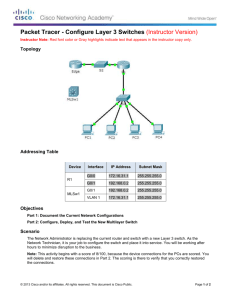
Configuring Windows Server 2008 Network Infrastructure
advertisement

Lesson Plans Configuring Windows Server 2008 Network Infrastructure (Exam 70-642) Table of Contents Course Overview .................................................................................................. 3 Section 0.1: Introduction ....................................................................................... 5 Section 0.2: Server Management.......................................................................... 6 Section 0.3: Remote Management........................................................................ 8 Section 0.4: Mathematical Foundations ................................................................ 9 Section 1.1: IPv4 Addressing .............................................................................. 10 Section 1.2: IPv4 Subnetting ............................................................................... 11 Section 1.3: IPv4 Host Configuration .................................................................. 13 Section 2.1: IPv6 ................................................................................................. 15 Section 2.2: IPv6 Addressing .............................................................................. 16 Section 2.3: IPv6 Configuration........................................................................... 18 Section 2.4: IPv6 Implementation ....................................................................... 20 Section 3.1: DHCP Configuration........................................................................ 21 Section 3.2: DHCP Options ................................................................................ 23 Section 3.3: Advanced DHCPv4 Settings ........................................................... 25 Section 3.4: Server Placement ........................................................................... 27 Section 3.5: Superscopes and Split Scopes ....................................................... 29 Section 3.6: DHCPv6 .......................................................................................... 30 Section 4.1: DNS Concepts ................................................................................ 32 Section 4.2: Name Resolution ............................................................................ 34 Section 4.3: Zone Configuration ......................................................................... 35 Section 4.4: Active Directory-integrated Zones ................................................... 37 Section 4.5: Resource Records .......................................................................... 39 Section 4.6: Client Configuration......................................................................... 40 Section 4.7: Dynamic DNS ................................................................................. 41 Section 4.8: Stub Zones and Forwarding ............................................................ 43 Section 4.9: Root Hints and Root Zone ............................................................... 45 Section 4.10: Zone Delegation ............................................................................ 46 Section 4.11: DNS Features ............................................................................... 47 Section 4.12: New DNS Features ....................................................................... 49 Section 4.13: Single-label Name Resolution ....................................................... 51 Section 4.14: DNS Design .................................................................................. 53 Section 5.1: Routing............................................................................................ 55 Section 5.2: RIP .................................................................................................. 57 Section 5.3: Demand-dial Routing ...................................................................... 59 Section 5.4: ICS and NAT ................................................................................... 61 Section 6.1: Remote Access Concepts ............................................................... 63 Section 6.2: Dial-up and VPN ............................................................................. 65 Section 6.3: SSTP............................................................................................... 67 Section 6.4: CMAK.............................................................................................. 69 Section 7.1: Network Location Profiles ............................................................... 70 Section 7.2: RADIUS .......................................................................................... 71 Section 7.3: Network Access Protection (NAP)................................................... 73 ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 1 Section 7.4: Network Authentication ................................................................... 75 Section 7.5: Firewall............................................................................................ 77 Section 7.6: IPsec ............................................................................................... 79 Section 7.7: DirectAccess ................................................................................... 81 Section 8.1: File Services ................................................................................... 83 Section 8.2: File Shares ...................................................................................... 85 Section 8.3: Offline Files ..................................................................................... 87 Section 8.4: NTFS Permissions .......................................................................... 88 Section 8.5: Share and NTFS Permissions ......................................................... 90 Section 8.6: EFS ................................................................................................. 91 Section 8.7: BitLocker ......................................................................................... 93 Section 8.8: BranchCache .................................................................................. 95 Section 8.9: Distributed File System (DFS) ......................................................... 97 Section 8.10: Shadow Copy ................................................................................ 99 Section 8.11: Backup and Restore.................................................................... 101 Section 8.12: Disk Quotas ................................................................................ 103 Section 8.13: FSRM Features ........................................................................... 105 Section 8.14: Print Services .............................................................................. 107 Section 9.1: WSUS ........................................................................................... 110 Section 9.2: Client Configuration....................................................................... 112 Section 10.1: Reliability and Performance Monitor ........................................... 114 Section 10.2: Event Viewer ............................................................................... 116 Section 10.3: Network Monitor .......................................................................... 118 Section 10.4: SNMP.......................................................................................... 120 Practice Exams ................................................................................................. 122 Appendix A: Approximate Time for the Course ................................................. 123 ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 2 Course Overview This course prepares students for the 70-642 Technology Specialist exam: Windows Server 2008 Network Infrastructure, Configuring. It focuses on the details of configuring the infrastructure of a network. Module 0 – Introduction This module introduces Microsoft’s recommendations of the technical experience a candidate should have before attempting the certification test. Students will become familiar with server and remote management tools. This module provides the mathematical calculations of how to convert numbers from binary to decimal and hexadecimal. This mathematical foundation is necessary for students to understand the IPv4 and IPv6 addresses they will be studying in the course. Module 1 – IPv4 This module discusses the details of configuring IPv4 addressing and subnetting. This includes topics of converting IPv4 addresses from binary to decimal, converting subnet masks to slant notation, identifying Ipv4 classes and ranges of IP addresses, and determining local and non-local hosts. Students will learn how to customize the number of subnets and hosts allowed on each subnet. Module 2 – IPv6 In this module students will learn why it will become necessary to migrate to IPv6. They will learn the basic format of IPv6 addresses, identifying IPv6 address types, and configuring IPv6 addresses using the GUI and command line. Interoperability strategies for implementing IPv4 and IPv6 are explored. Module 3 – DHCP This module covers DHCP configuration, customization options, and advanced settings. Students will learn proper server placement to assure client communication with the DHCP server, the rationale for creating superscopes and split scopes, and DHCPv6 options. Module 4 – DNS In Module 4 students will learn the details of how DNS translates host names to IP addresses and the process of DNS name resolution for both the client and server. Topics will also include; creating zone and zone transfers, creating or converting an Active Directory-integrated zone, creating and editing resource records, configuring client registration, automatically updating DNS using Dynamic DNS, resolving queries using stub zones and forwarding, using root hints and a root zone, managing zones through zone delegation, creating WINSintegrated zones and GlobalNames zones support, and implementing strategies and goals when designing a DNS solution. ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 3 Module 5 – Routing Module 5 teaches the students the basics of routing and how to manage routing table entries. Students will become familiar with installing RRAS components, and configuring RIP, demand-dial routing, and ICS and NAT solutions. Module 6 – Remote Access Module 6 discusses the details of configuring remote access and network authentication. Topics include; configuring a Remote Access server to use Dialup and VPN connections, configuring client connections, configuring a VPN using SSTP, and using CMAK to manage remote access. Module 7 – Network Access and Security In Module 7 students will learn several strategies for controlling network access and enhancing network security. These will include: controlling network location profiles, configuring a RADIUS client, server and proxy, configuring a DHCP server as an enforcement point, enforcing network authentication using Kerberos and NTLM, configuring a firewall, and configuring IPsec to protect IP packets during transmission. Module 8 – File and Print This module discusses managing network files and printing. Topics include: managing network file sharing and shared folders, controlling access using NTFS and share permissions, encrypting files and folders, protecting integrity of data through shadow copy, and backup and restore, restricting disk space using disk quotas and FSRM, and managing print services. Module 9 – WSUS In this module students will learn how to configure a WSUS server and client to manage the updating of software. They will also learn how to use MBSA to scan for security compliance. Module 10 – Performance and Reliability This module covers tools that are used to collect and monitor network data for performance and reliability. The Reliability and Performance Monitor provides network performance statistics. Event Viewer is used to monitor event logs. Network Monitor is used to gather information about network traffic. SNMP is used to manage network-attached devices. Practice Exams In Practice Exams students will have the opportunity to test themselves and verify that they understand the concepts and are ready to take the certification test. ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 4 Section 0.1: Introduction Summary This course prepares students for the 70-642 Technology Specialist exam: Windows Server 2008 Network Infrastructure, Configuring. Microsoft recommends at least one year experience in the following underlying technologies: IP addressing and services Names resolution File and print services Network access and remote access Monitoring network services This section introduces the instructor and the concepts that will be covered in this course. Video/Demo 0.1.1 Course Introduction Time 1:09 Total Time About 5 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 5 Section 0.2: Server Management Summary This section discusses a new management console, Server Manager, used to install and manage server components. Details include: Server Manager elements: o Role o Role services o Feature Windows PowerShell cmdlets that support Server Manager in Windows Server 2008 R2 The role of Server Core o Limited GUI support o Limited set of server roles o Features available in Windows Server 2008 R2 o Other limitations: No windows Shell Limited managed code support Only MSI support for unattended mode installs o Managing a server core system Students will learn how to: Configure and manage a server using the Server Manager. Install roles on a Server Core server. Configuring Server 2008 Network Infrastructure Objectives 102. Configure Dynamic Host Configuration Protocol (DHCP) 201. Configure a Domain Name System (DNS) server. Lecture Focus Questions: What are the differences among roles, role services, and features? How are dependencies handled during role installation? How does the server core installation differ from a standard server installation? What are the limitations of a server core installation? What are the advantages? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 6 Video/Demo Time 0.2.1 Using Server Manager 6:39 0.2.3 Server Core 1:37 0.2.4 Installing Roles on Server Core 6:05 Total 14:21 Total Time About 20 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 7 Section 0.3: Remote Management Summary This section examines using the following remote management tools to manage a server: Remote Desktop Remote Desktop Gateway MMC snap-ins Remote Server Administration Tools (RSAT) Windows Remote Shell Students will learn how to: Enable Remote Desktop on a Server Core. Enable remote management of the firewall. Open firewall ports to allow remote use of MMC snap-ins. Lecture Focus Questions: How do firewall ports affect your ability to remotely manage a server? What firewall port must be opened for Remote Desktop connections? What advantage does using TS Gateway have over using Remote Desktop? What is the effect of enabling the Remote Administration exception in the firewall? What are the operating system requirements for RSAT? Which remote administration tools could you use if the firewall had only ports 80 and 443 open? Video/Demo Time 0.3.1 Remote Management 4:06 0.3.2 Managing Server Core 14:45 Total 18:51 Total Time About 25 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 8 Section 0.4: Mathematical Foundations Summary This section explains the mathematical calculations to convert the following numbering systems: Base 2 - Binary Base 10 – Decimal Base 16 - Hexadecimal For students to understand IPv4 and IPv6 addresses they will need to know how to convert from binary to decimal and hexadecimal. Configuring Server 2008 Network Infrastructure Objectives 101. Configure IPv4 and IPv6 Addressing. Lecture Focus Questions: How does the decimal form of the binary number 10000000 differ from 01000000? What formula can you use to find the decimal equivalent for the binary number 00010000? How can you determine the binary value of the decimal number 161? What is the binary value for the hexadecimal value of E? What is E's decimal value? How many hexadecimal digits replace a full binary octet? Video/Demo 0.4.1 TCP/IP Mathematics Time 12:13 Total Time About 15 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 9 Section 1.1: IPv4 Addressing Summary In this section the students will learn how to convert IPv4 addresses and subnet masks from binary to decimal and how to convert subnet masks to slant notation. Students will learn: The five IPv4 classes of IP addresses with the range of IP addresses and the default subnet mask for each class. How to identify the Network ID, host ID, and the default gateway address to determine local and non-local hosts. Configuring Server 2008 Network Infrastructure Objectives 101. Configure IPv4 and IPv6 Addressing. o Configure IP address options Lecture Focus Questions: What is the format of an IPv4 address? What is the purpose of a subnet mask? What is the relationship between slash notation and the subnet mask? What is the default address class of the IP address 132.11.166.5? Video/Demo 1.1.1 IPv4 Addressing 1.1.2 Classful IPv4 Subnetting Total Time 6:10 11:22 17:32 Total Time About 20 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 10 Section 1.2: IPv4 Subnetting Summary This section discusses using IPv4 subnetting. Details include: Using a Variable Length Subnet Mask to vary the number of bits in the subnet mask to: o Subnet a single network address into multiple smaller subnets. o Create a supernet which combines multiple network addresses into a single larger subnet. Recommended subnetting tables for students to memorize: o Exponent values for powers of 2 o Binary subnet mask values and decimal equivalent values Students will learn how to: Given a network address and a custom mask, identify valid subnet addresses. Given a scenario with the desired number of hosts, choose a subnet address and mask. Given a subnet address and the subnet mask, identify valid host addresses on that subnet. Configuring Server 2008 Network Infrastructure Objectives 101. Configure IPv4 and IPv6 Addressing. o Subnetting o Supernetting Lecture Focus Questions: How many hosts can you have if you use a subnet mask of 255.255.255.192? How is a supernet different from a subnet? How can a magic number help you identify the possible subnet addresses when using a custom subnet mask? What is the decimal mask value for a /27 mask? How many approximate and actual hosts can you have when using a mask value of /23? What are the first and last addresses in a range used for? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 11 Video/Demo 1.2.1 Variable Length Subnet Mask (VLSM) 1.2.3 IPv4 Subnetting Cheat Sheet Total Time 17:19 4:38 21:57 Number of Exam Questions 4 questions Total Time About 30 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 12 Section 1.3: IPv4 Host Configuration Summary This section explores IPv4 host configuration. Details include: Configuration values: o IP address o Subnet mask o Default gateway o Host name o DNS server o WINS server o MAC address Methods used to configure IPv4 configuration settings: o Static (manual) assignment o Dynamic Host Configuration Protocol (DHCP) o Automatic Private IP Addressing (APIPA) o Alternate IP configuration Commands to configure Windows host with IPv4 configuration parameters TCP Chimney offloading Students will learn how to: Configure static and automatic IPv4 addressing. Specify an alternate IPv4 configuration. Use the command line to configure IPv4 settings. Configuring Server 2008 Network Infrastructure Objectives 101. Configure IPv4 and IPv6 Addressing. o Configure IP address options Lecture Focus Questions: What is the purpose of an alternate IPv4 configuration? When is a static configuration advantageous? When does a Windows computer use APIPA? What are its limitations? How can you tell when a computer has used APIPA to configure its IP address? What does the MAC address identify? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 13 Video/Demo Time 1.3.1 IPv4 Configuration 4:35 1.3.3 Configuring IPv4 Client Addressing 2:33 1.3.7 Using Netsh 7:32 1.3.9 Allowing Ping through the Firewall 3:45 Total 18:25 Lab/Activity Configure IP Settings Configure Automatic and Alternate Addressing Configure a Subnetted Address Number of Exam Questions 10 questions Total Time About 50 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 14 Section 2.1: IPv6 Summary This section discusses the need to migrate from IPv4 to IPv6. IPv4 was developed in 1974 and due to the rapid Internet growth we are running out of IPv4 addresses. Students will become familiar with the new features in IPv6 that are designed for the long term health and security of networks. Configuring Server 2008 Network Infrastructure Objectives 101. Configure IPv4 and IPv6 Addressing. Lecture Focus Questions: What are the reasons for the shift from IPv4 to IPv6? How does IPv6 make route summarization more efficient? How is IPsec treated differently in IPv6 than in IPv4? Why is NAT not needed when using IPv6? Video/Demo 2.1.1 IPv6 Concepts Time 3:47 Total Time About 5 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 15 Section 2.2: IPv6 Addressing Summary Students will learn the basic format of IPv6 addresses. IPv6 is a 128 bit address in which the first 64 bits called the prefix identifies the network and subnet address and the last 64-bits is the interface ID which identifies the network connection. They will also learn how to obtain the EUI-64 interface ID from the MAC address. Features of an IPv6 address Address types for IPv6: o Reserved o Multicast o Unicast Global unicast Link-local Unique local o Anycast o Loopback o Unspecified Details of the IPv6 64-bit prefix Configuring Server 2008 Network Infrastructure Objectives 101. Configure IPv4 and IPv6 Addressing. o Configure IP address options o Subnetting o Supernetting Lecture Focus Questions: What is the format of an IPv6 address? How can you represent leading zeroes and groups of zeroes in IPv6? Which type of IPv6 address uses the FC00::/7 prefix? How can you identify a link-local address? What does IPv6 use instead of a broadcast address? How can you easily identify IPv6 multicast addresses? What does the address ::1 represent? What is the purpose of the prefix length? What are the steps for deriving the EUI-64 interface ID from the MAC address? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 16 Video/Demo Time 2.2.1 IPv6 Addressing 3:57 2.2.3 IPv6 Address Types 8:42 2.2.5 IPv6 Prefix and Subnetting 2.2.7 IPv6 Interface ID Total 11:54 3:27 28:00 Total Time About 40 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 17 Section 2.3: IPv6 Configuration Summary This section examines the following details about IPv6 configuration: Methods to configure IPv6 information on a host: o Static full assignment o Static partial assignment o Stateless autoconfiguration o DHCPv6 The process to configure the IPv6 address for an interface States of an autoconfigured IPv6 address: o Tentative o Valid Preferred Deprecated o Invalid Commands to configure Windows hosts with IPv6 configuration parameters Students will learn how to: Configure IPv6 addresses using the GUI and the command line. Configure an advanced firewall rule to allow the ping command. Specify the IPv6 address and scope ID when using ping for a link-local address. Configuring Server 2008 Network Infrastructure Objectives 101. Configure IPv4 and IPv6 Addressing. o Configure IP address options o Subnetting Lecture Focus Questions: How does a host get its IPv6 address when using stateless autoconfiguration? What information does the DHCP server provide when using stateless DHCPv6? What address does a host use to request an address from a DHCP server? What is the difference between the M and O flags? What are the five states of an autoconfigured IPv6 address? How is the interface ID determined in static partial assignment? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 18 Video/Demo Time 2.3.1 IPv6 Configuration Facts 4:54 2.3.2 IPv6 Autoconfigured Address States 3:58 2.3.5 Configuring IPv6 Addresses 8:24 2.3.6 Using IPv6 Ping 8:09 Total 25:25 Number of Exam Questions 6 questions Total Time About 35 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 19 Section 2.4: IPv6 Implementation Summary In this section students will learn various strategies for implementing IPv4 and IPv6 interoperability: Dual stack Tunneling o Manually configured tunnel o Intra-site Automatic Tunnel Addressing Protocol (ISATAP) o 6-to4 tunneling o Teredo tunneling PortProxy Configuring Server 2008 Network Infrastructure Objectives 101. Configure IPv4 and IPv6 Addressing. o Interoperability between IPv4 and IPv6 Lecture Focus Questions: How does IPv6 support differ on various Microsoft operating systems? What limitations does ISATAP have for IPv6 implementation? Which IPv6 tunneling methods work through NAT? When should you implement Teredo? When is 6to4 tunneling automatically configured in Windows Server 2008? What technology allows an IPv4-only host to communicate with an IPv6only host? Video/Demo Time 2.4.1 IPv4 and IPv6 Interoperability 9:46 2.4.2 IPv6 Implementation in Server 2008 1:49 Total 11:35 Number of Exam Questions 3 questions Total Time About 20 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 20 Section 3.1: DHCP Configuration Summary This section discusses how to configure a DHCP server to deliver IP addresses to clients. Details include: Methods to obtain an address from a DHCP server: o DHCP Discover (D) o DHCP Offer (O) o DHCP Request (R) o DHCP ACK (A) Authorizing a DHCP server Objects to configure a DHCP server to deliver IP addresses: o Scope o Exclusion o Reservation The process to configure an existing server running server core for DHCP Using link layer filter to control the issuance or denial of DHCP leases based on MAC address for IPv4 Students will learn how to: Install and authorize a DHCP server. Create and activate scopes. Configure exclusion ranges and reservations. Configuring Server 2008 Network Infrastructure Objectives 102. Configure Dynamic Host Configuration Protocol (DHCP). o DHCP options o Exclusions o Authorize server in Active Directory o Scopes Lecture Focus Questions: What are the steps a client uses to acquire an address from DHCP? When must you authorize a DHCP server? What permissions do you need to authorize a DHCP server? Why does a DHCP server shut down if its address is not found in Active Directory? What does this protect against? How are reservations different from exclusions? How can you change the subnet on a scope? What are the two ways to exclude IP addresses from a scope? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 21 What information is necessary to configure a reservation? Video/Demo Time 3.1.1 DHCP Concepts 5:16 3.1.3 Installing DHCP 3:25 3.1.5 Configuring DHCPv4 Scopes 4:28 3.1.9 Using DHCP MAC Address Filtering 4:11 Total 17:20 Lab/Activity Authorize DHCP Servers Create a Scope Create Exclusion Ranges Create Client Reservations Number of Exam Questions 10 questions Time About 50 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 22 Section 3.2: DHCP Options Summary In this section students will learn about DHCP options to deliver a wide range of TCP/IP configuration parameters. Details include: Common option that can be used to configure DHCP: o 003 Router o 006 DNS Servers o 015 DNS Domain Name o 044 WINS/NBNS Servers o 046 WINS/NBT Node Type Levels that the DHCP options can be set at: o Server o Scope o Reservation Students will learn how to: Configure server, scope, and user/vendor class options. Design DHCP options to customize configuration and minimize administration. Configuring Server 2008 Network Infrastructure Objectives 102. Configure Dynamic Host Configuration Protocol (DHCP). o DHCP options Lecture Focus Questions: What are the most common DHCP options? Where can you configure DHCP options? How can you determine which options take precedence? How are DHCP options configured for IPv4 and IPv6? