Project Proposal Presentation
advertisement
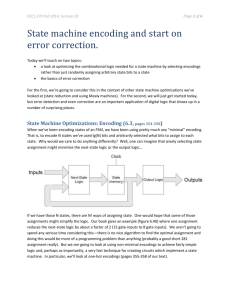
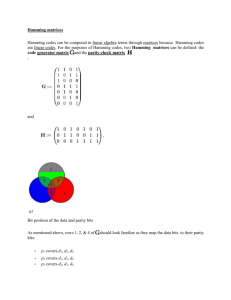
FEC Linear Block Coding Matthew Pregara & Zachary Saigh Advisors: Dr. In Soo Ahn & Dr. Yufeng Lu Dept. of Electrical and Computer Eng. 2 Table of Contents Motivation Introduction Hamming Code Example Tanner Graph/Hard Decision Decoding Simulink Simulation on Hamming Code VHDL Simulation Results Low Density Parity Check Code Timeline and Division of Labor Conclusion 3 Motivation FEC: Forward Error Correction Adds redundancy to message. Detects AND Corrects Errors. ARQ: Automatic Repeat Request Detects errors and requests retransmission. 4 Motivation (taken from [1]) 5 Redundancy Add extra bits (Parity Bits) to message. Increases number of bits sent, requiring larger transmission bandwidth. Decreases Parity number of errors in message. bits Information from multiple message bits 6 Linear Block Coding Block Codes are denoted by (n, k). k = message bits (message word) n = message bits + parity bits (codeword) # of parity bits: m = n - k Code Rate R = k/n Example: (7,4) code 4 message bits +3 parity bits = 7 codeword bits Code rate R = 4/7 7 Block Coding Diagram Transmitter Channel Receiver e m G (encoder matrix) u + + r r H’ (decoder matrix) S Error Lookup Table u’ Remove Parity bits m’ e m = message bit word u = code word r = received code word with error S = syndrome u’ = corrected code word m’ = received message word 8 Linear Block Coding cont. Error Detection T S rH (u e) H T u H eH T T mG H eH T S eH T T 10 Hamming Code G matrix is derived from a primitive polynomial, a factor of xn +1. Systematic G matrix is obtained from G matrix. H matrix is determined from systematic G matrix. G = [Ik | P], where P = parity matrix H = [PT | In-k]; HT = P I n-k 11 Encoding Message m, made of k bits, is post-multiplied by the G matrix using Modulo-2 arithmetic. Transmitter m G (encoder matrix) Channel Receiver e u + + r r H’ (decoder matrix) S Error Lookup Table e u’ Remove Parity bits m’ 12 Constructing G Starts with xn+1, n = 7. Factorize x7+1 Find = (x+1)(x3+x2+1)(x3+x+1). solution for one of the terms. (x3+x2+1) => [1 1 0 1] 13 Fill matrix with solution (shifting 1 entry in each row) 1 1 0 1 1 1 0 1 1 1 0 1 1 1 0 1 Fill empty entries with 0’s 1 0 0 0 0 1 0 0 0 0 1 0 0 0 0 1 1 0 1 1 0 1 1 0 1 0 1 1 0 1 0 1 0 0 1 0 0 0 0 1 Result is the systematic G matrix Find RREF 1 0 0 0 1 1 0 0 1 1 1 0 0 1 1 1 1 0 0 0 0 0 0 1 0 0 0 1 0 0 0 1 I4 1 1 0 0 1 1 1 1 1 1 0 1 P 14 Encoding m1 m2 m3 m1 m2 1 0 m4 0 0 m3 0 0 0 1 0 0 0 1 0 0 0 1 m4 1 1 0 0 1 1 1 1 1 1 0 1 p1 p2 p1 m1 m3 m4 p2 m1 m2 m3 p3 m2 m3 m4 p3 15 Encoding Example 1 0 1 0 1 1 0 0 0 0 0 1 0 0 0 1 0 0 0 1 1 1 0 0 1 1 1 1 1 1 0 1 1 0 1 1 p1 p2 p3 p1 m1 m3 m4 1 1 1 1 p2 m1 m2 m3 1 0 1 0 p3 m2 m3 m4 0 1 1 0 1 0 1 1 1 0 0 16 Decoding Received codeword of n bits is postmultiplied by HT to obtain the syndrome. Transmitter Channel Receiver e m G (encoder matrix) u + + r r H’ (decoder matrix) S Error Lookup Table e u’ Remove Parity bits m’ 17 Decoding Recall: 1 G = [Ik | P]; P = parity matrix 0 T | H = [P In-k ] 1 P T H I S = syndrome 1 n-k 1 m1 m2 m3 m4 p1 p2 1 0 1 p3 1 1 0 0 1 0 1 1 1 1 0 1 0 0 1 0 0 1 1 1 1 0 0 1 0 0 S1 S2 0 0 1 1 1 0 0 1 S3 S1 m1 m 3 m 4 p1 S2 m1 m 2 m 3 