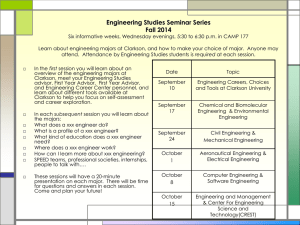
21ff0501Assignment
advertisement
Task- 2
Ans 1. This organization is the victim of DOS(Denial of Service) Smurf attack. As
shown in the sig. 2.2 the attacker broadcasts packets with the spoofed IP
address targeted towards the e sales application of the organization in which
peter works. Because packets are sent at broadcast address, it is received by all
the nodes within the network. Consequently, each and every nodes responds
which causes a large amount of echo responses packets, which exhausts the e
sales application resources and make the system very slow.
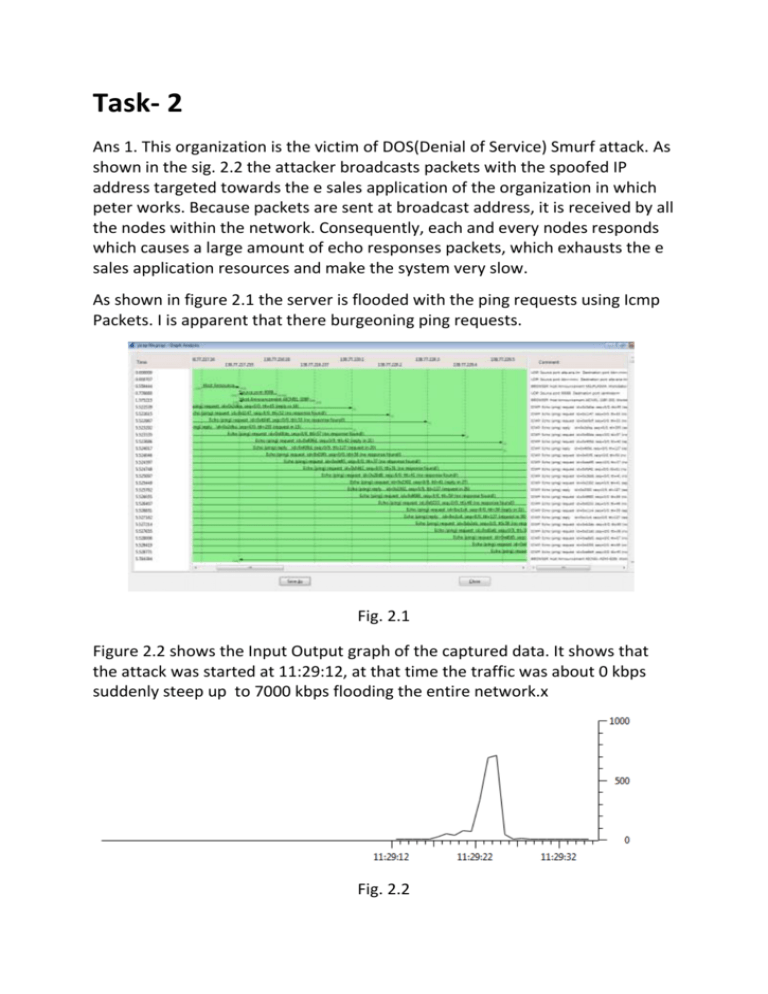
As shown in figure 2.1 the server is flooded with the ping requests using Icmp
Packets. I is apparent that there burgeoning ping requests.
Fig. 2.1
Figure 2.2 shows the Input Output graph of the captured data. It shows that
the attack was started at 11:29:12, at that time the traffic was about 0 kbps
suddenly steep up to 7000 kbps flooding the entire network.x
Fig. 2.2
Figure 2.3 shows that the packets captured during the smurf attack against the
server have flooded the server with ICMP packets. As shown ICMP type is 8
and code is 0.
Fig.2.3
Ans2. In this case attacker uses some web server denial of service tool which
are designed to generate volumes of unique traffic, hide the IP of the attacker
and hitting the server directly to slow down the resources of that server.