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 23 Video/Demo Time 3.2.1 DHCPv4 Options 3:55 3.2.2 Create DHCP Options 6:43 Total 10:38 Lab/Activity Configure Server Options Configure Scope Options Design Scope Options Design DHCP Options Number of Exam Questions 1 question Total Time About 30 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 24 Section 3.3: Advanced DHCPv4 Settings Summary This section examines using advanced DHCPv4 settings to optimize DCHP server performance. Details include Advanced DHCPv4 settings: o Bindings o Backup and Restore o Dynamic DNS o Conflict Detection The role of Bootstrap Protocol (BOOTP) Components required by BOOTP o Client workstation o DHCP server o TFTP server Steps to configure a DHCP server to support Bootstrap Protocol (BOOTP) clients for diskless network boot Students will learn how to: Configure server bindings. Backup or restore a DHCP server. Configure proxy settings for dynamic DNS updates. Set the number of conflict detection attempts. Configuring Server 2008 Network Infrastructure Objectives 102. Configure Dynamic Host Configuration Protocol (DHCP). o Creating new options o PXE boot Lecture Focus Questions: How does conflict detection work? How can this affect system performance? How can you transfer the DHCP configuration from one server to another? Why would you configure BOOTP? Which options should you configure through the BOOTP table and not DHCP options? What should you do so that host names for computers running Windows NT 4.0 are automatically registered using DDNS? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 25 Video/Demo Time 3.3.1 Advanced DHCPv4 Settings 2:00 3.3.2 Configuring Advanced Settings 2:49 Total 4:49 Number of Exam Questions 6 questions Total Time About 15 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 26 Section 3.4: Server Placement Summary In this section students will learn how DHCP server placement affects the ability of clients to communicate with the DHCP server. The following strategies to provide DHCP for multiple subnets are presented: DHCP server on each subnet Multihomed DHCP server BOOTP forwarding DHCP relay agent Students will learn how to: Configure a DHCP relay agent. Configuring Server 2008 Network Infrastructure Objectives 101 Configure IPv4 and IPv6 addressing. o Multi-homed 102. Configure Dynamic Host Configuration Protocol (DHCP). o DHCP relay agents Lecture Focus Questions: How can you provide DHCP services to clients on subnets that do not have a DHCP server? What is a multihomed server, and how is it used with DHCP? How does a DHCP relay agent differ from a router that has BOOTP forwarding enabled? What are the advantages to having a DHCP server on every subnet? How can BOOTP forwarding affect your network? Video/Demo Time 3.4.1 DHCP Server Placement 4:16 3.4.3 Configuring a DHCP Relay Agent 1:27 Total 5:43 ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 27 Lab/Activity Configure a DHCP Relay Agent Number of Exam Questions 4 questions Total Time About 15 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 28 Section 3.5: Superscopes and Split Scopes Summary This section discusses how and when to use superscopes and split scopes. Superscopes are used to combine multiple address ranges into a single logical range. Split scopes provide fault tolerance by two DHCP servers servicing a portion of each range for each subnet. Students will learn how to: Use the 80/20 rule to create a split scope. Configuring Server 2008 Network Infrastructure Objectives 102. Configure Dynamic Host Configuration Protocol (DHCP). o Scopes Lecture Focus Questions: What are the reasons for deploying a superscope? When using multiple DHCP servers for a single scope, how should you configure the scope range for each server? Why do you configure an exclusion for a part of the address range? How should you configure the relay agent to ensure that the preferred server responds before the backup server in a split scope deployment? How does a clustered server provide fault tolerance? Video/Demo 3.5.1 Superscopes and Split Scopes Time 8:01 Lab/Activity Add a DHCP Server on Another Subnet Number of Exam Questions 3 questions Total Time About 15 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 29 Section 3.6: DHCPv6 Summary This section examines configuring DHCPv6. Details include: Methods to assign IPv6 addresses to clients: o Stateless DCHPv6 o Stateful DHCPv6 Messages exchanged between the client and the DHCP when stateful DHCPv6 is used: o Solicit Packet (S) o Advertise Packet (A) o Request Packet (R) o Reply Packet (R) Students will learn how to: Create and activate an IPv6 scope using the global unicast prefix. Include address range exclusions as part of an IPv6 scope. Configuring Server 2008 Network Infrastructure Objectives 102. Configure Dynamic Host Configuration Protocol (DHCP). o DHCPv6 Lecture Focus Questions: What configuration information is provided by IPv6 routers when using IPv6 autoconfiguration? How does this differ from using APIPA with IPv4? What are the messages used to configure clients in stateful DHCPv6? Under what circumstances do you use stateful DHCPv6? What are the flag settings? What makes autoconfiguration of IPv6 hosts possible? Video/Demo Time 3.6.1 DHCPv6 4:01 3.6.2 Configuring DHCPv6 4:10 Total 8:11 ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 30 Number of Exam Questions 2 questions Total Time About 10 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 31 Section 4.1: DNS Concepts Summary In this section students will learn concepts of how the Domain Name System (DNS) translates host names to IP addresses. DNS is a distributed database with multiple servers holding different portions of the data. Components of the DNS hierarchy o .(dot) domain o Top Level Domains (TLDs) (.com, .edu, .gov) o Second-level and additional domains o Hosts Terms that relate to DNS: o A fully qualified domain name (FQDN) o Forward lookup o Authoritative server o Referral o Recursion Authoritative DNS zones: o Primary o Secondary o Active Directory-integrated Zone types: o Forward lookup zone o Reverse lookup zone Common resource records: o SOA (Start of Authority) o NS (name server) o A (host address) o AAAA (quad-A) o PTR (pointer) o CNAME (canonical name) o MX (Mail Exchanger) o SRV (service locator) o WINS and WINS-R resource records The role of Dynamic DNS (DDNS) Secure DDNS Configuring Server 2008 Network Infrastructure Objectives 201. Configure a Domain Name System (DNS) server. 202. Configure DNS zones. o Zone types o Dynamic Domain Name System (DDNS) ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 32 o Secure DDNS o Reverse lookup zones 203. Configure DNS records. o Record types Lecture Focus Questions: What is the purpose of DNS? How does an FQDN identify a host? How is an Active Directory-integrated zone different from a primary zone? How is secondary zone data changed? What is the difference between a forward lookup zone and a reverse lookup zone? What is the purpose of PTR records? How does DDNS simplify DNS management? What type of zone would you create if you wanted to use secure dynamic updates? Video/Demo Time 4.1.1 DNS Concepts 8:44 4.1.3 Authoritative Zones 8:28 4.1.5 Resource Records 4:52 4.1.7 Dynamic DNS 2:41 Total 24:45 Total Time About 30 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 33 Section 4.2: Name Resolution Summary This section examines the process of DNS name resolution for both the client and the server. Details include: On the client side, there are three checks a client can go through to resolve a DNS name to an IP address: o Hosts file o Local DNS cache o DNS server Command to view the local DNS cache (ipconfig /displaydns) Command to clear the local DNS cache (ipconfig /flushdns) The DNS name resolution process on the server: Configuring Server 2008 Network Infrastructure Objectives 205. Configure name resolution for client computers. Lecture Focus Questions: How does the DNS resolution process on a client differ from the resolution process on a server? Why are there two different DNS cache locations on a DNS server? How do entries in the HOSTS file affect name resolution? What are root hints and how do they affect name resolution performed by a DNS server? Video/Demo Time 4.2.1 DNS Client Name Resolution 9:41 4.2.2 DNS Server Name Resolution 3:54 4.2.3 Examining Name Resolution 7:26 Total 21:01 Number of Exam Questions 1 question Total Time About 25 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 34 Section 4.3: Zone Configuration Summary In this section students will learn the basics of zone configuration. Configuring the DNS server role The role of A zone transfer The role of a reverse lookup zone Students will learn how to: Add the DNS server role to a server. Create primary, secondary, and reverse lookup zones. Configure zone transfers between primary and secondary zones. Configuring Server 2008 Network Infrastructure Objectives 201. Configure a Domain Name System (DNS) server. o Cache-only 202. Configure DNS zones. o Reverse lookup zones 204. Configure DNS replication. o DNS secondary zones o Securing zone transfer o SOA refresh Lecture Focus Questions: How does a caching-only server reduce name resolution traffic? How can a secondary zone provide security for a DNS domain? What is the role of the SOA record during a zone transfer? What are the advantages to changing zone data through the dnscmd command rather than manually editing the zone file? Why would you choose a secondary server over a caching-only server? What type of name resolution is performed by reverse lookup zones? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 35 Video/Demo Time 4.3.1 Creating a Primary Zone 7:17 4.3.3 Creating Secondary Zones 8:12 4.3.6 Reverse Lookup Zones 6:14 4.3.7 Creating Reverse Lookup Zones 4:15 Total 25:58 Lab/Activity Create a Primary Zone Create a Secondary Zone Create a Reverse Lookup Zone Number of Exam Questions 19 questions Total Time About 65 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 36 Section 4.4: Active Directory-integrated Zones Summary This section discusses how Active Directory-integrated zones can be used to manage zone information. Students will learn how to: Create an Active Directory-integrated zone and configure the replication scope. Convert a primary zone to an Active Directory-integrated zone. Configuring Server 2008 Network Infrastructure Objectives 202. Configure DNS zones. o Active Directory integration 204. Configure DNS replication. o Active Directory Integrated replication scopes Lecture Focus Questions: What are some of the benefits of Active Directory-integrated (AD-I) zones? How is zone data for Active Directory-integrated zones replicated? Under which circumstances could you disable zone transfers for an AD-I zone? When would you need to continue using DNS zone transfers? How do AD-I zones integrate with other zone types such as primary or secondary? What are the four replication scopes of an AD-I zone? Video/Demo 4.4.1 DNS Integration with AD 4.4.2 Managing Active Directory-integrated Zones Total Time 8:06 10:31 18:37 Lab/Activity Create an Active Directory-integrated Zone Convert a Zone ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 37 Number of Exam Questions 10 questions Total Time About 40 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 38 Section 4.5: Resource Records Summary This section provides information about creating and managing resource records. Students will learn how to: Create common resource records. Adding or deleting a DNS record. Configuring Server 2008 Network Infrastructure Objectives 203. Configure DNS records. Lecture Focus Questions: What is the advantage to using DDNS to manage records? What record type would you use to add alternate names for a DNS host? What records are used to identify and locate domain controllers? What happens if you create A and PTR records together if the reverse lookup zone doesn't exist? What happens when you create a CNAME record with a blank name? Video/Demo 4.5.1 Creating Resource Records Time 8:03 Lab/Activity Create a Zone and Add Records Create A and CNAME Records Troubleshoot Name Resolution 1 Troubleshoot Name Resolution 2 Number of Exam Questions 11 questions Total Time About 40 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 39 Section 4.6: Client Configuration Summary In this section students will learn how to configure DNS client settings. Students will learn how to: Configure a connection-specific suffix using advanced TCP/IP properties. Specify a suffix search order. Manage DNS client registration. Configuring Server 2008 Network Infrastructure Objectives 205. Configure name resolution for client computers. o Suffix search order Lecture Focus Questions: What is the purpose of listing multiple DNS IP addresses on the client? What are the differences between a primary suffix and a connectionspecific suffix? What is a parent suffix? How are they used during name resolution? How do custom search suffixes differ from the default suffix search order? Video/Demo 4.6.1 DNS Client Settings Time 4:33 Lab/Activity Configure DNS Server Addresses Configure Search Suffixes 1 Configure Search Suffixes 2 Configure DNS Client Registration Configure DNS Group Policy Settings Number of Exam Questions 4 questions Total Time About 35 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 40 Section 4.7: Dynamic DNS Summary This section covers using Dynamic DNS to automatically update DNS records. Settings on the following components are used to configure Dynamic DNS: Client DHCP server DNS server Students will learn how to: Enable dynamic updates on a DNS zone. Configure DHCP server settings to support dynamic updates. Configuring Server 2008 Network Infrastructure Objectives 202. Configure DNS zones. o Secure DDNS 203. Configure DNS records. Lecture Focus Questions: What is the relationship between DNS and DHCP when using dynamic updates? What are the DDNS settings you can configure on the DHCP server? Which operating systems support dynamic updates? What are the restrictions on record creation when using secure dynamic updates? Which zone types support secure dynamic updates? How can DHCP be used to help the dynamic update process? Lab/Activity Enable Dynamic DNS Updates Troubleshoot Dynamic DNS 1 Troubleshoot Dynamic DNS 2 Troubleshoot Dynamic DNS 3 ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 41 Number of Exam Questions 4 questions Total Time About 25 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 42 Section 4.8: Stub Zones and Forwarding Summary This section discusses using stub zones and forwarding to resolve queries. Methods to control the server’s use of forwarders include: Secondary zone Stub zone Conditional forwarder Students will learn how to: Create a stub zone. Configure forwarders and conditional forwarding. Configuring Server 2008 Network Infrastructure Objectives 201. Configure a Domain Name System (DNS) server. o Conditional forwarding 204. Configure DNS replication. o DNS secondary zones o