Chapter title
advertisement

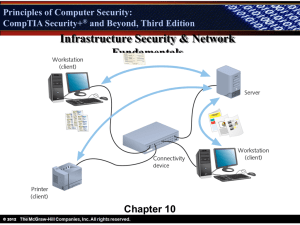
Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Operational and Organizational Security Chapter 3 © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Objectives • Identify various operational aspects to security in your organization. • Describe the physical security components that can protect your computers and network. • Identify environmental factors that can affect security. • Identify factors that affect the security of the growing number of wireless cellular technologies used for data transmission. • Prevent disclosure through electronic emanations. © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Key Terms • • • • Biometrics Bluetooth Guidelines Heating, Ventilation, and Air Conditioning (HVAC) • IEEE 802.11 • Physical security © 2012 • • • • • Policies Procedures Standards TEMPEST Uninterruptible power supply (UPS) Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Security Operations in Your Organization • The operational model of security – Protection = Prevention + (Detection + Response) • No matter how secure we attempt to make our systems, some way will always be found to circumvent the safeguards we have in place. • Prevention technologies are static. • Detection and response technologies are dynamic. © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Security Operations in Your Organization • Policies (continued) – High-level, broad statements of what the organization wants to accomplish • Procedures – Step-by-step instructions on how to implement policies in the organization • Standards – Mandatory elements regarding the implementation of a policy • Guidelines – Recommendations relating to a policy © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition The Operational Process and Policy Lifecycle Plan for security Evaluate the effectiveness Implement the plans Monitor the implementation © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Is This the Security Perimeter? © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition A More Complete Diagram © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Physical Security • Physical security consists of all mechanisms used to ensure that physical access to the computer systems and networks is restricted to only authorized users. • No matter how good your computer and network security is, if a person has physical access, then can compromise the CIA of your information in some way. © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Physical Security (continued) • Access from all six sides should be considered – – – – – – – – © 2012 Is there a false ceiling with tiles that can be removed? Is there a raised floor? Do the monitors face away from windows? Who has access to the facility? What type of access control is there to the area? Are there any guards? Who is allowed unsupervised access to the facility? Is there an alarm system or security camera set up? Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Access Controls • Authentication via – Something you have – key or card – Something you know – combination – Something you are – biometrics • Biometrics – More sophisticated and expensive – Not yet 100 percent foolproof • Two factor authentication – Using two of the methods for authentication • Other controls – Video surveillance, sign-in logs, security guards © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Physical Barriers • Principle of layered security – – – – – – © 2012 Fences Guard at the gate Open space Walls Signs denoting public and private areas Man trap Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Environmental Issues • Heating, ventilation and air conditioning (HVAC) – Used to maintain the comfort of an office environment – Also maintained environment for computers • Heat and humidity sensitive devices and network components • Uninterruptable Power Supply (UPS) – Used for critical systems so that a loss of power will not halt processing – The larger the battery, the longer the equipment can operate during a loss of power © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Fire Suppression • Fire is a common disaster. • Fire detectors – Smoke detection – Heat detection • Fire suppression – Sprinkler-based • Standard, but will further damage equipment – Gas-based • Halon was used and may still exist in some areas. • Halon displaces oxygen and can asphyxiate people in the area when it is dispersed. • Halon is being replaced with other gases such as argon, nitrogen, and carbon dioxide. Note that the same danger exists. © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Wireless • By wireless we mean cellular telephones (“cell phones”) • Cell phone network – Phones – Cells with accompanying base stations – Base stations – antennas, receivers, transmitters, and amplifiers – As a person travels, they enter and exit multiple cells. • Also used for networking – Bluetooth – for short range personal area network (PAN) – IEEE 802.11 – used for local area networks (LAN) © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Electromagnetic Eavesdropping • The van Eck phenomenon – Eavesdropping on what is being displayed on monitors by picking up and decoding the electromagnetic interference (EMI) produced by monitors. • This phenomenon also applies to printers and computers. © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition TEMPEST • Transient Electromagnetic Pulse Emanation STandard – The process for controlling emanations • Term also refers to a military program to control emanations • Three basic ways to protect emanations – Keep equipment at a safe distance. – Provide shielding for equipment. – Provide shielded enclosure, such as a room. © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Location • Where equipment is situated can increase or decrease its exposure to risk. – Where will you place access points? – How deep in the building can you place sensitive equipment? – What is the proximity of the building to roads? – Where are the monitors? – Where are your printers? © 2012 Principles of Computer Security: CompTIA Security+ Security+® and Beyond, Third Edition Chapter Summary • Identify various operational aspects to security in your organization. • Describe the physical security components that can protect your computers and network. • Identify environmental factors that can affect security. • Identify factors that affect the security of the growing number of wireless cellular technologies used for data transmission. • Prevent disclosure through electronic emanations. © 2012