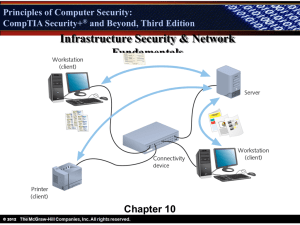
General Security Concepts - Digital Locker and Personal Web Space
advertisement

Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition General Security Concepts Chapter 2 © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Objectives • Define basic terms associated with computer and information security. • Identify the basic approaches to computer and information security. • Distinguish among various methods to implement access controls. • Describe methods used to verify the identity and authenticity of an individual. • Recognize some of the basic models used to implement security in operating systems. © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Key Terms • • • • • • • • © 2010 *-property Access control Auditability Authentication Availability Bell-LaPadula security model Biba security model Clark-Wilson security model • • • • • • • • Confidentiality Data aggregation Diversity of defense Hacking Host security Implicit deny Integrity layered security Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Key Terms (continued) • • • • • Least privilege Low-Water-Mark policy Network security Nonrepudiation Operational model of computer security • Phreaking © 2010 • • • • • Ring policy Security through Obscurity Separation of Duties Simple Security Rule Social engineering Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Basic Terms • Hacking – Previously used as a term for a person who had a deep understanding of computers and networks. He or she would see how things worked in their separate parts (or hack them). – Media has now redefined the term as a person who attempts to gain unauthorized access to computer systems or networks. • Phreaking – Hacking of the systems and computers used by phone companies © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition The CIA of Security CIA • Confidentiality • Integrity • Availability Additional Concepts • Authentication • Nonrepudiation • Auditability © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition The Operational Method of Computer Security • Protection = Prevention – Previous model • Protection = Prevention + (Detection + Response) – Includes operational aspects © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Sample Technologies in the Operational Model of Computer Security © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Security Principles • • • • • • • • • © 2010 Security approaches Least privilege Separation of duties Implicit deny Job rotation Layered security Defense in depth Security through obscurity Keep it simple Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Security Approaches • Ignore Security Issues – Security is simply what exists on the system “out of the box.” • Host Security – Each computer is “locked down” individually. – Maintaining an equal and high level of security amongst all computers is difficult and usually ends in failure. • Network Security – Controlling access to internal computers from external entities © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Least Privilege • Least privilege means a subject (user, application, or process) should have only the necessary rights and privileges to perform its task with no additional permissions. • By limiting an object's privilege, we limit the amount of harm that can be caused. • For example, a person should not be logged in as an administrator—they should be logged in with a regular user account, and change their context to do administrative duties. © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Separation of Duties • For any given task, more than one individual needs to be involved. • Applicable to physical environments as well as network and host security. • No single individual can abuse the system. • Potential drawback is the cost. – Time – Tasks take longer – Money – Must pay two people instead of one © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Implicit Deny • If a particular situation is not covered by any of the rules, then access can not be granted. • Any individual without proper authorization cannot be granted access. • The alternative to implicit deny is to allow access unless a specific rule forbids it. © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Job Rotation • The rotation of individuals through different tasks and duties in the organization's IT department. • The individuals gain a better perspective of all the elements of how the various parts of the IT department can help or hinder the organization. • Prevents a single point of failure, where only one employee knows mission critical job tasks. © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Layered Security • Layered security implements different access controls and utilizing various tools and devices within a security system on multiple levels. • Compromising the system would take longer and cost more than its worth. • Potential downside is the amount of work it takes to create and then maintain the system. © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Diversity of Defense • This concept complements the layered security approach. • Diversity of defense involves making different layers of security dissimilar. • Even if attackers know how to get through a system that compromises one layer; they may not know how to get through the next layer that employs a different system of security. © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Security Through Obscurity • Security through obscurity states that the security is effective if the environment and protection mechanisms are confusing or supposedly not generally known. • The concept’s only objective is to hide an object (not to implement a security control to protect the object). • It’s not effective. © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Keep It Simple • The simple security rule is the practice of keeping security processes and tools is simple and elegant. • Security processes and tools should be simple to use, simple to administer, and easy to troubleshoot. • A system should only run the services that it needs to provide and no more. © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Security Topics • Access control • Authentication • Social engineering © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Access Control • Access control is a term used to define a variety of protection schemes. • This is a term sometimes used to refer to all security features used to prevent unauthorized access to a computer system or network. • It’s often confused with