Questions
advertisement

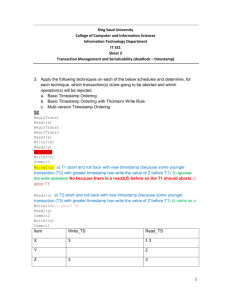
Questions Question 1: Models of Distributed Computation a. Synchronization; arbitrate resources requests in a fair manner b. A system is said to be non-deterministic when it contains a state S in which more than one events can occur (they are enable) and the event that will actually occur in S cannot be predicted. A probabilistic system is one that makes explicit use of randomness. For instance, a system which has a state transition that depends on the result of flipping a coin is probabilistic. Yes, there is a difference between non-deterministic systems and probabilistic systems. A system can be both non-deterministic and probabilistic. c. Lamport’s timestamp algorithm is said to be fault-tolerant. That means that even if some processors crash (fail-stop) during the execution of the Lamport’s timestamp algorithm, the remaining processor will continue to assign consistent timestamp to local events. d. Events in ANCEST(e) are those that causally precede e. Hence, in order to capture ANCEST(e) at e, one uses Vector timestamp. This because, with vector timestamp, each event carries its causal history. e. In the absence of a sending event, Algorithm 9.3 on page 334 might enter a deadlock. If processor p receives a message m2 that causally follws m1 and m1 is not received, message m2 will not become unblocked. Question 2 : Distributed algorithms design 1 a. One way to solve this problem consists of constructing a spanning tree. Then, from leaf nodes, to the root, each node sends the size of its subtree to its parent. When an internal node has received from all its children, it adds one to the sum of the values received from its children. Then it sends the result to its parent. Hence, recursively the size of the system is computed from leave to the root. When the root node has computed the size of the system, it broadcasts it to all other nodes in the system. b. Let E be the number of links (edges) in the system. O(E) messages are required. Question 3: Distributed algorithm design 2 a. This problem can be solved in a similar manner as in Question 2. Each node computes the maximum of the values of its subtree then it sends the result to its parent. When an internal node has received from all its children, it computes the maximum of the values received and its own value. Then it sends the result to its parent. In this manner, the maximum is computed recursively from leaf nodes up to the root. When the root has computed the maximum value of the system, it broadcasts the result to all other nodes in the system. Another way to solve this problem is to have each node launches a diffusing computing in order to collect all the values of the system. When a node has received (at the end of its diffusing computing) all the values, it simply computes the maximum of the set of values it just collected. Question 4: Distributed Mutual exclusion a. It is not possible (assuming fault-free systems) for the system to enter such a configuration. There are two reasons: From each node, one should reach the end of the waiting queue by following the cuurent_dir pointers. This is not the case in the picture. Each node in the system must have a current_dir pointer. However, this is not the case in the picture. Question 5: Distributed Agreement a. The BG(k) algorithm works in rounds of messages exchanges and k+1 rounds are required. In round 1, the commanding general sends M-1 messages. In round 2, there are M-1 lieutenants of round 1. Each lieutenant of round 1 acts as a commanding general in round 2 by sending M-2 messages. In round j>2, there are M-j lieutenants of round j-1.Each lieutenant of round j-1 acts as a commanding general by sending M-j-1 messages. Hence the number of messages is proportional to (M-1)(M2)…(M-j)(M-j-1) where j k+1. That is, the number of messages is proportional to (M-1)(M-2)…(M-k-1)(M-k). Hence, O(Mk) b. It is not possible to reach Byzantine Agreement in that case. The majority is not always possible. In fact, assume that we have four general and the commanding general is disloyal. If the commanding general sends three different values to lieutenant, each (loyal) lieutenant will receive the same set of three different values. Since there is no default value, no majority is achieved. Question 6: Concurrency control Determine, for each of the following schedulers, whether the schedule is serializable or not. We use the following notation: RI(X) means Read operation by transaction I, and WI(X) write operation by transaction I on item X. If the answer is affirmative, give a corresponding serial schedule. If the answer is negative, give the reason. a. SCH1: R1(X)R2(X)R1(U)R2(Z)W2(Y)W1(X)W2(U)W1(U) Is not serializable: T1 (rw/U) T2 (ww/U) T1, there is a cycle b. SCH2: R2(Y)W2(Y)R1(Y)W1(Y)R1(X)W1(X)R2(X)W2(X) Is not serializable: T1 (rw/Y) T2 (rw/Y) T1 c. SCH3: R1(X)R3(Z)R1(Y)R3(Y)W3(Z)R2(Y)R1(Z)R2(Z)W2(Z)W1(Y)W2(Z)W1(Z) Is not serializable: T1 (rw/Z) T2 (rw/Y) T1 d. A scheduler of a transaction system implements concurrency control using timestamps. Assume that the only transactions in the system are T1 and T2. Consider that the schedule has performed the following sequence of operations: R1(X)W1(X)R2(X)R1(Y)W1(Y)W2(X)R2(Y)W2(Y). Is this schedule feasible if the timestamp of T1 < T2? Explain your answer. Observe that: On X, transaction T1 arrives before T2. On Y, transaction T1 arrives before T2. Hence on both objects, transactions T1 and T2 arrive in a order that is consistent with their timestamp. R1(X)W1(X)R1(Y)W1(Y)R2(X)W2(X)R2(Y)W2(Y) is a serial schedule. Thus, this schedule is feasable. e. Is schedule R1(X)W1(X)R2(X)R1(Y)W1(Y)W2(X)R2(Y)W2(Y) feasible if T1 and T2 are 2PL transactions? Explain your answer. No. Because T1 does not release the lock on X until it has obtained also the lock on Y. Question 7: Commit Protocol a. Commit protocol is required in distributed systems to ensure the (atomic) “all-ornothing” property in presence of failure. In effect, in distributed system, the execution of a transaction involves many processors. We must be sure that if the transaction commits, its effects are made permanent at all sites that take part on it; and if the transaction aborts, its effects is undone at all the sites that are involved. Question 8: Checkpointing and recovery a. Picture b. P1 will roll back to the beginning of I13, P2 will roll back to the beginning of I23, P3 will roll back to the beginning of I34 Question 9: Trans algorithm A set of processors is running the Trans algorithm and the following events occur at processor P in that order. 1. Message “b1;[ack(a1),ack(a2)]” arrive at P; 2. Message “c1;[ack(b1), ack(d1)]” arrive at P; 3. Message “a2;[]” arrive at P; 4. Message “a1;[]” arrive at P; 5. Processor P multicasts message “p1;[ack(b1),nack(d1)]” a. For each step, give the corresponding DAG at processor P and the value of the variable nack_list and that of ack_list. b. After step 4, which messages can be delivered? Why? Messages a1,a2 and b1. Because, just after step 4, these messages are causal. c. In step 5 why processor P does not send a positive acknowledgement for message a1 and for message d1. Processor P does not send an acknowledgement for a1, because of the following invariant: A processor p broadcast an acknowledgement of message m only if p has received m and all messages that causally precede m. That is, the mechanism of transitive acknowledgement is used. Processor P does not send an acknowledgement for d1, because d1 is not yet received. (Again, to maintain the invariant)