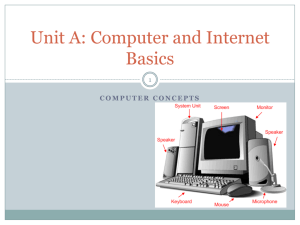
Information Technology Student worksheet
advertisement

Student Name 1, Student Name 2 Monday, February 08, 2016 BIM Teacher/Period Part I Directions: Cut & Paste, Fill-in-the-blank. 1. Pair up with your table partner and find Appendix A in the Office 2007 book. 2. Read through the Appendix and assignment together, discuss your personal experiences with computers whether on-the-job or at home (like do you have a laptop, desktop, MAC, PC or what do you wish you had, have you ever used a bar code scanner, do you Facebook, Skype/Oovoo, webcam..?). 3. Use the Word Bank table at the bottom of this assignment to fill-in-the-blanks. 4. As you find the answers you should Cut & Paste them from the Word Bank to the appropriate number in the assignment. Take turns cutting and pasting so both of you get practice. 5. When you are complete the Word Bank table should be blank. 6. Fill in the header and follow your teacher’s instructions for printing and grading. 1) A computer is used to 1) _______________, 2) 2)______________, and 3)_____________ data. 3) You enter data into a computer via 4) ________ devices. Examples of these include: 5)_____, 6)_____, 7)_____, 8)______, 9)_____ The 10)______ is a silicon chip that processes data and carries out instructions given to the computer. The CPU, computer memory and other electronic parts are stored on the computer’s 11)_________. 4) 5) 6) 7) 8) 9) 10) 11) A 12)____________________ can be both an input and output device because you can pull information from it or save information to it. Examples of these devices include: 13)______, 14)_____, 15)_____, 16)______, 17)______. 12) 13) 14) 15) 16) 17) The device that displays the results of the computer processing is an 18)________________. Examples include: 19)_______________ and 20)________________. 18) 19) 20) Computers have two types of memory 21)_____ and 22)____. 21) 22) The speed of a computer is measured by 23)_____________. 23) A 24)____ is two or more computers connected to share data. Computers connected within a small area such as a home, office, school, or building is called a 25) _________. There are three common pieces of network equipment used to build a network, the first is used to access the network, the second to convert the data to send and the third to join two or more networks. They are the 26) __________________. 24) 25) 26) Student Name 1, Student Name 2 Monday, February 08, 2016 Networks can be set up as 27)______________________. The 28)__________ is the largest network in the world. 27) 28) Network technology is often referred to as 29) __________, the personal computer is called the 30)____________ and the shared information is stored on the 31)____________. If the computer is storing web pages it is called the 32)___. 29) 30) 31) 32) To connect to the internet you need to subscribe to an 33) __. Dial-up internet connections are becoming obsolete as we move to always-on, faster technologies known as Digital Subscriber Lines (DSL). DSL comes from different companies using different medium including 34)____, 35)____ and 36)____. 33) Systems software refers to operating systems software. There are basically two widely used types of operating system software including 37)_______ and 38)________. The first personal computer was invented in 1974. It was mass marketed by 39) ____ in 1977 and by 40) _____ in 1981. You can change the way software or hardware works by using your computer’s 41)________. Examples of this include changing the speed of mouse clicks or the screen resolution. 42)__________ are software that runs the peripherals. Most configurations are changed automatically with 43) ________ software that comes with the computer’s operating system. 44) __________ are software programs that can damage your computer. They are created by people called 45) __________ and enter your computer without your knowledge. 46) _________ is a type of virus that tracks what you do on your computer for data-mining purposes. There are programs to protect your computer from viruses and spyware called 47) _______________. Installing these programs and running them on a regular basis is part of computer maintenance. Another type of maintenance is disk maintenance. You should run a program that looks for bad disk sectors and corrupted files. This is called optimizing or 48)__________ the disk. With the Internet boom has come a higher need to increase security and privacy of your electronic information. With the growing number of financial transactions taking place online 49)______________ is a growing problem. Another security breach is a criminal activity that is used by people to fraudulently obtain your password information, this is called 50) _________________. 34) 35) 36) 37) 38) 39) 40) 41) 42) 43) 44) 45) 46) 47) 48) 49) 50) BIM Teacher/Period Student Name 1, Student Name 2 Monday, February 08, 2016 BIM Teacher/Period Store Network Identity Theft RAM – random access memory Keyboard Magnetic Tape Apple LAN (Local Area Network) Scanner Spyware Client-server Network Card, Modem and Router IBM Hard Disk Drive Cable ROM – read-only memory Retrieve Monitor Hackers Internet Service Provider (ISP) Drivers DVD Microphone Bar Code Reader Input Viruses Satellite Flash, Stick or USB Drive Internet Wired or Wireless Phishing Macintosh (MAC) Client Web server Manipulate Central Processing Unit (CPU) Mouse/Touchpad Printer Output Device Utility software CD Storage Device Motherboard Microsoft Windows (PC) Defragmenting Server Plug and Play Fiber Optic (FIOS) Megahertz (MHz) & Gigahertz (GHz) Antivirus & Spyware Protection Part II: Using the knowledge you gained during the video and this exercise, complete the following: Scenario: You and your partner have decided to go into business together. You plan to have a small two person office. Using shapes/clipart in WORD draw a diagram showing two computers. Connect the computers to each other to share files and connect to peripheral devices you will need in your business. You must choose a minimum of 5 peripheral devices. Using text boxes, label the peripheral devices with their name and whether they are an input, output or input/output device. Add a page break after your diagram and on the second page write no more than one page about your office. You must use a minimum of ten words from the word bank. These words must be bolded and underlined. You may talk about whether you chose MACs or PCs, laptops or desktops, software you will need and peripheral devices you would have in your office and how they are connected. You may expand your topics to include other devices needed to operate your business like phones, copy machines and other internet uses like Skype/Oovoo and Facebook and how you might use the Internet for your business. Rubric (This is a major grade) Wait for printing instructions from your teacher: 1. 50 points Part I – one point per question 2. 50 points Part II a. 15 points diagram complete with two computers, 5 peripheral b. 15 points peripheral devices, labeled with name and input, output or input/output c. 20 points – two points per word from word bank