Security Part-1
advertisement

CS542: Topics in
Distributed Systems
Security
Why are Distributed Systems insecure?
Distributed component rely on messages sent and
received from network.
Is network (especially WAN networks) secure?
» Packets can be intercepted and modified at network layer!
Is client component secure?
Is client component who it claims to be?
Are users of calling components really who they claim
to be?
Security Threats
Leakage: An unauthorized party gains
access to a service or data.
Attacker obtains knowledge of a withdrawal or account
balance, e.g., via eavesdropping
Tampering: Unauthorized change of data,
tampering with a service
Attacker changes the variable holding your personal data
Vandalism: Interference with proper
operation, without gain to the attacker
Attacker does not allow any transactions to your account
E.g., DOS=denial of service
How Attacks are Carried Out
Attacks on Communication Channel / Network
Eavesdropping – Obtaining copies of messages
without authority.
Masquerading – Sending or receiving messages
with the identity of another principal (user or
corporation). Identity theft.
Message tampering – Intercepting messages and
altering their contents before passing them onto
the intended recipient.
Replaying – Intercepting messages and sending
them at a later time.
Denial of Service Attack – flooding a channel or
other resources (e.g., port) with messages.
Addressing the Challenges
Leakage: An unauthorized party gains
access to a service or data.
– Confidentiality : protection against disclosure to
unauthorized individuals.
Tampering: Unauthorized change of data,
tampering with a service
– Integrity : protection against alteration or corruption.
Vandalism: Interference with proper
operation, without gain to the attacker
– Availability : protection against interference with the
means to access the resources.
Security Requirements
Authentication: ensures that sender and receiver are
who they are claiming to be
Data integrity: ensure that data is not changed from
source to destination
Confidentiality: ensures that data is read only by
authorized users
Non-repudiation: ensures that the sender has strong
evidence that the receiver has received the message, and
the receiver has strong evidence of the sender identity. The
sender cannot deny that it has sent the message and the
receiver cannot deny that it has received the message
Security Policies & Mechanisms
A Security Policy indicates which actions each
entity (user, data, service) is allowed or prohibited
to take.
E.g., Only an owner is allowed to make transactions to his
account.
A Security Mechanism implements and enforces
the policy
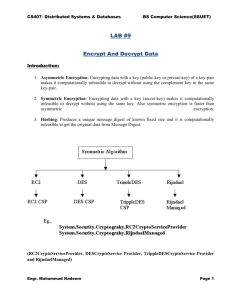
Security Mechanisms
Encryption / decryption: transforming data into something an
attacker cannot understand and vice-versa, i.e., providing a
means to implement confidentiality, as well as allowing user to
check whether data have been modified.
Authentication: verifying the claimed identity of a subject,
such as user name, password, etc.
Authorization: checking whether the subject has the right to
perform the action requested. verify access rights of principal
for resource.
Auditing: tracing which subjects accessed what, when, and
which way. In general, auditing does not provide protection,
but can be a tool for analysis of problems. Mainly an offline
analysis tool, often ex-post.
Designing Secure Systems
• Need to make worst-case assumptions about
attackers:
– exposed interfaces, insecure networks, algorithms and program
code available to attackers, attackers may be computationally
very powerful
– Typically design system to withstand a known set of attacks
(Attack Model or Attacker Model)
– Tradeoff between security and performance impact
• Designing Secure Systems
– Traditionally done as a layer on top of existing protocols.
Three phases:
– Design security protocol
– Analyze Protocol Behavior when under attacks
– Measure effect on overall performance if there were no attacks
(the common-case)
Familiar Names in the Security Literature
Source: G. Coulouris et al., Distributed Systems: Concepts and Design, Third Edition.
Notational Conventions
Source: G. Coulouris et al., Distributed Systems: Concepts and Design, Third Edition.
Cryptographic Terminology
Plain text: the message before encryption.
Cipher text: the message after encryption.
Key: information needed to convert from plain
text to cipher text (or vice-versa).
Function: the encryption or decryption
algorithm used, in conjunction with key, to
encrypt or decrypt message.
Key distribution: How to distribute keys
between senders and receivers
Requirements for modern cryptography
Kerkhoff’s principle: knowledge of encryption algorithm
should not be an advantage
With computers a brute force attempt is possible, i.e. try
every possible substitution until a valid message is
produced.
Computers are good at this, modern schemes must be
computationally hard to solve to remain secure.
