Cryptography As A Service
advertisement

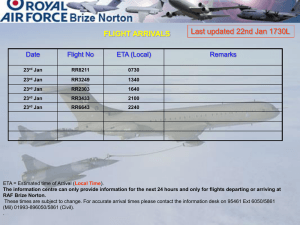
Cryptography As A Service Barclays Crypto Application Gateway and Beyond 23rd May 2013 George French – Barclays Dan Cvrcek – Smart Architects Unrestricted distribution Cryptography As A Service Key Management Applications Application Cryptography Interface Cryptography Policy Enforcement Application Authentication Application Key Management BCAG / CSG Service Vendor HSM interfaces HSMs 2 | Cryptography as a Service 23rd May 2013 Unrestricted distribution Application Cryptography Audit Logging Operations and Audit Beginning … Cryptography and Business Requirement Solution lead time Encrypt data (... and decrypt possibly) day Secure key generation and management, recovery months Decryption after 30 years, huge data collections (tera bytes), multiple application support, integration > year Support and recovery after incidents Multiply by 2+ As surprising as it may sound there are very few security products that would actually work and could be managed with a small operational team. The main culprits: - integration, scalability, reliability, support 3 | Cryptography as a Service 23rd May 2013 Unrestricted distribution Crypto Service Must Provide For … • Audit Cryptography is deployed as a control to mitigate a risk it is therefore necessary to be able to demonstrate that the control is effective. • Cryptographic Management • The problem with cryptography is the decryption process. • NEVER GIVE DEVELOPERS OPTIONS WHEN ENCRYPTING DATA • Centralised Management • Small teams even in multinational companies • Monitoring of usage / capacity • BAU operational tasks • Security audits • Information for business units 4 | Cryptography as a Service 23rd May 2013 Unrestricted distribution Problem Space for The Use of Cryptography What we are trying to manage Business •Capturing Business Requirements •Provision of a defined operational model •Project/Bespoke development •Testing 5 | Cryptography as a Service 23rd May 2013 Unrestricted distribution Problem Space for The Use of Cryptography What we are trying to manage Business Build • Capturing Business Requirements • Provision of a defined service • Risk Mitigation • Bullet •Requires Specialised knowledge •Meet requirements •Internal governance and standards compliance •Infrastructure build •Change management 6 | Cryptography as a Service 23rd May 2013 Unrestricted distribution Problem Space for The Use of Cryptography What we are trying to manage Business Build • Capturing Business Requirements. • Requires Specialised knowledge • Provision of a defined service. • Meet requirements • Risk Mitigation • Internal governance and standards compliance • Bullet • Infrastructure build • Change management Operation •Hardware Utilisation •Project model delivers variances •Patch and Security Vulnerability Management •Operation impact of outages •“Non-functional” Requirements 7 | Cryptography as a Service 23rd May 2013 Unrestricted distribution Problem Space for The Use of Cryptography What we are trying to manage Business Build • Capturing Business Requirements. • Requires Specialised knowledge • Provision of a defined service. • “The usual suspects” • Risk Mitigation • Internal governance and standards compliance • Bullet Operation Compliance • Hardware Utilisation • Project model delivers variances • Patch and Security Vulnerability Management • Operation impact of outages •Regulatory and scheme compliance •Internal Audit •Customer Due diligence 8 | Cryptography as a Service 23rd May 2013 Unrestricted distribution Problem Space for The Use of Cryptography What we are trying to manage Business Build • Capturing Business Requirements. • Requires Specialised knowledge • Provision of a defined service. • “The usual suspects” • Risk Mitigation • Internal governance and standards compliance • Bullet Operation • Hardware Utilisation • Project model delivers variances • Patch and Security Vulnerability Management Compliance • Regulatory and scheme compliance • Internal Audit • Customer Due diligence • Operation impact of outages ... I know nothing short of impossible but here we go 9 | Cryptography as a Service 23rd May 2013 Unrestricted distribution BCAG Cryptographic Approach Separating use from management and configuration – Use (business units): Request system authentication credentials (e.g., password); Do Crypto – e.g., Api.Encrypt(“CC_Number”, “ME”, “Main_DB”, <transaction>) – Management (BU and Crypto Operations): Policy – what business functions (e.g., encrypt credit card number), how many parties (DB, web app, middleware, …). – Technical (Crypto Operations): how many keys, algorithms, crypto modes, key lengths, key validity, and so on. 10 | Cryptography as a Service 23rd May 2013 Unrestricted distribution BCAG Business Approach Pay for what you use – Centralised use of resources (people, hardware, network, …) HSMs used “per operation”, not “per project”. – Commissioning of cryptographic system components by Crypto Operations skills; volume; and single place for deployment and management -> strategy. Decoupling components (i.e., HSM) from applications – Eliminate vendor lock-in; and – Introduce service-based architecture with replaceable products. 11 | Cryptography as a Service 23rd May 2013 Unrestricted distribution What Does It Look Like – Architectural Blocks Business Crypto support (1st line) Solution support (2nd line) Product support (3rd line) 12 | Cryptography as a Service 23rd May 2013 Unrestricted distribution System Mechanics - Onboarding Administrative process for enrolling new business application to BCAG 1. Capture Business Requirements – The most difficult part as the business does not usually have a structured description of cryptographic requirements 2. Convert BR to policy specification – Semi-automated process that generates a BCAG policy definition 3. Amend BCAG access control with new “user” privileges 4. Key generation and deployment (manual or semi-automatic process) 5. Use. 13 | Cryptography as a Service 23rd May 2013 Unrestricted distribution Mechanics - Operation And 3 pieces of information that have to align: 1. Authentication details = username and password 2. Policy = username and authorised operations and key locator data 3. Crypto Key definitions = key value and key locator data 14 | Cryptography as a Service 23rd May 2013 Unrestricted distribution Doing Crypto - Key Lookup • Traditionally • Key Label = Key Value • You change a key value, you get a new key label • The new key label has to be propagated to all applications using the old key • BCAG Approach • Structured key locators: user, function, base_function, from, to • Algorithm for locating keys • Dynamic, as it does not use 1:1 mapping but lookup algorithm • Efficient – 2 layers of caching of recently used keys 15 | Cryptography as a Service 23rd May 2013 Unrestricted distribution Key Lookup – BCAG 16 | Cryptography as a Service 23rd May 2013 Unrestricted distribution Beyond • Large data processing; we talk about • • Daily encryption of giga and terabytes of data • Protection of archives with 100,000s of DB tables Composite cryptography • Grouping cryptographic operations into transactions that require specific order of operations • Breach of a transaction is a potential data compromise • Centralised key management • Replacement of manual key loading to HSMs with an automatic process to minimise human errors and increase security 17 | Cryptography as a Service 23rd May 2013 Unrestricted distribution Beyond … banking • Platform for mobile app cryptography • Platform for financial services for future applications • • • Providing API and system for banking transactions to developers without actually building a bank Being able to build own virtual Central Bank with a few button clicks All this requires something like BCAG to: • Access to payment schemes (VISA, MasterCard) • Strong cryptographic system able to ensure pre-defined security properties (like cheating, counterfeiting … within the model of a virtual world) • In some cases compliance with financial regulations 18 | Cryptography as a Service 23rd May 2013 Unrestricted distribution Thank you for your attention! Dan@SmartArchitects.co.uk George.French@Barclays.com Security Policy – Two Abstractions Use - Visible for Business Units • Users • just names, possibly with domain (e.g., LDAP) • And authentication options (specs for tickets) • User groups – just names • Alias – just names for required crypto operations Manage - Internal to Crypto Management • Params – the technical bit, e.g. • • • • • • • [PARAMS CookieParams] ManagedEncryption=false Cipher=AES KeySize=128 ModeOfOperation=CBC IV=Random Padding=NoPad 20 | Cryptography as a Service 23rd May 2013 Unrestricted distribution Doing Crypto - Key Lookup as You Know It 21 | Cryptography as a Service 23rd May 2013 Unrestricted distribution