authentication. © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Authentication • Authentication deals with verifying the identity of a subject while access control deals with the ability of a subject (individual or process running on a computer system) to interact with an object (file or hardware device). • Three types of authentication – Something you know (password) – Something you have (token or card) – Something you are ( biometric) © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Access Control vs. Authentication • Authentication – This proves that you (subject) are who you say you are. • Access control – This deals with the ability of a subject to interact with an object. • Once an individual has been authenticated, access controls then regulate what the individual can actually do on the system. • Digital certificates – This is an attachment to a message, and is used for authentication. It can also be used for encryption. © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Authentication and Access Control Policies • Group policy – By organizing users into groups, a policy can be made that will apply to all users in that group. • Password policy – Passwords are the most common authentication mechanism. – Should specify: character set, length, complexity, frequency of change and how it is assigned. © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Social Engineering • Social engineering is the process of convincing an individual to provide confidential information or access to an unauthorized individual. • Social engineering is one of the most successful methods that attackers have used to gain access to computer systems and networks. • The technique relies on an aspect to security that can be easily overlooked: people. • Most people have an inherent desire to be helpful or avoid confrontation. Social engineers exploit this fact. • Social engineers will gather seemingly useless bits of information, that when put together, divulge other sensitive information. This is “data aggregation.” © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Security Policies & Procedures • Policy – High-level statements created by management that lay out the organization's positions on particular issues • Security policy – High-level statement that outlines both what security means to the organization and the organization's goals for security • Procedure – General step-by-step instructions that dictate exactly how employees are expected to act in a given situation or to accomplish a specific task © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Acceptable Use Policy • The acceptable use policy outlines the behaviors that are considered appropriate when using a company’s resources. • Internet use policy – This covers the broad subject of Internet usage. • E-mail usage policy – This details whether non-work e-mail traffic is allowed at all or severely restricted. © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Different Security Policies • Change management policy – This ensures proper procedures are followed when modifications to the IT infrastructure are made. • Classification of information policy – This establishes different categories of information and the requirements for handling each category. • Due care and due diligence – Due care is the standard of care a reasonable person is expected to exercise in all situations – Due diligence is the standard of care a business is expected to exercise in preparation for a business transaction. © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Different Security Policies (continued) • Due process policy – Due process guarantees fundamental fairness, justice and liberty in relation to an individual’s rights. • Need-to-know policy – This policy reflects both the principle of need to know and the principle of least privilege. • Disposal and destruction policy – This policy outlines the methods for destroying discarded sensitive information. © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Service Level Agreements • Service level agreements are contractual agreements between entities that describe specificed levels of service, and guarantee the level of service. – A web service provider might guarantee 99.99% uptime. – Penalties for not providing the service are included. © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Human Resources Policies • Employee hiring and promotions – Hiring – Background checks, reference checks, drug testing – Promotions – Periodic reviews, drug checks, change of privileges • Retirement, separation, and termination of an employee – Determine the risk to information, consider limiting access and/or revoking access • Mandatory vacation – An employee that never takes time off may be involved in nefarious activities and does not want anyone to find out. © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Security Models • Confidentiality models – Bell-LaPadula security model • Integrity models – Biba model – Clark-Wilson model © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Bell-LaPadula Security Model • Two principles – Simple security rule (“no read up”) – The *-property (pronounced "star property") principle (“no write down”) • Objective – Protect confidentiality © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Biba Model • Two principles based on integrity levels – Low-water policy (“no write up”) – Ring policy (“no read down”) • Objective – Protect integrity © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Clark-Wilson Model • Uses transactions as a basis for rules • Two levels of integrity – Constrained data items (CDI) • Subject to integrity controls – Unconstrained data items (UDI) • Not subject to integrity controls • Two types of processes – integrity verification processes (IVPs) – transformation processes (TPs) © 2010 Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Model Summary © 2010 Model Objective Policies Bell-LaPadula Confidentiality No read up No write down Biba Integrity No read down No write up Clark-Wilson Integrity Two levels of integrity – UDI and CDI IVP monitor TP (Transformation Processes) Principles of Computer Security: CompTIA Security+® and Beyond, Second Edition Chapter Summary • Define basic terms associated with computer and information security. • Identify the basic approaches to computer and information security. • Distinguish among various methods to implement access controls. • Describe methods used to verify the identity and authenticity of an individual. • Recognize some of the basic models used to implement security in operating systems. © 2010