15 May 1973 American National Bureau of standards
requests proposals for encryption standard
Data Encryption Standard, DES, developed. Standard
describes DEA, Data Encryption Algorithm
Since November 26, 2001, there’s AES, based on Rijndael
Cryptography
Encoding (encryption) of a message that can only be read
(decryption) by a key.
In shared key cryptography (symmetric cryptography) the
sender and the recipient know the key, but no one else does.
E.g., DES (Data Encryption Standard) – 56 b key operates on 64 b blocks
of data. Notation: KAB (M).
How do Alice and Bob get the shared key KAB to begin with?
In public/private key pairs messages are encrypted with a
published public key, and can only be decrypted by a secret
private decryption key.
Code for E & D
E.g., RSA / PGP keys – at least 512 b long
D(K, {M}K)=M
E(K,M)={M}K
Alice
Encryption
KBpub, E
is “open-source”
(hence known to attacker)
{M}K
Encryption
Decryption
Plain Text
(M)
Plain Text
(M)
Bob
Decryption
KBpriv, D
Cryptography
Shared versus public/private:
Shared reveals information to too many
principles; may need key distribution and
revocation/repudiation mechanisms
In electronic commerce or wide area
applications, public/private key pairs are
preferred to shared keys.
Public/private key encrypt/decrypt ops are
costly
May use hybrid: pub/pri generates a shared
key.
Presentation of many next few protocols
independent of which keying scheme, viz.,
shared or pub/priv
Symmetric Key
Both the sender and the receiver use the
same secret keys
Plaintext
Plaintext
Encrypt with
secret key
Internet
Ciphertext
Decrypt with
secret key
DES/AES: Symmetric Encryption
One key is used to both encrypt and decrypt data
Encryption and decryption functions are often
chosen to be the same
Security should not be compromised by making
function well-known as security comes from secret
keys
DES/AES: Using Secret Keys
Sender and recipient exchange keys through
some secure, trusted, non-network based
means.
Sender encodes message using function and
sends, knowing that only the holder of the key (the
intended recipient) can make sense of it.
Recipient decodes message & knows that only a
key-holding sender could have generated it.
Message can be captured but is of no use.
Data Encryption Standard (DES)
DES encrypts a 64-bit
block of plain text using
a 56-bit key
Three phases
1. Permute the 64 bits in the
block
2. Apply a given operation
16 times on the 64 bits
3. Permute the 64 bits using
the inverse of the original
permutation
1st phase
IP(input)
Round 1
2nd phase
..
.
Round 16
3rd phase
IP-1(input)
key
Initial Permutation (IP)
IP: bit 58 of input becomes 1st bit, bit 50
becomes 2nd bit, etc
58 50 42 34 26 18 10 2 60 52 44 36 28 20 12 4
62 54 46 38 30 22 14 6 64 56 48 40 32 24 16 8
57 49 41 33 25 17 9 1 59 51 43 35 27 19 11 3
61 53 45 37 29 21 13 5 63 55 47 39 31 23 15 7
IP-1: inverse of IP, e.g., IP(1) = 58, IP-1
8 48 16 56 24 64 32 39 7 47 15 55 23 63 31
(58) = 1 40
38 6 46 14 54 22 62 30 37 5 45 13 53 21 61 29
36 4 44 12 52 20 60 28 35 3 43 11 51 19 59 27
34 2 42 10 50 18 58 26 33 1 41 9 49 17 57 25
2nd Phase: Operation in each round
16 rounds
Each round i select a 48
bit key Ki from the original
56 bit key K. Perform (F is
a given function):
Li Ri 1
Ri Li 1 F ( Ri 1 , Ki )
0
63
63
32
Li-1
31
0
Ri-1
F
+
Li
Ri
Ki
Discussion of DES
Even through the DES algorithm is well known, but the key or
cipher is difficult to break using analytical methods.
Using a brute-force attack by simply searching for a key is
possible. However, for 56-bit key, there are 256 possible key
combinations, if we could search one key in 1 µs, then we
need 2283 years to try all keys. (Distributed.net broke a DES56 within 22 hours and 15 minutes, by using 100,000 PCs).
Use 3DES (K1, K2, K3), or DES-128 for high security.
Encrypting Larger Messages
Initialization Vector (IV) is a random number
generated by sender and sent together with the
ciphertext
IV
Block1
Block2
Block3
Block4
+
+
+
+
DES
DES
DES
DES
Cipher1
Cipher2
Cipher3
Cipher4
Cipher block chaining (CBC)
Each plaintext block is combined with the preceding
ciphertext block using XOR
i.e., ciphertextn+1 = plaintextn+1 ciphertextn
For decryption, the opposite is done, since XOR is idempotent, it
works.
