as the Web) was a milestone in the history of the Internet. Its creator, Tim Berners-Lee, defines it “as the universe of global network-accessible information” (Berners-Lee 1996). The tremendous commercial potential of the Web attracted businesses and provided opportunities. The emergence of giant Internetrelated businesses such as eBay and Google indicates that a new era has arisen due to web technologies. What is called the Internet is in fact a massive infrastructure that exploits a wide range of technologies and provides global communication channels for millions of people around the world. VoIP is an example of such a communication channel. 2-3 VoIP Architecture This section provides an overview of VoIP architecture by comparing it to PSTN, and describes its implementations. Three main VoIP implementations are discussed: (1) PC-to-PC, (2) PC-toPhone/phone-to-PC and (3) Phone-to-Phone. These are high-level overviews of VoIP functional architecture but they do not represent the physical implementation. 2-3-1 PSTN versus VoIP The main difference between PSTN and VoIP is in the method by which they transmit voice conversations. PSTN is a circuit switched network, while VoIP is a packet switched network. PSTN uses reliable2 fixed bandwidth with an end-to-end dedicated line (circuit) which is set up 2 Carrier class reliability is a term which refers to the 99.999 % availability of the PSTN. The downtime of PSTN is about 5 minutes in a year. 9 Chapter 2- Literature Review | by circuit switches. In contrast, VoIP splits the voice into packets and sends them independently through various paths using shared bandwidth (Goode 2002). PSTN is comprised of switches and network devices that provide fixed line telephone services. Its Quality of Service (QoS) is high and its network availability is almost 100%, while VoIP’s QoS is lower and its network availability is not known (Varshney et al. 2002). Additionally, VoIP is based heavily on the already existing worldwide PSTN networks, even though its active environment is the Internet. In fact, PSTN and VoIP overlap in terms of physical facilities as some of VoIP’s traffic originates and terminates via PSTN (Groom & Groom 2004, p. 10). The differences between PSTN and VoIP are discussed in detail in Schulzrinne and Rosenberg (1999), Varshney et al.( 2002) and Bross and Meinel (2008). 2-3-2 VoIP implementation VoIP can be broadly implemented in three different ways, namely PC-to-PC, PC-toPhone/phone-to-PC and Phone-to-Phone. These are discussed in sub-sections 2-3-2-1, 2-3-2-2 and 2-3-2-3, respectively. 2-3-2-1 PC-to-PC The first commercial PC-to-PC VoIP application was introduced by VocalTec in 1995 (Corrocher 2003). VocalTec released the “Internet Phone” software which enabled telephone conversations take place via PCs over the Internet (Groom & Groom 2004, p. 22). Figure 2-1 portrays VoIP PC-to-PC model. In this scenario, voice call is made from a softphone (computer) to another softphone (computer) through the Internet; PSTN is not involved. 10 Chapter 2- Literature Review | . Figure 2-1 VoIP implementation: PC-to-PC X-Lite (Mac/Windows), iChat (Mac), Gno-Phone (Linux), Net-Meeting (Windows) and Skype (cross platform, supports Mac, Windows and Linux) are examples of VoIP client software. X-Lite and Gno-Phone are designed to be used with different VoIP providers, including our own VoIP server, while others have to be used with a certain VoIP provider. Skype3 is the most prevalent VoIP PC to PC provider (Bonfiglio et al. 2008; Wallingeord 2006, p. 63) and its and its popularity has garnered the attention of the research community. For instance, Skype protocol is discussed in detail in Baset and Schulzrinne (2006) and Skype traffic is investigated in Perenyi et al. (2007), Bonfiglio et al. (2009), Branch, Heyde and Armitage (2009), while Srivatsa et al. (2010) and Ye et al. (2009) address Skype privacy issues. 2-3-2-2 PC-to-Phone/ Phone-to-PC Skype offers free services including PC-to-PC (Skype-to-Skype) voice/video calls, conference calls and instant messaging. However, Skype also provides fee applied services including PC-toPSTN (SkypeOut), which makes it possible for calls to be placed from PCs to landlines/mobiles, and PSTN-to-PC (SkypeIn). The last system enables calls to be placed from landlines/mobiles to PCs. 3 www.skype.com 11 Chapter 2- Literature Review | In a similar vein, Yahoo! Messenger provides free PC-to-PC (Yahoo! Messenger-to-Yahoo! Messenger) calls, but also offers paid services, allowing users to initiate and receive calls through “Phone Out” and “Phone In” services4. Google’s introduction of its Google Voice service enabled the company to become a telecommunication service provider like Skype and Yahoo. Currently, Google Voice offers free inbound and outbound calls to Canada and the US and paid international calls5. In the PSTN-to-PC scenario, voice call is made from PSTN telephones to PCs with VoIP software. In this scenario, voice traffic originates from PSTN and is then transmitted over the Internet (see Figure 2-3). In contrast, in the PC-to-PSTN scenario, voice call is made from PCs (with appropriate VoIP software) to PSTN. Here, voice traffic terminates in PSTN after being transmitted over the Internet (see Figure 2-2). Figure 2-2 VoIP implementation: PC-to-Phone Figure 2-3 VoIP implementation: Phone-to-PC 4 5 http://messenger.yahoo.com/features http://www.google.com/googlevoice/whatsnew.html 12 Chapter 2- Literature Review | The VoIP-PSTN gateways allow appropriate conversions between the two networks to take place. 2-3-2-3 Phone to Phone In its simplest form, voice call is made from a PSTN telephone to another PSTN telephone. Voice traffic originates and terminates in PSTN while it traverses through the Internet. This method is fashionable for individual and residential use. Figure 2-4 illustrates this model. Figure 2-4 VoIP implementation: Phone-to-Phone A pure VoIP network solution can be employed for inter-site communication in businesses. In its simplest form, a call is made from an IP phone to another IP phone completely through the site’s IP network; PSTN is not involved. IP phones are directly connected to networks via patch cables or wireless links. They have IP addresses and they communicate with VoIP servers through IP networks. In enterprises, IP Private Branch eXchange (PBX) handles inter-site communication. Figure 2-5 illustrates a simple pure VoIP implementation. Figure 2-5 Pure VoIP implementation: IP Phone-to-IP Phone 13 Chapter 2- Literature Review | In practice, enterprises, especially those who have multiple sites, are more likely to employ a variety of telephony network options for placing calls. This includes PSTN, the public Internet and private Wide Area Network (WAN) connection or Virtual Private Network (VPN). In this scenario, the IP PBX handles both intra-enterprise VoIP calls and PSTN call routing support. VoIP gateways provide connectivity between VoIP and PSTN. Figure 2-6 illustrates multi-site enterprise VoIP connection options. PSTN IP PBX IP PBX Phone Phone Computer Computer Internet IP Phone Gateway/Router IP Phone Fax Site 1 VPN VPN Private IP Network VPN Gateway/Router Fax Site 2 Private IP Network Figure 2-6 Multi-site enterprise VoIP implementation 2-4 VoIP Technology VoIP refers to a class of technologies that enables multimedia (text6/voice/video) traffic to be transferred over IP networks. The fundamental concept of VoIP is the digitization and packetization of the human voice. The speech (voice analogue signals) is converted into digital signals by appropriate coders/decoders and it is then broken into packets and transferred over Internet Protocol (IP)-based networks like the Internet. 6 Instant messaging (IM), which is a real time text base network communication method, is considered to be a VoIP service. IM is distinguishable from on line text chatting. Via IM only specified known users communicate, while via on line text chatting in addition to known users often anonymous users communicate. In addition to IM, fax is also considered to be a VoIP service. 14 Chapter 2- Literature Review | The procedures involved in placing voice conservation over VoIP can be broadly categorized in the following four stages: signaling, encoding/decoding, transport, and gateway. These are described in more detail in the following sub-sections. 2-4-1 Signaling In the signaling stage, calls between end nodes are established, maintained, and terminated. The details of the calls (codec type, packet size, etc.) are negotiated and agreed by the end nodes. Signaling protocols carry out these tasks. Session Initiation Protocol7 (SIP) and H.3238 are the two most common VoIP signaling protocols. The former was specified by the Internet Engineering Task Force (IETF)9, whereas the latter was developed by ITU-T10. In-depth description of SIP is provided in Schulzrinne and Rosenberg (1998b),Schulzrinne and Rosenberg (2000), while H.323 is discussed in detail in Thom (1996) and Hong and Mouchtaris (2000). Comparisons of SIP and H.323 can be found in Schulzrinne and Rosenberg (1998a), Glasmann, Kellerer and Muller (2001), Glasmann, Kellerer and Muller (2003), and Basicevic, Popovic and Kukolj (2008). 7 SIP was first defined in March 1999 by RFC 2543 (http://tools.ietf.org/html/rfc2543), and was then upgraded in June 2002 by RFC 3261 (http://www.ietf.org/rfc/rfc3261.txt). The latter RFC is one of the longest standards (269 pages) defined by Internet Engineering Task Force (IETF). 8 ITU-T recommendation H.323 (version 1) was approved on 8 November 1996 under the World Telecommunication Standardization Conference (WTSC) Resolution No. 1 and its title was ‘Visual telephone systems and equipment for local area networks which provide a non-guaranteed quality of service’. This version was revised and the second version titled ‘Packetbased multimedia communications systems’ (which reflected more its functionality and was consistent with its expanded scope) was approved on 6 February 1998. Over the past decade H.323 has been superseded by more recent versions. The last version of H.323 (ITU-T H.323 v7) was approved on 14 December 2009 with the same title as the second version. 9 www.ietf.org ITU-T is described in the foreword section (page iii) of the ‘Recommendation H.323 (12/09)’ (http://www.itu.int/rec/T-RECH.323-200912-I/en) as: 10 ‘ITU (International Telecommunication Union) is the United Nations Specialized Agency in the field of telecommunications. The ITU Telecommunication Standardization Sector (ITU-T) is a permanent organ of the ITU. The ITU-T is responsible for studying technical, operating and tariff questions and issuing Recommendations on them with a view to standardizing telecommunications on a worldwide basis.’ 15 Chapter 2- Literature Review | 2-4-2 Encoding/Decoding The converting and compressing of analog voice to digital data is accomplished by codecs in the encoding/decoding stage. The term codec11 is derived from the combination of coder/decoder. Based on Nyquist theorem, codecs convert analog voice into digital signals. According to Nyquist theorem, analog voice must be sampled at a minimum of more than twice its frequency (Broesch 1997). Since generally speech content is less than 4000 Hz (Davidson & Peters 2000), sampling rate of 8000 times per second is required. G.711, the most widely used codec in PSTN, employs pulse code modulation (PCM) algorithm for sampling purposes. PCM uses eight bits per sample and therefore requires (8000 Hz x 8 bit = 64000 bps = 64 kbps) 64 kbps bandwidth. Currently, this amount (64 kbps) is considered to be a baseline unit in terms of bandwidth requirement in VoIP networks. Assuming G. 711’s packet interval (gap between transmitted packets) is 10 ms (1/100th second), (64000 / 100 = 640) 640 bits (80 bytes) of G.711 data (voice data) is placed in each packet. Each codec employs a compression algorithm and based on the algorithm utilizes network bandwidth. Table 2-1 compares some codecs. Codec Algorithm Usual Rate (kb/s) G.711 PCM 64 G.726 ADPCM 32 G.729a CS-ACELP 8 G.723.1 MP-MLQ 6.3 G.723.1 ACELP 5.3 iLBC LPC 15.2 iLBC LPC 13.33 Table 2- 1 Audio Codecs 11 In some publications the term VOCODER (VoIP Coders) is used to refer to codec. However, codec is more prevalent. 16 Chapter 2- Literature Review | Many audio codes are available. The G-series12 (G.xxx) codecs which are defined by International Telecommunication Union13 -Telecommunication Standardization Sector (ITU-T)14 are fashionable in VoIP networks. iLBC15 (Internet Low Bitrate Codec) which is a free audio codec is currently used by popular VoIP PC-to-Phone providers, such as Skype and Yahoo! Messenger (Davidson et al. 2006). Furthermore, G.729 or G.723 codec is commonly used over WAN links since they offer a high compression rate while preserving reasonable speech quality (Hanes & Salgueiro 2008, p. 131). Codecs are discussed in detail in Karapantazis and Pavlidou (2009, pp. 2055-2059). 2-4-3 Transport After a call is established, actual voice traffic is transmitted between the end nodes. The Internet Protocol16 (IP) is used to transmit data from sources to destinations in packetswitched networks. Both sources and destinations are identified by IP addresses. As shown in Figure 2-7, the IP header contains source and destination address. Best routes between the source and destination nodes are determined by routing protocols. Version IHL Type of Service Total Length Identification Flags Fragment Offset Time to Live Protocol Header Checksum Source Address Destination Address Options Padding Data (Variable) Figure 2-7 IP header 12 http://www.itu.int/net/itu-t/sigdb/speaudio/Gseries.htm http://www.itu.int/en/pages/default.aspx 14 http://www.itu.int/ITU-T 15 http://www.ilbcfreeware.org 16 IP was defined in 1981 by RFC 791 (http://datatracker.ietf.org/doc/rfc791/) which is based on six earlier versions of IP specification. 13 17 Chapter 2- Literature Review | IP is employed by local network protocols, such as Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) to carry datagrams17 (packets). Therefore, UDP and TCP run on top of IP as the data portion of an IP datagram. Generally, TCP/IP is used when reliability is the main concern and UDP/IP is employed when speed of data delivery is of interest. TCP18 guarantees packet delivery by providing acknowledged and flow-controlled service. Therefore, it is generally the case that TCP is used in the signaling stage to ensure the reliability of call establishment. However, due to the time sensitive nature of VoIP traffic, it is not feasible to use TCP to carry the actual voice traffic. Since VoIP traffic is delay sensitive, controlling latency in VoIP networks is more important than controlling packet loss. Therefore; UDP19, which does not wait for acknowledgment of the delivered packets and does not require prior negotiations to establish special transmission channels, is used to carry voice traffic. UDP is a simple protocol which its header contains only four fields as depicted in Figure 2-8. Source Port Length Destination Port Checksum Figure 2-8 UDP header However, since UDP does not provide the information that the receiving nodes require to correctly reassemble the digitized voice packets into a voice signal, Real-time Transport Protocol (RTP) is employed in conjunction with UDP. Therefore, VoIP traffic is carried with an RTP/UDP/IP packet header. In other words, the actual voice data is transmitted by RTP packet 17 In the literature, datagram and packet are often considered to be synonymous. However, datagram refers to unreliable packet delivery. For instance, since UDP and IP do not guarantee packet delivery, UDP/IP packets are called datagrams. 18 TCP was defined in 1981 by RFC 793 (http://datatracker.ietf.org/doc/rfc793/) which is based on nine earlier versions of TCP specification. 19 UDP was defined in 1980 by RFC 768 (http://tools.ietf.org/html/rfc768). 18 Chapter 2- Literature Review | which is carried as data by the UDP datagram, and UDP itself is encapsulated by IP. Figures 2-9 and 2-10 illustrate the simplified layout of RTP/UDP/IP packet. IP header IP Payload UDP header UDP Payload IP header RTP header RTP Payload RTP UDP header header Voice Data Codec Payload (Actual Voice Data) Figure 2-9 RTP/UDP/IP packet Figure 2-10 RTP/UDP/IP packet RTP20 provides the necessary information, such as orders of the arriving packets and the variation of consecutive packets arrival time. The information is provided by the sequence number and timestamp field of RTP’s header (see Figure 2-11). V=2 P X CC M PT Sequence Number Timestamp Synchronization Source (SSRC) identifier Sontributing Source (CSRC) identifiers ……… Figure 2-11 RTP header However, RTP does not guarantee on-time delivery, reliability, Quality of Service (QoS) and resource reservation, and relies on its associated control protocol, Real Time Control Protocol (RTCP), for providing these. In fact, RTCP21 extends RTP’s functionality, particularly by 20 Packet structure and basic functions of RTP was first defined in 1996 by RFC 1889 (http://www.ietf.org/rfc/rfc1889.txt) and then it was updated in 2003 by RFC 3550 (http://tools.ietf.org/html/rfc3550). 21 RTCP was first defined in 1996 by RFC 1889 (http://www.ietf.org/rfc/rfc1889.txt) and then it was updated in 2003 by RFC 3550 (http://tools.ietf.org/html/rfc3550). 19 Chapter 2- Literature Review | monitoring QoS. This is done by receiving feedback on the quality of the delivered data which is conveyed by RTCP packets periodically sent by participants in an RTP session. 2-4-3-1 Bandwidth efficiency With advances in network technologies, more bandwidth is available now than in the past. However, bandwidth is still considered to be a premium resource, especially in wireless VoIP networks. Therefore, significant efforts have been made to minimize bandwidth consumption of network applications. The main techniques used to increase bandwidth efficiency in VoIP networks are speech compression codecs, Voice Activity Detection (VAD) and header compression. 2-4-3-1-1 Speech compression codecs The speech compression codecs technique employs appropriate codecs that require less bandwidth. The consumed bandwidth per call much depends on the selected codec and number of voice samples per packet. Davidson et al. (2006 p. 178) describe the correlation between bandwidth consumption and packet sizes. Packetization efficiency which refers to the number of voice samples in an IP packet is an important factor. On the one hand, placing less voice samples in an IP packet is inefficient since the header overhead will increase. On the other hand, when more voice samples in an IP packet are placed, the packet becomes larger, which this can lead to packet loss and the increase of end-to-end delay. The number of voice samples that is sent per packet depends on the employed codec. For example, G.711 usually takes 80 bytes of Voice data while G.729 takes 20 bytes (Oouch et al. 2002). Karam and Tobagi (2001) investigated the impact of packet size on bandwidth utilization and voice delay for G.729A, G.723.1 and G.711 codecs. It was concluded that 30 ms of speech for 20 Chapter 2- Literature Review | both G.729.A and G.723.1 with packet size of 30 bytes and 20 bytes respectively, and 10 ms speech for G.711 with packet size of 80 bytes, provide a reasonable trade-off between efficient network utilization and low voice delay. In another study, Oouch et al. (2002) studied the effect of packet size on voice quality under different network conditions for G.711 and G.729 codecs. They revealed that voice quality is not affected by the size of the packet when packet loss rates are very low. However, smaller packets are superior to larger ones in terms of voice quality when packet loss rates are moderate or high. 2-4-3-1-2 Voice Activity Detection Generally, in conversations, one speaks and one listens. In addition, there are breaks and pauses in normal conversations. This means that about 50 percent of the dedicated bandwidth for voice traffic transmission is wasted. According to Beritelli et al (cited in Chen et al. 2010), a typical conversation has a speech to non-speech ratio of forty to sixty. Voice Activity Detection (VAD) is a technique that enables the wasted bandwidth in VoIP networks be used for other purposes. This is achieved by detecting the voiced and non-voiced segments of analog sound signals. VAD function can be broadly divided into two modules, speech analysis and decision module (Huang & Lin 2009). The former extracts acoustic parameters from the input sound signal in order to distinguish speech from non-speech segments, while the latter based on the extracted parameters and decision rules determines whether the input signal is speech or noise (Chen et al. 2010). Quality of speech, level of compression and computational complexity of different VoIP VDA algorithms are compared in Venkatesha Prasad et al. (2002). 21 Chapter 2- Literature Review | 2-4-3-1-3 Header compression The voice packets usually have a payload of 20 to 60 bytes, depending on the employed codec (Karapantazis & Pavlidou 2009) and the IP version 4 (IPv4)/UDP/RTP header is 40 bytes. . It consists of an IP header of 20 bytes, an UDP header of 8 bytes and a RTP header of 12 bytes, while for IP version 6 (IPv6) this will be 60 bytes since the IPv6 header is 40 bytes. This means that bandwidth is used to transfer VoIP packets in which the payload is about the same size or even smaller than the header. A simplified form of IPv4/UDP/RTP and IPv6/UDP/RTP headers is illustrated in Figures 2-12 and 2-13. 20 bytes 8 bytes 12 bytes IPv4 header UDP header RTP header Voice Data Payload Headers 40 bytes 20 - 60 bytes Figure 2-12 IPv4/UDP/RTP headers (40 bytes) 40 bytes IPv6 header 8 bytes UDP header 12 bytes RTP header Voice Data Headers Payload 60 bytes 20 - 60 bytes Figure 2-13 IPv6/UDP/RTP headers (60 bytes) The header information including the source and destination addresses, type of service, protocol identifiers, etc. are essential for successful end-to-end transfer of packets over multiple links. However, in order to improve bandwidth efficiency IP/UDP/RTP headers can be compressed on a hop-by-hop basis. This means that the header of VoIP packets is compressed before being transferred on a link and it is decompressed at the other end of the link. According 22 Chapter 2- Literature Review | to Casner and Jacobson (1999), an IP/UDP/RTP header can be compressed to 2-4 bytes. Header compression is depicted in Figure 2-14. 20-40 bytes 8 bytes 12 bytes IPv4/IPv6 header UDP header RTP header Voice Data Payload Headers 40 - 60 bytes 20 - 60 bytes IPv4/IPv6/UDP/RTP header compression Voice Data Headers 2-4 bytes Payload 20 - 60 bytes Figure 2-14 IPv4/IPv6/UDP/RTP header compression The obvious advantage of header compression is efficient bandwidth utilization. However, improving the payload efficiency (the ratio of voice data (payload)/total packet size), which leads to shorter end-to-end delay, is a significant benefit of employing header compression. Since the IPv4/UDP/RTP header is 40 bytes, to have 50% payload efficiency we therefore need a payload of 40 bytes (40 bytes/80 bytes=50% payload efficiency). This is depicted in Figure 2-15. 