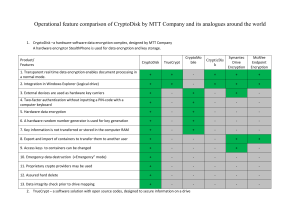
Document
advertisement

ENCRYPTION Jo Cromwell Cornelia Bradford History of Encryption Encryption has been around since antiquity Cryptography began around 2,000 B.C in Egypt (Hieroglyphics) The Spartans developed a transposition cipher Greeks provided 1st recorded ciphers using numerical substitutions – 5th Century B.C. Arabian 1st to document cryptanalytic methods - 1412 The Polybius Square 1 2 3 4 5 1 A B C D E 2 F G H I J 3 K L M N O 4 P Q R S T 5 U V W X Y/Z Telegraph 1835-- Samuel Morse invented the Morse Code 1843-- Construction of experimental telegraph line from Washington to Baltimore (40 miles) Radio 1895 – Changed Cryptology— Communications were open for anyone’s inspection Electromechanical Cryptography The rotor – a thick disk with two faces, 26 brass contacts, plaintext input face,and output (ciphertext) face Americans used rotors to break Japanese codes Germany used similar machines to the rotor Polish cryptanalysts broke Enigma early in WW2 First computers were used for decoding Enigma ciphers The Enigma Machine Like a typewriter, combining substitution and rotation ciphers in such a manner that the resulting overall cipher was difficult to break, unlike the constituent ciphers. The machine could decode as well as encoding messages. The Enigma is configured by selecting several rotors from a larger set, placing them in a particular order and a particular start position. Received messages are decoded by setting the Enigma to the same state as the encoding Enigma X instead of and processing the message again. The result is clear text with the letter spaces. Enigma Machine Enigma Machine Enigma Machine Encryption The conversion of data into ciphertext, that cannot be easily understood by unauthorized people. Decryption The process of converting encrypted data back into its original form so that it can be understood. Computer Encryption Text: Human, Plaintext: What you readable sequences of characters and words that are formed that can be encoded into computer readable format such as ASCII have before encryption Ciphertext: Encrypted test Cipher: Usually refers to the method of encryption Computer Encryption ASCII: American Standard Code for Information Exchange Most common format for text files in computers and on Internet Unix & DOS-based systems use ASCII Windows NT & 2000 use the newer Unicode IBM uses an 8-bit code, EBCDIC Computer Encryption Symmetric Key Encryption *Each computer has Public-key Encryption *Combination of Private Key and Secret Key Public Key *Code provides key to decoding message *Pretty Good Policy Authentication Verifies that information comes from a trusted source Works hand-in-hand with Encryption to create Secure Environment How Do You Authenticate? Password Pass Cards Digital Signatures Biometrics – – – – Fingerprint Scan Retina Scan Face Scan Voice Identification JOYS End danger of information interception Keeps business information secure Even if Info/Password is intercepted – Can’t Read! Government Standards National Institute of Standards and Technology (NIST) adopted Advanced Encryption Standard (AES) Banking industry will probably follow One B-I-G Algorithm Party! References www.howstuffworks.com www.all.net/books www.donet.com www.cescomm.com http://whatis.techtarget.com