Weaknesses: if the same message is sent to multiple
locations, they’ll be the same and the attacker may infer.
To add different piece of plaintext at the beginning of each message
A Scheme of Cipher Block Chaining
Source: G. Coulouris et al., Distributed Systems: Concepts and Design, Third Edition.
Stream ciphers
CBC is inappropriate for some apps., e.g.,
encryption of telephone conversations
==> Stream ciphers solve this problem
Main idea is to construct a keystream generator.
It’s analogous to adding “noise” to the system
A Stream Cipher
Source: G. Coulouris et al., Distributed Systems: Concepts and Design, Third Edition.
DES Properties
Provide confidentiality
» No mathematical proof, but practical evidence
suggests that decrypting a message without
knowing the key requires exhaustive search
» To increase security use triple-DES, i.e., encrypt
the message three times
Secret Key Encryption
Disadvantage: Number of keys needed increases
quadratically by number of objects (one key per pair of
communicating objects…)
Another problem with private key:
Key distribution
Public Key (Asymmetric) Encryption overcomes these
problem
Public-Key Cryptosystems: RSA
Asymmetric algorithm: a private and a public key
are used
First proposed by Diffie and Hellman
Basis: Trap-door functions
Are special type of one-way-functions that has a secret
exit, it is easy to compute it in one-way but it is infeasible
to compute the inverse if the secret is unknown
Two keys, Ke and Kd
D(Kd, E(Ke, M)) = M
RSA (Rivest, Shamir, and Adelman) Algorithm
Public-Key Cryptography: RSA
(Rivest, Shamir, Adleman)
Sender uses a public key
» Advertised to everyone
Receiver uses a private key
Plaintext
Plaintext
Encrypt with
public key
Internet
Ciphertext
Decrypt with
private key
Asymmetric Encryption
Gives 'one-way' security.
Two keys generated, one used with
decryption algorithm (private key) and one
with encryption algorithm (public key).
Generation of private key, given public key is
computationally hard.
Does not need secure key transmission
mechanism for key distribution.
Asymmetric Encryption: Using Public Keys
Recipient generates key pair.
Public key is published by trusted service.
Sender gets public key, and uses it to encode
message.
Recipient decrypts message with its private
key.
Replies can be encoded using sender’s public
key from the trusted distribution service.
Message can be captured but is of no use.
RSA Algorithm
Generating the private and public key
requires four steps:
Choose two very large prime numbers, p and q
Compute n = p x q and z = (p – 1) x (q – 1)
Choose a number d that is relatively prime to z
Compute the number e such that e x d = 1 mod z
Generating Public and Private Keys
Public key consist of pair (n, e)
Private key consists of pair (n, d)
RSA Encryption and Decryption
Encryption of message block m:
» c = me mod n
Decryption of ciphertext c:
» m = cd mod n
Example (1/2)
Choose p = 7 and q = 11 n = p*q = 77
Compute encryption key e: (p-1)*(q-1) =
6*10 = 60 chose e = 13 (13 and 60 are
relatively prime numbers)
Compute decryption key d such that 13*d =
1 mod 60 d = 37 (37*13 = 481)
Example (2/2)
n = 77; e = 13; d = 37
Send message block m = 7
Encryption: c = me mod n = 713 mod 77 = 35
Decryption: m = cd mod n = 3537 mod 77 = 7
Properties
Confidentiality
A receiver B computes n, e, d, and sends out (n, e)
» Everyone who wants to send a message to A uses (n,
e) to encrypt it
How difficult is to recover d ? (Someone that can do
this can decrypt any message sent to B!)
Recall that
d is relatively prime to (p-1)*(q-1)
So to find d, you need to find prime factors p and q
» This is provably very difficult
Public Key Encryption
Transmission of message is secure
» as only B has the matching private key to decrypt message
Differences between public and secret key
» One pair of keys generated for every object, so number
of keys is linear to number of objects
Because different functions:
» use of public keys is more complicated for reply messages. A
must generate pair of keys and publish its public key, which B
acquires to encrypt reply message
Pretty Good Privacy
Public Key encryption used in PGP
Generally available, and can be used for
» encryption of messages
» digital signatures.
PGP combines DES and RSA
» DES fast, but symmetric, hence key
distribution problem
» RSA slower, but no key distribution problem
» Solution: Use RSA to encrypt and distribute
key for DES encryption!!!