Enterprise network
advertisement

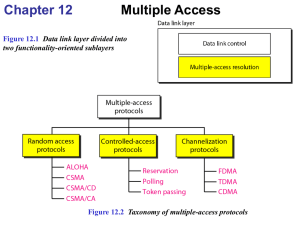
Enterprise network • • • • • • • • • 8.1:Introduction 8.2:LANs 8.3:Ethernet / IEEE802.3 8.4:Token ring 8.5:Bridges 8.6:FDDI 8.7:High-speed LANs 8.8:LAN protocol 8.9:Multicast LAN interconnect technologies 8.1:Introduction • PSTN • ISDN • PBX (private branch exchange) 8.2:LANs • LANs are used to interconnect distributed communities of end systems • To ensure the transmission bandwidth is shared fairly between all of the attached stations, a number of different medium access control (MAC) methods are used. These include (CSMA/CD) and Token ring 8.3:Ethernet / IEEE802.3 • Ethernet networks – and the more recent derivative IEEE802.3 – are used extensively in technical and office environment • CSMA/CD – All the stations are attached directly to the same cable/bus ,it is said to operate in a multiple access mode – The bus operates in the broadcast mode which means that every frames transmitted is received by all the other stations that are attached to the bus – Because of the broadcast mode ,this will result in the contents of the two frames being corrupted and a collision is said to have occurred CSMA/CD Protocol • Carrier Sense before transmission • Carrier Sense while transmission • Collision: Two or more stations transmitting simultaneously • Backoff: Random delay after collision • Deference: Defers transmission if channel is sensed busy • Collision Window (Slot time): Round-trip propagation delay time plus some carrier sense time. In IEEE 802.3, this value is defined to be 51.2 us. CSMA/CD Collision Handling • Collision Signal is generated by Physical layer. • Jam signal (collision enforcement): To make sure that all stations involved in the collision will detect collision. A pattern of 32 bits. • Collision backoff and retransmission method (Truncated Binary Exponential Backoff Algorithm, BEBA): – n : number of collisions experienced (n <= 16) – k : Min (n,10) -- Truncation – r : Random delay time (unit: slot time) between 0 <= r < 2k CSMA/CD worse-case collision detection Hub configuration principles IEEE 802.3 Frame Format 8.4:Token ring • All the stations are connected together by a set of unidirectional links in the form of a ring and all frame transmissions between any of the stations take place over it by circulating the frame around the ring • Only one frame transfer can be in progress over the ring at a time • Fig 8.5 Token ring network operation Token ring wiring configuration Token ring Frame Format 8.5:Bridges • There are two types of bridges , the one are used with Ethernet LANs, knows as transparent bridges , and the others with token ring LANs, known as source routing bridges. Bridge vs Repeater 8.5.1:Transparent bridges • With a transparent bridge, as with a repeater,the presence of one (or more) bridges in a route between two communicating stations is transparent to the two stations . All routing decisions are made exclusively by the bridge(s) • Fig 8.12 • A bridge maintains a forwarding database • Bridge learning – Forwarding database to be created in advanced Transparent bridges(cont.) 8.5.2:Source routing bridges • The major difference between a LAN base on source routing bridges and one base on spanning tree bridges is that with the latter the bridges collectively perform the routing operation in a way that is transparent to the end stations. Conversely, with source routing , the end stations perform the routing function. • Fig 8.15 Token ring Frame Format Example 8.6:FDDI • FDDI is an optical fiber-based ring network that supports a bit rate of 100 Mbps . It can used for the interconnection of segments spread over a wider geographical area than a single building, such as a university campus or manufacturing plant. • Fig 8.18 • Use two counter-rotating rings to enhance reliability:primary ring and secondary ring • Two type of station: DAS and SAS • Fig 8.19 Physical interface FDDI Frame Format 8.7:High-speed LANs • 8.7.1:Fast Ethernet • 8.7.2:Switched Fast Ethernet • 8.7.3:Gigabit Ethernet 8.7.1:Fast Ethernet • Fast Ethernet was to use the same shared, halfduplex transmission mode as Ethernet but to obtain a*10 increase in operational bit rate over 10BaseT while at the same time retaining the same wiring systems , MAC method , and frame format. • The major technological hurdle to overcome with Fast Ethernet was how to achieve a bit rate of 100Mbps over 100m of UTP cable. • Fig 8.26 Collision detection • Fig 8.28 • Detect a collision by detecting a signal on pair 2 while it is transmitting and , the hub detects a collision by the presence of a signal on pair 1 8.7.2:Switched Fast Ethernet • In order to allow multiple access/transfers to be in progress concurrently, two developments have been made: – Switch hub architecture – Duplex working over the circuits that connect the stations to the hub. • Fig 8.29 8.8:LAN protocol 8.8.1:Physical layer 8.8.2:MAC sublayer 8.8.3:LLC sublayer 8.8.4:Network layer • IPX – connectionless • TCP/IP 8.9:Multicast LAN interconnect technologies • • • • 8.9.1:Intersite gateways 8.9.2:ISDN switched connection 8.9.3:Frame relay 8.9.4:High bit rate leased lines 8.9.1:Intersite gateways 8.9.2:ISDN switched connection 8.9.3:Frame relay 8.9.4:High bit rate leased lines Summary