20 bytes 8 bytes 12 bytes IPv4 header UDP header RTP header Voice Data Headers Payload 40 bytes 40 bytes Figure 2-15 50% payload efficiency 23 Chapter 2- Literature Review | According to Goode (2000), it takes 5 ms to accumulate 40 bytes at 64kb/s while at 8kb/s it takes 40 ms to accumulate 40 bytes. Therefore, low payload efficiency, especially in conjunction with low bit rate codecs, will increase the end-to-end delay. The following equation is proposed by Goode (2000, p. 1499): Codec output rate (kb/s) The call bandwidth requirement (kb/s) BW = R + H/S Payload sample size (milliseconds) Header size (bits) Low BW leads to long packetization delay and more complex codec. To achieve the requirements for reasonable call bandwidth, reasonable codec complexity and an acceptable packetization delay, a trade-off must be made (Goode 2000, p. 1499). Header Compressions is discussed in (Karapantazis & Pavlidou 2009; Casner & Jacobson 1999; Degermark, Nordgren & Pink 1999; Koren et al. 2003; Engan, Casner & Bormann 1999; Engan, Casner & Bormann 2003; Liu et al. 2001). 24 Chapter 2- Literature Review | Header Compressions methods such as IP Header Compression (IPHC)22, Compressed Real-time Transport Protocol (CRTP)23, Enhanced CRTP24 and RObust Header Compression (ROHC)25 are defined in deferent Request for Comments (RFCs)26. 2-4-4 Gateway Direct connection between packet switched network (VoIP) and circuit-switched networks (PSTN) is not feasible, because in addition to voice data, signaling data is also exchanged between VoIP and PSTN networks. In PSTN, the Signaling System Number 7 (SS7) is used, while in VoIP, SIP and H.323 are the most common signaling protocols. 22 IP Header Compression (IPHC) is described in RFC 2507- ‘IP Header Compression’ (http://www.faqs.org/rfcs/rfc2508.html) in 1999. IPHC can be applied to multiple IP headers and TCP/UDP headers on a hop-to-hop basis. The mechanism for TCP header compression in RFC 2507 is similar to the proposed technique in 1990 in RFC 1144 – ‘Compressing TCP/IP Headers for LowSpeed Serial Links’ (http://www.faqs.org/rfcs/rfc1144.html). 23 Compressed Real-time Transport Protocol (CRTP) is described in RFC 2508 – ‘Compressing IP/UDP/RTP Headers for LowSpeed Serial Links’ in 1999 (http://www.faqs.org/rfcs/rfc2508.html). By employing CRTP, IP/UDP/RTP headers can be compressed to 2-4 bytes. 24 Enhanced CRTP is described in RFC 3545 – ‘Enhanced Compressed RTP (CRTP) for Links with High Delay, packet Loss and Reordering’ in 2003 (http://www.faqs.org/rfcs/rfc3545.html). This document describes a header compression method for point to point links with packet loss and long delays. It is based on CRTP which is described in RFC 2508 – ‘Compressing IP/UDP/RTP Headers for Low-Speed Serial Links’. CRTP does not work well in networks with packet loss and long delays. 25 RObust Header Compression (ROHC) described in RFC 3095 – ‘RObust Header Compression (ROHC): Framework and four profiles: RTP, UDP, ESP, and uncompressed’ in 2001 (http://www.faqs.org/rfcs/rfc3095.html). The abstract of this RFC states: This document specifies a highly robust and efficient header compression scheme for RTP/UDP/IP (Real-Time Transport Protocol, User Datagram Protocol, Internet Protocol), UDP/IP, and ESP/IP (Encapsulating Security Payload) headers. ROHC header compression is proposed for links with significant error rates and long round-trip times. 26 RFC 2509 – ‘IP Header Compression over PPP’ (http://www.faqs.org/rfcs/rfc2509.html) describes an option for negotiating the use of IPHC & CRTP over the Point-to-Point Protocol. The authors in a more recent version in 2003 in RFC 3544 – ‘IP Header Compression over PPP’ (http://www.faqs.org/rfcs/rfc3544.html) defined extensions to the PPP Control Protocols for improvement in IPHC & CRTP usage over the Point-to-Point Protocol. 25 Chapter 2- Literature Review | During the gateway stage, protocol translation and media transcoding between VoIP and PSTN are provided. Consequently, PSTN calls can be completed through VoIP networks and vice versa. In fact, connectivity between the PSTN (circuit switched network) and VoIP (packet switched network) is navigated through the VoIP/PSTN gateway. This is illustrated in Figure 216. Figure 2-16 VoIP/PSTN gateway Building on this theme, VoIP/PSTN gateways transfer voice and fax data, in real-time, between VoIP and PSTN networks and their functionality can be categorized as signaling gateway and media gateway. Signaling gateway provides interworking of signaling between VoIP/PSTN networks, while media gateway compresses, packetizes and delivers voice packets to the VoIP network; its procedure is the exact opposite of the PSTN network (Karapantazis & Pavlidou 2009). 26 Chapter 2- Literature Review | 2-5 Security/privacy The Oxford Advanced Learner’s Dictionary27 defines security as ‘the activities involved in protecting a country, building or person against attack, danger, etc. and it defines privacy as ‘the state of being alone and not watched or disturbed by other people’. There is a relationship between security and privacy. From the VoIP perspective, a simple definition is that privacy is having a communication that is free from unauthorized access and security means maintaining this privacy. . VOIPSA28 provides a more general definition of security and privacy. Privacy is defined as: The Privacy Concept is the privilege of all people to have their communication systems and content free from unauthorized access, interruption, delay or modification. And security is defined as: 1) the right to protect privacy, 2) a method of achieving privacy and 3) ways to keep communication systems and content free from unauthorized access, interruption, delay or modification. 27 Oxford Advanced Lerner’s dictionary – 7th edition – the software version The Voice Over IP Security Alliance (VOIPSA) is an non-profit organization which according to its website (www.voipsa.org/About) their ‘… aims [are] to fill the void of VoIP security related resources through a unique collaboration of VoIP and Information Security vendors, providers, and thought leaders.’ and their ‘… mission is to drive adoption of VoIP by promoting the current state of VoIP security research, VoIP security education and awareness, and free VoIP testing methodologies and tools.’ 28 27 Chapter 2- Literature Review | 2-5-1 VoIP/PSTN security: a comparison It is generally assumed that PSTN is more secure than VoIP. Basically, PSTN security is based on the physical security of the core network equipment and the related components on the customer's premises. This model known as ‘physical wire security’ seems to be efficient enough for PSTN since attacks which require physical access usually do not scale in a distributed environment. However, an eavesdropper can wiretap PSTN by physically accessing telephone lines which is much easier than to wiretap VoIP systems. Security issues in PSTN are discussed in (Porter et al. 2006a, pp. 114-118). On the other hand, the nature of VoIP security is such that it is not based on wire security. However, by gaining access to traffic on a VoIP network that is not well secured, VoIP packets could be captured, modified, reassembled or controlled to overturn the security behavior. VoIP systems may be attacked by non-specialists using free VoIP-sniffers such as Vomit29 and VoiPong30, but hacking PSTN generally requires specialist knowledge. 2-5-2 VoIP security For data to be transmitted over IP networks, a large number of parameters have to be configured. Many of these parameters are configured dynamically and since a wide range of configurations is involved, networks suffer from potentially vulnerable points. Generally, VoIP uses the existing IP networks and therefore inherits their vulnerabilities. Adding voice traffic to IP networks complicates security issues and introduces a range of vulnerabilities. This is because VoIP requires VoIP-specific configurable parameters in addition to the existing ones in the underlying IP networks, such as call processing components. These parameters change dynamically each time VoIP services are started or restarted. 29 Voice Over Misconfigured Internet Telephones (vomit) is a completely free utility (even commercial use of it is permitted) that converts VoIP conversations (only G.711 encoded) on Cisco IP phones into wave files (http://vomit.xtdnet.nl/). 30 VoIPong is an open source utility which converts VoIP conversations (only G.711 encoded) into wave files (http://www.enderunix.org/voipong/). 28 Chapter 2- Literature Review | Providing integrated services (messenger, email and web) in addition to rich media (voice, video, text and fax) (Patrick 2009) and VoIP-PSTN interconnection, are other factors which complicate VoIP security. From a security perspective, VoIP is not just another application attached to the IP network. Although VoIP packets traverse IP network routes and are distributed between the IP networkconnected machines, the network components including switches, routers, firewalls and network address translation (NAT), must be VoIP aware, so that they can provide specific VoIP security features. For example, ordinary firewalls are generally not able to protect VoIP systems from VoIP specific application layer attacks, such as malformed H.323 or SIP messages, due to the fact that these firewalls cannot detect such attacks. To address these kinds of flaws, VoIP security devices/modules and systems, such as Session border controllers (SBCs) 31, should be employed. VoIP security has been discussed from different perspectives. VoIP general security issues, VoIP providers’ security issues, SIP/H.323 security, Man-In-The-Middle (MITM) and Denial of Service (DoS), Spam over Internet Telephony (SPIT) and Biometric encryption are discussed in the following sub-sections. 2-5-2-1 General VoIP security issues Studies in this category generally do not contain in-depth technical discussions. They only provide a broad overview of VoIP security, guidelines, and a classification of vulnerabilities and possible threats and attacks. Therefore, they are not informative for professionals, but are valuable literature for new researchers in the field of VoIP security. 31 According to the Gartner Report, ‘IT Market Clock for Enterprise Networking Infrastructure, 2010’, Session border controllers (SBCs) provides ‘… a secure, controlled connection for points between networks that provide interactive, Internet Protocol (IP)based communications like Session Initiation Protocol (SIP)-based unified communications (UC)’. Furthermore, in another Gartner Report, ‘How to Leverage SIP Trunks, Session Border Control and Session Management for Cost Savings and UC Deployment’ it is stated that ‘ Session border controllers (SBCs) can reduce SIP-based denial of service (DoS) threats that originate from within and outside an organization…’ and ‘… improve[s] enterprise communications security,… , operational efficiency and reliability’. 29 Chapter 2- Literature Review | General VoIP security issues have been addressed in different papers (Dantu et al. 2009; Epstein 2009, pp. 323-347; Gupta & Shmatikov 2007; Butcher, Xiangyang & Jinhua 2007; Douglas & Tom 2004). Namely, Kuhn, Walsh and Fries’ (2005) research in this area is notable. This study is a special report from the US National Institute of Standards and Technology (NIST) which provides security recommendations for VoIP implementation. In this research, the VoIP’s risks, threats and vulnerabilities are analyzed along with the encryptions that can be applied. Further, the effect of securing VoIP on QoS is discussed in depth. Similarly, Walsh and Kuhn’s (2005) study discusses the overall security aspects of VoIP and avoids technical details. It concentrates on the need for new technologies to combat security breaches. 2-5-2-2 VoIP providers’ security issues The studies in this category evaluate security issues of VoIP providers. Different security features concerning the popular VoIP providers are analyzed and sometimes are compared. Skype, due to its widespread usage, has drawn more attention than other VoIP providers. Skype security has been discussed from different angles. For example, Simon and Slay (2010) discuss Skype security from the forensic perspective. Their study shows that it is feasible to exploit the physical memory of the computer on which Skype was running, in order to recover the digital evidence. Moreover, Zhu and Fu (2010) address Skype passive traffic analysis attacks and show that privacy of Skype calls can be compromised by launching passive traffic analysis attacks. In Sengar et al. (2010) a transparent packet marking scheme is presented for tracing Skype packets in order to disclose the path and the origins and destination of a Skype call. Additionally, Wang, Chen and Jajodia (2005) investigate Skype encryption and show that when a unique watermark is embedded into the encrypted flow, it is feasible to trace calls and launch a timing attack. An overview of Skype security is addressed in Piccard (2006, pp. 103-121), and Porter and Gough (2007, pp. 253-262). 30 Chapter 2- Literature Review | Some weighty papers have surveyed security issues of other dominant VoIP providers. For instance, the study conducted by Zhang et al. (2009a) shows that a remote attacker who knows the IP address and phone number of a Vonage (residential VoIP provider in the US) client is able to eavesdrop and hijack calls by launching a DNS spoofing attack. Although Ahmed and Shaon’s (2009) research mainly concentrates on comparing the QoS in different VoIP providers (Skype, GTalk, and Gizmo), the compared security criteria amongst them are useful. 31 Chapter 2- Literature Review | 2-5-2-3 SIP/H.323 security VoIP comprises different components with a range of protocols where each has its own security concerns. H.323 and Session Initiation Protocol (SIP) are the two most common signaling protocols used in VoIP’s signaling stage (Basicevic, Popovic & Kukolj 2008; Glasmann, Kellerer & Muller 2003; Glasmann, Kellerer & Muller 2001). In some papers VoIP security is discussed from its signaling protocol’s perspective. In the literature, SIP security has drawn more attention than H.323 security. This is due to the adoption of SIP for IP Multimedia Subsystem (IMS) 32 in 3G (3GPP) and Next Generation Networks (NGNs)33 (Geneiatakis et al. 2006). 32 IP multimedia subsystem (IMS) is an architecture which is designed to provide IP multimedia communication services. Telecommunication service providers employ IMS to deliver interactive multimedia service to their customers. IMS encompasses circuit-switched communication networks and packet-switched networks and uses VoIP technology and SIP standard (Porter et al. 2006b, p. 500 ). In other words, IMS combines telecommunication technologies with wireless and wired networks in order to provide the All-IP environment to deliver multimedia services in 3G and more advanced networks such as 3.5G and 4G. IMS is discussed in detail in (Handa 2009, pp. 1-24; Chen et al. 2008 and Martínez Perea 2008, pp. 501-540). IP multimedia subsystem (IMS) was proposed by Third Generation Partnership Project (3GPP) <http://www.3gpp.org> to provide IP multimedia network for telecom operators. 3GPP is the IMS standardization body. IMS is introduced in 3GPP specifications release 5 (Rel-5) and has been further developed in latter releases (now Rel-11). IMS architecture and main flows are defined in <http://www.3gpp.org/ftp/Specs/html-info/23228.htm> and IMS service requirements are addressed in <http://www.3gpp.org/ftp/Specs/html-info/22228.htm>. 33 The term Next Generation Network (NGN) is generally used to indicate the shift to a more advanced network. These networks have higher broadband speed connections and have migrated from circuit-switched communication networks (PSTN) to packet-switched IP networks, and provide integrated services on a single network (Sarrocco & Ypsilanti 2007). NGN in addition to providing the existing fixed and mobile telephony services provides multimedia (IPTV, etc.) and content delivery (audio/video streaming, etc… ) services, and extends IMS to support additional technologies (Baroncelli et al. 2010). NGN is discussed in Richardson (2007), pp. 207-224, Mohapatra (2009) and Sarrocco and Ypsilanti (2007). A detailed definition of NGN is provided by ITU-T. According to ITU-T Recommendation Y.2001 (12/2004) p. 2, NGN is defined as: A packet-based network able to provide telecommunication services and able to make use of multiple broadband, QoS-enabled transport technologies and in which service-related functions are independent from underlying transport related technologies. It enables unfettered access for users to networks and to competing service providers and/or services of their choice. It supports generalized mobility which will allow consistent and ubiquitous provision of services to users. International Telecommunication Union - Telecommunication Standardization Sector (ITU-T) <http://www.itu.int/net/ITUT/info/Default.aspx> have produced two fundamental recommendations about NGN, ITU-T Recommendation Y.2001 (12/2004)- General overview of NGN <http://www.itu.int/rec/T-REC-Y.2001/e> and ITU-T Recommendation Y.2011- General principles and general reference model for next generation networks <http://www.itu.int/rec/T-REC-Y.2011/e>. 32 Chapter 2- Literature Review | Some studies focus on a specific security issue of SIP/H.323 signaling protocols, while some studies survey general security vulnerabilities of these protocols. For example, Al-Allouni et al. (2009) propose two flooding attack metrics, Attack Time and Attack Rate in order to evaluate SIP flooding attack. Ge et al. (2009) concentrate on timing attack which aims to reveal the calling history of SIP-based VoIP systems. In contrast, Geneiatakis et al. (2006) provide a comprehensive survey on SIP’s security and analyze possible threats and attacks. Similarly, Geneiatakis and Lambrinoudakis (2007) and Geneiatakis et al. (2005) discuss SIP security vulnerabilities in much detail in order to evaluate security and deploy intrusion detection systems. 2-5-2-4 Man-In-The-Middle (MITM) and Denial of Service (DoS) Man-In-The-Middle (MITM) and Denial of Service (DoS) are two traditional attack types which can be applied to either the VoIP or underlying IP network. MITM34, which is also known as session hijacking attacks or bucket-brigade attack, is a type of attack that requires attackers to have access to network traffic. By sniffing and eavesdropping on the packets that come across a network, attackers gain access to a legitimate connection between two parties. According to Rufi (2007, p. 779), a MITM attack might lead to ‘…theft of information, hijacking of an ongoing session to gain access to private network resources, traffic analysis to derive information about a network and its users, Denial-of-Service (DoS), corruption of sent data, and introduction of new information into network sessions.’ The effects of such MITM attacks might be more serious than DoS to VoIP users since they would in all likelihood not notice the attack. It is generally the case that these attacks’ main 34 The origin of the term “Man in the middle” is derived from the ball game where two players try to pass a ball to each other while one player between them attempts to catch it (http://searchsecurity.techtarget.com/sDefinition/0,,sid14_gci499492,00.html). 33 Chapter 2- Literature Review | ramification is a major risk to data integrity, such as identity theft and call redirection (Arul, Shanmugam 2009). Wang et al. (2008) demonstrate that the US leading VoIP providers (Vonage, AT&T and Gizmo) are vulnerable to MITM attack. In their scenario when a user dials a number the VoIP call is diverted to the bogus interactive voice response or bogus representative. Since the user has dialed the correct number, s/he is confident that the interactive voice response or representative is genuine. Therefore, s/he might be deceived and emit sensitive information such as a credit card number. In a similar vein, Zhang et al. (2009a) and Zhang et al. (2009b) discuss MITM attacks on VoIP networks. DoS attack refers to attacks which attempt to make a computer resource unavailable to its intended users. Sisalem, Kuthan and Ehlert (2006) state that SIP-based VoIP is vulnerable to DoS attacks which aim to put a huge load on memory and CPU of VoIP servers. Al-Allouni et al. (2009) classify VoIP potential DoS attacks into three general classes: Message Flows Attacks, Flooding Attacks and Malformed Message Attacks. These divisions have been further subclassified. 2-5-2-5 Spam over Internet Telephony Spam refers to unsolicited bulk messages that are sent through computer networks. A widely known type of spam is e-mail spam and often the term ‘spam’ has only referred to e-mail spam. However, spam can be applied to any medium which is being abused by unwanted messages such as mobile phone messaging spam. Spam over Internet Telephony (SPIT) is an emerging kind of spam (Mu et al. 2010; Gritzalis & Mallios 2008; Quittek et al. 2008) that constitutes a potential threat to VoIP. It is more severe than email spam due to its attack nature, and consequently VoIP systems require a real-time defense mechanism. 34 Chapter 2- Literature Review | Different methods have been proposed for detecting and preventing SPIT. Quittek et al. (2007) propose a SPIT prevention system which distinguishes human callers from automatic SPIT generators based on checking typical human communication patterns. Similarly, Huang, Yu and Feng’s (2009) SPIT prevention system works based on voice activity analysis. Yu-Sung et al.’s (2009) model detects spam in VoIP calls by employing clustering, a data mining technique. Based on the call parameters, calls with similar features are placed in a cluster for SPIT or legitimate calls. Call features are derived from the signaling and media protocols. For more accurate clustering, this approach may use users’ feedback to mark calls as non-SPIT or SPIT. 2-5-2-6 Biometric encryption Employing biometric encryption for securing VoIP is an area which has not been widely explored. In the IT security context, biometric refers to the measurement of physiological and behavioral characteristics for authentication purposes. Fingerprints and voice are instances of physiological measurements. Arul and Shanmugam (2009) propose a cryptographic system for securing VoIP which generates the private key from fingerprints. This key is used in the process of encrypting and decrypting VoIP traffic. Kopsidas, Zisiadis and Tassiulas (2006) propose a protocol based on biometrics to provide a secure end-to-end VoIP communication. The Voice Interactive Personalized Security (VoIPSEC) protocol employs a two-level verification scheme where in the first level voice and in the second level video biometry data are used. Similarly, Zisiadis, Kopsidas and Tassiulas (2007a) and Zisiadis, Kopsidas and Tassiulas (2007b) discuss VoIPSEC and the usage of biometry data. 2-5-3 Myths about VoIP security Myths surrounding VoIP have been discussed in Cherry (2005) and Sundquist and Service (2006). In both studies the myth about VoIP security has been described alongside other myths. 35 Chapter 2- Literature Review | However, Patrick (2009, pp. 14-15) merely addresses the myths about VoIP security and cast light on them. These myths are summarized in Table 2-2. Myth Reality 1- Traditional phone systems (PSTN) are more secure than VoIP systems The biggest concern in relation to this myth is wiretapping. It has to be noted that wiretapping PSTN is much easier than wiretapping VoIP. This is because an eavesdropper can wiretap PSTN by physically accessing telephone lines which are not well secured (like outside buildings). However, an eavesdropper, to be able to sniff voice packets has to locate his sniffing tool on the same broadcasting domain as the VoIP devices. This is very hard for external hackers to do due to the fact that VoIP devices are located in places which are either well secured (network equipment’s in IT centers) or at least have some level of security (IP phones/cables at offices or residences. 