DNS stub zones o Active Directory Integrated replication scopes o Securing zone traffic Lecture Focus Questions: How does conditional forwarding differ from standard forwarding? How does a stub zone differ from a secondary zone? How do conditional forwarders differ from stub zones? What records are copied to the zone when you create a stub zone? Why isn't a stub zone authoritative for the zone? Video/Demo Time 4.8.1 Stub Zones and Conditional Forwarding 10:05 4.8.2 Configuring Forwarding and Stub Zones 11:16 Total 21:21 ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 43 Lab/Activity Configure a Stub Zone Configure Conditional Forwarding Number of Exam Questions 4 questions Total Time About 35 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 44 Section 4.9: Root Hints and Root Zone Summary This section provides an overview of root hints and the root zone. Students will learn how to: Configure or delete a root zone. Configure other DNS servers to point to your server via root hints. Configuring Server 2008 Network Infrastructure Objectives 201. Configure a Domain Name System (DNS) server. o Root hints Lecture Focus Questions: Why would you want to create a zone named . (dot)? What is the purpose of the root hints file? Why would you delete the root hints? What is the name and location(s) of the root hints file on a Windows 2008 server? Video/Demo 4.9.1 Root Hints Time 4:26 Lab/Activity Configure Root Hints Create a Root Zone Number of Exam Questions 5 questions Total Time About 20 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 45 Section 4.10: Zone Delegation Summary This section explores using zone delegation to divide DNS namespace into separate zones. Students will learn how to: Manage zones through delegation. Configuring Server 2008 Network Infrastructure Objectives 202. Configure DNS zones. o Zone delegation Lecture Focus Questions: Why might you decide to use zone delegation? What does a delegation identify? What records are created when you delegate a domain? Video/Demo Time 4.10.1 DNS Zone Delegation 5:12 4.10.2 Delegating a Domain 5:21 Total 10:33 Lab/Activity Delegate Domains Create a Delegated Zone Number of Exam Questions 1 question Total Time About 20 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 46 Section 4.11: DNS Features Summary This section discusses the following DNS features: Aging and Scavenging Methods for performing load balancing through DNS: o DNS Round Robin o Netmask Ordering o Record Weighting o Network Load Balancing (NLB) Windows Server 2008 R2 command-line tools Students will learn how to: Configure DNS Round Robin. Manage DNS from the command line. Configuring Server 2008 Network Infrastructure Objectives 202. Configure DNS zones. o Zone scavenging 204. Configure DNS replication. o Round robin Lecture Focus Questions: How do stale records affect DNS server performance? How does the no-refresh interval affect scavenging? When is a DNS record considered stale? What is the difference between DNS Round Robin and Network Load Balancing? How does convergence make NLB a dynamic solution? Video/Demo Time 4.11.1 DNS Refresh and Scavenging 2:58 4.11.3 DNS Round Robin 3:23 4.11.6 DNS Command-line Tools Total 12:21 18:42 ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 47 Lab/Activity Configure DNS Round Robin Number of Exam Questions 9 questions Total Time About 35 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 48 Section 4.12: New DNS Features Summary This section discusses new features for Windows Server 2008 and Windows 2008 R2: Link-Local Multicast Name Resolution (LLMNR) Background zone loading IPv6 DNS Support Read-only Domain Controller (RODC) GlobalNames Zone Global Query block List Conditional Forwarding Domain controller search DNSSEC Devolution Cache Locking Socket Pool Auditing Students will learn how to: Configure DNS Devolution. Configure DNS Cache Locking. Configure DNS Socket Pools. Configuring Server 2008 Network Infrastructure Objectives 201. Configure a Domain Name System (DNS) server. o Conditional forwarding o Socket pooling o Cache locking 202. Configure DNS zones. o GlobalNames o DNS Security Extensions (DNSSEC) 205. Configure name resolution for client computers. o Link-Local Multicast Name Resolution (LLMNR) o DNS devolution ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 49 Lecture Focus Questions: How does background loading have a positive effect on name resolution? How can you ensure that a DNS response is from a valid server? How does DNS Devolution simplify name resolution? How can you defend against cache poisoning attacks? What is the effect of enabling cache locking on Dynamic DNS? What advantage is to be gained by using a larger DNS socket pool? Video/Demo Time 4.12.1 New 2008 DNS Features 4:11 4.12.2 DNS Devolution 3:46 4.12.3 Configuring DNS Devolution 4:16 4.12.4 Cache Locking and Socket Pools 3:06 4.12.5 Configuring DNS Cache Locking 5:47 4.12.6 Configuring Socket Pool 3:12 4.12.7 DNS Security (DNSSec) 4:36 Total 28:54 Number of Exam Questions 10 questions Total Time About 45 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 50 Section 4.13: Single-label Name Resolution Summary In this section students will learn how to configure a GlobalNames zone. Details include: Strategies to provide single-label name resolution: o GlobalNames zone o Link-Local Multicast Name Resolution (LLMNR) o HOSTS file Managing the GlobalNames zone Students will learn how to: Enable GlobalNames zone support. Create a GlobalNames zone and add CNAME records to support singlelabel name resolution. Configuring Server 2008 Network Infrastructure Objectives 202. Configure DNS zones. o GlobalNames 205. Configure name resolution for client computers o Configuring HOSTS file o Link-Local Multicast Name Resolution (LLMNR) Lecture Focus Questions: When would you use the GlobalNames zone? What type of records do you create in the GlobalNames zone? How can you extend the GlobalNames zone across multiple forests? Which strategies can you use to provide single-label name resolution for IPv6 hosts? When will a Windows client use LLMNR? What limitations does relying on LLMNR have? Video/Demo Time 4.13.1 GlobalNames Zones and LLMNR 2:06 4.13.2 Configuring the GlobalNames Zone 8:50 Total 10:56 ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 51 Lab/Activity Configure a GlobalNames Zone Number of Exam Questions 8 questions Total Time About 25 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 52 Section 4.14: DNS Design Summary In this section students will learn the strategies and goals for designing DNS namespace. They will also learn a variety of configuration options to use and security considerations when designing a DNS solution. Details include: The goals of Namespace design: o Allow internal users to access internal resources. o Allow external users to access external resources. o Allow internal users to access external public resources. o Prevent external users from accessing internal resources. Methods to accomplish these goals: o Same internal and external domain name o Different internal and external domain names o External domain name with an internal subdomain DNS configuration options: o Primary zone o Secondary zone o Reverse lookup zone o Active Directory-integrated zone o Caching-only server o Zone delegation o Forwarders o Conditional forwarding o Stub zone o Root zone o Root hints o Dynamic DNS o WINS-integrated zone o GlobalNames zone o Link-Local Multicast Name Resolution (LLMNR) o HOSTS file Goals for designing security for DNS Methods to improve DNS security Configuring Server 2008 Network Infrastructure Objectives 201. Configure a Domain Name System (DNS) server. o Conditional forwarding o Root hints o Cache-only 202. Configure DNS zones. o Zone types ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 53 o Active Directory integration o Dynamic Domain Name System (DDNS) o GlobalNames o Zone delegation o Reverse lookup zones 204. Configure DNS replication. o DNS stub zones o Securing zone transfer 205. Configure name resolution for client computers o Link-Local Multicast Name Resolution (LLMNR) Lecture Focus Questions: When using internal and external DNS, what are the three possible scenarios for the DNS namespace? What are the advantages and disadvantages of each of the three methods? What are the goals of any split namespace design? When should you use conditional forwarding instead of a standard forward? When should you use a WINS server instead of configuring a GlobalNames zone? How do Active Directory-integrated zones improve security and fault tolerance of DNS data? What type of zones should you use on DNS servers exposed to the public network? Video/Demo 4.14.1 DNS Namespace Design Time 7:40 Number of Exam Questions 2 questions Total Time About 20 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 54 Section 5.1: Routing Summary In this section students will become familiar with routing concepts and the commands to manage routing table entries. Details include: NPAS includes the following role services: o Network Policy Server (NPS) o Remote Access Service o Routing o Health Registration Authority (HRA) o Host Credential Authorization Protocol (HCAP) Routing terminology: o Router o Static Route o Route metric o Default route o Persistent route Commands to manage routing table entries Multicast routing details Students will learn how to: Install the RRAS components of the Network Policy and Access services. Add and modify IPv4 and IPv6 routes through the command line or GUI. Configuring Server 2008 Network Infrastructure Objectives 103. Configure Routing. o Static routing o Choosing a default gateway Lecture Focus Questions: Which role do you install on a Windows Server 2008 server to get the routing component? What is the purpose of a default route? Under what circumstances can you most effectively use static routes? What is the route add switch that allows you to make a route permanent? What routes are automatically added to the routing table when routing is enabled? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 55 Video/Demo 5.1.2 Routing Concepts 5.1.3 Installing Routing and Remote Access 5.1.4 Configuring Static Routes Total Time 10:27 2:07 13:52 26:26 Lab/Activity Enable LAN Routing Add Static Routes Number of Exam Questions 10 questions Total Time About 50 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 56 Section 5.2: RIP Summary This section provides an overview of RIP dynamic routing protocols. Details include: Key features of RIP that can be configured: o Packet protocol o Authentication o Route Filters o Neighbors o Timers o Clean-up updates o VLSM support Students will learn how to: Configure RIP by adding the RIP protocol and adding interfaces to run RIP. Configure RIP sending and receiving protocols, filters, and neighbor lists. Configuring Server 2008 Network Infrastructure Objectives 103. Configure Routing. o Routing Internet protocol (RIP) o Maintaining a routing table Lecture Focus Questions: What is the difference between static and dynamic routing? What routing protocols does Windows Server 2008 support? What is the difference between RIP version 2 and RIP? Why has RIP version 2 become the standard? What is Silent RIP and how does it affect learning and sharing routes? What affect does configuring neighbors have on RIP broadcasts and multicasts? What is route summarization? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 57 Video/Demo Time 5.2.1 Dynamic Routing 4:20 5.2.2 Configuring RIP 3:16 Total 7:36 Lab/Activity Configure RIP Routing Number of Exam Questions 9 questions Total Time About 25 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 58 Section 5.3: Demand-dial Routing Summary This section discusses the processes to establish demand-dial routing to connect two networks through a link that is available on demand. Details include: The process to establish a demand-dial link Details about using demand-dial connections Features of demand-dial routing: o Demand-dial filters o Packet filters o Auto-static routing Configuring and enabling demand-dial routing Students will learn how to: Use the Routing and Remote Access wizard to configure demand-dial routing. Configure auto-static routing for RIP. Configuring Server 2008 Network Infrastructure Objectives 103. Configure Routing. o Demand-dial routing 301 Configure remote access. o Packet filters Lecture Focus Questions: How is a demand-dial link established? What is the difference between dial-in and dial-out credentials? How do demand-dial filters differ from packet filters? Which filter type would you configure to prevent a specific traffic type from using a demand-dial link? Why is auto-static routing important when using demand-dial routing? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 59 Video/Demo Time 5.3.1 Demand-dial Routing 4:17 5.3.2 Configuring Demand-dial Routing 6:59 Total 11:16 Lab/Activity Configure Demand Dial Routing Configure Auto-static Routing Number of Exam Questions 5 questions Total Time About 30 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 60 Section 5.4: ICS and NAT Summary In this section students will learn the basics of using Internet Connection Sharing (ICS) and Network Address Translation (NAT) to share an Internet connection with an internal private network. NAT allows you to connect a private network to the Internet without obtaining registered addresses for every host. Configuring NAT Students will learn how to: Configure a server as a NAT router. Configure a NAT router to provide DHCP and DNS proxy services. Configure address and port mappings in NAT. Configuring Server 2008 Network Infrastructure Objectives 301. Configure remote access. o Network Address Translation (NAT) Lecture Focus Questions: What does a NAT router do? What are the address ranges you can use when you deploy NAT? How can NAT provide security for a private network? What changes take place automatically to the TCP/IP settings when you enable ICS on an interface? What are the limitations of using ICS over NAT? When would ICS be a good choice? When must you use NAT instead of ICS? Video/Demo Time 5.4.1 ICS and NAT 6:18 5.4.2 Configuring NAT 6:26 Total 12:44 ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 61 Lab/Activity Configure NAT Number of Exam Questions 3 questions Total Time About 25 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 62 Section 6.1: Remote Access Concepts Summary Students will learn concepts of the Remote Access process. Details include: Remote access connections o Point-to-point (PPP) for a dial-up connection o Virtual Private Network (VPN) use a tunneling protocol that wraps and protect packets in transit o VPN protocols supported by Windows Server 2008 and Vista Point-to-Point Tunneling Protocol (PPTP) Layer Two Tunneling Protocol (L2TP) Secure Socket Tunneling Protocol (SSTP) Authentication protocols: o Password Authentication Protocol (PAP) o Challenge Handshake Authentication Protocol (CHAP) o Microsoft Challenge Handshake Authentication Protocol version 2 (MS-CHAP v2) o Extensible Authentication Protocol-Transport Layer Security (EAPTLS) The role of remote access authorization Remote access is allowed or denied based on components of network policies: o Conditions o Constraints o Permissions o Settings Configuring Server 2008 Network Infrastructure Objectives 301. Configure remote access. o Remote Access Policy o VPN protocols such as Secure Socket Tunneling Protocol (SSTP) and IKEv2 o RAS authentication by using MS-CHAP, MS-CHAPv2, EAP Lecture Focus Questions: Which VPN protocols does Windows Server 2008 support? Which authentication protocols support smart card use? What makes CHAP vulnerable to security breaches? What is the difference between authorization and authentication? What is the server's response to a connection that doesn't match the conditions for a policy? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 63 What is the difference between constraints and conditions? How are they similar? What happens to a connection that matches the policy conditions but not the policy constraints? How many other policies will be checked in this scenario? Where does the server find the permissions for a connection? What must occur before settings are applied? Video/Demo Time 6.1.1 Remote Access Connections 3:35 6.1.3 Remote Access Authentication 4:39 6.1.5 Remote Access Authorization 2:59 Total 11:13 Number of Exam Questions 5 questions Total Time About 25 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 64 Section 6.2: Dial-up and VPN Summary This section explores configuring a Remote Access server to use Dial-up and VPN connections. Details include: Configuration tasks on the server to allow a remote client to connect to a remote access server: o Enable remote access o Configure ports o Configure addressing o Configure network policies Comparison of configuration settings for dial-up and VPN client connections: o General tab o Options tab o Security tab o Networking tab o Sharing tab Students will learn how to: Enable remote access on a Windows Server 2008 server. Configure VPN ports on a server. Control remote access by configuring network access policies. Create a client dial-up connection. Configure a client VPN connection. Configuring Server 2008 Network Infrastructure Objectives 301. Configure remote access. o Dial-up o VPN reconnect Lecture Focus Questions: Which setting must you configure in Routing and Remote Access to allow remote clients to access the private network, and not just the resources on the remote access server? What object in Routing and Remote Access identifies a logical connection to the remote access server? What are the ways that you can configure a remote access client to get an address for the remote access connection? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 65 What role do network policies play when you configure the remote access server? How do network policy constraints differ from conditions? When would you use the same setting in a constraint instead of a condition? Why does the policy application order affect whether or not clients can connect to a remote access server? When viewing the properties of a network connection, when will the Sharing tab be visible? Video/Demo 6.2.1 Configuring a Remote Access Server 6.2.9 Creating Client Connections Total Time 14:52 9:57 24:49 Lab/Activity Configure a Remote Access Server Reconfigure a Server for Remote Access Configure a VPN Server Configure VPN Ports Create a Network Access Policy 1 Create a Network Access Policy 2 Number of Exam Questions 11 questions Total Time About 75 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 66 Section 6.3: SSTP Summary This section examines using Secure Socket Tunneling Protocol (SSTP) to establish a VPN connection. Details include: SSTP features SSTP client requirements SSTP server requirements Students will learn how to: Request a server certificate for SSTP. Configure a remote access server to allow SSTP connections. Configure a VPN connection on a client computer to use SSTP. Configuring Server 2008 Network Infrastructure Objectives 301. Configure remote access. o VPN protocols such as Secure Socket Tunneling protocol (SSTP) and IKEv2 Lecture Focus Questions: What advantages does using SSTP have over using either PPTP or L2TP for a VPN connection? What ports must you open in a firewall to allow SSTP? How can you ensure that the SSTP client trusts the SSTP server certificate? What client and server operating systems support SSTP? Video/Demo Time 6.3.1 SSTP 1:56 6.3.2 Configuring SSTP 5:56 Total 7:52 ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 67 Number of Exam Questions 2 questions Total Time About 10 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 68 Section 6.4: CMAK Summary This section provides an overview of how the Connection Manager Administration Kit (CMAK) is used to manage remote access for larger deployments. Connection Manager is used to configure client remote access connections. Connection settings are stored in profiles for either VPN or dial-up connections. Details include: Components of the Connection Manager: o Connection Manager Administration Kit (CMAK) o Connection Point Services Configuring Server 2008 Network Infrastructure Objectives 301. Configure remote access. o Connection Manager Lecture Focus Questions: What permissions do you need to create a profile? How do profiles facilitate remote access connection configuration deployment? What methods can you use to distribute profiles to clients? What does a phone book tell clients? Video/Demo 6.4.1 Connection Manager Administration Kit (CMAK) Time 1:15 Number of Exam Questions 2 questions Total Time About 5 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 69 Section 7.1: Network Location Profiles Summary This section provides a summary of using network location profiles to identify network connection types. Details include: Network profile types: o Domain o Public o Private Configuring profile settings manually Enforcing profile settings Students will learn how to: Change the location type on a client computer. Configure Network List Manager Policies to control client network connections profiles. Configuring Server 2008 Network Infrastructure Objectives 104. Configure Windows Firewall with Advanced Security. o Configure firewall by using Group Policy o Network location profiles Lecture Focus Questions: What are the characteristics of a Public network? Why is network discovery disabled for the Public profile? What are the firewall and antivirus software recommendations for the Private profile? How are security settings controlled in the Domain profile? What can you control through the All Networks policy? Video/Demo Time 7.1.1 Network Location Profiles 1:31 7.1.2 Configuring Network List Manager Policies 6:00 Total 7:31 Total Time About 10 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 70 Section 7.2: RADIUS Summary This section discusses using Remote Authentication Dial-In User Service (RADIUS) to consolidate network policies for multiple servers to authenticate remote access clients. Details include: Components of a RADIUS solution: o Remote access clients o RADIUS client o RADIUS server o RADIUS proxy o Remote RADIUS server group o Network policies o Connection request policies o RADIUS Accounting o NPS templates o User account databases o RADIUS messages Configuring the components to configure a RADIUS solution: o RADIUS server o RADIUS client o Remote access client o RDIUS proxy o RADIUS accounting Best practices for configuring NPS for RADIUS Students will learn how to: Configure a remote access server as a RADIUS client. Configure a RADIUS server. Configure a RADIUS proxy by configuring Remote RADIUS Server groups and Connection Request policies. Configuring Server 2008 Network Infrastructure Objectives 301. Configure remote access. 304. Configure Network Policy Server (NPS) o RADIUS accounting o Connection Request policies o RADIUS proxy o NPS templates ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 71 Lecture Focus Questions: When using a RADIUS solution, where are network access policies configured? What is the difference between a RADIUS client and a remote access client? Why would you implement a RADIUS proxy? What is the difference between a RADIUS client and a RADIUS proxy? What is the difference between a connection request policy and a network access policy? How does the RADIUS proxy use the remote RADIUS server group when processing authentication requests? Video/Demo Time 7.2.1 RADIUS 3:57 7.2.2 Installing the NPS Role 2:08 7.2.3 Configuring RADIUS 6:25 Total 12:30 Lab/Activity Configure a RADIUS Server Configure a RADIUS Client Configure a RADIUS Proxy Number of Exam Questions 9 questions Total Time About 40 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 72 Section 7.3: Network Access Protection (NAP) Summary This section examines how NAP can be used to regulate network access or communication based on a computer’s compliance with health requirement policies. Details include: Features of NAP o Health state validation o Health policy compliance o Limited access network Components that comprise the NAP system: o NAP Client o NAP Server o Enforcement Server (ES) o Remediation Server Configuring NAP requires: o Configuring the NAP server o Configuring the client computer o Configuring the following enforcement points: DHCP VPN 802.1x Remote Desktop Gateway IPsec Students will learn how to: Configure a DHCP server as an enforcement point. Configure SHV settings, remediation server groups, health policies, and network policies for NAP. Enable NAP enforcement on a client computer. Configuring Server 2008 Network Infrastructure Objectives 302. Configure Network Access Protection (NAP). o DHCP enforcement o VPN enforcement o Configure NAP health policies o IPsec enforcement o Multi-configuration System Health Validator (SHV) ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 73 Lecture Focus Questions: Why is a non-compliant computer not necessarily an immediate security threat? What happens to a computer that receives a limited access health state validation? What functions are performed by the System Health Validator (SHV)? Which NAP component do you modify to identify the health checks that should be performed? How do remediation servers and auto-remediation help clients become compliant? Which enforcement method uses Connection Authorization Policies? Which one uses Connection Request Policies? Which one uses a Health Registration Authority (HRA)? What type of communication occurs in the boundary network when using IPsec enforcement? Video/Demo 7.3.1 Network Access Protection (NAP) Time 4:53 7.3.3 Configuring DHCP Enforcement 15:56 7.3.4 Configuring VPN Enforcement 13:03 7.3.5 NAP Enforcement Configuration Total 8:16 42:08 Number of Exam Questions 17 questions Total Time About 65 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 74 Section 7.4: Network Authentication Summary In this section students will learn network authentication mechanisms for logging on to the server or domain. Details include: Kerberos authentication and authorization NTLM authentication and authorization Conditions of when to use different authentication methods: o Kerberos o NTLM v2 o NTLM or LM Best practices regarding configuring domain authentication Kerberos policy settings: o Enforce user logon restrictions o Maximum lifetime for service ticket o Maximum lifetime for user ticket o Maximum lifetime for user ticket renewal o Maximum tolerance for computer clock synchronization Students will learn how to: Configure Group Policy to enforce the use of NTLMv2 for authentication. Lecture Focus Questions: What advantages does Kerberos have over NTLM? What disadvantages does it have compared to NTLM? What are the conditions for running NTLMv2? When can you deploy Kerberos? When should you use NTLM instead of NTLMv2? Video/Demo Time 7.4.1 LAN Authentication 1:49 7.4.2 Configuring LAN Authentication 2:41 Total 4:30 Lab/Activity Enforce NTLM v2 ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 75 Number of Exam Questions 1 question Total Time About 15 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 76 Section 7.5: Firewall Summary This section discusses the specifics of managing a firewall. Details include: Tools you can use to manage the firewall: o Windows Firewall (in Control Panel) o Windows Firewall with Advanced Security Features of Windows Firewall with Advanced Security: o Profiles o Firewall rules o Connection security rules o Monitoring o Policies Use Window Firewall with Advanced Security to create the following types of inbound and outbound rules: o Program rule o Port rule o Predefined rule o Custom rule Types of connection security rules: o Isolation o Authentication exemption o Server-to-server o Tunnel o Custom Action options that apply to the traffic which meet the rule’s conditions: o Allow the connection o Block the connection o Allow the connection if it is secure Options that can be configured for network profiles: o Firewall state o Inbound connections o Outbound connections Tips for managing firewall settings Port numbers for common services Students will learn how to: Use the Basic Firewall to allow traffic based on port, protocol, or application. Use the Windows Firewall with Advanced Security to manage custom firewall rules. Use Group Policy to enforce firewall rules. ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 77 Configuring Server 2008 Network Infrastructure Objectives 104. Configure Windows Firewall with Advanced Security. o Inbound and outbound rules o Custom rules o Authorized users o Authorized computers o Configure firewall by using Group Policy o Network location policies o Isolation policy o Connection security rules Lecture Focus Questions: When must you use the Advanced Firewall instead of the Basic Firewall? When would you configure a custom exception? What does the exception scope do? What are the components of a policy? Why should you allow traffic based on application instead of port when possible? How can a policy help you maintain security integrity in your network? Video/Demo 7.5.1 Windows Firewall 7.5.3 Configuring Windows Firewall with Advanced Security 7.5.4 Configuring Firewall GPO Settings Total Time 4:04 14:07 2:39 20:50 Number of Exam Questions 11 questions Total Time About 40 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 78 Section 7.6: IPsec Summary This section provides the details of how Internet Protocol Security (IPsec) protects IP packets during transmission. Details include: IPsec protocols: o Authentication Header (AH) o Encapsulating Security Payload (ESP) o Internet Key Exchange (IKE) o Authenticated IP (AuthIP) Phases to establish the IPsec connection: o Phase 1 (Main Mode) o Phase 2 (Quick Mode) Protocols supported for configuring IPsec: o Integrity: SHA1 MD5 o Encryption: AES-256 AES-192 AES-128 3DES (Triple-DES) DES o Key exchange: Elliptic Curve Diffie-Hellman P-384 Elliptic Curve Diffie-Hellman P-256 Diffie-Hellman Group 14 Diffie-Hellman Group 2 Diffie-Hellman Group 1 Authentication: o Kerberos o NTLMv2 o Computer certificates, including health certificates o Preshared key Configuring IPsec through Windows Firewall with Advanced Security console Students will learn how to: Configure connection security rules by determining the rule type, requirements, authentication method, and profile(s) to which the rule applies. Monitor connection security rules and security associations. ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 79 Configuring Server 2008 Network Infrastructure Objectives 104. Configure IPsec. o IPsec group policy Lecture Focus Questions: Under which circumstances should you not use Authentication Header (AH)? What additional services does Encapsulating Security Payload (ESP) provide over AH? What is the difference between data integrity and data confidentiality? What method is used to provide data integrity? What method provides confidentiality? What enhancements does AuthIP provide over IKE? What are the requirements for using AuthIP? What are the phases of an IPsec connection? What does the key lifetime affect? What function is performed by the Diffie-Hellman protocol? Video/Demo Time 7.6.1 IPsec 6:14 7.6.3 IPsec Connection Security Rules 3:13 7.6.4 Configuring IPsec 7:17 7.6.6 IPsec Improvements 3:16 Total 20:00 Number of Exam Questions 10 questions Total Time About 40 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 80 Section 7.7: DirectAccess Summary This section discusses using DirectAccess as an automatic connectivity solution. Details include: A comparison of a VPN solution to a DirectAccess solution The support that DirectAccess provides DirectAccess connection methods: o Full enterprise network access (end-to-edge) o Selected server access (modified end-to-edge) o End-to-end The process that the DirectAccess client uses to connect to intranet resources DirectAccess requirements for the: o Infrastructure o Server o Client Configuration details for DirectAccess components: o Server o Client side Configuring Server 2008 Network Infrastructure Objectives 303. Configure DirectAccess. o IPv6 o IPsec o Server requirements o Client requirements Lecture Focus Questions: What are the advantages of using DirectAccess to access corporate file servers? What is the difference between full enterprise network access and selected server access? What are the requirements for a DirectAccess server? How does the client's IP address configuration affect how the client sends traffic to the DirectAccess server? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 81 Video/Demo 7.7.1 DirectAccess Time 9:00 Number of Exam Questions 13 questions Time About 30 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 82 Section 8.1: File Services Summary This section explores installing the File Services role to manage network file sharing. When installing the File Services role, the following role services are available to choose from: o File Server o Distributed File System (DFS) o File Server Resource Manager (FSRM) o Services for Network File System (NFS) o Windows Search Service o Windows Server 2003 File Services o BranchCache for network files Managing file services on the server includes the following features and options: o NTFS permissions o NTFS quotas o Shadow copies o Server Backup (added as a server feature) o Storage Manager for SANs (added as a server feature) Configuring Server 2008 Network Infrastructure Objectives 401. Configure a file server. o File share publishing o Branch Cache o NTFS permissions Lecture Focus Questions: What features are provided by File Server Resource Manager (FSRM)? What does file screening allow you to do? When might you use Services for Network File System (NFS)? What role service would you add to allow replication for DFS with nonWindows Server 2008 servers? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 83 Video/Demo 8.1.1 Installing the File Services Role Time 3:01 Number of Exam Questions 1 question Total Time About 5 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 84 Section 8.2: File Shares Summary This section discusses creating and managing shared folders. Details include: Tools to create or manage shared folders: o Windows Explorer o Shared Folder snap-in o Share and Store Management snap-in o Command line A comparison of shared folder permissions and roles Facts about shared folders Students will learn how to: Configure and manage shared folders and files. Restrict share access through share permissions and user limits. Configuring Server 2008 Network Infrastructure Objectives 401. Configure a file server. o File share publishing o Share permissions o NTFS permissions o Access-based Enumeration (ABE) o Share and Storage Management console Lecture Focus Questions: What permissions do you need to share a folder or configure share permissions? What is the difference between the read permission and the change permission? How does using access-based enumeration on shared folders modify what users can see? What tools are available to you to create and manage shares? What is the effect of appending $ to a share name? What shared folder features can you manage in the Share and Storage Management console vs. the Shared Folder snap-in? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 85 Video/Demo 8.2.1 File Share Concepts 8.2.2 Sharing Folders 8.2.3 Using Share and Storage Management Console Total Time 4:19 11:05 4:47 20:11 Lab/Activity Share a Folder with a Second Name Remove a Shared Folder Number of Exam Questions 7 questions Total Time About 40 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 86 Section 8.3: Offline Files Summary This section provides information about using offline files to work with documents in shared folders even when the user is not connected to the network. Students will learn how to: Configure caching options for offline files, including automatic caching of files and caching of applications. Configure offline availability on the client. Manage synchronization settings through the Sync Center. Configuring Server 2008 Network Infrastructure Objectives 401. Configure a file server. o Offline Files Lecture Focus Questions: How does the offline files feature ease file management for mobile users? What happens to NTFS permissions on cached copies of files? How does synchronization affect files? What steps can you take to reconcile synchronization conflicts? What is the result of encrypting the offline files cache with the user key? What security vulnerability does this resolve? Video/Demo 8.3.1 Enabling Offline Files Time 12:54 Lab/Activity Enable Share Caching Disable Share Caching Number of Exam Questions 1 question Total Time About 25 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 87 Section 8.4: NTFS Permissions Summary This section explores using NTFS permissions to control access to folders and files on an NTFS partition. Details include: Permissions for folders and files: o Read o Write o List Folder Contents o Read & Execute o Modify o Full Control Special permissions How file ownership affects access and assigning permissions The effects of copying or moving files with NTFS permissions Effective permissions are the sum of all permissions from the following sources: o Explicit assignment o Group membership o Inheritance Examples of effective NTFS permissions Suggestions for planning NTFS permissions Students will learn how to: Configure NTFS permissions. Copy, remove, and modify inherited permissions. Identify the effective permissions a user has to a file or folder. Change file or folder ownership. Configuring Server 2008 Network Infrastructure Objectives 401. Configure a file server. o NTFS permissions Lecture Focus Questions: When do NTFS permissions apply? What are the differences between the NTFS Full Control permission and the Modify permission? Which permission assignment overrides all other permission assignments? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 88 What is the advantage of the Take Ownership right? When can you use this right to the greatest effect? What happens to permissions when a file with NTFS permissions is moved to a non-NTFS partition? How might a user end up with more NTFS permissions to a folder than what appear on the access control list for that user? How can you prevent a member of a group from getting the NTFS permissions assigned to the group without removing the user from the group? Video/Demo 8.4.1 NTFS Permissions 8.4.2 Configuring NTFS Permissions Total Time 6:07 13:11 19:18 Lab/Activity Configure NTFS Permissions Remove Inherited Permissions Number of Exam Questions 3 questions Total Time About 40 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 89 Section 8.5: Share and NTFS Permissions Summary In this section students will learn how share permissions and NTFS permissions work together to control access. Students will learn how to: Configure combined NTFS and share permissions. Configuring Server 2008 Network Infrastructure Objectives 401. Configure a file server. o Share permissions o NTFS permissions Lecture Focus Questions: What are the differences and similarities between NTFS permissions and share permissions? What strategy can you use to combine NTFS and share permissions? Why should you assign permissions to groups rather than users? How do logged on users get updated permissions? Video/Demo 8.5.1 Share and NTFS Permissions Time 4:51 Lab/Activity Configure Share Permissions Configure NTFS and Share Permissions 1 Configure NTFS and Share Permissions 2 Number of Exam Questions 5 questions Total Time About 25 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 90 Section 8.6: EFS Summary This section discusses using Encrypting File System (EFS) to encrypt a file or folder. Details include: Operating systems in which EFS is available: o Windows Server 2008 o Windows Vista Business o Windows Vista Enterprise o Windows Vista Ultimate Requirements to encrypt a file or folder: o Must have Write permissions to a file or folder o Cannot encrypt System or Read-only files o Cannot encrypt and compress a file or folder at the same time Users who can open an encrypted file: o The user who originally encrypted the file o Additional users who have been designated as additional users o Designated recovery agents (DRAs) Implementing encryption Recovering encrypted files Moving or copying encrypted files Enforcing encryption settings for offline files Rules to determine the encrypted state of a file Tips when saving encrypted files on a remote computer Students will learn how to: Encrypt or decrypt a file or folder. Add authorized users to allow encrypted file access. Designate DRAs for file recovery. Configure EFS settings in Group Policy. Configuring Server 2008 Network Infrastructure Objectives 401. Configure a file server. o Encrypting file system (EFS) Lecture Focus Questions: What is the importance of the DRA in the encryption process? Which users have access to encrypted files and folders? What is the relationship between encryption and compression? What is the significance of encrypting the pagefile? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 91 How does Rekeywiz affect your encryption deployment? Video/Demo 8.6.1 EFS 8.6.2 Managing Encrypted Files Total Time 4:27 13:24 17:51 Lab/Activity Encrypt a Folder Number of Exam Questions 7 questions Total Time About 35 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 92 Section 8.7: BitLocker Summary This section examines using BitLocker to protect unauthorized data access on lost or stole laptops or other compromised system. Details include: The role of BitLocker Components of BitLocker o BitLocker partition o Trusted Platform Module (TPM) o USB device o BIOS support How BitLocker differs from the EFS BitLocker configuration involves creating the following security components: o TPM owner password o Recovery key o PIN o Startup key o Data volume key o Data Recovery Agent BitLocker modes which determine the security level: o TPM-only o TPM with startup key o TPM with PIN o TPM with PIN and startup key o Without a TPM Configuring and managing BitLocker Students will learn how to: Generate recovery keys and create a BitLocker DRA. Configure BitLocker to implement BitLocker without a TPM. Configure BitLocker To Go to deny write access to unauthorized USB flash devices. Configuring Server 2008 Network Infrastructure Objectives 401. Configure a file server. o BitLocker ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 93 Lecture Focus Questions: What is the difference between suspending protection and decrypting the drive? When implementing BitLocker, why is it a good idea to run a system check before encrypting the drive? What is the difference in function between BitLocker and BitLocker To Go? When using BitLocker what are the requirements of the Trusted Platform Module? How can you implement BitLocker without a TPM? What will happen when BitLocker is enabled but then you lose the USB flash device which holds the key? Video/Demo Time 8.7.1 BitLocker 4:54 8.7.3 BitLocker Configuration 4:27 8.7.4 Implementing BitLocker without a TPM 4:25 8.7.5 Configuring BitLocker Recovery Agents 4:08 Total 17:54 Number of Exam Questions 12 questions Total Time About 40 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 94 Section 8.8: BranchCache Summary This section discusses using BranchCache to store content in remote location so that users in branch offices can access information more quickly. Details include: The role of BranchCache BranchCache operates in one of the following modes: o Hosted Cache o Distributed Cache Configuration of BranchCache: o Content server o Hosted cache server o Distributed cache mode Configuring BranchCache clients Tools to configure BranchCache on branch office client computers: o Netsh o Group Policy o Windows Firewall with Advance Security Students will learn how to: Configure BranchCache clients. Install and configure a BranchCache content server. Install and configure a BranchCache hosted cache server. Configuring Server 2008 Network Infrastructure Objectives 401. Configure a file server o BranchCache Lecture Focus Questions: Under which circumstances should you enable distributed cache mode versus hosted cache mode? How does BranchCache treat traffic while in transit? When would you choose to configure BranchCache using Group Policy rather than netsh? When BranchCache settings have been configured using both the netsh command and Group Policy, which settings take precedence? Why does a hosted cache server need an enrolled server certificate from a trusted CA? What is the difference between the BranchCache feature and the BranchCache for network files role service? