- W3Professors
advertisement

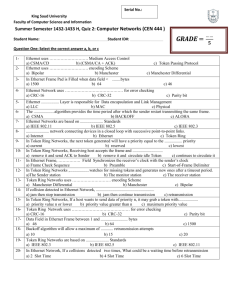
Contributed by: Anubhooti Malhotra Himani Sharma BCA-2(A) The Institution of Electrical and Electronics Engineers (IEEE) has developed several standards for LANs. These standards are collectively known as IEEE 802 or Project 802. The IEEE project 802 divides data link layer into two sub layers: Logical link control (LLC) and Medium access control (MAC). LLC provides one single data link control protocol for all IEEE LANs. This single LLC protocol can provide interconnectivity between different LANs as it makes the MAC sub layer transparent. On the other hand MAC provides different protocols for the different LANs. 802.1 Network management and Internetworking . 802.2 Logical Link Control (LLC). 802.3 Ethernet or CSMA/CD. 802.4 Token Bus. 802.5 Token Ring. 802.6 Metropolitan Area Networks (MAN) or Distributed Queue Dual Bus (DQDB). 802.7 Band pass Technical Advisory Group. 802.8 Fibre Optic Technical Advisory Group. 802.9 Integrated Data and Voice Network. 802.10 Security Working Group. 802.11 Wireless LAN. 802.12 Demand priority 802.13 802.14 Cable Modems 802.15 Wireless PAN 802.15.1 Bluetooth certification 802.15.4 ZigBee certification 802.16 Broadband Wireless Access(WiMax certification) 802.16e (Mobile) Broadband Wireless Access 802.16.1 Local Multipoint Distribution Service 802.17 Resilient Package Ring 802.18 Radio Regulatory TAG 802.19 Coexistence TAG 802.20 Mobile Broadband Wireless Access 802.21Media Independent Handoff 802.22 Wireless Regional Area Network 802.23 Wireless ISDN System IEEE 802.3 supports a LAN standard originally developed by Xerox and later extended by a joint venture between Digital Equipment Corporation, Intel Corporation, and Xerox. This was called Ethernet. IEEE 802.3 defines two categories: baseband and broadband. The word base specifies a digital signal. The word broad specifies an analog signal. IEEE divides the baseband category into five different standards: 10Base5, 10Base2, 10Base-T, 1Base5, and 100Base-T. The first num (10, 1, 100) indicates the data rate in Mbps. The last number or letter (5, 2, 1, or T) indicates the maximum cable length or the type of cable. Carrier Sense Multiple Access with Collision Detection Whenever multiple users have unregulated access to a single line, there is a danger of signals overlapping and destroying each other. Such overlaps, which turns the signals into unusable noise, are called collisions. As traffic increases on a multiple access link, so do collisions. A LAN therefore needs a mechanism to coordinate traffic, minimize the number of collisions that occur, and maximize the number of frames that are delivered successfully. In CSMA system, any workstation wishing to transmit must first listen for existing traffic on the line. A device listens by checking for a voltage. If no voltage is detected, the line is considered idle and the transmission is initiated. CSMA cuts down on the number of collisions but does not eliminate them. Collisions can still occur. If another station has transmitted too recently for its signal to have reached the listening station, the listener assumes the line is idle and introduces its own signal onto the line. The final step is the addition of collision detection (CD). In CSMA/CD the station wishing to transmit first listens to make certain the link is free, then transmits its data, then listens again. During the data transmission, the station checks the line for the extremely high voltages that indicate a collision. If a collision is detected, the station quits the current transmission and waits a predetermined amount of time for the line to clear, then sends its data again. Each station on an Ethernet network (such as a PC, workstation, or printer) has its own network interface card (NIC). The NIC usually fits inside the station and provides the station with a six byte physical address. The number on the NIC is unique. The baseband system use Manchester digital encoding. There is one broadband system, 10Broad36. Ethernet LANs can support data rates between 1 and 100 Mbps. Preamble: The first field of the 802.3 frame, the preamble, contains seven bytes of alternating 0s and 1s that alert the receiving system to the coming frame and enable it to synchronize its input timing. Start frame delimiter (SFD): The second field of the 802.3 frame signals the beginning of the frame. The SFD tells the receiver that everything that follows is data, starting with the addresses. Destination Address (DA): The destination address (DA) field is allotted six bytes and contains the physical address of the packet’s next destination. Source Address (SA): The source address (SA) field is also allotted six bytes and contains the physical address of the last device to forward the packet. Length/type of PDU: These next two bytes indicate the number of bytes in the coming PDU. 802.2 frame (PDU): This field of the 802.3 frame contains the entire 802.2 frame as modular, removable unit. CRC: The last field in the 802.3 frame contains the error detection information in this case a CRC-32. The first of the physical standards defined in the IEEE 802.3 model is called 10Base5, thick Ethernet, or Thicknet. The nickname derives from the size of the cable, which is roughly the size of garden hose and too stiff to bend with your hands. 