2- To protect network and VoIP end users against threats, strict encryption and authentication is sufficient It is obvious that encryption and authentication is crucial for securing networks; however, some advanced attackers get through by impersonating, and then bypassing the authentication and encryption process. 3- Securing underlying IP networks can secure VoIP networks as well From the network layer perspective, securing the IP network will partially protect VoIP data. However, from the application layer perspective this does not apply. This is because security devices like firewalls generally are not able to detect VoIP specific application layer attacks, such as malformed H.323 or SIP messages which target the servers. Security devices should be VoIP aware and this can be achieved by employing VoIP security devices/modules. To retain a secure VoIP system, both IP network and VoIPspecific security issues must be addressed. Table 2-2 The three myths about VoIP security 36 Chapter 2- Literature Review | 2-5-4 VoIP Threat Taxonomy Vulnerabilities and threats to VoIP systems have been discussed and classified in various studies (Kuhn, Walsh & Fries 2005; Frost 2006; Porter 2006, pp. 3-25; Stanton 2006; Butcher, Xiangyang & Jinhua 2007; Dantu et al. 2009; Patrick 2009, pp. 19-44). However, the VOIPSA’s ‘VoIP Security and Privacy Threat Taxonomy’ document provides the most comprehensive classification of security and privacy threats which VoIP’s systems may face. These threats are categorized as: Misrepresentation Theft of Services Unwanted Contact Eavesdropping Interception and Modification Service Abuse Intentional Interruption of Service Other Interruptions of Service. Each threat is further sub-classified. The VOIPSA threat taxonomy is summarized in Table 2-3, Table 2-4, Table 2-5 and Table 2-6. VOIPSA’s VoIP Security and Privacy Threat Taxonomy Threat class Threat sub-classes Misrepresentation of Identity Misrepresentation of Authority Misrepresentation Misrepresentation of Rights Misrepresentation of Content Examples false caller ID name or number false voice, name, or organization in a voice/video mail false email false presence information presentation of a password, key or certificate of another circumvention of conditional access false claim of government authority bypassing ordinary authentication presentation of a password, key or certificate to gain rights not granted circumvention of conditional access to gain rights not granted modification of access control lists false impersonation of the voice of a caller false impersonation of the words of a caller misleading printed words, still images or moving images in video modifications of spoken, written or visual content Table 2-3 VOIPSA’s VoIP Security and Privacy Threat Taxonomy – Misrepresentation threat 37 Chapter 2- Literature Review | VOIPSA’s VoIP Security and Privacy Threat Taxonomy Threat class Threat sub-classes Unauthorized deletion or altering of billing records Unauthorized bypass of lawful billing systems Theft of Services Unauthorized billing Taking of service provider property Harassment Extortion Unwanted Contact Unwanted Lawful Content Call Pattern Tracking Traffic Capture Number Harvesting Conversation Reconstruction Eavesdropping Voicemail Reconstruction Fax Reconstruction Video Reconstruction Text Reconstruction Call Black Holing Call Rerouting Fax Alteration Conversation Alteration Interception and Modification Conversation Degrading Conversation Impersonation and Hijacking False Caller Identification Call Conference Abuse Premium Rate Service (PRS) Fraud Service Abuse Improper Bypass or Adjustment to Billing Other Improper Access To Services Table 2- 4 VOIPSA’s VoIP Security and Privacy Threat Taxonomy – various threats The Interruption of Service threat is categorized as Denial of Service and Physical Intrusion. The Denial of Service is sub-classified into 4 categories: VoIP Specific Denial of Service, Network Services DoS, Underlying Operating System/Firmware DoS and Distributed Denial of Service. The VoIP Specific Denial of Service is further sub-classified as shown in Table 2-5. 38 Chapter 2- Literature Review | VOIPSA’s VoIP Security and Privacy Threat Taxonomy Threat class Threat sub-classes Threat sub-classes Threat sub-classes Request Flooding Interruption of Service VoIP Specific Denial of Service Denial of Service Malformed Requests and Messages Examples User Call Flooding User Call Flooding Overflowing to Other Devices Endpoint Request Flooding Endpoint Request Flooding after Call Setup Call Controller Flooding Request Looping Directory Service Flooding Disabling Endpoints with Invalid Requests Injecting Invalid Media into Call Processor Malformed Protocol Messages QoS Abuse Spoofed Messages Call Hijacking Faked Call Teardown Message Faked Response Registration Hijacking Media Session Hijacking Server Masquerading Network Services DoS Underlying Operating System/Firmware DoS Distributed Denial of Service Physical Intrusion Table 2-5 VOIPSA’s VoIP Security and Privacy Threat Taxonomy – Interruption of Service threat Physical intrusion threat includes unauthorized physical access to systems/equipment, cables/wires and networking equipment. Social engineering attacks may occur because of physical intrusion vulnerability. VOIPSA’s VoIP Security and Privacy Threat Taxonomy Threat class Threat sub-classes Loss of Power Resource Exhaustion Performance Latency Table 2- 6 VOIPSA’s VoIP Security and Privacy Threat Taxonomy – Other Interruption of Service Threat Other Interruptions of Service 39 Chapter 2- Literature Review | Chapter 3- Methodology This chapter describes the methodology of this thesis and it is organized as follows: Section 3.1 provides an overview of this chapter Section 3.2 introduces the research approach and discusses the concept of research epistemologies, qualitative and quantitative research and research reasoning process. Section 3.3 describes the sampling method used in this research Section 3.4 describes the approach of data analysis in this research Section 3.5 describes the research ethics Section 3.6 describes the on-line questionnaire design Section 3.7 summarizes this chapter and introduces Chapter 4 40 Chapter 3- Methodology | 3-1 Overview This chapter aims to establish the research methodology used in this thesis in order to answer the research question. This study seeks to evaluate the users’ awareness of VoIP security vulnerabilities, and their attitude towards privacy and security in VoIP communications. An on-line questionnaire was designed to collect information in order to investigate these matters. The overall research process is summarized in Figure 3-1. Literature study Finding a gap in the literature Employing suitable research methodology Designing a questionnaire Collecting data Analyzing data Result interpretation Disseminating research outcome Figure 3-1 Overall research process 41 Chapter 3- Methodology | 3-2 Approach This thesis is a positivist quantitative research which intends to evaluate users’ perspectives on VoIP’s security vulnerabilities. The research reasoning process is inductive and is depicted in Figure 3-3. For quantitative data collection purpose, an anonymous on-line questionnaire was designed. 3-2-1 Research epistemologies Chua (1986) classifies research epistemologies into positivist, interpretive and critical. These three categories are the philosophical perspective of the underlying research epistemology. Epistemology refers to the perspectives on knowledge and the ways in which it can be obtained (Hirschheim 1985; Myers 1997b). Hirschheim (1985) describes epistemology in detail by first defining what knowledge is and then, addressing how valid knowledge can be acquired. The essence of research epistemologies is to define different approaches for obtaining knowledge which is valid. Validity is the most important feature of the obtained knowledge. It should be noted that research epistemologies do not always contain ‘hard and fast’ differences; their differences can be blurred. It is a matter of debate whether these research epistemologies can be accommodated within a single research strategy. Kaplan and Duchon (1988) believe that there is no need to clearly distinguish between positivist and interpretive studies. Instead, there is a middle road and ‘no one approach to information systems research can provide the richness that information systems, as a discipline, needs for further advancement’. This thesis is a positivist study which is explained in Section 3-2-1-1 along with justifications for employing this research epistemology. In Sections 3-2-1-2 and 3-2-1-3 interpretive and critical studies are respectively discussed. 42 Chapter 3- Methodology | 3-2-1-1 Positivist studies The positivist approach has been defined by many scholars over the recent past decades. Hirschheim (1985), for example, provides a historical perspective on positivist science. He begins his account from the 17th century to the present day and his description of positivism as consists of the following five stages: 1. Arrival of positivism 2. Anti-positivism 3. Re-entering of positivism (logical positivism) 4. Contemporary critics 5. Post-positivism. Orlikowski and Baroudi (1991, p. 5) define positivist studies as: Positivist studies are premised on the existence of a priori fixed relationships within phenomena which are typically investigated with structured instrumentation. Such studies serve primarily to test theory, in an attempt to increase predictive understanding of phenomena. Shanks (2002) believes that the positivist paradigm is comprised of theories, propositions, hypotheses and hypothesis testing. In his study, he discusses these issues in detail and provides guidelines for conducting positivist case study research. Varey et al. (2002, p. 232) describe the main characteristics of positivist researches as ‘… formal propositions, quantifiable measures of variables, hypothesis testing and the drawing of inferences about a phenomenon from a sample to defined population…’ Similarly, Myers (1997b) states that: Positivists generally assume that reality is objectively given and can be described by measurable properties which are independent of the observer (researcher) and his or her instruments. Positivist studies generally attempt to test theory, in an attempt to increase the predictive understanding of phenomena. 43 Chapter 3- Methodology | Objectivity is an important factor in positivist studies; therefore, conclusions or theories in such studies are based on measurable properties that are consistent with this study. The aim of this thesis is to explore users’ perspectives on VoIP’s security vulnerabilities and also study their awareness and attitudes towards these issues. This is done by analyzing and interpreting the results of the designed questionnaire. This approach is by nature a positivist study since hypotheses are tested based on quantifiable measures and the conclusions are generalized. 3-2-1-2 Interpretation studies Myers (1997b) defines interpretation as: Interpretive researchers start out with the assumption that access to reality (given or socially constructed) is only through social constructions such as language, consciousness and shared meanings. Myers (1997b) also argues that ‘Interpretive studies generally attempt to understand phenomena through the meanings that people assign to them…’ In a similar vein Orlikowski & Baroudi (1991, p. 5) describe interpretive studies as: Interpretive studies assume that people create and associate their own subjective and intersubjective meanings as they interact with the world around them. Interpretive researchers thus attempt to understand phenomena through accessing the meanings that participants assign to them. The main characteristics of interpretive studies are described in Bailey’s (2007, p. 53) book where social reality is ‘…a dynamic entity, historically situated in time and space, context specific and shaped by the researcher’s views of the world…’. 44 Chapter 3- Methodology | In contrast to positivist studies, objectivity and generalization are not considered in interpretive studies. Instead, a deeper understanding of the phenomena in natural settings from the participants’ perspective is sought. Principles for conducting and evaluating interpretive studies in information systems are discussed in Klein and Myers’ (1999) analysis. 3-2-1-3 Critical studies Cecez-Kecmanovic (2001, p. 142) defines critical studies as ‘… a process of inquiry that seeks to achieve emancipatory social change by going beyond the apparent to reveal hidden agendas, concealed inequalities and tacit manipulation…’. Myers (1997b) states that ‘critical research focuses on the oppositions, conflicts and contradictions in contemporary society, and seeks to be emancipatory…’ In their work, Orlikowski and Baroudi (1991, p. 6) describe critical studies as aiming: … to critique the status quo, through the exposure of what are believed to be deep-seated, structural contradictions within social systems, and thereby to transform these alienating and restrictive social conditions. The term ‘critical’ is an umbrella term under which related but different approaches in the social science fall. The ‘critical theory’ is the common denominator in these approaches and for this reason critical research epistemology has its roots in critical theory35 (Howcroft & Trauth 2004, p. 196; Cecez-Kecmanovic 2001, p. 142). Researchers in critical studies are seen as social critiques who challenge the ideologies, beliefs and assumptions of the status quo. Both interpretive and critical approaches evolved as a reaction to positivism (Cecez-Kecmanovic 2001, p. 142). While interpretive studies aim is to understand societal influences, critical studies try to question them (Howcroft & Trauth 2004, p. 201). 35 The critical theory is discussed in Hammersley’s (1995) book, ‘The politics of social research’. 45 Chapter 3- Methodology | 3-2-2 Qualitative or quantitative research In this section, both qualitative and quantitative methodologies are described and the fundamental differences between them are discussed. It is argued that the quantitative research methodology suits this thesis best. 3-2-1-1 Qualitative research There have been many academic discussions and debates about qualitative research. Some provide in-depth descriptions of qualitative research while others simply describe it at an introductory level. A detailed description of qualitative research is provided by (Strauss & Corbin 1998, pp. 11-12) as ‘… [qualitative research] can refer to research about persons’ lives, lived experiences, behaviors, emotions, and feelings as well as about organizational functioning, social movements, cultural phenomena, and interactions between nations’. They also state that qualitative research has three major components as: First, there are the data, which can come from various sources such as interviews, observations, documents, records, and films. Second, there are the procedures that researchers can use to interpret and organize the data. … Written and verbal reports make up the third component. These may be presented as articles in scientific journals, in talks (e.g., conferences), or in books. Similarly, Denzin and Lincoln (2000, pp. 3-4) define qualitative research as: Qualitative research is a situated activity that locates the observer in the world. It consists of a set of interpretive material practices that make the world visible. …qualitative research involves an interpretive, naturalistic approach to the world. This means that qualitative researchers study things in their natural settings, attempting to make sense of or interpret phenomena in terms of the meanings people bring to them. Qualitative research involves the studied use and collection of a variety of empirical materials - case 46 Chapter 3- Methodology | study, personal experience, introspective, life story, interview, observational, historical, interactional, and visual texts - that describe routine and problematic moments and meaning in individuals’ lives. Myers (1997a, p. 241) simply expresses qualitative research as methods which help researchers to ‘…understand and explain social phenomena’. More recently, Myers (2009) provides examples of both qualitative methods (‘…action research, case study research and ethnography’) and qualitative data sources (‘…observation and participant observation (fieldwork), interviews and questionnaires, documents and texts, and the researcher's impressions and reactions’). Qualitative research is concerned with ‘images, feelings, impressions and qualities’ (Bouma 2000, p. 19) and provides viewpoints that takes into account culture, personality and other nuances related to humans and society (Babbie 2001, p. 37). Findings of qualitative research are not based on statistical procedures rather they are based on the interpretation of the researcher. 3-2-1-2 Quantitative research According to Johnson and Onwuegbuzie (2004), ‘…the major characteristics of traditional quantitative research are a focus on deduction, confirmation, theory/hypothesis testing, explanation, prediction, standardized data collection, and statistical analysis’. They also cite that: … quantitative purists believe that …the observer is separate from the entities that are subject to observation …[and] social science inquiry should be objective … and real causes of social scientific outcomes can be determined reliably and validly... [quantitative] researchers should eliminate their biases, remain emotionally detached and uninvolved with the objects of study, and test or empirically justify their stated hypotheses. Myers (1997b) believes that ‘quantitative research methods were originally developed in the natural sciences to study natural phenomena. Examples of quantitative methods now well 47 Chapter 3- Methodology | accepted in the social sciences, include survey methods, laboratory experiments, formal methods (e.g. econometrics) and numerical methods such as mathematical modeling’; and Babbie (2001, p. 37) simply remarks that quantitative research is ‘… where things are quantifiable, measurable, explained and finite’. The emphasis in quantitative research is on objective reality which is transformed into testable hypotheses. Data are collected through experimentations and testing, and results are based on statistical or other numerical analyses. The major data type is numeric data which is analyzed employing statistical techniques. Reliability and validity of quantitative researches are discussed in Bryman (2004, pp. 70-74). The intention of this thesis is to explore users’ perspectives on VoIP’s security vulnerabilities and investigate their awareness and attitudes towards them. This is achieved by employing a survey method which is a traditional approach in quantitative studies. Accordingly, a questionnaire is designed and the findings are based on quantifiable measures which are then analyzed and reported as numbers, charts and percentages. As a consequence of the discussion and definitions of qualitative and quantitative research, it is concluded that quantitative research is the most suitable method for this study. 3-2-1-3 Triangulation Although most researchers employ either qualitative or quantitative research methods, some tend to combine them in one study. The combination of research methods in one study is called triangulation (Myers 1997b) or mixed methodology. Denzin (1978, p. 291) defines triangulation as ‘the combination of methodologies in the study of the same phenomenon’. An in-depth and detailed discussion of triangulation can be found in Jick (1979). The notion of combining qualitative and quantitative research methods is not new and in fact it has a long tradition (19th century France) in sociological research (Erzberger & Prein 1997). Triangulation has been a matter of debate over the years and has been the subject of much discussion by scholars. For instance, Lee (1991) provides an integrated framework for the 48 Chapter 3- Methodology | interpretive and positivist approaches, and Gable (1994) discusses the benefits of integrating case study (qualitative) and survey (quantitative) research methods. In this study, case study is the main research method and the emphasis is on how it can be enriched by survey research. Similarly, Ragin (1987) in his book, The Comparative Method, and Kaplan and Duchon (1988) in their paper, provide useful discussions of triangulation. Mingers (2001) is a scholar who believes that ‘…research results will be richer and more reliable if different research methods, preferably from different (existing) paradigms, are routinely combined together’. Mathison (1988) also believes that triangulation is ‘…a strategy for increasing the validity of evaluation and research findings’. Nevertheless, some researchers criticize triangulation. For example, (Blaikie 1991) argues that ‘… the use of triangulation has been plagued with a lack of awareness of the different and incommensurate ontological and epistemological assumptions associated with various theories and methods’. Denzin (1978, pp. 294-307) provides an in-depth discussion of triangulation by outlining four types of triangulation: (1) data triangulation; (2) investigator triangulation; (3) theory triangulation; and (4) methodological triangulation. Mathison (1988) argues that only 3 types of triangulation are practical and the theory triangulation ‘…is problematic at best, and likely impossible in reality’. He refers to Denzin’s note at the end of the chapter and writes that even Denzin is uncertain about the plausibility of the theory triangulation. There is no unique and best research approach. Although triangulation (mixed methodology) is not necessarily the most suitable method, it might be an appropriate one. Triangulation has a number of advantages. In a triangulated research design the deficiency of a method can be overcome by using the advantages of another method. For instance, quantitative data collection approaches can be employed to test hypotheses which are generated by qualitative methods. Actual studies of the use of triangulation can be found in Markus (1983) and Amaratunga and Baldry (2001). The strengths and weaknesses of triangulation are summarized in Johnson and (Onwuegbuzie 2004, p. 21). 