Principles of Computer Security
advertisement

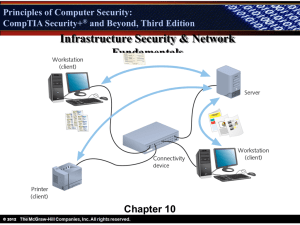
Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Remote Access Connection, Authentication, Authorization Chapter 11 © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Key Terms (continued) • • • • • • © 2012 Layer 2 Tunneling Protocol (L2TP) Mandatory access control (MAC) Point-to-Point Tunneling Protocol (PPTP) Remote Access Server (RAS) Role-based access control (RBAC) Rule-based access control (RBAC) Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Remote Access Process • Requires two things: – A temporary network connection – A series of protocols to negotiate privileges and commands • To establish proper privileges, three steps are used: – Authentication – Authorization – Accounting © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Identification • The process of assigning a computer ID to a specific user, computer, network device or computer process. • User IDs should not be shared or descriptive of job function. • Links the logon ID or user ID to previously assigned credentials. © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Authentication • The process of binding a specific ID to a specific computer connection • Four categories of secrets are used: – – – – © 2012 What users know (password) What users have (tokens/key cards) What users are (biometrics) What users do Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Kerberos • A network authentication protocol designed for the client/server environment. • Uses tickets in a two-step process with the client. – An authentication server issues a ticket-granting ticket to the client. – The ticket is then presented to a Kerberos server to request a ticket granting access to that server. – The server the issues a client-to-server ticket to the client. • The entire session is encrypted. © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Kerberos Operations © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Tokens • A hardware device that counts as both something-youhave and something-you-know. • A number is displayed on the screen that is used in conjunction with a user ID. • The number changes at a constant interval. • Even if someone finds the token, they won’t know the corresponding user ID. © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition One-Time Password Generator Token © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Multifactor • Uses more than one authentication mechanism at the same time. Examples include: – Biometric scanners and a PIN – Hardware tokens – ATM card and a PIN • Increase the level of security, as multiple methods would need to be spoofed accurately and simultaneously. © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Single Sign-On • One authentication method works for every system that a user needs to access. • Reduces login hassles: – Fewer usernames and passwords to remember • Inherently less secure: – If a login is compromised for one system, all systems the user can access are also compromised © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Access Control • Access is the ability of a subject to interact with an object. • An access control matrix shows what can be accessed by whom. © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Models of Access Control • • • • © 2012 Discretionary access control (DAC) Mandatory access control (MAC) Role-based access control (RBAC) Rule-based access control (RBAC) Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Discretionary Access Control • The owner of an object can decide what other subjects can access the object and what specific access they may have. • Often use access control lists © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Mandatory Access Control • The operating system decides what access will be granted to an object, based on its label. • Every subject and every object in the system has a label, and they must match before access is granted. – For example, a subject with a “secret” label cannot access an object with a “top-secret” label. © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Role-Based Access Control • Users are assigned a set of roles that they can perform. • Each role is assigned the access permissions needed to carry out its function. • Simplifies access control: people who need the same level of access are assigned to the same role, instead of having to give them all permission individually. © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Rule-Based Access Control • The ACL contains a series of rules, and these rules are used to determine whether or not access to a resource is granted. • Can be used in addition to other access control methods or as a stand-alone method. © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Authentication Protocols • Numerous authentication protocols exist. Some of them include: – – – – – © 2012 L2TP and PPTP PPP EAP CHAP SSH Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition L2TP and PPTP • Layer 2 Tunneling Protocol (L2TP) and Point-to-Point Tunneling Protocol (PPTP) are both OSI Layer 2 tunneling protocols. • Tunneling is the encapsulation of one packet within another: – This allows you to hide the original packet from view – Provides greater security © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition PPP • Point-to-Point Protocol (PPP) is an OSI Layer 2 protocol used to connect devices. • Used for establishing dial-in connections over serial lines or Integrated Services Digital Network (ISDN) services. • Has several authentication mechanisms: PAP, CHAP, and EAP. © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition PPTP • An extension of PPP that enables the creation of virtual private networks (VPNs) • Enables the secure transfer of data from a remote PC to a server by creating a VPN across a TCP/IP network • Involves three computers: – The PPTP client – The NAS (usually an ISP) – The PPTP server © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition L2TP • Designed for use across all kinds of networks, including ATM and Frame Relay • Can be implemented by both hardware and software • Designed to work with established AAA services such as RADIUS and TACACS+ © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Telnet • Allows users to log in remotely and access resources as if they had a local terminal connection • Offers little security, as usernames, passwords, and all data are passed in clear text over the TCP/IP connection • Access control to Telnet on machines and routers should be implemented when they are first set up • Uses TCP port 23 © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Secure Shell (SSH) • Secure Shell is a protocol series designed to facilitate secure network functions across an insecure network. • SSH was designed as a replacement for the insecure telnet. • SSH uses TCP port 22. • SSH has three major components: – Transport layer protocol – User authentication protocol – Connection protocol © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition VPNs • A virtual private network is a secure network built on top of a physical network. • It’s not a protocol in and of itself, but rather a method of using protocols to achieve secure communications. • It is typically used to access a corporate data network from a home PC across the Internet. © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition VPN Service Over an Internet Connection © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition IPsec • Operates at OSI Layer 3, the network layer • Content and context protection • Provides a sweeping array of services: – – – – – © 2012 Access control Connectionless integrity Traffic-flow confidentiality Rejection of replayed packets Data security (encryption) Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Vulnerabilities of Remote Access Methods • • • • © 2012 Plaintext credential passing Strength of the encryption algorithm Bugs can open the system to attack Vendor responsiveness to fixing the bugs once they are discovered Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Chapter Summary • Discuss the methods and protocols for remote access to networks. • Explain authentication methods and the security implications in their use. • Implement virtual private networks (VPNs) and their security aspects. • Describe Internet Protocol Security (IPsec) and its use in securing communications. © 2012