EC312: Applications of Cyber Engineering Exam #1 – Review
advertisement
EC312: Applications of Cyber Engineering
Exam #1 – Review Solutions
Lesson 1 – Computer System Review
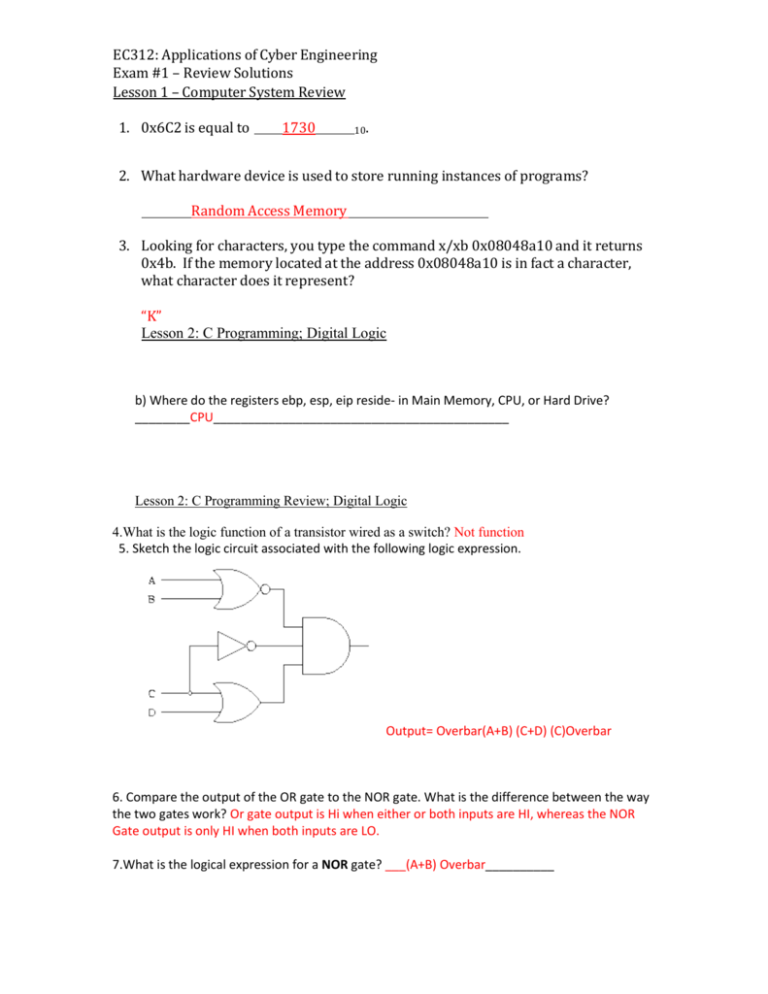
1. 0x6C2 is equal to
1730
10.
2. What hardware device is used to store running instances of programs?
Random Access Memory
3. Looking for characters, you type the command x/xb 0x08048a10 and it returns
0x4b. If the memory located at the address 0x08048a10 is in fact a character,
what character does it represent?
“K”
Lesson 2: C Programming; Digital Logic
b) Where do the registers ebp, esp, eip reside- in Main Memory, CPU, or Hard Drive?
________CPU___________________________________________
Lesson 2: C Programming Review; Digital Logic
4.What is the logic function of a transistor wired as a switch? Not function
5. Sketch the logic circuit associated with the following logic expression.
Output= Overbar(A+B) (C+D) (C)Overbar
6. Compare the output of the OR gate to the NOR gate. What is the difference between the way
the two gates work? Or gate output is Hi when either or both inputs are HI, whereas the NOR
Gate output is only HI when both inputs are LO.
7.What is the logical expression for a NOR gate? ___(A+B) Overbar__________
EC312: Applications of Cyber Engineering
Exam #1 – Review Solutions
8.What data type would be optimal to store the following classes of data?
A. Number of jellybeans in a jar
int
B. Cost of a Snickers bar
float
C. The circumference of a lollipop
float
D. Individual letters in ‘skittles’
char
E. The whole word ‘skittles’
string
F. Phone number of a local dentist
int
5.
6.
7.
8.