49 Chapter 3- Methodology | 3-2-1-4 Compare and contrast: quantitative versus qualitative research From an epistemological perspective, qualitative and quantitative research lie respectively within the domain of interpretivist (naturalist) and positivist (empiricist) epistemologies. Lincoln and Guba (1985, p. 37) list the different axioms between qualitative (naturalist) and quantitative (positivist) research (Table 3-1). The nature of reality The relationship of knower to the known The possibility of generalization Quantitative (positivist) Qualitative (naturalist) Reality is single, tangible and fragmentable. Realities are multiple, constructed and holistic. Knower and known are independent, a dualism. Knower and known are interactive and inseparable. Time and context free generalizations (nomothetic statements) are possible. Only time and context bound working hypotheses (idiographic statements) are possible. There are real causes, linkages Temporally precedent to or simultaneous with their effects. All entities are in a state of mutual simultaneous shaping, so that it is impossible to distinguish causes from effects. The role of values Inquiry is value-free. Inquiry is value-bound. The possibility of causal Table 3-1 The Different axioms between qualitative (naturalist) and quantitative (positivist) research Modified from Lincoln and Guba (1985, p. 37) Qualitative research constructs social reality (cultural meaning) with a focus on interactive processes and events and utilizes thematic analysis while researchers are involved with the studied phenomenon. In contrast, quantitative research measures objective facts with a focus on variables and employs statistical analysis while researchers are detached from the studied phenomenon (Neuman 2003, p. 16). Qualitative research is often associated with social sciences and is the “what’s it like?” study method which emphasizes ‘…the qualities of entities and on processes and meanings that are 50 Chapter 3- Methodology | not experimentally examined or measured (if measured at all) in terms of quantity, amount, intensity, or frequency… [and] …seek answers to questions that stress how social experience is created and given meaning’ (Denzin & Lincoln 2000, p. 10). In contrast, quantitative research is associated with the sciences which lend themselves well to quantification, such as mathematics, physics and chemistry. Here the emphasis is on ‘…the measurement and analysis of causal relationships between variables, not processes’ (Denzin & Lincoln 2000, p. 10). Glesen and Peshkin (1992) compare and contrast qualitative and quantitative research. Their summary of the differences is shown in Table 3-2. Quantitative Research (Positivist Research) Assumptions Purpose Qualitative Research (Interpretivist Research) -Social facts have an objective reality -Reality is socially constructed -Primacy of method -Primacy of subject matter -Variables can be identified and relationships measured -Variables are complex, interwoven, and difficult to measure -Etic (outside's point of view) -Emic (insider's point of view) -Generalizability -Contextualization -Prediction Causal explanations -Interpretation -Understanding actors' perspectives Approach Researcher role -Begins with hypotheses and theories -Ends with hypotheses and grounded theory -Manipulation and control -Emergence and portrayal -Uses formal instruments -Researcher as instrument -Experimentation -Naturalistic -Deductive -Inductive -Component analysis -Searches for patterns -Seeks consensus, the norm -Seeks pluralism, complexity -Reduces data to numerical indices -Makes minor use of numerical indices -Abstract language in write-up -Descriptive write-up -Detachment and impartiality -Personal involvement and partiality -Objective portrayal -Empathic understanding Table 3-2 Qualitative and quantitative research compared and contrasted (adapted from Glesen and Peshkin (1992) 51 Chapter 3- Methodology | 3-2-3 Research reasoning process In this section deductive and inductive research reasoning processes are described along with justifications for employing inductive reasoning in this research. Goel and Dolan (2004) define reasoning as: … the cognitive process of drawing inferences from given information. All arguments involve the claim that one or more propositions (the premises) provide some grounds for accepting another proposition (the conclusion). The research reasoning process can be categorized as deductive and inductive reasoning. 3-2-3-1 Deductive reasoning Goel and Dolan (2004) believe that deductive reasoning evaluates the validity of deductive arguments. They describe the validity as ‘… a function of the relationship between premises and conclusion and involves the claim that the premises provide absolute grounds for accepting the conclusion’ and provide the following example as a deductive argument which can be validated: All men are mortal; Socrates is a man; Socrates is mortal 3-2-3-2 Inductive reasoning In deductive reasoning validity is evaluated but in inductive reasoning arguments are never valid. However, the plausibility or reasonableness of inductive arguments can be evaluated. Below is an example of an inductive argument (Goel & Dolan 2004): Socrates is a man; Socrates is mortal; all men are mortal 52 Chapter 3- Methodology | Klauer (1996) describes inductive reasoning as ‘…the process whereby regularities or order are detected and, inversely, whereby apparent regularities, seeming generalizations, are disproved or falsified’. He points out that inductive reasoning can be considered as a process of detecting commonalities by stating similarities and differences. However, he emphasizes that ‘…it is not enough to compare whole objects globally to each other. Instead, they have to be compared with respect to their attributes or to the relations held in common.’ 3-2-3-3 Compare and contrast: deductive versus inductive reasoning Trochim (2006) provides a simple and easy-to-understand definition of both deductive (topdown approach) and inductive (bottom-up approach) reasoning. These are depicted in Figures 3-2 and 3-3. Theory Observation Hypothesis Pattern Observation Tentative hypothesis Comfirmation Theory Figure 3- 2 Deductive research reasoning process Figure 3- 3 Inductive research reasoning process As shown in Figure 3-2, the deductive reasoning process moves from the more general to the more specific while inductive reasoning works the other way around. Deductive reasoning begins from a theory and narrows down to a specific hypothesis which is testable by observations. In contrast to this, inductive reasoning begins with specific observations in order to detect patterns to be able to propose some tentative hypotheses. Deductive reasoning processes end with the confirmation or rejection of a theory which is 53 Chapter 3- Methodology | based on the collected data in the observation stage, while inductive reasoning processes end with a development of a theory (Trochim 2006). It should be noted that the inductive reasoning approach is useful for theory building while deductive reasoning is useful for theory testing. As this study intends to develop theories concerning users’ perspectives on VoIP’s security vulnerabilities, inductive reasoning seems to be the appropriate choice. Furthermore, since in this research the theories were developed based on the detected patterns which were explored by 1) designing a questionnaire 2) collecting data 3) analyzing data and 4) result interpretation, it was concluded that inductive reasoning is the best research method of reasoning for this study. 3-3 Sampling In quantitative research the emphasis is on generalization and the aim is to apply the findings (relationships amongst quantifiable measured parameters) to the general population. When the interested population36 is small it is easy to survey the entire population. For example, For example, if the population consists of the Heads of School at the University of South Australia, we then have to survey only about 20 people in order to survey the complete population. However, when the population is large (i.e. international students in Australia or Australian aged 25-55, etc.) in most cases it is not practical or due to time and budget constraints it is not feasible to survey each and every one of the individuals in the interested population. Therefore, a sample representative of the population is surveyed which is much faster, cheaper and easier. Statistical extrapolations can be made from the selected sample to the interested population. Sampling is a statistical technique that refers to the sample selection approaches. Sampling is discussed in detail in (Yates 1960, pp. 1-47; Sudman 1976). 36 In terms of sampling, population refers to all the individuals who fall into the category of interest (Hall 1996, p. 107). 54 Chapter 3- Methodology | 3-4-1 General universe, population and sample In the context of sampling there are 3 overlapping different types of group of individuals: (1) general universe; (2) population (working universe); and (3) sample (Rose 1982, pp. 56-59). This concept is depicted in Figure 3-4. General universe Population Sample Figure 3- 4 Sampling overlapping entities Table 3-3 defines these entities (group of individuals) in the context of this study. Entities Definition General universe All the people who use VoIP as a mean of communication Population (working universe) Students enrolled in the School of Computer and Information Science at the, University of South Australia Sample The respondents to the questionnaire Table 3- 3 Definition of group of individuals in this thesis 55 Chapter 3- Methodology | 3-4-2 Sampling types Different sampling techniques have been discussed in numerous studies (Nardi 2006, pp. 107126; Hall 1996, pp. 106-116; De Vaus 1995, pp. 60-79; Henry 1990, pp. 17-32; Weisberg 1977, pp. 17-26; Warwick 1975, pp. 69-77). The provided classification of sampling in these studies slightly varies. There is, however, a consensus that sampling is broadly categorized as probability sampling (or ‘unbiased sampling’ or ‘random sampling’) and non-probability sampling (or ‘biased sampling’ or ‘nonrandom sampling’). According to Henry (1990, p. 17): Probability samples are selected in such a way that every member of the population actually has a possibility [nonzero probability with the same chance] of being included in the sample. Nonprobability samples are selected based on the judgment of the researchers [not by chance or known probabilities of selection] to achieve particular objectives of the research at hand. Figure 3-5 depics Nardi’s (2006, pp. 107-126) classifications of sampling. 56 Chapter 3- Methodology | Simple Random Sampling Probability Sampling Stratified Random Sampling Systematic Random Sampling Cluster or Multistage Sampling Sampling Convenience or accidental Sampling Non-Probability Sampling Purposive or Judgmental Sampling Quota Sampling Snowball Sampling Figure 3- 5 Classification of sampling 3-4-3 The used sampling type In evaluating users’ awareness of VoIP security vulnerabilities, and their attitudes towards privacy and security in VoIP communications, this thesis uses an on-line questionnaire that was designed to collect information in order to investigate these matters. The goal was to survey the entire population; therefore, the ‘Recruitment email’ (refer to Appendix B) was sent to all students enrolled at the School of Computer and Information Science (CIS), University of South Australia. 57 Chapter 3- Methodology | Surveying the entire population implies that each and every student has to be surveyed and obviously this was not the case in this research. There were 300 students in CIS but only 107 responded to the on-line questionnaire and this means that only 35.6% of the population participated – just over a third of the student cohort. Purposive sampling was employed in this study. In order to describe how this sampling method was improved, Simple Random Sampling (SRM) is defined and then purposive sampling is addressed. 3-4-3-1 Simple Random Sampling Simple Random Sampling (SRS) falls under the probability sampling category which implies each student had an equal chance (probability) of being selected. As mentioned earlier, an email which advertized the on-line questionnaire (the recruitment email, refer to Appendix B) was sent to all the students of CIS; consequently, each student had nonzero probability with the same chance of being selected. According to Sudman (1976, pp. 49-50), SRS has two main characteristics: ‘…(1) the probabilities of selection are equal for all elements, and (2) sampling is done in one stage with elements of the sample selected independently of one another …’. The sampling method used in this research was done in one stage and students were selected independently of each other; therefore, both features of SRM were addressed. Henry (1990, p. 27) in regard to SRS states that: All members of the study population are either physically present or listed, and the members are selected at random until a previously specified number of members or units has been selected. … [it is assumed 58 Chapter 3- Methodology | that the selection is] without replacement37. This means that once a unit is selected in the sampling process, it is removed from the pool eligible for future selection. In a true SRS each unit or member of the population should be clearly and unambiguously identified (Warwick 1975, p. 77) and listed. The complete list of all possible elements in the population that are uniquely recognizable is called a sample frame. From the sample frame the samples are chosen by applying a random selection process. For example, a common random selection process 38 is using a table of random numbers. It should be pointed out that the above-mentioned procedure could not be used in this research. This is due to the fact that the complete list of CIS students was not available to the author. 3-4-3-2 Purposive sampling According to Guarte and Barrios (2006) ‘Purposive sampling is described as a random selection of sampling units within the segment of the population with the most information on the characteristic of interest’. However, in other studies purposive sampling is part of the nonprobability sampling category (Warwick 1975; Weisberg 1977), which is considered to be an example of biased sampling and non-random sampling. The studied population (working universe) in this research consists of the students in the School of Computer and Information Science (CIS) at the University of South Australia. The reason for 37 In simple random sampling there is a theoretical issue on whether once an unit is selected it should be removed from the pool or it should be remained for possible reselection in the sampling process. These approches are called sampling without replacement and sampling with replacement, respectively. In practice sampling without replacement is more prevalent. 38 In a random selection process or a random technique the goal is to apply the random (chance) process to the rage of numbers corresponding to the list (Warwick 1975, p. 77). In this way samples are chosen randomly. In Sudman (1976, p. 50) there is a detailed discussion on the randomness of chance (random) selection processes. And in (Nardi 2006, p. 114) and (De Vaus 1995, pp. 61-64) there are examples of how to use a table of random numbers. 59 Chapter 3- Methodology | this selection is that it is assumed that the students at CIS are generally familiar with VoIP and network security concepts. To avoid introducing bias into the sample selection and increasing the validity of the sampling, we ensured that the two main characteristics of SRS namely, independence between selected elements and sampling at once, were included in the sampling process. As mentioned earlier, an email advertising the on-line questionnaire (the recruitment email, see Appendix B) was sent to all the students of CIS; consequently, each student had nonzero probability with the same chance of being selected. 3-4 Data Analysis (Quantitative Data) 3-4-1 Coding Preliminary step in quantitative data analysis is coding. In addition to coding, classifying the responses enables the data to be better analyzed. The responses to the on-line questionnaire are classified by sequential number orders and then coded. As illustrated in Table 3-4, each respondent has only one code for each variable. The open questions are listed separately and grouped into small categories. For coding and analyzing the collected data, SPSS39 (PASW Statistics 17.0 (release 17.0.2)) and Microsoft Excel 2007 were used. 39 PASW (Predictive Analytics SoftWare) Statistics was the premier vendor for SPSS (Statistical Package for the Social Sciences). After IBM acquired the company, the PASW software became IBM SPSS Statistics. SPSS (http://www.spss.com) is a software that is used to analyze data collected from observations, surveys, etc. This program provides a range of statistical analyses along with graphical presentation of data and currently it is offered in 4 versions, 1-Standard (Fundamental analytical capabilities), 2- Professional (Additional capabilities), 3- Premium (A full range of analytical techniques) and 4- IBM SPSS Statistics for Educators (Faculty Packs and Campus Edition software). 60 Chapter 3- Methodology | Number Variable Name Type of variable Nationality Average monthly talking time Average monthly international call time via phone/mobile Using computer to make calls/voice chat Average monthly use of computer to make calls/voice chat Preferred way to make international calls Preferred service for international calls via land line/mobile Main reason for choosing this service nominal (categorical) nominal (categorical) Preferred software for making calls/voice chat Main reason for choosing this software Concerned features when making international calls Comparison of security between international/long distance calls and domestic calls nominal (categorical) nominal (categorical) Background 1 2 3 4 5 6 7 8 nominal (categorical) nominal (categorical) nominal (categorical) nominal (categorical) nominal (categorical) nominal (categorical) Awareness/attitude towards VoIP security/privacy 1 2 3 4 5 6 7 8 9 10 11 12 Privacy concerns when making calls (regardless of the used service) Traditional telephony security versus VoIP security Concern about VoIP privacy (eavesdropping) Possibility of privacy breaches in VoIP versus traditional telephony Concern about VoIP security Possibility of privacy/security breaches in VoIP Discussing security/privacy issues with service providers The discussed security/privacy issues with service providers nominal (categorical) nominal (categorical) ordinal nominal (categorical) nominal (categorical) nominal (categorical) ordinal Open-ended ordinal Open-ended Table 3- 4 Data Analysis 3-4-2 Relationship between variables According to the SPSS tutorial, the purpose of a cross-tabulation is to show the relationship (or otherwise) between two variables. Cross-tabulation tables or contingency tables demonstrate 61 Chapter 3- Methodology | the relationship between nominal40 or ordinal41 variables. The size of the table is determined by the number of distinct values for each variable, with each cell in the table representing a unique combination of values. A number of statistical tests are available to determine if the relationship between variables is statistically significant. In this study, chi-square test - which is more common and appropriate for almost any kind of data - is used. In a chi-square test the “Asymp. Sig” value (significance value) indicates whether the two variables are related (dependent). The lower the value, the more likely it is that the two variables are related. In this study, we selected a significance level of 0.05, and consequently an “Asymp. Sig” value less than 0.05 implies that the two variables are related. 3-5 Research Ethics Because human subjects were involved, ethics approval was obtained from the Human Research Ethics Committee of the University of South Australia prior to the start of this research. Furthermore, since the participants came from the university’s School of Computer and Information Science, written approval to recruit participants was obtained from the Head of the school. The participant information sheet (refer to Appendix A) explaining the purpose and scope of the study was distributed to potential participants. It informed them of their level of commitment and also gave them confidence to participate in this research. 40 As illustrated in Table 3-4 the questionnaire contains 16 questions that use nominal (categorical) scales. These questions produce categorical (nominal) data that have no numerical value and fit into categories such as country. Four (4 out of 16) of the categorical questions (questions 3, 5, 14 and 18 refer to Appendix C) are dichotomous (data take on one of two values such as yes or no). 41 As illustrated in Table 3-4 the questionnaire contains 2 questions (questions 12 and 16 refer to Appendix C) that use ordinal scales. These questions produce ordinal data that shows order exists among the categories. This indicates that one observation is more important or of greater values than others. These questions are also referred as scales questions. 62 Chapter 3- Methodology | Since submitting the completed on-line questionnaire is an act of consent, seeking consent from participants was not necessary. The questionnaire was anonymous and did not contain any personal questions. Therefore, participants' identity remained confidential. Furthermore, in the participant information sheet, it was stated that completing the questionnaire is optional. 3-6 Questionnaire design The on-line questionnaire is anonymous and Google Docs was used to design it. The answers to the questions are stored at Google’s server in Google Docs spreadsheet format and it is accessible by logging into the corresponding Gmail account. The questionnaire contains closed and open questions. Closed questions are asked when the potential answers are known or a scale is used. Otherwise, open questions are asked. In designing the questionnaire, the following points were considered: Use simple words Avoid vague language Provide easy-to-understand instructions Design an appealing and easy-to-follow layout Use short and easy-to-understand questions Avoid hypothetical questions Use leading and unambiguous questions Avoid asking two questions within a single question Provide enough room to answer questions 63 Chapter 3- Methodology | 3-7 Summary For this thesis quantitative research methodology was employed and in order to evaluate users’ perspective on VoIP’s security vulnerabilities, an anonymous on-line questionnaire, using Google Docs, was designed. Chapter 4 describes the results and findings. 64 Chapter 3- Methodology | Chapter 4- Results This chapter presents the results of this study. It is organized as follows: Section 4.1 provides an overview of this chapter Section 4.2 describes the overview and analysis of the questions concerning the online questionnaire. Section 4.3 65 summarizes this chapter and introduces Chapter 5 Chapter 4- Results | 4-1 Overview This chapter summarizes the results and findings regarding the on-line questionnaire (refer to Appendix C and Chapter 3). The on-line questionnaire was designed to collect information in order to evaluate the users’ awareness of VoIP security vulnerabilities, and their attitudes towards privacy and security in VoIP communications. The ‘Recruitment email’ (refer to Appendix B) was sent to all students at the University of South Australia’s School of Computer and Information Science (CIS), to encourage them to answer the questionnaire. Out of 30042 recruitment email sent, 107 valid responses were received. To analyze the collected data, SPSS (PASW Statistics 17.0 (release 17.0.2)) and Microsoft Excel 2007 were used. 4-2 The survey results The results of the on-line questionnaire are presented in this section, while the discussions of the investigated issues are provided in the next chapter. The results are categorized into two main categories: firstly, background; and secondly, awareness of/attitude to VoIP security/privacy. In the first category, general information such as nationality, average monthly talking time and etc… are investigated. The second category intends to explore the participants’ awareness and attitudes towards VoIP security and privacy. Furthermore, the relationships between the two categories are examined in order to investigate whether any relationship exists between users’ call habits and awareness/ attitude towards VoIP security and privacy. It should be emphasized that in this study privacy is considered as eavesdropping while VoIP security is considered to be other violating actions such as toll fraud. However, the occurrence of privacy breaches indicates that the system is not well secure. In that sense, privacy breaches in the VoIP system are synonymous to security vulnerabilities. 42 This is the approximate (not precise) number of students who received the recruitment email. 