p 2 S3 m 2 m 3 m 4 p 3 18 Syndrome Table 19 Example continued correctcodeword: 1 0 1 1 1 0 0 S 0 0 0 corruptedcodeword: 1 1 1 1 1 0 0 S 0 1 1 20 Correcting Errors In this case the 2nd bit is corrupted Invert the corrupted bit according to the location found by the syndrome table S 0 1 1 1 1 1 1 1 0 0 0 1 0 0 0 0 0 1 0 1 1 1 0 0 21 Tanner Graph and Hard Decision Decoding (8,4) Example V1 (2458) C1 V2 V3 (1236) (3678) C2 V4 V5 C3 V6 (1457) C4 V7 V8 V1 V2 0 1 H 0 1 1 1 0 0 V3 V4 V5 V6 V7 V8 0 1 1 0 1 0 0 1 1 0 0 1 0 1 1 0 0 0 1 1 1 0 1 0 C1 C2 C3 C4 22 Hard Decision Decoding C1 V1 1 V2 1 0 V3 C2 V4 V5 C3 V6 C4 V7 V8 Check Nodes C1 1 0 1 0 1 C2 C3 C4 Activities Receive V2→ 1 V4→ 1 V5→ 0 V8→ 1 Send 0 → V2 0 → V4 1 → V5 0 → V8 Receive V1→ 1 V2→ 1 V3→ 0 V6→ 1 Send 0 → V1 0 → V2 1 → V3 0 → V6 Receive V3→ 0 V6→ 1 V7→ 0 V8→ 1 Send 0 → V3 1 → V6 0 → V7 1 → V8 Receive V1→ 1 V4→ 1 V5→ 0 V7→ 0 Send 1 → V1 1 → V4 0 → V5 0 → V7 23 Variable Node Decisions Variable Nodes yi Messages from Check Nodes Decision V1 1 C2 → 0 C4 → 1 1 V2 1 C1 → 0 C2 → 0 0 V3 0 C2 → 1 C3 → 0 0 V4 1 C1 → 0 C4 → 1 1 V5 0 C1 → 1 C4 → 0 0 V6 1 C2 → 0 C3 → 1 1 V7 0 C3 → 0 C4 → 0 0 V8 1 C1 → 0 C3 → 1 1 24 Simulink Model of (7,4) Hamming Code Eb 5dB N0 Eb 9dB N0 26 Simulation Results Field Programmable Gate Array(FPGA) 27 Encoding Decoding 28 Simulation Results Hardware Description Language 29 Low Density Parity Check Code Offers performance close to Shannon’s channel capacity limit. Can correct multiple bit errors. Low decoder complexity. (taken from [1] 31 LDPC Code Start The entries of 1 in H are sparsely populated From The with H matrix first the H matrix, find the systematic G matrix entries of 1 in G are not sparsely populated, causing encoder complexity. 32 LDPC Code Decoding is done iteratively. To operate close to Shannon limit under very low SNR, the dimensions of H matrix are very large. For real-time operations, the dimensions of H matrix are constrained by hardware , and decoding time allowed, and others. Division of Labor Zack MATLAB Encoder Simulink design of encoder/channel Implementation of VHDL on FPGA Performance analysis of FPGA implementaiton Matt MATLAB Decoder Simulink design of Decoder Implementation of Xilinx system generator Performance analysis of MATLAB/Simulink implementation Timeline 29-Jan-13 MATLAB Implementation 18-Feb-13 Performance Analysis 10-Feb-13 Simulink Implementation Feb 1/25/2013 13-Mar-13 FPGA Implementation 17-Apr-13 Performance Analysis 2-Mar-13 System Generator Design Mar 28-Apr-13 Student Expo 14-May-13 Presentation Apr May 5/15/2013 35 Conclusion LDPC coding is to be implemented. Preliminary investigations are performed. Examined Hamming coder/decoder under Matlab and Simulink environment. Tanner graph representation of LDPC examples researched. Plans to choose an LDPC coding scheme and to implement it using FPGA. 36 References [1] Valenti, Matthew. Iterative Solutions Coded Modulation Library Theory of Operation. West Virginia University, 03 Oct. 2005. Web. 23 Oct. 2012. <www.wvu.edu>. [2] B. Sklar, Digital Communications, second edition: Fundamentals and Applications, Prentice-Hall, 2000. [3] Xilinx System Generator Manual, Xilinx Inc. , 2011. 37 Q and A’s Thank Any you for listening. questions or suggestions are welcome.