9. How many total bytes would be needed to store the following variables?
int
float
char
33 Bytes
tacos, nachos = 14, chimichangas;
burritos = 2, pico, de, gallo;
tortilla, *guacamole;
EC312: Applications of Cyber Engineering
Exam #1 – Review Solutions
10. Match the term on the left with its appropriate description on the right:
k _ printf
a. the C programming language
m #include <…>
b. the C assignment operator
f _ scanf
c. a UNIX text editor, can be used to write C programs
i _ gcc
d. translates assembly language into machine language
h _ machine language
e. the format string for an integer value
c _ nano
f. allows the program to receive keyboard input
d _ assembler
g. the C escape sequence for a new line
a _ high level language
h. instructions expressed as bits, also called object code
l _ assembly language
i. program that converts source code to object code
e _ %d
j. all of the simple instructions hard-wired on a CPU
b_ =
k. function which displays text to the monitor
g _ \n
l. English-like words that represent machine code
j _ instruction set
m. allows the use of functions from various header files
11. Study the program below:
#include <stdio.h>
int main()
{
int apples=42;
printf(“There are %c apples in my barrel\n”, apples);
return 0;
}
Which type of error does the program represent? Circle one below, then describe the
mistake.
Syntax Error
Run-Time Error
Logic Error
Instead of a number, the ASCII character associated with that number will be printed.
EC312: Applications of Cyber Engineering
Exam #1 – Review Solutions
Lesson 3 – Registers and Memory
8. Examine the following C program and describe the expected output.
(Note: The output for count%2 is the remainder of count divided by 2.
i.e. for 4%2, the remainder is 0.)
#include<stdio.h>
int main()
{
int count;
for(count=1; count<=100; count=count+1)
{
if(count%2==0)
printf(“Echo\n”)
else
printf(“Oscar\n”)
}
}
The program will count from 1
to 100 and will print “Echo” if
the number is even and will
print “Oscar” if the number is
odd.
9. Describe what this line of code accomplishes:
Takes 4 byte info in address ebp-4 and adds it to eax and with the result of
the addition stored in eax.
10. Recall that in RAM you have stored the object code for
your program as well as additional memory allocated for
your variables within the program.
You type into the debugger the command i r ebp and
get the result 0xbffff810. Upon further
review of the assembly code you
determine that two integers are stored in
memory, one at address ebp-8 and the
other at ebp+4. What are the hidden
decimal numbers?
Integer 1:
0
Integer 2:
134513696_
Program
Code
~
~
EC312: Applications of Cyber Engineering
Exam #1 – Review Solutions
Lesson 4 - Arrays
11. Answer the questions about the character string in memory below.
0x53
a) What is the minimum number of
bytes that could have safely been
allocated for this string?
0x69
6
0x4C
b) Write this declaration, name the
array ‘myString’
0x32
0x39
0x00
0x00
char myString[6];
c) What is the address of ‘myString’?
0x00003D16
d) What character is at myString[1]?
“i”
Lesson 5 – Strings and Pointers
12. Given the following declarations, what would be the C statement to assign
ptrVar1 the value in floatVar1?
float
float
floatVar1 = 3.14;
*ptrVar1;
*ptrVar1 = floatVar1;
13. Given the following C statements, what would the result of the printf statement
be?
int
int
pickles = 1, carrots = 13;
*veggie_ptr;
veggie_ptr = &pickles;
*veggie_ptr = *veggie_ptr + 1;
printf(“I have %d pickles, hey hey hey hey!\n”, pickles);
I have 2 pickles, hey hey hey hey!
EC312: Applications of Cyber Engineering
Exam #1 – Review Solutions
Lesson 6 – Functions and the Stack
14. Circle the appropriate words to complete the statement below:
To use a function we must invoke it with a
prototype.
function. A
for a
called the
The values /
return value
parameters /
/ function
call /
argumentsare the inputs to a
value
/ parameter
/ argument is a placeholder that “stands in”
value
/ parameter
/ argument. The result from a function is
return value
/
function call
/
prototype.
15. Place the following elements in the order the will appear (from bottom to top) on the
stack during a function call from main (while executing the instructions for that
function).