66 Chapter 4- Results | 4-2-1 Background 4-2-1-1 Nationality As depicted in Figures 4-1 and 4-2, the majority (60%) of participants in this study (64 out of 107) are Australian, while 40% are from 18 different countries (43 out of 107). Results by Country Others Others 40% Australia Australia 60% Figure 4-1 Overall results by country In second place was Iran with 10 respondents and this country was followed by Afghanistan (8), China (5) and India (4). Either 1 or 2 respondents come from other countries. Figure 4-2 illustrates the number of participants according to country. Number of Participants by country 64 10 1 1 1 2 1 1 2 1 1 1 2 South Korea Malaysia Maldives Russia South Africa Taiwan Trinidad and Tobago United Kingdom Vietnam 4 Iran China Canada Australia Afghanistan 1 Japan 5 Italy 1 India 8 Fiji 70 60 50 40 30 20 10 0 Figure 4-2 Number of Participants by Country The participants’ nationality was asked in order to investigate whether there is any relationship between nationality and awareness and attitude towards security/privacy issues in VoIP. No relationship was found. 67 Chapter 4- Results | 4-2-2-2 Average monthly talking time As shown in Table 4-1, more respondents either spend more than 7 hours (37.4%) or 1 to 4 hours (34.6%) per month talking on the phone/mobile. Average monthly talking time Frequency Percent 1 hour – 4 hours 37 34.6 4 hours – 7 hours 15 14.0 Less than 1 hour 15 14.0 More than 7 hours 40 37.4 Total 107 100.0 Table 4-1 Average monthly talking time The time spent talking was asked in order to investigate whether any relationship exists between talking time and awareness and attitude towards security/privacy issues in VoIP. The relationship between the average monthly talking time and participants’ concern about VoIP security and privacy (eavesdropping) was found to be significant. This is illustrated in Tables 4-2 and 4-3. Chi-Square value of the relationship: Pearson Chi-Square - Asymp. Sig. (2-sided): .005 Concern about VoIP privacy (eavesdropping) Average monthly talking time: 1 hour – 4 hours Count % 4 hours – 7 hours Count % Less than 1 hour Count % More than 7 hours Count % Total Count % No Yes Total 25 10 35 71.4% 28.6% 100.0% 9 6 15 60.0% 40.0% 100.0% 10 4 14 71.4% 28.6% 100.0% 13 26 39 33.3% 66.7% 100.0% 57 46 103 55.3% 44.7% 100.0% Table 4-2 Relationship between talking time and being concern about VoIP privacy (eavesdropping) 68 Chapter 4- Results | Chi-Square value of the relationship: Pearson Chi-Square - Asymp. Sig. (2-sided): .036 Concern about VoIP Security (1=Not concerned, 5=Very concerned) Average monthly talking time: 1 hour – 4 hours Count % 4 hours – 7 hours Count % Less than 1 hour Count % More than 7 hours Count % Total Count % 1 2 3 4 5 Total 13 4 9 6 1 33 39.4% 12.1% 27.3% 18.2% 3.0% 100.0% 2 5 0 4 2 13 15.4% 38.5% .0% 30.8% 15.4% 100.0% 4 3 2 5 1 15 26.7% 20.0% 13.3% 33.3% 6.7% 100.0% 6 2 12 11 6 37 16.2% 5.4% 32.4% 29.7% 16.2% 100.0% 25 14 23 26 10 98 25.5% 14.3% 23.5% 26.5% 10.2% 100.0% Table 4-3 Relationship between talking time and being concern about VoIP security Table 4-2 indicates that those who spend more time on the phone/mobile are more concerned about privacy (eavesdropping) when using VoIP. 56.5% (26 out of 46) of the respondents who use phone/mobile more than 7 hours per month are concerned about VoIP privacy, while only 8.7% (4 out of 46) of the respondents who use phone/mobile less than 1 hour per month have the same concern. Table 4-3 indicates that the majority of respondents who use phone/mobile more than 7 hours per month are more concerned about VoIP security. Only 21.6% (8 out of 37) of the respondents who use phone/mobile more than 7 hours per month selected either Scale 1 or 2 (not or little concerned), while 45.9% (17 out of 37) selected either Scale 4 or 5 (very concerned). 4-2-3-3 Average monthly international call time via phone/mobile As shown in Table 4-4, more respondents (34.6%) do not use phone/mobile for making international calls. However, 29% spend less than 1 hour and 22.4% spend 1 to 3 hours each 69 Chapter 4- Results | month on making international calls using phone/mobile. Only 14% dedicate more than 3 hours of their phone/mobile conversation time to international calls. Average monthly international call time Frequency Percent 1 hour – 3 hours 24 22.4 Less than 1 hour More than 3 hours N/A Total 31 15 37 107 29.0 14.0 34.6 100.0 Table 4- 4 Average monthly international call time The average monthly international call time (via phone/mobile) was asked in order to investigate whether any relationship exists between international talking time and awareness and attitude towards security/privacy issues in VoIP. It turns out that the relationship between average monthly international talking time (via phone/mobile) and participants’ concerns about privacy (regardless of the used service), particularly about VoIP privacy and VoIP security, was found to be significant. This is illustrated in Tables 4-5, 4-6 and 4-7. Chi-Square value of the relationship: Pearson Chi-Square - Asymp. Sig. (2-sided): .001 Privacy concerns when making calls (1=Not concerned, 5=Very concerned) Average monthly international call time: 1 hour – 3 hours Count % Less than 1 hour Count % More than 3 hours Count % N/A Count % Total Count % 1 2 3 4 5 Total 3 3 8 6 3 23 13.0% 13.0% 34.8% 26.1% 13.0% 100.0% 6 8 5 10 1 30 20.0% 26.7% 16.7% 33.3% 3.3% 100.0% 1 1 0 8 5 15 6.7% 6.7% .0% 53.3% 33.3% 100.0% 11 14 3 6 2 36 30.6% 38.9% 8.3% 16.7% 5.6% 100.0% 21 26 16 30 11 104 20.2% 25.0% 15.4% 28.8% 10.6% 100.0% Table 4-5 Relationship between international talking time and being concern about privacy when making calls 70 Chapter 4- Results | Table 4-5 indicates that the majority of respondents who make international calls by phone/mobile are concerned about privacy (eavesdropping). 80.4% (33 out of 41) of the respondents who are very concerned about privacy (selected either 5 or 4 on the scale of 1 to 5) use phone/mobile to make international calls. The same trend applies to those who selected 3 on the 1 to 5 scale. Chi-Square value of the relationship: Pearson Chi-Square - Asymp. Sig. (2-sided): .002 Concern about VoIP privacy (eavesdropping) Average monthly 1 hour – 3 hours Count % international call time: Less than 1 hour Count % More than 3 hours Count % N/A Count % Total Count % No Yes Total 8 16 24 33.3% 66.7% 100.0% 17 12 29 58.6% 41.4% 100.0% 5 10 15 33.3% 66.7% 100.0% 27 8 35 77.1% 22.9% 100.0% 57 46 103 55.3% 44.7% 100.0% Table 4-6 Relationship between international talking time and being concern about VoIP privacy (eavesdropping) Table 4-6 indicates that most respondents who use VoIP to make international calls by their phone/mobile are concerned about privacy (eavesdropping). The table shows that 82.6% (38 out of 46) of the respondents who use VoIP to make international calls on their phone/mobile are concerned about privacy (eavesdropping), and in contrast, 52.6% (30 out of 57) are not. Table 4-7 indicates that the majority of respondents who use phone/mobile more than 1 hour/month for making international calls are more concerned about VoIP security. Only 18.4% (7 out of 38) who use phone/mobile more than 1 hour/month for making international calls selected either Scale 1 or 2 (not or little concerned), while 47.3% (18 out of 38) selected either Scale 4 or 5 (very concerned) and 34.2% (13 out of 38) selected Scale 3. 71 Chapter 4- Results | Chi-Square value of the relationship: Pearson Chi-Square - Asymp. Sig. (2-sided): .006 Concern about VoIP security (1=Not concerned, 5=Very concerned) Average monthly 1 hour – 3 hours Count % international call time: Less than 1 hour Count % More than 3 hours Count % N/A Count % Total Count % 1 2 3 4 5 Total 4 1 9 4 5 23 17.4% 4.3% 11 2 39.3% 7.1% 1 1 6.7% 6.7% 9 10 39.1% 17.4% 21.7% 6 8 21.4% 28.6% 4 6 8 28.1% 31.3% 12.5% 25.0% 25 14 1 28 3.6% 100.0% 3 15 26.7% 40.0% 20.0% 4 23 26 100.0% 100.0% 1 32 3.1% 100.0% 10 98 25.5% 14.3% 23.5% 26.5% 10.2% 100.0% Table 4-7 Relationship between international talking time and being concern about VoIP security 4-2-4-4 Using computers to make calls/voice chat As shown in Table 4-8 most respondents (68.2%, 73 out of 107) use computers to make calls/voice chat. Using computer to make calls/voice chat Frequency Percent No 34 31.8 Yes Total 73 107 68.2 100.0 Table 4- 8 Usage of computers to make calls/voice chat The question concerning usage of computers to make calls/voice chat was asked in order to investigate whether any relationship exists between talking time and awareness and attitude towards security/privacy issues in VoIP. The relationship between using computers to make calls/voice chat and the possibility of privacy breaches emerged as being significant. This is illustrated in Table 4-9. 72 Chapter 4- Results | Chi-Square value of the relationship: Pearson Chi-Square - Asymp. Sig. (2-sided): .041 Using computer to make calls/voice chat Possibility of privacy breaches in traditional telephony versus VoIP Don’t know Count % (Possibility of privacy breaches in traditional No telephony is not more than possibility of privacy breaches in VoIP) Same Count % Count % (Possibility of privacy breaches in traditional telephony is more than possibility of privacy breaches in VoIP) Yes Total Count % Count % No Yes Total 17 18 35 48.6% 51.4% 100.0% 6 21 27 22.2% 77.8% 100.0% 5 10 15 33.3% 66.7% 100.0% 5 23 28 17.9% 82.1% 100.0% 33 72 105 31.4% 68.6% 100.0% Table 4-9 Relationship between using computer to make calls/voice chat and possibility of privacy breaches Table 4-9 indicates that approximately the same number of participants, regardless of the use of computers to make calls/voice chat, think either traditional telephony is more secure than VoIP or vice versa. 18.1% (6 out of 33) of the respondents who do not use computers to make calls/voice chat believe that privacy breaches are more likely to occur in VoIP while 15.1% (5 out of 33) think the opposite. 29.1% (21 out of 72) of the respondents who use computers to make calls/voice chat believe that breaches of privacy are more possible in VoIP while 31.9% (23 out of 72) think the opposite is the case. 4-2-5-5 Average monthly use of computers to make calls/voice chat Table 4-10 shows that 27.1% of the respondents (29 out of 107) do not use computers to make calls/voice chat while 72.9% (78 out of 107) do so. 25.2% (27 out of 107) spend 1 hour–3 hours, 24.3% (25 out of 107) spend less than 1 hour and 24.3% (26 out of 107) spend more than 3 hours per month on computers making calls/voice chat 73 Chapter 4- Results | Average monthly use of computer to make calls/voice chat Frequency Percent 1 hour – 3 hours 27 25.2 Less than 1 hour More than 3 hours N/A Total 25 26 29 107 23.4 24.3 27.1 100.0 Table 4-10 Average monthly use of computer to make calls/voice chat It has to be pointed out that no relationship was found between average monthly use of computer to make calls/voice chat and awareness and attitude towards security/privacy issues in VoIP. 4-2-6-6 Preferred way to make international calls Table 4-11 indicates that 50.5% of the respondents (54 out of 107) prefer to use computers to make international calls while 46.7% (50 out of 107) prefer to use landline/mobile. Preferred way to make international calls Frequency Percent Computer 54 50.5 Land line/mobile 50 46.7 Total Missing Total 104 97.2 3 2.8 107 100.0 Table 4-11 Preferred way to make international calls This question was asked in order to investigate whether the participants prefer to use computers or landline/mobile to make international calls and whether this preference is related to VoIP privacy/security issues. The relationship between the preferred methods to make international calls (via computer or landline/mobile) and participants’ opinions about whether traditional telephony is more secure than VoIP, and also participants’ concern about VoIP privacy and VoIP security, was found to be significant. This is illustrated in Tables 4-12, 4-13 and 4-14. 74 Chapter 4- Results | Chi-Square value of the relationship: Pearson Chi-Square - Asymp. Sig. (2-sided): .022 Preferred way to make international calls Traditional telephony security versus VoIP security Don’t know Computer Land line/mobile Total 12 9 21 57.1% 42.9% 100.0% Count % (Traditional telephony is not more secure than VoIP) No Count % Same Count % (Traditional telephony is more secure than VoIP) Yes Count % Total Count % 20 8 29 69.0% 27.6% 100.0% 6 6 12 50.0% 50.0% 100.0% 14 27 43 32.6% 62.8% 100.0% 54 50 107 50.5% 46.7% 100.0% Table 4-12 Relationship between the preferred way to make international calls and participants’ opinion about whether traditional telephony is more secure than VoIP Table 4-12 indicates that the majority of participants who prefer to use computers for international calls do not think that traditional telephony (landline/mobile) is more secure than VoIP. In contrast most participants who prefer traditional telephony (landline/mobile) over computer for making international calls think the opposite. 37% (20 out of 54) of the respondents preferring computers over landline/mobile for international calls believe that traditional telephony is not more secure than VoIP, and 54% (27 out of 50) of the respondents choosing landline/mobile think that traditional telephony is more secure than VoIP. Chi-Square value of the relationship: Pearson Chi-Square - Asymp. Sig. (2-sided): .003 Concern about VoIP privacy (eavesdropping) Preferred way to make Computer Count % international calls Land line/mobile Count % Total Count % No Yes Total 36 16 52 69.2% 30.8% 100.0% 19 29 48 39.6% 60.4% 100.0% 55 45 100 55.0% 45.0% 100.0% Table 4-13 Relationship between the preferred way to make international calls and participants’ concern about VoIP privacy 75 Chapter 4- Results | Table 4-13 indicates that the participants who prefer to use computers for international calls are less concerned about VoIP privacy issues and in contrast, those who prefer landline/mobile are more concerned. This seems to be contradictory due to the fact that when we use computers for international calls we are actually using VoIP, while in the case of landline/mobile, VoIP might be used. 65.4% (36 out of 55) of the respondents who prefer computers over landline/mobile for international calls are not concerned about privacy (eavesdropping) in VoIP. It emerged that 64.4% (29 out of 45) who prefer landline/mobile are concerned. Chi-Square value of the relationship: Pearson Chi-Square - Asymp. Sig. (2-sided): .001 Concern about VoIP security (1=Not concerned, 5=Very concerned) Preferred way to make Computer Count % international calls Land line/mobile Count % Count Total % 1 2 3 4 5 Total 21 7 11 11 1 51 41.2% 13.7% 21.6% 21.6% 2.0% 100.0% 4 7 12 14 9 46 8.7% 15.2% 26.1% 30.4% 19.6% 100.0% 25 14 23 25 10 97 25.8% 14.4% 23.7% 25.8% 10.3% 100.0% Table 4-14 Relationship between the preferred way to make international calls and participants’ concern about VoIP security The relationship between the preferred way to make international calls and participants’ concerns about VoIP privacy and VoIP security are consistent. Both relationships indicate that the respondents who prefer computers over landline/mobile for international calls are less concerned about VoIP privacy and vice versa. Table 4-14 indicates that the majority of the participants who like to use computers for international calls selected either Scale 1 or 2 (not or little concerned). Conversely, the majority of the participants who prefer to use line/mobile for international calls selected either Scale 4 or 5 (very concerned). 54.9% (28 out of 51) of the respondents who prefer computers selected either Scale 1 or 2 from a five-point scale (not or little concerned about privacy when making international calls using VoIP ). However, 21.5% (11 out of 51) selected Scale 3, and 50% (23 out of 46) who prefer land 76 Chapter 4- Results | line/mobile selected either Scale 4 or 5 from a five-point scale (very concerned about privacy when making international calls using VoIP). Furthermore, 26% (12 out of 46) selected Scale 3 which also indicates their concern about privacy when using VoIP services. 4-2-7-7 Preferred service for international calls via land line/mobile Skype is the most commonly used service followed by landline/mobile (traditional services) and Discount International call services. As illustrated in Figure 4-3, “Lower cost” by 59% (59 out of 100) followed by “Convenience” by 27% (27 out of 100) and “Quality” by 12% (12 out of 100) are the main reasons for choosing a service (or services) for making international calls via landline/mobile. 12, 12% 27, 27% 59, 59% 2, 2% Convenience Friend/family suggestion Lower cost Quality Figure 4- 3 The main reason for choosing a service for international calls via Land line/mobile The preferred service for international calls via landline/mobile was asked in order to investigate which service (or services) participants prefer and whether this preference is related to VoIP privacy/security issues. The relationship between the preferred service for international calls via landline/mobile and participants’ concern about VoIP privacy and whether they had discussed security/privacy issues with their service provider was found to be significant. 77 Chapter 4- Results | The relationship between the preferred service for international calls via landline/mobile and participants’ concerns about VoIP privacy indicates that the majority of the respondents who are not concerned about VoIP privacy (eavesdropping) use Skype. This compares markedly to those who are concerned about this issue. Furthermore, the relationship reveals that 70.9% (22 out of 31) of the participants who are not concerned about VoIP privacy use Skype, while only 25.8% (8 out of 31) who are concerned about VoIP privacy use Skype. Furthermore, 48.2% (14 out of 29) of the respondents, whether being concerned about VoIP privacy or not, use landline/mobile (traditional services) for making international calls. The relationship between the preferred service for international calls via landline/mobile and whether they had discussed security/privacy issues with their service provider indicates that the majority of respondents who have never discussed security/privacy issues with their telephone/VoIP service provider use either landline/mobile (traditional services) or Skype for making international calls. The relationship also reveals that 100% (29 out of 29) and 90.3% (28 out of 31) of the participants who have not discussed security/privacy issues with their service provider use landline/mobile (traditional services) and Skype, respectively. 4-2-8-8 Preferred software for making calls/voice chat Table 4-15 shows that Skype is the most common used software (65.8%, 52 out of 79) followed by Yahoo! Messenger (11.3%, 9 out of 79) and MSN (0.03%, 3 out of 79). The table also shows that 73.8% (79 out of 107) use software and 21.5% (23 out of 107) do not use software to make calla/voice chat. 78 Chapter 4- Results | Preferred software for making calls/voice chat Frequency Percent MSN 3 2.8 N/A 23 21.5 Skype 52 48.5 Yahoo! Messenger 9 8.4 Others 15 14.0 Total 102 Missing Total 95.3 5 4.7 107 100.0 Table 4-15 Preferred software for making calls/voice chat In another summation of the evidence, Figure 4-4 shows that “Convenience” (51%, 40 out of 78) is the main reason for choosing the software for making calls/ voice chat, followed by “Quality” (28%, 22 out of 78), “Friend/family suggestion” (18%, 14 out of 78) and “Security” (3%, 2 out of 78). 22, 28% 14, 18% Convenience 2, 3% 40, 51% Friend/family suggestion Quality Security Figure 4- 4 Reason for choosing software for making calls/ voice chat by computer It should be pointed out that no relationship was found to exist concerning preferred software for making calls/voice chat and awareness and attitude towards security/privacy issues in VoIP. 79 Chapter 4- Results | 4-2-2 Awareness/attitude towards VoIP security/privacy 4-2-2-1 Concerned features when making international calls Figure 4-5 illustrates that the participants are mostly concerned about lower cost (56%, 57 out of 102) followed by quality (30%, 31 out of 102), convenience (9%, 9 out of 102) and security (3%, 3 out of 102). It has to be pointed out that two participants answered higher cost and video as their concerned feature. 3, 3% 2, 2% 9, 9% Convenience Lower cost 31, 30% 57, 56% Quality Security Others Figure 4-5 The most concerned feature when making international calls The question about concerned feature when making international calls was asked so that the feature that participants were most concerned about cold be investigated. It is a question that also referred to VoIP privacy/security issues. As depicted in Figure 4-5, participants are most concerned about lower cost and less concerned with security. A significant relationship was found for the most concerned feature when making international calls and the participants’ concerns about VoIP privacy. This is illustrated in Table 4-16. 80 Chapter 4- Results | Chi-Square value of the relationship: Pearson Chi-Square - Asymp. Sig. (2-sided): .008 Concern about VoIP privacy (eavesdropping) The most concerned feature Convenience Yes Total 2 6 8 25.0% 75.0% 100.0% 0 1 1 % .0% 100.0% 100.0% Count 39 17 56 69.6% 30.4% 100.0% 13 18 31 41.9% 58.1% 100.0% 0 3 3 .0% 100.0% 100.0% 1 0 1 100.0% .0% 100.0% 55 45 100 55.0% 45.0% 100.0% Count % when making international calls No higher cost Lower cost Count % Quality Count % Security Count % video Count % Total Count % Table 4-16 Relationship between the most concerned feature when making international and participants’ concern about VoIP privacy Table 4-16 indicates that the majority of the respondents who are most concerned about “Lower cost” when making international calls are not concerned about VoIP privacy (eavesdropping), while most respondents who are most concerned about “Convenience, Quality and Security” when making international calls are concerned about VoIP privacy (eavesdropping). The table also reveals that 70.9% (39 out of 55) of the participants who selected “Lower cost” also answered “No” (not concerned about VoIP privacy). Furthermore, 75% (6 out of 8) of the participants who selected “Convenience”, 58% (18 out of 31) who selected “Quality” and 100% (3 out of 3) who selected “Security” also answered “Yes” (concerned about VoIP privacy). 81 Chapter 4- Results | 4-2-2-2 Comparison of security between international/long distance calls and domestic calls Table 4-17 shows more respondents (35.5%, 38 out of 107) did not know whether international/long distance calls are less secure than domestic calls. 