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 95 Video/Demo Time 8.8.1 BranchCache 4:56 8.8.3 BranchCache Configuration 6:48 8.8.4 Configuring BranchCache 2:25 Total 14:09 Number of Exam Questions 11 questions Total Time About 35 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 96 Section 8.9: Distributed File System (DFS) Summary This section explores using DFS to logically organize shared folders on multiple servers into a single logical folder hierarchy called a namespace. Details include: DFS includes the following namespace components: o Namespace o Namespace server o Namespace root o Folder Components to control replication o Replication group o Replicated folder o Connection DFS configuration Types of namespace: o Stand-alone o Domain-based Configuring a Replication Group Students will learn how to: Create stand-alone or domain-based DFS namespaces. Add folders and folder targets to a namespace. Configure DFS replication by creating replication groups and replicated folders. Configuring Server 2008 Network Infrastructure Objectives 402. Configure Distributed File System (DFS). o DFS namespace o DFS configuration and application o Creating and configuring targets o DFS replication o Read-only replicated folder o Failover cluster support o Health reporting Lecture Focus Questions: What is the advantage of a domain-based namespace over a stand-alone namespace? What is the role of a namespace server? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 97 How can you achieve fault tolerance using DFS? What role do connections play in DFS replication? When can you add a failover cluster to a DFS replication group? How can you prevent users from adding or change files in a replicated folder? How can hides files and folders that users do not have permission to access? Video/Demo Time 8.9.1 DFS 7:23 8.9.2 New DFS Features 4:51 8.9.4 Enabling DFS 9:17 8.9.5 Configuring DFS Read-Only Replicated Folders and Access Based Enumeration 3:49 Total 25:20 Lab/Activity Create a DFS Structure Number of Exam Questions 11 questions Total Time About 50 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 98 Section 8.10: Shadow Copy Summary This section covers using shadow copy to make copies of files at regular intervals. This allows you to take a snapshot of files and shared folders which can be used at a later date to recover previous versions of a file or recover a deleted file. Details include: Facts about using shadow copies Recommendations for using shadow copies Students will learn how to: Enable shadow copies on a volume. Configure shadow copy settings, including storage location, size, and schedule. Create snapshots. Save, copy, or restore previous versions of files. Configuring Server 2008 Network Infrastructure Objectives 403. Configure shadow copy services. o Restoring data o Shadow copy services Lecture Focus Questions: How much disk space do shadow copies take by default? What is the maximum number of shadow copies the system stores? What happens when the system reaches this limit? What happens to NTFS permissions when you restore a file? When you copy a file? Why is it recommended that you place shadow copies on different volumes? How should client work patterns affect your shadow copies schedule? What is the relationship between shadow copies and regular backups? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 99 Video/Demo Time 8.10.1 Shadow Copy Services 3:09 8.10.2 Enabling Previous Versions 5:45 Total 8:54 Lab/Activity Enable Shadow Copies Number of Exam Questions 9 questions Total Time About 25 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 100 Section 8.11: Backup and Restore Summary In this section students will become familiar with Windows Server Backup which is used to provide backup and recovery for Windows Server 2008 and replaces NTbackkup.exe. Details include: Using Windows Server Backup Windows Server Backup provides three ways to run backups: o Windows Server Backup MMC snap-in o Wbadmin from the command line o PowerShell cmdlets for Windows Server Backup Volume options you can select for Windows Server Backup: o Full Server o Critical volumes/Bare metal recovery o System state o Individual volumes o Folders or file Storage type for Windows Server Backup: o Internal disk o External disk o Shared folder o DVD, other optical, or removable media Types of backups you can perform using Windows Server Backup: o Automatic backup o Manual backup o Scheduled backup o System state backup Tools to perform a system recovery: o Files and folders o Volumes o Applications o Backup catalog o Operating system or full server o System state Students will learn how to: Install the Windows Server Backup features. Configure a regular backup schedule. Configure and run a Backup Once backup operation. Restore a backup, restoring the full server, volume or selected folders and files. ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 101 Configuring Server 2008 Network Infrastructure Objectives 403. Configure backup and restore. o Backup types o Backup schedules o Managing remotely o Restoring data o Volume snapshot services (VSS) o Bare metal restore Lecture Focus Questions: Which backup storage device would you choose if you wanted to be able to restore individual folders or files? What storage types are available when using automatic backups? What happens to a local disk when you designate it for use by Windows Server Backup? How can you create automatic backups with a frequency less than once a day? Video/Demo Time 8.11.1 Server Backup 5:20 8.11.2 Using Windows Server Backup 7:22 8.11.3 Performing a Bare Metal Restore 5:42 Total 18:24 Lab/Activity Back Up a Server Number of Exam Questions 17 questions Total Time About 50 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 102 Section 8.12: Disk Quotas Summary This section examines using disk quotas to restrict the amount of disk space user’s files can use on an NTFS volume. Disk quotas are set up per volume and per user and cannot be configured using groups. Students will learn how to: Configure disk quotas and enforce quota limits. Add quota entry exceptions for specific users. Enable quota logging for warning levels. Configuring Server 2008 Network Infrastructure Objectives 404. Manage file server resources. o Quota by volume or quota by user o Quota entries Lecture Focus Questions: Are disk quotas configured on disks, volumes, folders, or files? What effect does compressing files have on the disk quota limit? What actions can be taken when a user exceeds the disk quota limit? How can you have a disk quota configured, but still allow users to exceed the quota limits? What conditions must be met before you can delete a disk quota entry? Which user is exempt from disk quotas? Video/Demo 8.12.1 Configuring Disk Quotas Time 2:40 Lab/Activity Enable Quota Restrictions Create a Quota Entry Modify Quota Limits ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 103 Number of Exam Questions 5 questions Total Time About 25 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 104 Section 8.13: FSRM Features Summary This section explores using the File Server Resource Manager (FSRM) snap-in to manage folder and volume quotas. Details include: FSRM features: o Quotas o Notifications o File Screening o Storage Reports o File Classification o File Management Methods for configuring quotas: o NTFS Disk Quotas o Folder and Volume Quotas Students will learn how to: Configure volume and folder quotas Create quota templates. Configure file screens and file screen exceptions. Create custom file groups. Generate FSRM reports for both quotas and overall file system use. Schedule FSRM reports. Assign file classification information to files. Create file management tasks. Configuring Server 2008 Network Infrastructure Objectives 404. Manage file server resources. o FSRM o Quota entries o Quota templates o File classification o File management tasks o File screening Lecture Focus Questions: What are the primary differences between disk quotas and quotas implemented through FSRM? How does a soft quota differ from a hard quota? How do quota templates facilitate quota management? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 105 What is the difference between a quota and a file screen? How is an active file screen more restrictive than a passive file screen? How can you automatically assign classification information to files? What can you accomplish with the file expiration task? Video/Demo Time 8.13.1 FSRM Quotas and File Screening 5:46 8.13.2 FSRM File Classifications and Management 6:06 8.13.3 Configuring FSRM Quotas and File Screening 8:57 8.13.4 Configuring FSRM File Classifications and Management 8:40 Total 29:29 Number of Exam Questions 15 questions Total Time About 50 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 106 Section 8.14: Print Services Summary In this section students will learn how to manage print services on a Windows Server 2008 system by installing the Print and Document Services role. Details include: Key definitions: o Print server o Printer o Print device o Print driver o Print queue o Printer port Managing printing on a Windows Server 2008 R2 Services that the Print and Document Services role is composed of: o Print server o LPD Service o Internet Printing o Distributed Scan Server Facts about Print and Document Services The role of Print Management Configuring printers Features to be aware of when managing printing: o Printer permissions o Printer pooling o Multiple printer objects o List in Active Directory o Deploy with Group Policy o Export/import printer o Manage print drivers o Manage documents in the print queue o Location-aware printing o Print driver isolation o Client-Side Rendering (CSR) Students will learn how to: Install the Print and Document Services role. Create and share a printer. Modify printer properties, including the following: o Sharing o Listing in Active Directory o Adding ports o Modifying security permissions ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 107 o Enabling pooling o Scheduling availability o Designating priority Deploy printers using Group Policy. Manage the default printer based on the location. Configuring Server 2008 Network Infrastructure Objectives 405. Configure and monitor print services. o Printer share o Publish printers to Active Directory o Printer permissions o Deploy printer connections o Install print drivers o Export and import print queues an printer settings o Print pooling o Print priority o Print driver isolation o Location-aware printing o Print management delegation Lecture Focus Questions: What is the difference between a print device and a printer? When would you add the LPD service when configuring the Print Services role? For which physical printing configurations would you choose a local printer when adding a printer? When would you choose a network printer? Under which circumstances would you configure a printer to use multiple print devices? When would you configure multiple printers for a single print device? How can you ensure important print jobs will automatically be printed before any other print jobs? How do clients obtain the correct driver for shared printers? When would you choose to isolate a print driver? What is the advantage of location-aware printing? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 108 Video/Demo Time 8.14.1 Print Services 7:15 8.14.2 Installing the Print Services Role 1:49 8.14.4 Configuring Printing 14:03 8.14.5 Migrating Print Server and Configuring Print Driver Isolation 3:44 8.14.6 Delegating Printer Management 3:19 8.14.7 Configuring Location Aware Printing 2:23 Total 32:33 Lab/Activity Create and Share a Printer Configure Printer Pooling Restrict Printer Access Number of Exam Questions 26 questions Total Time About 80 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 109 Section 9.1: WSUS Summary This section discusses how Windows Server Update Services (WSUS) allows you to configure a server on your intranet as a centralized point for updating software. Details include: The advantages of using WSUS Components that WSUS uses: o Microsoft Update o Windows Server Update Services (WSUS) server o Automatic Update Deployment scenarios for WSUS: o Single WSUS server o Multiple independent servers o Multiple synchronized servers o Disconnected WSUS server Microsoft Update and WSUS support updating many Microsoft products, including: o Window operating systems o Exchange Server o SQL Server o Microsoft Office Criteria for controlling updates: o Product family o Update classification o Language Configuring WSUS on the server: o Installation o Configure the server o Approve updates o Add downstream servers Students will learn how to: Install WSUS and configure a WSUS server to download updates from Microsoft Update. Synchronize and approve updates. Configure a child server as a replica of an upstream server. Run reports to view client and update information. ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 110 Configuring Server 2008 Network Infrastructure Objectives 501. Configure Windows Server Update Services (WSUS) server settings. o Update type selection o Client settings o Software updates o Test and approval o Disconnected networks Lecture Focus Questions: How do clients receive updates in the absence of WSUS? What are the disadvantages that this method poses for your network? When should you deploy multiple, independent WSUS servers? How is this configuration similar to a single WSUS server? How would you deploy WSUS when an Internet connection is not allowed for an isolated network? How does the Store updates locally setting affect where client computers go to get update files? What is the difference between synchronizing updates, downloading updates, and approving updates? Video/Demo Time 9.1.1 WSUS 8:11 9.1.3 Installing the WSUS Role 6:27 9.1.4 Configuring WSUS Server Settings 7:01 9.1.5 Configuring a Downstream Server 3:06 9.1.6 Viewing WSUS Reports 4:22 Total 29:07 Number of Exam Questions 4 questions Total Time About 40 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 111 Section 9.2: Client Configuration Summary This section covers WSUS Client Configuration and Targeting. Each client computer must have the Automatic Updates client software to use automatic updates. Targeting allows you to manage deployment of updates to specific computers through the use of groups. Details include: Automatic Update policies: o Configure Automatic Updates o Specify intranet Microsoft Update service location o Enable client-side targeting o Reschedule Automatic Updates Scheduled Installations o No auto-Restart For Scheduled Automatic Updates and Installations o Automatic updates detection frequency o Allow automatic Updates immediate installation o Delay restart of schedule installations o Re-prompt for restart with scheduled installations o Allow non-administrators to receive update notifications o Do not display ‘Install Updates and Shut Down’ option in Shut Down Windows dialog box Download of updates options: o Automatic o Notification Installation of updates options: o Automatic (Scheduled) o Notification The role of targeting Methods to assign client computers to a group: o Server-side targeting o Client-side targeting Students will learn how to: Control client update behavior through Group Policy. Create computer groups for targeting, and manually modify group membership. Enable client-side targeting on the WSUS server. Configure client-side targeting through Group Policy. ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 112 Configuring Server 2008 Network Infrastructure Objectives 501. Configure Windows Server Update Services (WSUS) server settings. o Client settings o Group Policy Object (GPO) o Client targeting o Software updates o Test and approval Lecture Focus Questions: By default, how often does the client check for updates? Which policy allows you to have clients check more frequently? Which policy do you edit to point clients to your WSUS server instead of the Microsoft Update website? How are updates installed if you enable the Do not display 'Install Updates and Shut Down' option in Shut Down Windows dialog box policy? When using client-side targeting, how do you identify the computer group for a specific computer? How does this differ from server-side targeting? Video/Demo 9.2.1 Configuring Automatic Updates Client 9.2.3 Targeting 9.2.4 Configuring WSUS Targeting Total Time 10:59 1:59 11:26 24:24 Lab/Activity Enforce WSUS Settings Number of Exam Questions 5 questions Total Time About 40 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 113 Section 10.1: Reliability and Performance Monitor Summary This section examines using Reliability and Performance Monitor. Details include: Windows Reliability and Performance Monitor combines the functionality of the following components: o Resource Monitor o Reliability Monitor o Performance Monitor o Data Collector Sets Using the Reliability and Performance Monitor Students will learn how to: View system real-time statistical displays. Add specific object counters to Performance Monitor for local or remote machines. Use the System Stability Chart to see historical system information. Configure and run Data Collector Sets for system baselines and to preserve performance statistics. Configuring Server 2008 Network Infrastructure Objectives 502. Capture performance data. o Data Collector Sets o Performance Monitor o Reliability Monitor o Monitoring System Stability Index o Analyze performance data Lecture Focus Questions: What is the relationship between a counter and an object? What service must a remote computer run to allow you to connect to it using Reliability and Performance Monitor? What kind of data collector allows you to capture software process events? What action can you take if you want to know when the CPU in a system runs over 80% more than 15% of the time? How do data collector sets help you manage data collection and reports? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 114 Video/Demo Time 10.1.1 Reliability and Performance Monitor 4:15 10.1.2 Using Performance Monitor 6:23 10.1.3 Using Data Collector Sets 10.1.4 Using Resource Monitor Total 13:41 3:27 27:46 Number of Exam Questions 13 questions Total Time About 45 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 115 Section 10.2: Event Viewer Summary This section discusses how to access and manage event logs through Event Viewer. Details include: The role of Event Viewer Common event logs include: o Application o Security o System o Setup o ForwardedEvents Features available with event logs: o Log size o Save events o Filter events o Custom views o Attach a task o Event Log Online Help The role of event subscriptions Services used by event subscriptions: o Windows Remote Management (WinRM) o Windows Event Collector (Wecsvc) Subscription types: o Collector initiated o Source computer initiated Delivery optimization options: o Normal o Minimize bandwidth o Minimize latency o Custom Configuring event subscriptions Students will learn how to: View events to gather information, such as Event ID, Log Name, User, and Computer. Create event filters and custom log views. Search and save logs. Attach tasks to events or to logs. Configure subscriptions to pull events from remote machines. ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 116 Configuring Server 2008 Network Infrastructure Objectives 503. Monitor event logs. o Custom views o Application and services logs o Subscriptions o Attaching tasks to events to find and filter Lecture Focus Questions: Which log do you view to troubleshoot errors during a software installation? What options do you have for a log file that has reached its designated capacity? What happens to the data in a log that you save that has a filter on it? How does a custom view differ from adding a filter to a log? How can you combine events from multiple logs into a single report? What tasks can you attach to an event or log? What is the purpose of the Event Log Online Help link inside each event? What two services are required to configure event subscriptions? Where do you go to view events collected from remote computers collected using event subscriptions? Video/Demo 10.2.1 Event Viewer 10.2.2 Using Event Logs 10.2.4 Configuring Event Subscriptions Total Time 5:15 10:21 5:30 21:06 Number of Exam Questions 12 questions Total Time About 40 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 117 Section 10.3: Network Monitor Summary This section discusses the basics of using Network Monitor to monitor network traffic. Details include: The role of Network Monitor Using Network Monitor o Promiscuous mode o Filters Display filter Capture filter o Aliases o Conversations o Parsers Students will learn how to: Configure Network Monitor to capture packets. Configure and remove capture and display filters. Configure conversations to group data by type. Save captured files for troubleshooting and analysis. Configuring Server 2008 Network Infrastructure Objectives 504. Gather network data. o Network Monitor Lecture Focus Questions: What are the differences between display filters and capture filters? What should you do after you have modified a capture filter? Why is this unnecessary when reconfiguring a display filter? What is the difference between capturing in promiscuous mode and capturing without promiscuous mode? When will using promiscuous mode not result in significant differences in the data captured? How can aliases make troubleshooting easier? What permissions do you need to run Network Monitor? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 118 Video/Demo Time 10.3.1 Network Monitor 3:17 10.3.2 Using Network Monitor 8:53 Total 12:10 Number of Exam Questions 5 questions Total Time About 20 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 119 Section 10.4: SNMP Summary This section discusses using Simple Network Management Protocol (SNMP) to manage network-attached devices. Details include: Components that make up an SNMP system: o Managed devices o SNMP agent o SNMP manager o Network Management Station (NMS) o Management Information Base (MIB) Methods that communication can occur between agents and managers: o Polling o Traps Definition of a community name Facts about using SNMP Students will learn how to: Add SNMP Agent support to workstations and servers. Configure the SNMP Agent service properties. Configuring Server 2008 Network Infrastructure Objectives 504. Gather network data. o Simple Network Management Protocol (SNMP) Lecture Focus Questions: What is the difference between polling and traps? Why is the default community name a security vulnerability? What does each of the community rights allow the agent or device to do? Why might READ WRITE and READ CREATE rights pose a security threat? ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 120 Video/Demo Time 10.4.1 SNMP 5:12 10.4.2 Configuring SNMP 5:48 Total 11:00 Number of Exam Questions 3 questions Total Time About 20 minutes ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 121 Practice Exams Summary This section provides information to help prepare students to take the exam and to register for the exam. Students will also have the opportunity of testing their mastery of the concepts presented in this course to reaffirm that they are ready for the certification exam. For example, all questions that apply to Objective 100. IP Addressing are grouped together and presented in practice exam Objective 100: IP Addressing, All Questions. Students will typically take about 60-90 minutes to complete each of the following practice exams. Objective 100: IP Addressing, All Questions (92 questions) Objective 200: Name Resolution, All Questions (88 questions) Objective 300: Network Access, All Questions (65 questions) Objective 400: File and Print, All Questions (130 questions) Objective 500: Monitoring and Managing, All Questions (42 questions) The Certification Practice Exam consists of 50 questions that are randomly selected from the above practice exams. Each time the Certification Practice Exam is accessed different questions may be presented. The Certification Practice Exam has a time limit of 135 minutes -- just like the real certification exam. A passing score of 95% should verify that the student has mastered the concepts and is ready to take the real certification test. ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 122 Appendix A: Approximate Time for the Course The total time for the LabSim for Configuring Windows Server 2008 Network Infrastructure Exam 70-642 course is approximately 41 hours and 17 minutes. The time is calculated by adding the approximate time for each section which is calculated using the following elements: Video/demo times Approximate time to read the text lesson (the length of each text lesson is taken into consideration) Simulations (5 minutes assigned per simulation) Questions (1 minute per question) The breakdown for this course is as follows: Module Sections Time Minute HR:MM 0.0 Introduction 0.1 Introduction 0.2 Server Management 0.3 Remote Management 0.4 Mathematical Foundations 5 20 25 15 65 1:05 1.1 IPv4 Addressing 1.2 IPv4 Subnetting 1.3 IPv4 Host Configuration 20 30 50 100 1:40 2.1 IPv6 2.2 IPv6 Addressing 2.3 IPv6 Configuration 2.4 IPv6 Implementation 5 40 35 20 100 1:40 3.1 DHCP Configuration 3.2 DHCP Options 3.3 Advanced DHCPv4 Settings 3.4 Server Placement 3.5 Superscopes and Split Scopes 3.6 DHCPv6 50 30 15 15 15 10 135 2:15 1.0 IPv4 2.0 IPv6 3.0 DHCP ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 123 4.0 DNS 4.1 DNS Concepts 4.2 Name Resolution 4.3 Zone Configuration 4.4 Active Directory-integrated Zones 4.5 Resource Records 4.6 Client Configuration 4.7 Dynamic DNS 4.8 Stub Zones and Forwarding 4.9 Root Hints and Root Zone 4.10 Zone Delegation 4.11 DNS Features 4.12 New DNS Features 4.13 Single-label Name Resolution 4.14 DNS Design 30 25 65 40 40 35 25 35 20 20 35 45 25 20 460 7:40 50 25 30 25 130 2:10 25 75 10 5 115 1:55 10 40 65 15 40 40 30 240 4:00 5.0 Routing 5.1 Routing 5.2 RIP 5.3 Demand-dial Routing 5.4 ICS and NAT 6.0 Remote Access 6.1 Remote Access Concepts 6.2 Dial-up and VPN 6.3 SSTP 6.4 CMAK 7.0 Network Access Security 7.1 Network Location Profiles 7.2 RADIUS 7.3 Network Access Protection (NAP) 7.4 Network Authentication 7.5 Firewall 7.6 IPsec 7.7 DirectAccess 8.0 File and Print 8.1 File Services 8.2 File Shares 8.3 Offline Files 8.4 NTFS Permissions 5 40 25 40 ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 124 8.5 Share and NTFS Permissions 8.6 EFS 8.7 BitLocker 8.8 BranchCache 8.9 Distributed File System (DFS) 8.10 Shadow Copy 8.11 Backup and Restore 8.12 Disk Quotas 8.13 FSRM Features 8.14 Print Services 25 35 40 35 50 25 50 25 50 80 525 8:45 9.1 WSUS 9.2 Client Configuration 40 40 80 1:20 45 40 20 20 125 2:05 92 88 65 130 42 50 467 7:47 2477 41:17 9.0 WSUS 10.0 Performance and Reliability 10.1 Reliability and Performance Monitor 10.2 Event Viewer 10.3 Network Monitor 10.4 SNMP Practice Exams 100: IP Addressing (92 questions) 200: Name Resolution (88 questions) 300: Network Access (65 questions) 400: File and Print (130 questions) 500: Monitoring and Managing (42 questions) Certification Practice Exam (50 questions) Total Time ©2011 TestOut Corporation (Rev 8/11) Configuring Windows Server 2008 Network Infrastructure (70-642) 125