Document
advertisement

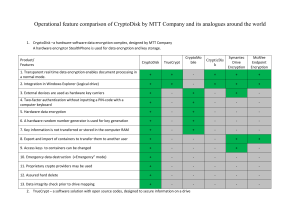
CryptDB: Processing Queries on an Encrypted Database Raluca Ada Popa Catherine M.S. Redfield Nickolai Zeldovich Hari Balakrishman Presented By: Jeremy Winters Agenda • • • • • • • • Need Threat Model Implementation Types of Encryption and Onions Query Processing Experimental Evaluation Performance Evaluation Summary Need “…in a recent attack on the Sony Playstation Network, attackers apparently gained access to about 77 million personal user profiles, some of which included credit card information.” Threat Model CryptDB Passive Attacks – Compromised hardware – System Administrators – Cloud solutions Implementation Implementation • 3 Components • • • Application Proxy DBMS Encryption Types Encryption Types Random (RND) – Maximum security Deterministic (DET) – Plaintext results in consistent ciphertext Order-Preserving Encryption (OPE) – 100 < 200 | 4ex5d < 7gfa3 Encryption Types Homomorphic Encryption (HOM) – Math functions (ex. Addition) Join (JOIN and OPE-JOIN) – Equality Joins Word Search (SEARCH) – LIKE Goal ‘Our goal is to use the most secure encryption schemes that enable running the requested queries.’ Onions Data Sensitivity Use in Queries Query Processing Query Processing Steps 1. Application issues query, intercepted by proxy and rewritten. 2. If necessary, adjust column encryption level. 3. Proxy sends encrypted query to DBMS for execution. 4. Encrypted result returned, proxy decrypts, returns to application. Query Processing Experimental Evaluation Experimental Evaluation Performance Evaluation Performance Evaluation • .60ms (~ 26%) performance degradation in queries issued per second. • • • 24% mysql-proxy 23% encryption / decryption 53% parsing and processing queries Summary CryptDB CryptDB utilizes several encryption technologies to take steps to secure data within your client/server applications from passive attacks. More secure that encryption provided by DBMS. DBMS decrypts data to perform queries. Supports most relational queries – not all. Further research is being done here. Questions?