27.1% (29 out 107) believed that international/long distance calls are less secure than domestic calls while 21.5% (23 out 107) thought the opposite and 14% (15 out 107) believed that both are the same in terms of security. Comparison of security between international/long distance calls and domestic calls (International/long distance calls are not more secure than domestic calls) (International/long distance calls are more secure than domestic calls) Frequency Percent Don’t know 38 35.5 No 23 21.5 Same 15 14.0 Yes 29 27.1 Total 105 98.1 Missing 2 1.9 Total 107 100.0 Table 4- 17 Are international/long distance calls less secure than domestic calls? This question was asked in order to investigate participants’ opinions about whether international/long distance calls are less secure than domestic calls. This question also intends to find any relationship between the participants’ opinions and VoIP privacy/security issues. The relationship between participants’ opinions about whether international/long distance calls are less secure than domestic calls and whether privacy breaches in traditional telephony are more likely than in VoIP was found to be significant. This is illustrated in Table 4-18. In fact, Table 4-18 indicates that about half of the respondents (44.8%, 13 out of 29) who think international/long distance calls are less secure than domestic calls (regardless of the used service) also believe that privacy breaches are less possible in traditional telephony (landline/mobile) than in VoIP. Furthermore, almost the same number of participants who were 82 Chapter 4- Results | not sure whether international/long distance calls are less secure than domestic calls thinks the opposite about the possibility of privacy breach in VoIP and traditional telephony. Chi-Square value of the relationship: Pearson Chi-Square - Asymp. Sig. (2-sided): .013 Comparison of security between international/long distance calls and domestic calls Don’t know Count % (International/long distance calls are not more secure than domestic calls) No Count % Same Count % (International/long distance calls are more secure than domestic calls) Yes Total Count % Count % Possibility of privacy breaches in VoIP versus traditional telephony Don’t know No* Same Yes** Total 18 9 3 8 38 47.4% 23.7% 7.9% 21.1% 100.0% 8 4 3 8 23 34.8% 17.4% 13.0% 34.8% 100.0% 4 1 6 4 15 26.7% 6.7% 40.0% 26.7% 100.0% 5 13 3 8 29 17.2% 44.8% 10.3% 27.6% 100.0% 35 27 15 28 105 33.3% 25.7% 14.3% 26.7% 100.0% Table 4-18 relationship between participants’ opinion about whether international/long distance calls are less secure than domestic calls and whether privacy breaches in traditional telephony is more possible or in VoIP * Possibility of privacy breaches in traditional telephony is not more than possibility of privacy breaches in VoIP ** Possibility of privacy breaches in traditional telephony is more than possibility of privacy breaches in VoIP 4-2-2-3 Privacy concerns when making calls Table 4-19 shows that 28% (30 out of 107) of the participants selected Scale 4, 24.3% (26 out of 107) selected Scale 2, 19.6% (21 out of 107) selected Scale 1, 15% (16 out of 107) selected Scale 3 and 10.3% (11 out of 107) selected Scale 5. 83 Chapter 4- Results | Privacy concerns when making calls (Five point scale) Frequency Percent 1 (Not concerned) 21 19.6 2 26 24.3 3 16 15.0 4 30 28.0 5 (Very concerned) 11 10.3 Total 104 97.2 Missing 3 2.8 Total 107 100.0 Table 4- 19 Concern about privacy when making calls/ voice chat (Five-point scale) This question was asked in order to investigate that regardless of the used service, how concerned are participants about privacy (eavesdropping) when making calls/ voice chat. The answers reveal that the majority of the participants are not concerned or are little concerned about privacy (eavesdropping) when making calls/ voice chat. Specifically, 43.9% (47 out of 107) selected either Scale 1 or 2, highlighting that participants are not concerned or are little concerned about privacy (eavesdropping) when making calls/ voice chat, while 38.3% (41 out of 107) selected either Scale 4 or 5, indicating they are seriously concerned about privacy. Furthermore, 15% (16 out of 107), by selecting Scale 3, indicated that they are neutral. This question also intends to find any relationship between the participants’ concerns about privacy (eavesdropping) when making calls/ voice chat and other VoIP privacy/security issues. The relationship between participants’ concerns about privacy when making calls (regardless of the used service) and participants’ concerns about VoIP privacy and security was found to be significant. This is illustrated in Tables 4-20 and 4-21. Table 4-20 indicates that the majority of the participants who are concerned about VoIP privacy are also concerned about privacy when making calls either via traditional telephony or VoIP. The reverse trend applies for those who are not concerned about VoIP privacy. This group 84 Chapter 4- Results | selected either Scale 1 or 2 (not or little concerned) indicating regardless of the used service they are not concerned about privacy when making calls. Chi-Square value of the relationship: Pearson Chi-Square - Asymp. Sig. (2-sided): .000 Privacy concerns when making calls (1=Not concerned, 5=Very concerned) Concern about VoIP privacy No Count % (eavesdropping) Yes Count % Total Count % 1 2 3 4 5 Total 20 23 5 8 1 57 35.1% 40.4% 8.8% 14.0% 1.8% 100.0% 1 3 11 21 9 45 2.2% 6.7% 24.4% 46.7% 20.0% 100.0% 21 26 16 29 10 102 20.6% 25.5% 15.7% 28.4% 9.8% 100.0% Table 4-20 relationship between participants’ concerns about privacy when making calls and participants’ concerns about VoIP privacy The table reveals that 75.4% (43 out of 57) of the respondents who selected either Scale 1 or 2 from a five-point scale (not or little concerned about privacy when making calls/voice chat) also answered “No” (not concerned about privacy when using VoIP). However, 15.7% (9 out of 57) selected either Scale 4 or 5, which is not consistent with their “No” answer. Furthermore, 66.6% (30 out of 45) of the respondents selecting either Scale 4 or 5 from a fivepoint scale (very concerned about privacy when making calls/voice chat) also answered “Yes” (concerned about privacy when using VoIP). Furthermore, 24.4% (11 out of 45) chose Scale 3, which also indicates their concern about privacy when using VoIP services. Table 4-21 indicates that the participants’ concerns about privacy when making calls (regardless of the used service) and participants’ concerns about VoIP privacy are consistent. In both questions the majority (60.8%, 57 out of 97) of the respondents selected the same scale which points out that most of them are concerned at the same level about security/privacy regardless of the used service. The table reveals that 15.4% (15 out of 97) in both questions selected Scale 1, 11.3% (11 out of 97) Scale 2, 10.3% (10 out of 97) Scale 3, 15.4% (15 out of 97) Scale 4 and 8.2% (8 out of 97) Scale 5. 85 Chapter 4- Results | Chi-Square value of the relationship: Pearson Chi-Square - Asymp. Sig. (2-sided): .000 Privacy concerns when making calls (1=Not concerned, 5= Very concerned) Concern about VoIP 1 (Not concerned) Count % about security 2 Count % 3 Count % 4 Count % 5 (Very concerned) Total Count 1 2 3 4 5 Total 15 6 1 3 0 25 4.0% 12.0% .0% 100.0% 60.0% 24.0% 1 11 1 1 0 14 7.1% 78.6% 7.1% 7.1% .0% 100.0% 1 4 10 8 0 23 .0% 100.0% 3 25 4.3% 17.4% 43.5% 34.8% 1 3 4.0% 3 12.0% 12.0% 60.0% 12.0% 0 0 0 % .0% .0% .0% Count 18 24 15 % 15 2 8 20.0% 80.0% 29 11 18.6% 24.7% 15.5% 29.9% 11.3% 100.0% 10 100.0% 97 100.0% Table 4-21 relationship between participants’ concerns about privacy when making calls and participants’ concerns about VoIP security 4-2-2-4 Traditional telephony security versus VoIP security Table 4-22 shows that the majority of the respondents (40.2%, 43 out of 107) believe that traditional telephony (landline/mobile) is more secure than VoIP while 27.1% (29 out 107) think the opposite, and 11.2% (12 out 107) believe that both are the same in terms of security. 19.6% (21 out 107) did not know whether traditional telephony (landline/mobile) is more secure than VoIP. Traditional telephony security versus VoIP security (Traditional telephony is not more secure than VoIP) (Traditional telephony is more secure than VoIP) Frequency Percent Don’t know 21 19.6 No 29 27.1 Same 12 11.2 Yes 43 40.2 Total 105 98.1 Missing 2 1.9 Total 107 100.0 Table 4-22 Is traditional telephony (land line/mobile) more secure than VoIP? 86 Chapter 4- Results | This question was asked in order to investigate the participants’ opinions about whether traditional telephony (landline/mobile) is more secure than VoIP. The answers to this question reveal that participants believe that traditional telephony (landline/mobile) is more secure than VoIP. The relationship between participants’ views about whether traditional telephony (landline/mobile) is more secure than VoIP and whether privacy breaches in traditional telephony is more possible or in VoIP was found to be significant. This is illustrated in Table 423. Chi-Square value of the relationship: Pearson Chi-Square - Asymp. Sig. (2-sided): .002 Possibility of privacy breaches in VoIP versus traditional telephony Don’t know Count % (Possibility of privacy breaches in traditional telephony is not more than No possibility of privacy breaches in VoIP) Same Count % Count % (Possibility of privacy breaches in Yes traditional telephony is more than possibility of privacy breaches in VoIP) Count Total Count % % Traditional telephony security versus VoIP security Don’t know No* Same Yes** Total 12 7 2 14 35 34.3% 20.0% 5.7% 40.0% 100.0% 3 6 2 16 27 11.1% 22.2% 7.4% 59.3% 100.0% 2 3 6 4 15 13.3% 20.0% 40.0% 26.7% 100.0% 4 13 2 9 28 14.3% 46.4% 7.1% 32.1% 100.0% 21 29 12 43 105 20.0% 27.6% 11.4% 41.0% 100.0% Table 4-23 relationship between participants’ opinion about whether traditional telephony is more secure than VoIP and whether privacy breaches in traditional telephony is more possible or in VoIP * Traditional telephony is not more secure than VoIP ** Traditional telephony is more secure than VoIP Basically, these two questions are similar and target the same notion. The questionnaire was carefully designed in such a way that the researcher could cross-check the answers. 87 Chapter 4- Results | Table 4-23 demonstrates that most of those who did not know whether traditional telephony (landline/mobile) is more secure than VoIP also did not know whether privacy breaches are more possible when using traditional telephony (landline/mobile) or when using VoIP. The same trend applies to the participants who answered “Same” in both questions. The table reveals that only 31.4% (33 out of 105) of the respondents gave identical answers to both questions and 68.5% (72 out of 105) of the answers are not consistent. 4-2-2-5 Concern about VoIP privacy (eavesdropping) As shown in Table 4-24, about over half of the participants (53.3%, 57 out of 107) answered that they are not concerned about privacy (eavesdropping) when using VoIP while 43% (46 out of 107) answered the opposite. Concern about VoIP privacy (eavesdropping) Frequency Percent No 57 53.3 Yes 46 43.0 Total Missing Total 103 96.3 4 3.7 107 100.0 Table 4-24 Concern about VoIP privacy (eavesdropping) This question was asked in order to investigate whether the participants are concerned about privacy (eavesdropping) when make calls using VoIP. The answers to this question reveal that more of the participants are not concerned about privacy (eavesdropping) when using VoIP. A significant relationship was found to exist between participants’ concern about privacy (eavesdropping) when making calls using VoIP and their concern about VoIP security. This is illustrated in Table 4-25. 88 Chapter 4- Results | Table 4-25 indicates that the participants’ concern about VoIP privacy (eavesdropping) and VoIP security is consistent. The majority of the participants who are concerned about VoIP privacy (eavesdropping) also selected either Scale 4 or 5 (very concerned). This shows they are also concerned about VoIP security. The same trend applies to those who answered “No” (not concerned about VoIP privacy) by selecting either Scale 1 or 2 (not or little concerned). Chi-Square value of the relationship: Pearson Chi-Square - Asymp. Sig. (2-sided): .000 Concern about VoIP Security (1=Not concerned, 5=Very concerned) Concern about VoIP privacy No Count % (eavesdropping) Yes Count % Total Count % 1 2 3 4 5 Total 23 13 11 6 0 53 43.4% 24.5% 20.8% 11.3% .0% 100.0% 2 1 12 20 9 44 4.5% 2.3% 27.3% 45.5% 20.5% 100.0% 25 14 23 26 9 97 25.8% 14.4% 23.7% 26.8% 9.3% 100.0% Table 4-25 relationship between participants’ concern about VoIP privacy and VoIP security The table reveals that 67.9% (36 out of 53) of the respondents who are not concerned about privacy when using VoIP also selected either Scale 1 or 2 from a five-point scale. This indicates they are not at all or are little concerned about VoIP privacy when making international calls. However, only 20.7% (11 out of 53) selected Scale 3 which is not consistent with their “No” answer. This table also reveals that 65.9% (29 out of 44) of the respondents who are concerned about VoIP privacy also chose either Scale 4 or 5 from a five-point scale. It suggests that they are very concerned about VoIP privacy when making international calls. Furthermore, 27.2% (12 out of 44) selected Scale 3 which also indicates their concern about privacy when using VoIP services. 89 Chapter 4- Results | 4-2-2-6 Possibility of privacy breaches in VoIP versus traditional telephony Table 4-26 shows that more of respondents (32.7%, 35 out of 107) did not know whether privacy breaches are more possible when using traditional telephony (landline/mobile) or when using VoIP. Nearly one-quarter of participants (26.2%, 28 out 107) believed that traditional telephony (landline/mobile) is less secure than VoIP while 25.2% (27 out 107) thought the opposite, and 14% (15 out 107) believed that both are the same in terms of privacy. This question was asked in order to investigate the participants’ opinions about whether privacy breaches are more likely to occur when using traditional telephony (landline/mobile) or when using VoIP. The answers to this question reveal that most of the participants do not know whether privacy breaches are more likely to occur when using VoIP or when using traditional telephony (landline/mobile. Possibility of privacy breaches in VoIP versus traditional telephony Frequency Percent 35 32.7 27 25.2 15 14.0 28 26.2 105 98.1 Don’t know (Possibility of privacy breaches in traditional telephony is No not more than possibility of privacy breaches in VoIP) Same (Possibility of privacy breaches in traditional telephony is Yes more than possibility of privacy breaches in VoIP) Total Missing 2 1.9 Total 107 100.0 Table 4-26 Privacy breach is more possible in traditional telephony or VoIP? 4-2-2-7 Concern about VoIP security Table 4-27 shows that 24.3% (26 out of 107) of the participants selected Scale 4, 23.4% (25 out of 107) selected Scale 1, 21.5% (23 out of 107) selected Scale 3, 13.1% (14 out of 107) selected Scale 2 and 9.3% (10 out of 107) selected Scale 5. 90 Chapter 4- Results | Concern about VoIP security (Five point scale) Frequency Percent 1 (Not concerned) 25 23.4 2 14 13.1 3 23 21.5 4 26 24.3 5 (Very concerned) 10 9.3 Total 98 91.6 System Missing Total 9 8.4 107 100.0 Table 4-27 Concerned about VoIP security (Five-point scale) This question was asked in order to investigate how concerned the participants are about security issues when making international calls using VoIP. It emerged that 36.6% (39 out of 107) selected either Scale 1 or 2, revealing that participants are not concerned or are little concerned about security issues when using VoIP. Furthermore, 33.3% (36 out of 107) selected either Scale 4 or 5, indicating they are seriously concerned about security. Finally, 21.5% (23 out of 107) chose Scale 3 and this meant that they are neutral about the issue. 4-2-2-8 Possibility of privacy/security breaches in VoIP Figure 4-6 illustrates that 82% (55 out of 67) of the answers was valid and 18% (12 out of 67) irrelevant. There were no invalid answers. 12, 18% Valid answer 55, 82% Irrelevant answer Figure 4- 6 Valid and irrelevant answers 91 Chapter 4- Results | This question was asked in order to investigate participants’ opinions about the possibility of privacy and security breaches when using VoIP. Below is a summary of participants’ opinions: VoIP is less secure than regular landline/mobile services due to the nature of the technology. Since VoIP providers offer low-cost services, it is not expected that they offer the best facilities and privacy. Security/privacy is not a major concern due to the fact that the content of the conversations is not security sensitive (calling family, etc.). Do not talk about anything sensitive/important using VoIP/landline/mobile if you do not want it to be known. Conversations are monitored and analyzed by government agencies to protect national security. 4-2-2-9 Discussing security/privacy issues with service providers Table 4-28 shows that the majority of the participants (88.8%, 95 out of 107) had never discussed security/privacy issues with their telephone/VoIP service provider, while only 8% (8 out of 103) did so. Discussing security/privacy issues with service providers Frequency Percent No 95 88.8 Yes 8 7.5 Total 103 96.3 Missing 4 3.7 Total 107 100.0 Table 4-28 Discussing security/privacy issues with telephone/VoIP service provider 92 Chapter 4- Results | This question was asked in order to investigate whether the participants had ever discussed security/privacy issues with their telephone/VoIP service provider. The answers to this question reveal that most participants had never done this. 4-2-2-10 The discussed security/privacy issues with service providers As illustrated in Figure 4-7, only 1 answer to this question was valid and relevant. Two answers were invalid (one was a comment about the questionnaire and the other one was the character “-”) and 11 were irrelevant. Since no trend could be ascertained because the percentage of valid answers was so meager, no meaningful summarization can be provided. However, Table 4-30 presents the only valid answer. The discussed security/privacy issues with service providers I asked them how secure is their service? and they replied that our encryption method your call be safe and secure Table 4-29 The discussed security/privacy issues with service providers 1, 6% 2, 12% Invalid answer Irrelevant answer Valid answer 14, 82% Figure 4- 7 Valid, invalid and irrelevant answers 93 Chapter 4- Results | 4-5 Summary The results and findings of the on-line questionnaire are summarized and analyzed using SPSS and Microsoft Excel 2007. The overview and analysis of on-line questionnaire are presented. In addition, the relationship between variables were examined (using the chi-square test) and when a relationship was found to be significant and meaningful, it was explained in more detail. The next chapter, Chapter 5, discusses the knowledge developed in this thesis. It also describes the limitations of this study and suggests some possibilities for further research. 94 Chapter 4- Results | Chapter 5- Discussion This chapter provides a discussion about the knowledge developed in this study. It is organized as follows: Section 5.1 provides an overview of this chapter Section 5.2 provides a discussion about the results and findings of this research Section 5.3 describes the limitations of this study Section 5.4 introduces some possibilities for further research 95 Chapter 5- Discussion | 5-1 Overview In the previous chapter, the results and findings were presented, and overviews and analysis of the questions included in the on-line questionnaire were provided. This chapter provides a discussion of the results and findings, and outlines the limitations in this study. Further avenues for further research are suggested. 5-2 Discussion of the results and findings The discussion of the results and findings is presented into two sections, “Background” and “Awareness/attitude towards VoIP security/privacy”. The Background section provides discussion about the background characteristics of participants in regard to making calls/voice chat and their nationality. The second section discusses participants’ awareness and attitudes towards VoIP security and privacy issues, which are the aims of this research. 5-2-1 Background 5-2-1-1 Nationality There were no relationships between nationality and awareness/attitude towards security/privacy issues in VoIP. This is due to the fact that most of the countries (13 out of 18) had either 1 or 2 participants. Most of the respondents (60%, 64 out of 107) are Australian, while the rest of the participants (40%, 43 out of 107) are from 17 other countries. Obviously the sample size is too small to conclude that there is a relationship between nationality and awareness/attitude towards security/privacy issues in VoIP. 5-2-1-2 Average monthly talking time The analyses of the findings highlight the following in relation to average monthly talking time: 96 Chapter 5- Discussion | - Participants who spend more time on phone/mobile dedicate more of their conversation time to international calls. In all, 93.3% (14 out of 15) of the respondents who use phone/mobile more than 7 hours per month dedicate more than 3 hours to international calls, while 45.2% (14 out of 31) who use phone/mobile 1 to 4 hours per month dedicate less than 1 hour per month to international calls. - The majority of the respondents who use phone/mobile more than 1 hour per month also use computers to make calls/voice chat. Furthermore, the majority of the respondents who use phone/mobile less than 1 hour per month do not use computers to make calls/voice chat. Analyses indicate that 75.6% (28 out of 37) of the respondents who use phone/mobile 1 to 4 hours per month, 53.3% (8 out of 15) of those who use phone/mobile 4 to 7 hours per month and 77.5% (31 out of 40) of those who use phone/mobile more than 7 hours per month use computers to make calls/voice chat. Analysis further shows that 60% (9 out of 15) of the respondents who use phone/mobile less than 1 hour per month do not use a computer to make calls/voice chat. - The majority of those who speak more on phone/mobile also spend more time on computers making calls/voice chat. Findings show that 65% (26 out of 40) of the respondents who use phone/mobile more than 7 hours per month spend more than 1 hour per month on computers for making calls/voice chat, and 60% (9 out of 15) of those who use phone/mobile less than 1 hour per month do not use a computer to make calls/voice chat. In regard to users’ awareness and attitude towards VoIP privacy and security, the average monthly talking time is related to the participants’ concern about VoIP privacy and security issues. Those who speak more are more concerned. However, it has to be pointed out that although the results highlight that the participants who spend more than 7 hours/month on the phone/mobile are more concerned about VoIP privacy (eavesdropping) and VoIP security, there is no technical reason to support this belief. If a VoIP system is vulnerable to privacy/security breaches, the duration of the communication will not affect the system’s level of security and 97 Chapter 5- Discussion | consequently will not affect the users. For instance, in Zhu and Fu’s (2011) study, the duration of Skype calls is not a metric in their proposed traffic analysis attacks on Skype calls. This indicates that if one uses Skype more often, he or she is not more vulnerable to such attacks. Similarly, in Benini and Sicari’s (2008) research the risk assessment method they proposed when assessing the risks of intercepting VoIP calls is not related to the duration of calls. 5-2-1-3 Average monthly international call time The analyses of the findings highlight the following with reference to average monthly international call time: - The time dedicated to international calls when using phone/mobile follows the same pattern as the time spent on computers for calls/voice chat. Those who spend more (or less) time on phone/mobile for international calls spend more (or less) time on computers for calls/voice chat. Less than half (44.0% -11 out of 25) of the respondents who use phone/mobile for less than 1 hour/month for international calls also spend less than 1 hour/month on computers for calls/voice chat. The same trend applies to the other categories, 1 hour – 3 hours, more than 3 hours and N/A. -The respondents who make international calls by phone/mobile use discount international call services (or international telephone cards) and most respondents who do not make international calls by phone/mobile use Skype. This is consistent with the findings regarding the preferred software for making calls/voice chat. Almost all the VoIP free applications in addition to offering voice and video calls and chats, provide file transfer and instant messaging features. From this perspective Skype does not offer a unique service. The popularity of Skype is due to the fact that it is one of the first that targeted the PC-to-PC call market. In addition, the quality of services offered by Skype is reasonable and the (SkypeOut which enables calls to be placed from PCs to landlines/mobiles), and PSTN-to-PC (SkypeIn - which enables calls to be placed from landlines/mobiles to PCs) means that Skype offers a complete solution for making calls. 