10Base5 is a bus topology LAN that uses baseband signalling and has maximum segment length of 500 meters. The second Ethernet implementation defined by the IEEE 802 series is called 10Base2 or thin Ethernet. Thin Ethernet provides an inexpensive alternative to 10Base5 Ethernet, with the same data rate. The advantages of thin Ethernet are reduced cost and ease of installation. It also uses a bus topology. o The most popular standard defined in the IEEE 802.3 series is 10Base-T, a star topology LAN using unshielded twisted pair (UTP) cable instead of coaxial cable. o It supports a data rate of 10 Mbps and has a maximum length of 100 meters. Star LAN is an AT & T product used infrequently today because of its slow speed. At only 1 Mbps, it is 10 times slower than the three standards discussed above. What is interesting about Star LAN is its range, which can be increased by a mechanism called Daisy Chaining. Like 10Base-T, star LAN uses twisted pair cable to connect stations to a central intelligent hub. Local area networks have a direct application in a factory automation and process control, where the nodes are computers controlling the manufacturing process. In this type of application, real time processing with minimum delay is needed. Processing must occur at the speed as the objects moving along the assembly line. Furthur….. Ethernet Is not suitable protocol for this purpose because the number of collisions is not predictable and the delay in sending data from the control centre to the computers along the assembly line is not a fixed value. Token Bus combines the features of Ethernet and Token Ring. It combines the physical configuration of Ethernet and collision free feature of Token Ring. Token Bus is a physical bus that operates as a logical ring using tokens. Stations are logically organized into a ring. A token is passed among stations. If a station wants to send data, it must wait and capture the token. However, like Ethernet, stations communicate via a common bus. Token Bus is limited to factory automation and process control and has no commercial application in data communication. Also, the details of the operation are very involved. When a station passes the token, it sends a token to its logical neighbour irrespective of where that station is physically located on the cable. MAC SUB LAYER When the ring is initialized, stations are inserted into it in order of station address, from highest to lowest. Token passing is done from high to low address. Whenever a station acquires the token, it can transmit frames for a specific amount of time. If a station has no data, it passes the token immediately upon receiving it. The Token Bus defines four priority classes, 0, 2, 4, and 6 for traffic, with 0 the lowest and 6 the highest. Each station is internally divided into four substations, one at each priority level i.e. 0, 2, 4 and 6. ring. As input comes into the MAC sub layer from above, the data are checked for priority and routed to one of the four substations. Thus each station maintains its own queue of frames to be transmitted. When a token comes into the station over the cable, it is passed internally to the priority 6 substation, which can begin transmitting its frames, if it has any. When it is done or when its time expires, the token is passed to the priority 4 substation, which can then transmit frames until its timer expires. After this the token is then passed internally to priority 2 substation. This process continues until either the priority 0 substation has sent all its frames or its time expires. After this the token is passed to the next station in the ring. FRAME FORMAT The various fields present in the frame format are: Preamble: This field is 1 byte long. It is used for synchronization. Start Delimiter: This one byte field marks the beginning of frame. Frame Control: This one byte field specifies the type of frame. It distinguishes data frame from control frames. For data frames it carries frame’s priority. Destination Address: It specifies 2 to 6 bytes destination address. Source Address: It specifies 2 to 6 bytes source address. Data: This field may be up to 8182 bytes long when 2 bytes address are used & up to 8174 bytes long when 6 bytes address is used. Checksum: This 4 byte field detects transmission errors. End Delimiter: This one byte field marks the end of frame. Token Ring resolves this uncertainty by requiring that stations take turns sending data. Each station may transmit only during its turn and may send only one frame during each turn. The mechanism that coordinates this rotation is called Token passing. A token is a simple placeholder frame that is passed from station to station around the ring. Token Ring resolves this uncertainty by requiring that stations take turns sending data. Each station may transmit only during its turn and may send only one frame during each turn. The mechanism that coordinates this rotation is called Token passing. A token is a simple placeholder frame that is passed from station to station around the ring. ADDRESSING Token ring uses a 6-byte address which is imprinted on the NIC card similar to Ethernet addresses. ELECTRICAL SPECIFICATION Signaling: Token ring uses differential Manchestar encoding. Data rate: token ring supports data rates of upto 16 Mbps. References Castelli, Matthew (2002). Network Consultants Handbook. Cisco Press. ISBN 1-58705-039-0. Gallo, Michael; Hancock, William M. (2001). Networking Explained. Digital Press. ISBN 1-55558-252-4. External links IEEE 802.5 Web Site Get the IEEE 802.5 standard Troubleshooting Cisco Router Token Ring Interfaces Futureobservatory.org discussion of IBM's failure in token ring technology 802 Committee website IEEE 802 Standards