Return Address
Main Variables
Function Variables
Saved Frame Pointer
Function Arguments
esp
ebp
Top
esp
Function Variables
ebp
Saved Frame Pointer
Return Address
Function Arguments
Main Variables
Bottom
EC312: Applications of Cyber Engineering
Exam #1 – Review Solutions
16. a) Given the following source code and debugger output, construct the stack frame
for the function main in the diagram below part b. Show where the base pointer
(label as EBP-Main) and stack pointer (label as ESP-Main) are pointing to, and
show where the arguments to exam_function are stored in memory.
#include<stdio.h>
void exam_function( int x, int y, int z)
{
int some_class;
int best_class;
int my_class;
best_class = x;
my_class = z;
some_class = y;
}
int main()
{
exam_function( 2005, 2003, 2015 );
}
EC312: Applications of Cyber Engineering
Exam #1 – Review Solutions
b) Using your answer from part a), and the additional debugger output below,
construct the stack frame for the function exam_function. Show the location of
the base pointer (label as EBP-Exam) and stack pointer (label as ESP-Exam) on
the figure. Note on your figure:
• the location of best_class, some_class, and my_class
• the location of the return address
• the location of the prior value of the base pointer (EBP-Main)
Address
BFFFF7E8
BFFFF7EC
BFFFF7F0
BFFFF7F4
BFFFF7F8
BFFFF7FC
BFFFF800
BFFFF804
BFFFF808
BFFFF80C
BFFFF810
BFFFF814
BFFFF818
BFFFF81C
BFFFF820
Value
Description
7DF (2015)
7D5 (2005)
7D3 (2003)
BFFFF818
0804838A
7D5 (2005)
7D3 (2003)
7DF (2015)
my_class, ESP-Exam
best_class
some_class
SFP, EBP-Exam
Return Address
ESP-Main
EBP-Main
EC312: Applications of Cyber Engineering
Exam #1 – Review Solutions
Lesson 7 – Buffer Overflow Introduction
17. For the pawn function below, is it possible to overwrite the value you will get
for your item with an amount of your choosing by overwriting the value
variable on the stack during the scanf( ) call below? Explain.
void pawn()
{
char item[12];
int value = 100;
printf(“What have you come to sell? “);
scanf(“%s”, item);
}
int main()
{
pawn();
}
Not possible, value is higher up on the stack than item.
18. Describe the mechanism by which a segmentation fault occurs.
A variable on the stack is written to so far beyond it’s allocated boundaries that it is able to overwrite
the Saved Frame Pointer and/or the Return Address, thus causing unsuccessful attempts to access
memory segments to which the current process is not permitted.
19. For the following program invocation:
midshipman@EC310 ~$ ./a.out wait 8 mate
A) What is the value of argc?
4
B) What is the value of argv[1]?
“wait”
C) What is the data type of argv[2]?
string
Lesson 8 – File I/O and Permissions
20. Which segment of memory is physically highest (smallest addresses)?
a) Heap
b) Stack
c) Text
d) Registers
EC312: Applications of Cyber Engineering
Exam #1 – Review Solutions
21. You are viewing the access privileges of a file exam1.sh and they read:
-r-xr-xr-Check all privileges granted to the owner:
read
write
execute
22. You give the command chmod g-x exam1.sh
What access privilege(s) did you change and to whom do they apply?
The associated group may no longer execute the program.
Lesson 9 – Privilege Management
23. The following is the output of ‘ls –l’ for the shutdown command, which is a
system administration program.
We can see that it is owned by the root user (administrator) but it is executable
by everyone.
A) Why, then, does the system not shut down when run by a normal user, like
jose?
The shutdown functionality is only available to the user ID of root.
B) How can the root user modify the permissions to this program to allow
anyone to shut down the computer? (Give the command, then an explanation of
how it solves this problem)
chmod u+s /sbin/shutdown
Any user running shutdown will have setuid permission of root for this process.
24. (a)
What does the sudo command accomplish? Be specific.
Enables a user to perform a task as though they were the superuser (root).
(b)
Who can execute the sudo command? Be specific.
Anyone who has explicitly been granted permission to do so by the root user in the
/etc/sudoers file.