98 Chapter 5- Discussion | Skype is so widespread that it is in fact synonymous with PC-to-PC and low cost international calls. In regard to users’ awareness and attitudes towards VoIP privacy and security, the average monthly international call time is similar to the average monthly talking time. Both are related with the participants’ concern about VoIP privacy and security, and those who speak more are naturally more concerned. However, as discussed in section 5-2-1-2, from a technical point of view the duration of the communication has no effect on the system’s security. Therefore the users who speak more will not be affected. 5-2-1-4 Using computers to make calls/voice chat The analyses of the findings highlight the followings in relation to the use of computers to make calls/voice chat: - The majority of the respondents who use computers to make calls/voice chat spend either 1 hour – 3 hours or more than 3 hours each month doing this. Analyses reveal that 72.6% (53 out of 73) of the respondents who use computers to make calls/voice chat spend either 1 hour – 3 hours or more than 3 hours, while 37.7% (20 out of 73) spend less than 1 hour every month on a computer for this purpose. -The majority of the respondents who use a computer to make calls/voice chat prefer to use it for making international calls and those who do not use prefer using landline/mobile. Analyses reveal that 66.6% (48 out of 72) of the respondents who use computers to make calls/voice chat prefer computers while 33.3% (24 out of 72) prefer landline/mobile to make international calls. - The majority of the respondents who use a computer to make calls/voice chat use Skype. 71% (49 out of 69) of the respondents who use computer to make calls/voice chat use Skype, 0.08% 99 Chapter 5- Discussion | (6 out of 69) use Yahoo! Messenger, 0.04% (3 out of 69) use MSN and either 0.01% (1 out of 69) or 0.02% (2 out of 69) use various less common applications. In regard to users’ awareness and attitude towards VoIP privacy and security, using computers to make calls/voice chat is related to the participants’ opinions about the possibility of privacy breaches in VoIP and traditional telephony. The majority of the participants who use computers for making calls/voice chat believe that privacy breaches are less possible in VoIP than in traditional telephony. This attitude may refer to the network knowledge that computer users have. It has been pointed out in Porter et al. (2006a, pp. 114-118) that eavesdropping VoIP is harder in comparison to eavesdropping PSTN. This is due to the fact that PSTN security is considered to be physical wire security while for wiretapping VoIP attackers must have access to the communication channel of VoIP parties. This is due to the distributed environment of IP networks being more difficult to penetrate. 5-2-1-5 Average monthly use of computer to make calls/voice chat The analyses of the findings highlight the following in regard to the average monthly use of computers to make calls/voice chat: - The majority of the respondents - regardless of the time they spend on a computer for making calls/voice chat - use Skype. This is consistent with the previous analysis (using computers to make calls/voice chat) where the majority of the respondents who use computers to make calls/voice chat do use Skype. Analyses reveal that 55.5% (15 out of 27) of the respondents who spend 1 to 3 hours/month, 65.3% (17 out of 26) of those who spend more than 3 hours/month, and 52% (13 out of 25) of those who spend less than 1 hour/month on computers to make calls/voice chat use Skype. 100 Chapter 5- Discussion | 5-2-1-6 Preferred way to make international calls The analyses of the findings highlight the followings in relation to the preferred way to make international calls: - The majority of the respondents regardless of their preference for using either computers or landline/mobile for making international calls use Skype. Analyses reveal that 55.5% (30 out of 54) of the respondents who prefer to use computers for international calls and 42% (21 out of 50) of those who prefer landline/mobile over computer use Skype. This indicates that Skype is the most common service for making international calls either via computer or landline/mobile. - It is obvious that the reason for choosing a service by those who are most concerned about “lower cost” when making international calls, is the lower cost that the service offers. However, the same trend does not apply to those who chose a service for other reasons such as convenience, friend/family suggestion, quality and security. Analyses reveal that 42.4% (42 out of 99) of the respondents who are most concerned about lower cost when making international calls want a service that is cheaper. Therefore, the feature that the respondents are most concerned about when making international calls matches the reason that they choose a service for making such calls. This is not the case for those who chose a service for convenience (74%, 20 out of 27) and lower cost (27.5%, 16 out of 58) when making international calls since the reason for selecting a service differs from the concerned feature. This may indicate that the respondents did not accurately answer the questions. 5-2-1-7 Preferred service for international calls via land line/mobile The analyses of the findings highlight the following concerning the preferred service for making international calls via landline/mobile: Skype is the most commonly used service followed by landline/mobile (traditional services) and Discount International call services. The common factor with “Skype” and “Discount 101 Chapter 5- Discussion | International call services” is the lower cost that these services offer. In contrast, “landline/mobile (traditional services)” is more convenient and offers higher quality of service. However, it can be argued that Skype could be used on landline/mobile; therefore, the convenience and lower cost factors are addressed. 5-2-1-8 Preferred software for making calls/voice chat The analyses of the findings highlight the following in relation to the preferred software for making calls/voice chat: Convenience followed by quality, friend/family suggestion and security is the main reason for choosing computer software for making calls/ voice chat. In all, 49.3% (39 out of 79) of the respondents choose software for convenience, 25.3% (20 out of 79) for quality, 16.4% (13 out of 79) for friend/family suggestion and only 0.02% (2 out of 79) for security. This clearly highlighted the fact that respondents are least concerned about security features of the software they use. 5-2-2 Awareness/attitude towards VoIP security/privacy 5-2-2-1 Concerned features when making international calls The analyses of the findings highlight the following in relation to the participants’ most concerned feature when making international calls: - Participants are most concerned about lower cost followed by quality, convenience and security. Therefore, they are least concerned about security and this is probably due to the fact that generally people who make international calls talk to their relatives/friends and the content of their conversations is not confidential. Confidential and sensitive conversations go through end-to-end secure lines, which is common in enterprises and government-sensitive sectors. 102 Chapter 5- Discussion | - The majority of the respondents who are most concerned about “Convenience, Quality and Security” when making international calls are concerned about VoIP privacy (eavesdropping). In contrast, most of those (68.4%, 39 out of 57) who are most concerned about “Lower cost” are not concerned about VoIP privacy. This demonstrates that when most participants are paying less for their calls they are not concerned about the privacy of their conversations. This is consistent with the participants’ opinions about the possibility of privacy and security breaches in VoIP. Answers reveal that most of the participants did not expect VoIP providers to offer the best facilities and privacy since they offer low-cost services. 5-2-2-2 Comparison of security between international/long distance calls and domestic calls The analyses of the findings highlight the following in relation to the participants’ opinion about whether international/long distance calls are more secure or domestic calls: - More of the respondents (35.5%, 38 out of 107) do not know whether international/long distance calls are less secure than domestic calls. Only 27.1% (29 out 107) believe that international/long distance calls are less secure than domestic calls. Additionally, 44.8% (13 out of 29) of the respondents who believe international/long distance calls are less secure than domestic calls (regardless of the used service) also believe that PSTN is more secure than VoIP. This is due to the fact that VoIP is much more likely to be used for international than domestic calls. 5-2-2-3 Privacy concerns when making calls The analyses of the findings highlight the following in relation to the participants’ opinions about privacy (eavesdropping) when making calls/ voice chat: 103 Chapter 5- Discussion | - In all, 43.9% (47 out of 107) of the participants are not concerned or are little concerned about privacy (eavesdropping) when making calls/ voice chat. In contrast, 38.3% (41 out of 107) of the participants are seriously concerned about privacy, and 15% (16 out of 107) remained neutral on this issue. - The majority of the participants who are concerned about VoIP privacy and VoIP security are also concerned about privacy when making calls via traditional telephony and vice versa. This indicates that participants’ concern about privacy/security when making calls is not related to the service they use. In other words, these participants are concerned about privacy/security when making calls either by traditional telephony or VoIP. 5-2-2-4 Comparison of VoIP and traditional telephony from privacy/security perspective The analyses of the findings highlight the following when comparing VoIP and traditional telephony from the privacy/security perspective: - The majority of the participants believe that traditional telephony (landline/mobile) is more secure than VoIP. However, they do not know that the likelihood of privacy breaches in VoIP is more or the likelihood of privacy breaches in traditional telephony (landline/mobile) is more. This is in line with Patrick’s (2009, pp. 14-15) study where myths about VoIP security were addressed. He argues that although it is generally assumed that the traditional phone system (PSTN) is more secure than VoIP, this is not necessarily true. It has to be noted that PSTN security is based on physical security. Therefore, an eavesdropper can wiretap PSTN by physically accessing telephone lines which is much easier to do than to wiretapping VoIP systems. 104 Chapter 5- Discussion | 5-2-2-5 Concern about VoIP privacy (eavesdropping)/security The analyses of the findings highlight the followings in relation to participants’ concern about VoIP privacy (eavesdropping) and VoIP security: - The majority of the participants neither are concerned about VoIP privacy (eavesdropping) nor about VoIP security. - Participants’ concern about VoIP privacy and security is consistent. The majority of those (65.9%, 29 out of 44) who are concerned about VoIP privacy (eavesdropping) are also concerned about VoIP security, and the majority of participants (67.9%, 36 out of 53) who are not concerned about VoIP privacy are also not concerned about VoIP security. It has to be pointed out that in the on-line questionnaire privacy is considered to be eavesdropping and VoIP security is considered as other violating actions such as toll fraud. 5-2-2-6 Discussing security/privacy issues with service providers The analyses of the findings highlight the following in relation to the discussing security and/or privacy issues with service providers: - Most of the participants (88.8%, 95 out of 107) never discussed security/privacy issues with their service provider. This is in line with participants’ most concerned feature when making calls/voice chat. For international calls via PSTN participants are most concerned about lower cost (59%, 59 out of 100) and least concerned about security (2%, 2 out of 100). For calls/voice chat via computers participants are most concerned about convenience (51%, 40 out of 78) and least concerned about security (3%, 2 out of 78). This indicates that participants either using PSTN or VoIP are least concerned about security. 105 Chapter 5- Discussion | 5-3 Limitations One limitation of this study is the total number of the surveyed population. Although a sample of 107 participants is reasonable out of a population of about 300 students at the CIS, , more significant findings might be revealed from a larger sample. This is particularly important since when applying the chi-square test in order to determine if the relationship between variables is significant, the value of the expected count should be more than 5. When the sample is not large, some cells in the cross-tabulated tables may have an expected value of less than 5, which makes the chi-square test unreliable. To avoid this, researchers either combine categories or increase the sample size. In this study, the researcher could neither combine categories (due to the nature of the questions) nor increase the sample size (due to time limitation and the long process of obtaining ethics approval). Another limitation of this study is that the researcher did not have access to the complete list of the CIS student population. Consequently, it was not possible to apply truly the Simple Random Sampling (SRS) method, which is the preferred sampling technique in quantitative studies. 5-4 Further research Due to time constraints in conducting this study and the difficulties experienced in obtaining research ethics approval, the surveyed population was limited to the students at the School of Computer and Information Science, University of South Australia. Further research on this topic would entail a larger sample population, comprising the general population and students from other universities. Although this study attempted to investigate whether there is a relationship between nationality and awareness/attitude towards security/privacy issues in VoIP, this was not the major focus of this research. To enrich this study with cross-cultural perspectives, surveys 106 Chapter 5- Discussion | should be conducted in overseas universities. Finally, some suggestions could be offered to both VoIP service providers and VoIP users with regard to security/privacy issues. 107 Chapter 5- Discussion | Chapter 6- Conclusion The conclusion of this thesis is presented in this chapter 108 Chapter 6- Conclusion | The purpose of this thesis was to evaluate the users’ awareness of VoIP security vulnerabilities, and their attitudes towards privacy in VoIP communications. VoIP technology is widely established and it represents a major trend in telecommunications where an increasing number of stakeholders are involved. The lower cost and greater flexibility of VoIP over traditional phone systems are the key drivers of its wide acceptance in both businesses and individual uses. However, VoIP, like other technologies, while offering opportunities, introduces security risks as well. Since VoIP uses IP networks to transfer voice/video/data traffic, it complicates networking security, and it is vulnerable to both VoIP specific attacks and attacks to the underlying IP network. VoIP security has been widely studied from the technical and industrial perspectives. No known research to the best of the researcher’s knowledge has evaluated users’ perspectives on VoIP security and privacy vulnerabilities. This study evaluated the users’ awareness and attitudes towards privacy and security issues in VoIP communications. For this reason, an on-line questionnaire was designed to collect information, and to analyze the collected data quantitative-statistical techniques were employed. The findings of this study revealed that the majority of participants are neither concerned about VoIP privacy (eavesdropping) or VoIP security. They also do not expect to have the best facilities and privacy features when using VoIP since VoIP providers generally offer low-cost services. Also, the findings indicate that participants are most concerned about lower cost and least concerned about security when making international calls. However, most respondents who make international calls (either using VoIP or traditional telephony, and either by phone or via computer) are at some level concerned about privacy (eavesdropping). The same trend applies to domestic and interstate calls as well. 109 Chapter 6- Conclusion | For other participants where security/privacy is not a major concern, it is believed that the content of their conversations does not contain sensitive information (calling family, etc.). However, these participants are concerned about security/privacy issues if they are having a business/private conversation. Most of the participants believe that traditional telephony (landline/mobile) is more secure than VoIP. However, they are not aware that whether the likelihood of privacy breaches in VoIP is more or the likelihood of privacy breaches in traditional telephony (landline/mobile) is more. This is does not apply to the majority of the participants who use computers for making calls/voice chat since they believe that privacy breaches are less possible in VoIP than in traditional telephony. It is commonly believed that, regardless of the used service (VoIP/landline/mobile), privacy breaches are very possible and therefore one should not talk about anything sensitive or important. There is also a widespread belief that conversations are monitored and analyzed by governments for reasons of national security. There is a relationship between conversation duration and awareness and attitude towards security/privacy issues in VoIP. Those who spend more time talking either by phone or via computers, are more concerned about security/privacy. However, the respondents who prefer computers over landline/mobile for international calls are less concerned about VoIP privacy and vice versa. Convenience is the main reason for choosing specific software for making calls/voice chat by computers, although the respondents are least concerned about the security features of the software they use. In this regard, Skype is the most common service that participants use. There is no relationship between the time they spend on a computer for making calls/voice chat and the choice of Skype as software. However, those who speak more on phone/mobile 110 Chapter 6- Conclusion | also spend more time on computers for making calls/voice chat. Furthermore, most of the respondents who use computers to make calls/voice chat use Skype. 111 Chapter 6- Conclusion | Appendix A – Participant information sheet University of South Australia Division of Information Technology, Engineering and the Environment School of Computer and Information Science Participant information sheet Name: Alireza Heravi Qualification: Bachelors’ degree in computer engineering -software Contact: 0451053463 Research title: “Evaluation of users’ perspective on VoIP security vulnerabilities” Invitation to participate You are all invited to participate in this research study by answering an on-line anonymous questionnaire which will take less than 10 minutes. Participation is voluntary and highly appreciated. Following provides detailed information about the research. Purpose of this study VoIP refers to making calls through computers/ International telephone card/ Skye/ Cheep International call service providers and etc... The significance of security issues in voice over IP (VoIP) communications is well known and many papers have been published to address VoIP’s security vulnerabilities. However so far, no known research have been conducted to evaluate users’ perspective on these issues. This study seeks to evaluate the users’ awareness of VoIP security vulnerabilities, and their attitude towards privacy in VoIP communications. An on-line anonymous questionnaire is designed to collect information in order to investigate this matter. Collected information - The questionnaire is anonymous and no personal information is asked. 112 Appendix A |Participant information sheet - All records containing personal information will remain confidential and no information which could lead to identification of any individual will be released. - The questionnaire only contains questions regarding users’ opinion about VoIP security (e.g. Skype, voice chat, etc...). - Since the on-line questionnaire is designed by using Google Docs, the information will be stored at Google’s server. - Since the information is stored on Google’s server, it can be assumed that the information is secure and is only accessible by the researcher. - This study is a short-term research projects for assessment purposes only and the information will be stored for 12 months as a computer file (Google Docs spreadsheet). What the participant will be expected to do: It is expected that participants only answer the on-line anonymous questionnaire. Possible risks: - Since the questionnaire is anonymous, there is no possible risk for participants. - Participants are free to withdraw from the research project at any stage without affecting their status now or in the future. Final research findings Participants who wish to be provided with the final research findings please contact the researcher Email: heray004@mymail@unisa.edu.au The summary of the research findings will be emailed to participants who are keen to have it. This project has been approved by the University of South Australia's Human Research Ethics Committee. If you have any ethical concerns about the project or questions about your rights as a participant please contact the Executive Officer of this Committee, Tel: +61 8 8302 3118; Email: vicki.allen@unisa.edu.au' 113 Appendix A |Participant information sheet Appendix B- Recruitment email Dear All My name is Alireza Heravi and I’m doing LMCP (Master of Science (Computer and Information Science) program at UniSA, Division of Information Technology, Engineering and the Environment, School of Computer and Information Science. A partial fulfillment of the requirements for LMCP is submitting a thesis. My thesis title is “Evaluation of users’ perspective on VoIP’s security vulnerabilities” VoIP refers to making calls through computers/ International telephone card/ Skye/ Cheep International call service providers and etc... For this purpose I designed an on-line anonymous questionnaire. The questionnaire aims to explore the users’ perspective on security and privacy issues while using VoIP services to communicate. - Filling the questionnaire will take less than 10 minutes No personal information is asked. The online anonymous questionnaire is accessible through the following address: https://spreadsheets.google.com/viewform?formkey=dHlieHNkX1hQZHZYQVAzd3hCUGVnRHc6MQ Your participation is highly appreciated Thank you Alireza Heravi 114 Appendix B |Recruitment email Appendix C – Questionnaire 115 Appendix C – Questionnaire | 116 Appendix C – Questionnaire | 117 Appendix C – Questionnaire | 118 Appendix C – Questionnaire | References Ahmed, AS & Shaon, RH 2009, 'Evaluation of popular VoIP services', paper presented at the Adaptive Science & Technology, 2009. ICAST 2009. 