Different type of attack tools are TFN(Tribe flood network), Stacheldraht,
TFN2K. Some of the freely available tools are: LOIC (Low Orbit Ion Canon),
XOIC, HULK (HTTP Unbearable Load King).
References
[1] http://sggs.ac.in/ncacns/wp-content/uploads/NCACNS_paper18.pdf
[2] http://www.sans.org/reading-room/whitepapers/detection/denial-serviceattacks-mitigation-techniques-real-time-implementation-detailed-analysi33764
[4] “Denial of Service attacks and mitigation techniques: Real time
implementation with detailed analysis” By Subramani rao Sridhar rao.
Task 3
Ans 1. As per the given information in which hacker is trying to send spam
emails to thousands of user using the email detail of kirandeep’s blog. In this
case firstly the hackers is trying for spoofing i.e he is hiding his original email
Id to send the spam email to others accounts. Secondly and pertinently, hacker
is trying for the email Injection. Because, from the contact us page of the blog
email can only be sent to Kirandeep’s email account, but hacker is using email
injection to add multiple receipt addresses in the header of the mail by using
cc, bcc property of the mail header.
Ans2. Usually Php mail function work as follows:
<?php mail($recipient,$subject,$message,$headers); ?>
-Now, this will produce the raw output like this:
To: $recipient
Subject: $subject
$headers
$message
-This function will be called as follows:
<?php mail("recipient@domail.xxx","Hello","Hi,\nYour site is
Meticulous.\nBye","From: sender@anonymous.xxx\n"); ?>
-Produce the Output:
To: recipient@victim.xxx
Subject: Hello
From: sender@anonymous.xxx
Hi,
Your site is meticulous.
Bye
-Now if Hacker fill the form as follows(By adding the cc and bcc recipients ):
From:
sender@anonymous.www%0ACc:recipient@someothersite.xxx%0ABcc:somebl
oke@grrrr.xxx,someotherbloke@oooops.xxx
Subject: Win USD $1 million.
Message: You can now claim your winning amount(usd $1 million) just by
sending us your Bank Account details.
-It will actually look like this:To: recipient@victim.xxx
Subject: Win USD $1 million.
From: sender@anonymous.xxx
Cc:recipient@someothersite.xxx
Bcc: somebloke@grrrr.xxx,someotherbloke@oooops.xxx………………(Can add any
number of Recipients
Message: You can now claim your winning amount(usd $1 million) just by
sending us your Bank Account details.
This mail has been injected successfully. By using this method attacker can add
any no of recipient.
ANS3. The most common and golden rule is to filter and validate the data.
Either by regular expression or string function and Mod Security(To secure the
page from email injection on server level)
For eg (expression and string validation): In this We will restrict any
occurrence of \n or \r which are used for the new line.
<?php
$from = $_POST["sender"];
if (eregi("(\r|\n)", $from)) {
die("Why ?? :(");
}
?>
Eg Mod security :
With Mod escurity it is possible to scan the POST or GET body for Bcc, Cc, or To
and restrict any request that contains those letters.
SecFilterSelective ARGS_VALUES "\n[[:space:]]*(to|bcc|cc)[[:space:]]*:.*@"
Secondly, We can use captcha to stop bots from performing abusive actions on
a website. CAPTCHA works by presenting a challenge to the user (typically in
the form of an image containing jumbled-up letters) which must be solved to
proceed in the interaction flow.
For eg:
CAPTCHA seems perfect because bots only have access to that which is in the
document source. Text within images cannot be seen by an internet bot and
therefore the bot cannot submit a response to the challenge.
We can make our webform more secure by limiting the characters in the field
of message. However, it cannot restrict the email injection but it will lower
down its tendency.
REFERENCES
[1] http://www.damonkohler.com/2008/12/email-injection.html
[2] http://www.codeproject.com/Articles/428076/PHP-Mail-InjectionProtection-and-E-Mail-Validatio
[3] http://en.wikipedia.org/wiki/Email_injection