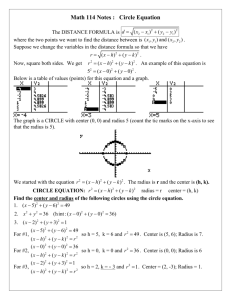
aaaconfig –show output , think thats ok. Have set the Password
advertisement
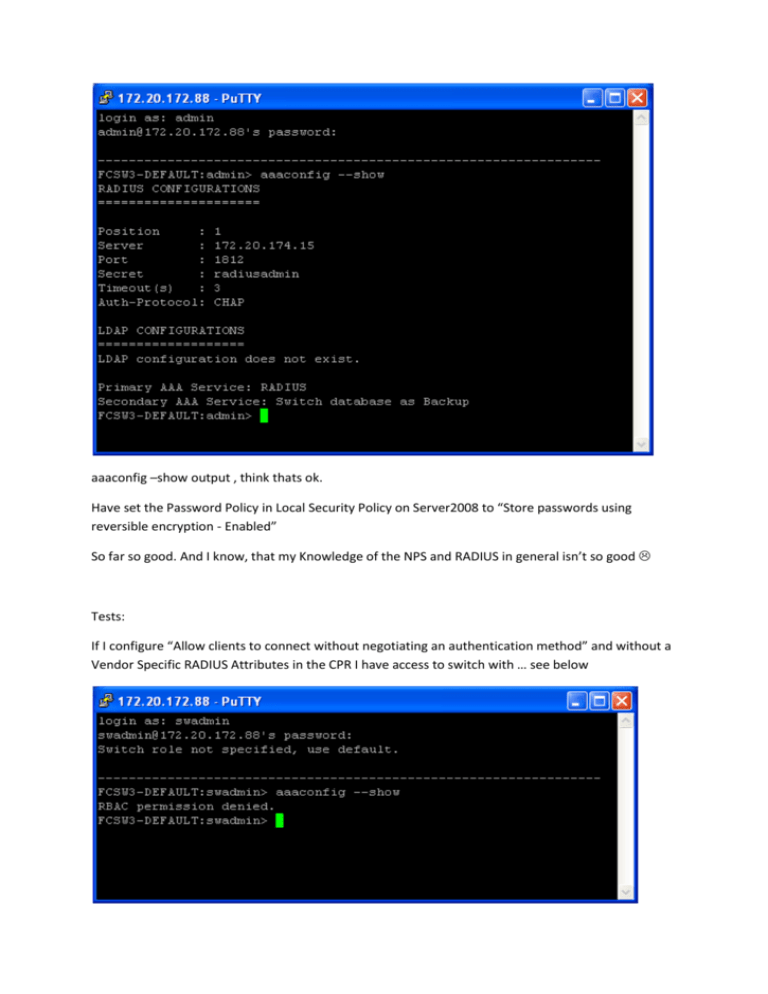
aaaconfig –show output , think thats ok. Have set the Password Policy in Local Security Policy on Server2008 to “Store passwords using reversible encryption - Enabled” So far so good. And I know, that my Knowledge of the NPS and RADIUS in general isn’t so good Tests: If I configure “Allow clients to connect without negotiating an authentication method” and without a Vendor Specific RADIUS Attributes in the CPR I have access to switch with … see below A correct access happens with my CPR “clientaccess” and in this Properties configured “Conditions” daily access (no restrictions). The RADIUS Attribute here is in Vendor Specific only “admin” nothing else. With my CPR “Brocade” and “Conditions” RADIUS Standard plus Vendor Specific attributes – no access Now the Network Policy comes to the game. Without any Network Policy I have no access to the switch. So configured a “Secure Wired (Ethernet) Connection” NP with all the Vendor Specific Attributes as described in the Admin Guide. But this configuration doesn’t work. So I have taken a standard NP from the GUI “Connections to other access servers” and this works. Results: With all the Vendor Specific Attributes the RADIUS config don’t work. My swadmin user is a local user account on the Win Server2008 in group “admin”. With the minimal RADIUS configuration I can login to the switch (PuTTY) with admin role (have add a new user “test” with role).