2nd International Conference on. Al-Allouni, H, Rohiem, AE, Hashem, M, El-moghazy, A & Ahmed, AEA 2009, 'VoIP Denial of service attacks classification and implementation', paper presented at the Radio Science Conference, 2009. NRSC 2009. National. Alsmairat, I, Shankaran, R, Orgun, M & Dutkiewicz, E 2009, 'Securing Session Initiation Protocol in Voice over IP Domain', paper presented at the Dependable, Autonomic and Secure Computing, 2009. DASC '09. Eighth IEEE International Conference on. Amaratunga, D, Baldry, D 2001, ‘Case study methodology as a means of theory building: Performance measurement in facilities management organisations’, Work Study, Vol. 50, no. 3, pp. 95-105. Arul, P & Shanmugam, A 2009, ‘Generate a key for AES using biometric for VoIP network security’ Journal of Theoretical and Applied Information Technology, vol 15, no. 2, viewed 7 June 2010, < http://www.jatit.org/volumes/research-papers/Vol5No2/2Vol5No2.pdf>. Babbie, E 2001, The practice of learning social research, 9th edn, Wadsworth Thomson Learning, Belmont, California, USA Bailey, KD 2007, Methods of Social Research, 4 edn, The Free Press, New York. Baset, SA & Schulzrinne, HG 2006, 'An Analysis of the Skype Peer-to-Peer Internet Telephony Protocol', paper presented at the INFOCOM 2006. 25th IEEE International Conference on Computer Communications. Proceedings. Baroncelli, F, Martini, B, Martini, V & Castoldi, P 2010, 'Extending next generation network (NGN) architecture for connection-oriented transport', Computer Communications, vol. In Press, Corrected Proof. 119 References | Basicevic, I, Popovic, M & Kukolj, D 2008, 'Comparison of SIP and H.323 Protocols', paper presented at the Digital Telecommunications, 2008. ICDT '08. The Third International Conference on, June 29 2008-July 5 2008. Baumann, R, Cavin, S & Schmid, S 2006, Voice over IP - security and SPIT, Swiss Army, FU Br 41, KryptDet Report, University of Berne, viewed 15 April 2010, < http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.63.6329&rep=rep1&type=pdf>. Benini, M & Sicari, S 2008, 'Assessing the risk of intercepting VoIP calls', Computer Networks, vol. 52, no. 12, pp. 2432-2446. Berners-Lee, T 1996, 'WWW: past, present, and future', Computer, vol. 29, no. 10, pp. 69-77. Bonfiglio, D, Mellia, M, Meo, M, Ritacca, N & Rossi, D 2008, 'Tracking Down Skype Traffic', paper presented at the INFOCOM 2008. The 27th Conference on Computer Communications, IEEE. Blaikie, NWH 1991 ‘A critique of the use of triangulation in social research’, Quality and Quantity, Vol. 25, no. 2, pp. 115-136. Bonfiglio, D, Mellia, M, Meo, M & Rossi, D 2009, 'Detailed Analysis of Skype Traffic', Multimedia, IEEE Transactions on, vol. 11, no. 1, pp. 117-127. Bouma, G 2000, The research process, 4th edn, Oxford University Press, Melbourne, Vic. Branch, PA, Heyde, A & Armitage, GJ 2009, Rapid identification of Skype traffic flows, ACM, Williamsburg, VA, USA, pp. 91-96. Brittain, JE 2005, 'Electrical Engineering Hall of Fame: Alexander Graham Bell', Proceedings of the IEEE, vol. 93, no. 2, pp. 467-470. Broesch, JD 1997, 'Signal Acquisition', in Digital Signal Processing Demystified, Newnes, Burlington, pp. 49-58. 120 References | Bross, JFM & Meinel, C 2008, 'Can VoIP Live up to the QoS Standards of Traditional Wireline Telephony?', paper presented at the Telecommunications, 2008. AICT '08. Fourth Advanced International Conference on, 8-13 June 2008. Bryman, A 2004, Social research methods, 2ed edn, Oxford University Press. Butcher, D, Xiangyang, L & Jinhua, G 2007, '15-Security Challenge and Defense in VoIP Infrastructures', Systems, Man, and Cybernetics, Part C: Applications and Reviews, IEEE Transactions on, vol. 37, no. 6, pp. 1152-1162. Casner, S & Jacobson, V1999, ‘Compressing IP/UDP/RTP headers for low-speed serial links’, IETF RFC 2508, viewed 22 February 2011, < http://www.faqs.org/rfcs/rfc2508.html >. Cecez-Kecmanovic, D 2001, ‘Doing Critical IS Research: the Question of Methodology’ in QualitativeResearch in Information Systems: Issues and Trends, eds EM Trauth, Idea Group Publishing, Hershey PA, US. Chen, C-Y, Wu, T-Y, Huang, Y-M & Chao, H-C 2008, 'An efficient end-to-end security mechanism for IP multimedia subsystem', Computer Communications, vol. 31, no. 18, pp. 4259-4268. Chen, S-H, Guido, RC, Truong, T-K & Chang, Y 2010, 'Improved voice activity detection algorithm using wavelet and support vector machine', Computer Speech & Language, vol. 24, no. 3, pp. 531-543. Cherry, S 2005, 'Seven myths about voice over IP', Spectrum, IEEE, vol. 42, no. 3, pp. 52-57. Chua, WF 1986, 'Radical Developments in Accounting Thought', The Accounting Review, vol. 61, no. 4, pp. 601-632. Corrocher, N 2003, 'The diffusion of Internet telephony among consumers and firms: Current issues and future prospects', Technological Forecasting and Social Change, vol. 70, no. 6, pp. 525-544. 121 References | Dantu, R, Fahmy, S, Schulzrinne, H & Cangussu, J 2009, 'Issues and challenges in securing VoIP', Computers & Security, vol. , vol. 28, no. 8, pp. 743-753. Davidson, J & Peters, J 2000, Voice over IP Fundamentals, Cisco Press, Indianapolis, USA. Davidson, J, Peters, J, Bhatia, M, Kalidindi, S & Mukherjee, S 2006, Voice over IP Fundamentals, Second Edition, 2 edn, Cisco Press, Indianapolis, USA. Degermark, M, Nordgren, B &Pink, S 1999, ‘IP Header Compression’, IETF RFC 2507, viewed 20 February 2011, < http://www.faqs.org/rfcs/rfc2507.html >. Denzin, NK 1978, The research act: A theoretical introduction to sociological methods, 2nd edn, McGraw-Hill, New York. Denzin, NK, Lincoln, YS 2000, ‘Introduction’, in Handbook of Qualitative Research, 2nd edn, eds NK Denzin & YS Lincoln, Sage Publications, Thousand Oaks, California, pp. 1–30. De Vaus, DA 1995, Surveys in social research, 4th ed. edn, Allen & Unwin, North Sydney. Douglas, CS & Tom, L 2004, 'VoIP Security: Not an Afterthought', ACM Queue, vol. 2, no. 6. Engan, M, Casner, S & Bormann, C 1999, ‘IP Header Compression over PPP’, IETF RFC 2509, viewed 23 February 2011, < http://www.faqs.org/rfcs/rfc2509.html >. Engan, M, Casner, S & Bormann, C 2003, ‘IP Header Compression over PPP’, IETF RFC 3544, viewed 23 February 2011, < http://www.faqs.org/rfcs/rfc3544.html >. Epstein, J 2009, 'Securing Voice', in Scalable VoIP Mobility, Newnes, Boston, pp. 323-347. Erzberger, C, Prein, G 1997, ‘Triangulation: Validity and empirically-based hypothesis construction’, Quality and Quantity, Vol. 31, no. 2, pp. 141-154. 122 References | Flood, JE 1976, 'Alexander Graham Bell and the invention of the telephone', Electrical Engineers, Proceedings of the Institution of, vol. 123, no. 12, pp. 1387-1388. Frost, N 2006, 'VoIP threats - getting louder', Network Security, vol. 2006, no. 3, pp. 16-18. Gable, GG 1994, 'Integrating case study and survey research methods: an example in information systems', Eur J Inf Syst, vol. 3, no. 2, pp. 112-126. Ge, Z, Fischer-Huebner, S, Martucci, LA & Ehlert, S 2009, 'Revealing the Calling History of SIP VoIP Systems by Timing Attacks', paper presented at the Availability, Reliability and Security, 2009. ARES '09. International Conference on. Geneiatakis, D, Kambourakis, G, Dagiuklas, T, Lambrinoudakis, c & Gritzalis, S 2005, SIP Security Mechanisms: A state-of-the-art review, Department of Information and Communication Systems Engineering, University of the Aegean, viewed on 10 April 2010, <http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.105.7241&rep=rep1&type=pd f >. Geneiatakis, D, Dagiuklas, T, Kambourakis, G, Lambrinoudakis, C, Gritzalis, S, Ehlert, KS & Sisalem, D 2006, 'Survey of security vulnerabilities in session initiation protocol', Communications Surveys & Tutorials, IEEE, vol. 8, no. 3, pp. 68-81. Geneiatakis, D & Lambrinoudakis, C 2007, 'An ontology description for SIP security flaws', Computer Communications, vol. 30, no. 6, pp. 1367-1374. Glasmann, J, Kellerer, W & Muller, H 2001, 'Service development and deployment in H.323 and SIP', paper presented at the Computers and Communications, 2001. Proceedings. Sixth IEEE Symposium on, 2001. Glasmann, J, Kellerer, W & Muller, H 2003, 'Service architectures in H.323 and SIP: A comparison', Communications Surveys & Tutorials, IEEE, vol. 5, no. 2, pp. 32-47. Glesne, C, Peshkin, A 1992, Becoming a qualitative researcher: An introduction, Longman, New York. 123 References | Goel, V & Dolan, RJ 2004, 'Differential involvement of left prefrontal cortexin inductive and deductive reasoning', Cognition, vol. 93, no. 3, pp. B109-B121. Goode, B 2002, 'Voice over Internet protocol (VoIP)', Proceedings of the IEEE, vol. 90, no. 9, pp. 1495-1517. Gritzalis, D & Mallios, Y 2008, 'A SIP-oriented SPIT Management Framework', Computers & Security, vol. 27, no. 5-6, pp. 136-153. Groom, FM & Groom, KM 2004, The Basics of Voice over Internet Protocol, International Engineering Consortium, Chicago. Guarte, J & Barrios, E 2006, 'Estimation Under Purposive Sampling', Communications in Statistics: Simulation & Computation, vol. 35, no. 2, pp. 277-284. Gupta, P & Shmatikov, V 2007, 'Security Analysis of Voice-over-IP Protocols', paper presented at the Computer Security Foundations Symposium, 2007. CSF '07. 20th IEEE. Hall, DJ 1996, Practical social research: project work in the community, MacMillan, Houndmills, Basingstoke, Hampshire. Hammersley, M 1995, The politics of social research, Sage Publications, London. Handa, A 2009, 'Introduction to IMS', in System Engineering For IMS Networks, Newnes, Burlington, pp. 1-24. Hanes, D & Salgueiro, G 2008, Fax, Modem, and Text for IP Telephony, Cisco Press, Indianapolis, USA. Henry, GT 1990, Practical sampling, Sage Publications, Newbury Park. 124 References | Hirschheim, RA 1985, ‘Information Systems Epistemology: An Historical Perspective, London School of Economics, viewed 7 January 2011, <http://areadocenti.eco.unicas.it/virili/TerracinaRW/Kit/HirschheimISEpistemology.pdf>. Hong, L & Mouchtaris, P 2000, 'Voice over IP signaling: H.323 and beyond', Communications Magazine, IEEE, vol. 38, no. 10, pp. 142-148. Howcroft, D, Trauth, EM 2004, ‘The Choice of Critical Information Systems Research’ in Information Systems Research: Relevant Theory and Informed Practice, B Kaplan, DP Truex, D Wastell, AT Wood-Harper & JI DeGross, Kluwer Academic Publishers Boston, US. Huang, H & Lin, F 2009, 'A speech feature extraction method using complexity measure for voice activity detection in WGN', Speech Communication, vol. 51, no. 9, pp. 714-723. Huang, H, Yu, H-T & Feng, X-L 2009, 'A SPIT Detection Method Using Voice Activity Analysis', paper presented at the Multimedia Information Networking and Security, 2009. MINES '09. International Conference on, 18-20 Nov. 2009. Jick, TD 1979, 'Mixing Qualitative and Quantitative Methods: Triangulation in Action', Administrative Science Quarterly, vol. 24, no. 4, pp. 602-611. Johnson, RB & Onwuegbuzie, AJ 2004, 'Mixed Methods Research: A Research Paradigm Whose Time Has Come', Educational Researcher, vol. 33, no. 7, pp. 14-26. Kaplan, B & Duchon, D 1988, 'Combining Qualitative and Quantitative Methods in Information Systems Research: A Case Study', MIS Quarterly, vol. 12, no. 4, pp. 571-586. Karam, MJ & Tobagi, FA 2001, 'Analysis of the delay and jitter of voice traffic over the Internet', paper presented at the INFOCOM 2001. Twentieth Annual Joint Conference of the IEEE Computer and Communications Societies. Proceedings. IEEE, 2001. Karapantazis, S & Pavlidou, F-N 2009, 'VoIP: A comprehensive survey on a promising technology', Computer Networks, vol. 53, no. 12, pp. 2050-2090. 125 References | Klauer, KJ 1996, 'Teaching inductive reasoning: some theory and three experimental studies', Learning and Instruction, vol. 6, no. 1, pp. 37-57. Klein, HK, Myers, MD 1999, ‘A Set of Principles for Conducting and Evaluating Interpretive Field Studies in Information Systems’, MIS Quarterly, vol. 23, no. 1, pp. 67-94. Kleinrock, L 2008, 'History of the Internet and its flexible future', Wireless Communications, IEEE, vol. 15, no. 1, pp. 8-18. Kopsidas, S, Zisiadis, D & Tassiulas, L 2006, 'Voice Interactive Personalized Security (VoIPSEC) protocol: Fortify Internet telephony by providing end-to-end security through inbound key exchange and biometric verification', paper presented at the Hot Topics in Web Systems and Technologies, 2006. HOTWEB '06. 1st IEEE Workshop on, 13-14 Nov. 2006. Koren, T, Casner, S, Geevarghese, J, Thompson, B & Ruddy, P 2003, ‘Enhanced Compressed RTP (CRTP) for Links with High Delay, packet Loss and Reordering’, IETF RFC 3545, viewed 20 February 2011, < http://www.faqs.org/rfcs/rfc3545.html >. Kuhn, DR, Walsh, JT & Fries, S 2005, Security Considerations for Voice Over IP Systems, National Institute of Standards and Technology, U.S. Department of Commerce, viewed on 10 April 2010, <http://csrc.nist.gov/publications/nistpubs/800-58/SP800-58-final.pdf>. Lee, AS 1989, 'A Scientific Methodology for MIS Case Studies', MIS Quarterly, vol. 13, no. 1, pp. 33-50. Lee, AS 1991, 'Integrating Positivist and Interpretive Approaches to Organizational Research', Organization Science, vol. 2, no. 4, pp. 342-365. Lincoln, YS, Guba, EG 1985, Naturalistic Inquiry, Sage Publications, Newbury Park, California. Liu, Z, Martensson, A, Miyazaki, A, Svanbro, K, Wiebke, T, Yoshimura, T & Zheng, H 2001, ‘RObust Header Compression (ROHC): Framework and Four Profiles: RTP, UDP, ESP, and Uncompressed’, IETF RFC 3095, viewed 23 February 2011, < http://www.faqs.org/rfcs/rfc3095.html >. 126 References | Lukasik, S 2010, 'Why The ARPANET Was Built', Annals of the History of Computing, IEEE, vol. PP, no. 99, pp. 1-1. Markus, ML 1983, 'Power, Politics, and MIS Implementation', Communications of the ACM, vol. 26, no. 6, pp. 430-444. Martínez Perea, R 2008, 'The IMS', in Internet Multimedia Communications Using SIP, Morgan Kaufmann, Burlington, pp. 501-540. Mathison, S 1988, 'Why Triangulate?', Educational Researcher, vol. 17, no. 2, pp. 13-17. Mingers, J 2001, 'Combining IS Research Methods: Towards a Pluralist Methodology', Information Systems Research, vol. 12, no. 3, pp. 240-259. Mohapatra, SK 2009, 'Integrated planning for Next Generation Networks', paper presented at the Integrated Network Management-Workshops, 2009. IM '09. IFIP/IEEE International Symposium on, 1-5 June 2009. Mu, x, ller, J & Massoth, M 2010, 'Defense against Direct Spam over Internet Telephony by Caller Pre-validation', paper presented at the Telecommunications (AICT), 2010 Sixth Advanced International Conference on, 9-15 May 2010. Myers, MD 1997a, 'Qualitative Research in Information Systems', MIS Quarterly, vol. 21, no. 2, pp. 241-242. Myers, MD 1997b, 'Qualitative Research in Information Systems', MIS Quarterly, viewed 7 January 2011, <http://www.qual.auckland.ac.nz/>. Myers, MD 2009, Qualitative Research in Business & Management, Sage Publications, London. Neuman, WL 2003, Social research methods: Qualitative and quantitative approaches, 5th edn, Allyn and Bacon, Boston. 127 References | O'Neill, JE 1995, 'The role of ARPA in the development of the ARPANET, 1961-1972', Annals of the History of Computing, IEEE, vol. 17, no. 4, pp. 76-81. Oouch, H, Takenaga, T, Sugawara, H & Masugi, M 2002, 'Study on appropriate voice data length of IP packets for VoIP network adjustment', paper presented at the Global Telecommunications Conference, 2002. GLOBECOM '02. IEEE, 17-21 Nov. 2002. Orlikowski, WJ & Baroudi, JJ 1991, 'Studying Information Technology in Organizations: Research Approaches and Assumptions', Information Systems Research, vol. 2, no. 1, pp. 1-28. Patrick, P 2009, Voice over IP Security, Cisco Press, Indianapolis, USA. Perenyi, M, Gefferth, A, Trang Dinh, D & Molnar, S 2007, 'Skype Traffic Identification', paper presented at the Global Telecommunications Conference, 2007. GLOBECOM '07. IEEE. Piccard, P 2006, 'Skype Security', in Syngress Force Emerging Threat Analysis, Syngress, Rockland, pp. 103-121. Porter, T 2006, 'Threats to VoIP Communications Systems', in Syngress Force Emerging Threat Analysis, Syngress, Rockland, pp. 3-25. Porter, T & Gough, M 2007, 'Skype Security', in How to Cheat at VoIP Security, Syngress, Burlington, pp. 253-262. Porter, T, Kanclirz, J, Zmolek, A, Rosela, A, Cross, M, Chaffin, L, Baskin, B & Shim, C 2006a, 'PSTN Architecture', in Practical VoIP Security, eds. P Thomas, K Jan, Z Andyet al, Syngress, Burlington, pp. 91-121. Porter, T, Kanclirz, J, Zmolek, A, Rosela, A, Cross, M, Chaffin, L, Baskin, B & Shim, C 2006 b, ' The IP Multimedia Subsystem: True Converged Communications', in Practical VoIP Security, Syngress, Burlington, pp. 499-517. 128 References | Quittek, J, Niccolini, S, Tartarelli, S, Stiemerling, M, Brunner, M & Ewald, T 2007, 'Detecting SPIT Calls by Checking Human Communication Patterns', paper presented at the Communications, 2007. ICC '07. IEEE International Conference on, 24-28 June 2007. Quittek, J, Niccolini, S, Tartarelli, S & Schlegel, R 2008, 'On Spam over Internet Telephony (SPIT) Prevention', Communications Magazine, IEEE, vol. 46, no. 8, pp. 80-86. Ragin, CC 1987, The Comparative Method: Moving Beyond Qualitative and Quantitative Strategies, University of California Press, Berkeley, Los Angeles and London. Richardson, T 2007, 'Next Generation Network Management', in The Cable and Telecommunications Professionals' Reference (Third Edition), ed. H Goff, Focal Press, Boston, pp. 207-224. Rose, G 1982, Deciphering sociological research, Macmillan, London. Rufi, A 2007, Network Security 1 and 2 Companion Guide (Cisco Networking Academy), Cisco Press, Indianapolis, USA. Sarrocco, C & Ypsilanti, D 2007, ‘Convergence and next generation networks’, ministerial background report 2, Organization for Economic Cooperation and Development (OECD), viewed 9 March 2011, <http://www.oecd.org/dataoecd/25/11/40761101.pdf>. Schulzrinne, H & Rosenberg, J 1998a, ‘A Comparison of SIP and H.323 for Internet Telephony’, proceedings of the 1998 Workshop on Network and Operating System Support for Digital Audio and Video (NOSSDAV '98), July 1998, Cambridge, England. Schulzrinne, H & Rosenberg, J 1998b, 'Signaling for Internet telephony', paper presented at the Network Protocols, 1998. Proceedings. Sixth International Conference on, 13-16 Oct 1998. Schulzrinne, H & Rosenberg, J 1999, 'Internet Telephony: architecture and protocols - an IETF perspective', Computer Networks, vol. 31, no. 3, pp. 237-255. 129 References | Schulzrinne, H & Rosenberg, J 2000, 'The Session Initiation Protocol: Internet-centric signaling', Communications Magazine, IEEE, vol. 38, no. 10, pp. 134-141. Sengar, H, Zhen, R, Haining, W, Wijesekera, D & Jajodia, S 2010, 'Tracking Skype VoIP Calls Over The Internet', paper presented at the INFOCOM, 2010 Proceedings IEEE, 14-19 March 2010. Shanks, G 2002, 'Guidelines for Conducting Positivist Case Study Research in Information Systems', Australasian Journal of Information Systems, vol. 10, no. 1. Simon, M & Slay, J 2010, 'Recovery of Skype Application Activity Data from Physical Memory', paper presented at the Availability, Reliability, and Security, 2010. ARES '10 International Conference on, 15-18 Feb. 2010. Sisalem, D, Kuthan, J & Ehlert, S 2006, 'Denial of service attacks targeting a SIP VoIP infrastructure: attack scenarios and prevention mechanisms', Network, IEEE, vol. 20, no. 5, pp. 26-31. Srivatsa, M, Iyengar, A, Liu, L & Jiang, H 2010, 'Privacy in VoIP Networks: Flow Analysis Attacks and Defense', Parallel and Distributed Systems, IEEE Transactions on, vol. PP, no. 99, pp. 11. Stanton, R 2006, 'Secure VoIP - an achievable goal', Computer Fraud & Security, vol. 2006, no. 4, pp. 11-14. Strauss, AC, Corbin, JM 1998, Basics of Qualitative Research: Techniques and Procedures for Developing Grounded Theory, 2ed edn, Sage Publications, London. Sudman, S 1976, Applied sampling, Academic Press, New York. Sundquist, J & Service, N 2006, Top 10 Myths about VoIP, Epygi Technologies Ltd., viewed on 3 March 2011, <http://www.epygi.com/pdf/WhitePapers/Epygi%20white%20paper%20%2010%20VoIP%20Myths.pdf>. 130 References | Thom, GA 1996, 'H.323: the multimedia communications standard for local area networks', Communications Magazine, IEEE, vol. 34, no. 12, pp. 52-56. Trochim, WMK 2006, The Research Methods Knowledge Base, 2nd edition, viewed 4 January 2011, <http://www.socialresearchmethods.net/kb/dedind.php>. Varey, R J, Wood-Harper, T, Wood, R 2002, ‘A theoretical review of management and information systems using a critical communications theory’, Journal of Information Technology, vol.17, no. 4, pp. 229-240. Varshney, U, Snow, A, McGivern, M & Howard, C 2002, 'Voice over IP', Commun. ACM, vol. 45, no. 1, pp. 89-96. Venkatesha Prasad, R, Sangwan, A, Jamadagni, HS, Chiranth, MC, Sah, R & Gaurav, V 2002, 'Comparison of voice activity detection algorithms for VoIP', paper presented at the Computers and Communications, 2002. Proceedings. ISCC 2002. Seventh International Symposium on, 2002. VOIPSA, 2005, ‘VoIP Security and Privacy Threat Taxonomy’ viewed on 27 February 2011, <http://www.voipsa.org/Activities/VOIPSA_Threat_Taxonomy_0.1.pdf>. Wallingeord, T 2006, VoIP HACKS Tips & Tools for Internet Telephony, O'reilly, Sebastopol, CA, US. Walsh, TJ & Kuhn, DR 2005, 'Challenges in securing voice over IP', Security & Privacy, IEEE, vol. 3, no. 3, pp. 44-49. Wang, X, Chen, S & Jajodia, S 2005, Tracking anonymous peer-to-peer VoIP calls on the internet, ACM, Alexandria, VA, USA, pp. 81-91 Wang, X, Zhang, R, Yang, X, Jiang, X & Wijesekera, D 2008, Voice pharming attack and the trust of VoIP, ACM, Istanbul, Turkey, pp. 1-11. Warwick, DP 1975, The sample survey: theory and practice, McGraw-Hill, New York. 131 References | Weisberg, HF 1977, An introduction to survey research and data analysis, W. H. Freeman, San Francisco. Yates, F 1960, Sampling methods for censuses and surveys, 3rd ed., revised and enlarged. edn, C. Griffin, London. Ye, Z, Yuanchao, L, Vikram, A & Huirong, F 2009, 'On Privacy of Skype VoIP Calls', paper presented at the Global Telecommunications Conference, 2009. GLOBECOM 2009, IEEE. Yu-Sung, W, Bagchi, S, Singh, N & Wita, R 2009, 'Spam detection in voice-over-IP calls through semi-supervised clustering', paper presented at the Dependable Systems & Networks, 2009. DSN '09. IEEE/IFIP International Conference on, June 29 2009-July 2 2009. Zhang, R, Wang, X, Farley, R, Yang, X & Jiang, X 2009a, On the feasibility of launching the manin-the-middle attacks on VoIP from remote attackers, ACM, Sydney, Australia, pp. 61-69. Zhang, R, Wang, X, Yang, X, Farley, R & Jiang X 2009b, ‘An Empirical Investigation into the Security of Phone Features in SIP-Based VoIP Systems’, ISPEC pp. 59-70. Zhu, Y & Fu, H 2010, 'Traffic analysis attacks on Skype VoIP calls', Computer Communications, vol. In Press, Corrected Proof. Zisiadis, D, Kopsidas, S & Tassiulas, L 2007a, 'An Architecture for Secure VoIP and Collaboration Applications', paper presented at the Security, Privacy and Trust in Pervasive and Ubiquitous Computing, 2007. SECPerU 2007. Third International Workshop on, 19-19 July 2007. Zisiadis, D, Kopsidas, S & Tassiulas, L 2007b, 'Voice Interactive Personalized Security Protocol: Definition and Security Analysis', paper presented at the Secure Network Protocols, 2007. NPSec 2007. 3rd IEEE Workshop on, 16-16 Oct. 2007. 132 References |