Project Report
advertisement

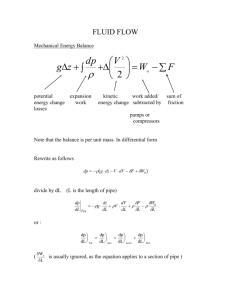
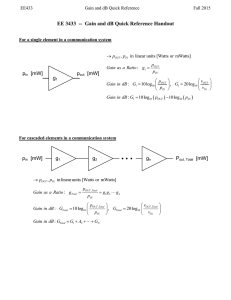
Joshua Adadevoh Micro Computer System 1 project Project Statement Audio data Encryption using the TI OMAP-L137 processor on the OMAP-L137 EVM. Coding is done in C utilizing lessons from the lab About the project An input audio signal is received via the codec on the board, and converted to hexadecimal values. The hex values are then passed through an encryption algorithm and are scrambled. The scrambled code is then converted back to an audio signal, and passed out through the output buffers to the codec and relayed through the speakers. Implementation I started by looking into writing my own encryption algorithm as opposed to trying one of the previous ones from old labs. I used c++ to write the algorithm on visual studios so I could test it out. My implementation was simple; I created two arrays of size 512 each to emulate the buffers pIn and pOut. I then filled the one for pIn with values from 1 to 512, and passed it through the decryption algorithm. Algorithm: I set all the values in my pOut emulator to equal 0, then a random number from 0 to 511 is chosen using the rand() function, and this number is used as the position for pOut example rand () = 32, and we have pOut[32]. This randomly selected pOut location is then checked, to see if it equals 0, if so then that means this random number hasn’t been selected before, and A value from pIn is then stored in the pOut location in question. If the selected location does not equal zero, then that means this number has come up before, and the pOut position already contains a value from pIn. The algorithm is repeated until all positions of pOut are accounted for. Board Interface: The work done in this class, on the OMAP EVM is all done in C, so I believed it would be a simple matter to move my c++ code to code composer and run the program. I simply added the algorithm as another function in the original c code, and passed the required arguments to it. Results: The signal was encrypted adequately. Sometimes you can hear a bit of the music beat, if it is a song, but otherwise the sound is relatively indiscernible. I also took screen shots of the original signal, before and after encryption for confirmation Before: After: Conclusion: Ideally my project should have come with decryption algorithm as well, but I did not have time to implement one, and since code employs a random seed for its encryption it can prove to be almost impossible to re-construct for the original signal. However I had a pseudo code for my decryption algorithm which I did not have time to create. We know that the back bone of the encryption is basically the random selection of numbers from 0 to 511, so I proposed to have an array store the values that passed the check, i.e. those that were selected as locations of pOut to house values from pIn. This array then acts as our key of sorts, and since we know that the values are taken from pIn in an incrementing order of i+1, starting at i = 0 up to i = 511 it would be a simple matter of reconstructing the original pIn signal should we choose to, but for the purpose of encryption this is probably information that the programmer (or his recipient in the case of a message being sent) alone should know. References: http://www.cplusplus.com/ http://my.fit.edu/~vkepuska/ece3551/