Non-interactive zero
advertisement

Probabilistically checkable proofs,
hidden random bits and
non-interactive zero-knowledge proofs
Jens Groth
University College London
Non-interactive zero-knowledge proof
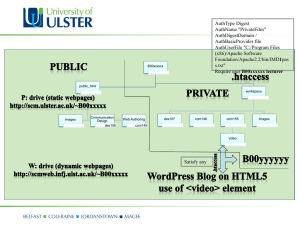
Common reference string:
0100…11010
(x,w)RL
Statement: xL
Proof:
Zero-knowledge:
Prover
Nothing but truth revealed
Soundness:
Verifier
Statement is true
Non-interactive zero-knowledge proofs
Adaptive soundness:
• Statement C is satisfiable circuit
Adversary sees CRS
before attempting to
• Perfect completeness
cheat with false (C,)
• Statistical soundness
• Computational zero-knowledge
• Uniformly random common reference string
• Efficient prover – probabilistic polynomial time
• Deterministic polynomial time verifier
Our results
• Security level: 2-k
• Trapdoor perm size: kT = poly(k)
• Circuit size: |C| = poly(k)
• Witness size: |w| |C|
CRS in bits
Proof in bits
Assumption
Kilian-Petrank
|C|∙kT∙k∙(log k)
|C|∙kT∙k∙(log k)
Trapdoor perms
This talk
|C|∙kT∙polylog(k) |C|∙kT∙polylog(k) Trapdoor perms
CRS in bits
Proof in bits
Assumption
Gentry
poly(k)
|w|∙poly(k)
Lattice-based + NIZK
G-Ostrovsky-Sahai
k3/polylog(k)
|C|∙k3/polylog(k)
Pairing-based
This talk
|C|∙polylog(k)
|C|∙polylog(k)
Naccache-Stern
Other work
poly(k)
|w| + poly(k)
FHE + NIZK
Encrypted random bits
Statement:
(x,w)RL
CRS
E01...0
c1 1)
pk(0;r
E11…1
1pkc(1;r
; 2r2 2)
E00…1
(0;r
pkc
33 3)
K(1k) (pk,sk)
E10…0
0pkc(1;r
; 4r4 4)
xL
Hidden random string - soundness
Statement: xL
(x,w)RL
0
1
0
1
Hidden random string – zero-knowledge
Statement: xL
0
1
Using hidden random bits for NIZK
• Random bits not useful; need bits withProbably
structure
hidden
pairs
• Use statistical sampling to get “good”
blocks
are 00 and 11
10
11
00
01
Statements
|| = O(|C|)
Idea in Kilian-Petrank
Zero-knowledge:
• Interpret pairs of bits as truth Does
values
?1 correspond
– T = {01,10}
F = {00,11}
to T = 01 or F = 11?
10
?0
Soundness: T
F can only be
opened one F
way
11
1?
Completeness:
T can be opened
as 0 or 1
F
00
0?
T
01
?1
Completeness
Reveal: ?0 1? ?1 = 0
F F11
10T 11
Soundness
• If not a satisfying assignment there is a clause
where all literals are false
– x1 x2 x3 gives F F F
• There is 50% chance to catch a cheating prover
– 11, 00, 00 has no opening to XOR = 0 so prover caught
– 11, 00, 11 can be opened to XOR = 0 so prover lucky
• Will use repetition to decrease prover’s chance
Consistency problem
• Cannot let prover designate truth-value pairs to
literals because a cheating prover might choose
an inconsistent assignment
• Need to ensure prover chooses correct and
consistent assignment
I see many bad
Consistency
blocks. Statistically
the remaining hidden
are good.
• Interpret 12-blocks of bits as 6blocks
truth values
– Good block = TTTFFF or FFFTTT
TTTFFF
FTFTFF
FFFTTT
FTFFTF
Consistency
• Divide hidden random bit-string into 12-bit blocks
• Call a block of 6 truth-value pairs for good if it is of
one of these two forms
TTTFFF or FFFTTT
• Prover reveals all bits associated with bad blocks
such that only good blocks remain
Using blocks
Unrevealed bit-pair
shows positive/negative
• Remaining good blocks literals for variable
10?
TTT 011
FFF
TT?
FFF
x1 = F
x2 = T
x3 = F
x4 = F
01?
FFF 110
TTT
FF?
TTT
111 10?
TTT
FFF
TT?
Negative literals
01?
TTT 110
FFF
TT?
FFF
Positive literals
Using blocks
• After discarding bad blocks the remaining hidden
blocks are statistically speaking mostly good
• We assign each block to a variable xi in a
deterministic way
• Each block has 6 truth-values TTTFFF or FFFTTT
– If xi = T reveal 5 bits in TTTFF? or FF?TTT
– If xi = F reveal 5 bits in TT?FFF or FFFTT?
– Revelations correspond to 5 appearances xi, xi, xi, xi, xi
• The last unrevealed truth-value uniquely determines the
assignment of truth-values to literals
• The verifier now checks all clauses XOR to 0
Soundness
• The prover has several degrees of freedom
– Can choose which false statement to prove
– Can choose the public key for the encryption scheme,
each one of which will give different hidden random bits
– Can choose the truth-value assignment
– May leave a few bad blocks unrevealed
• Use repetition to lower risk of cheating
– Instead of revealing single bits for each literal we will
reveal several bit-strings and in each clause all bitstrings most XOR to 0
• Statistical analysis shows with sufficient repetition
a prover has negligible chance of cheating
Two new techniques
• More efficient use of hidden random bits
– Kilian-Petrank:|C|∙k∙(log(k)) hidden random bits
– This work:
|C|∙polylog(k) hidden random bits
• More efficient implementation of hidden bits
– Trapdoor permutations:
kT = poly(k) bits per hidden random bit
– Naccache-Stern encryption:
O(log k)
bits per hidden random bit
Traditional proofs
(x,w)RL
Proof:
The statement
is
Statement:
xL
true because bla
bla bla bla bla
bla bla bla. QED
I’d better
read it very
carefully
Probabilistically checkable proofs
(x,w)RL
Proof:
ThexL
statement is
Statement:
true because bla
bla bla bla bla
bla bla bla. QED
Ok, let me
spot check
in random
places
Satisfiability of 3SAT5 formula
Satisfiability of gap-3SAT5 formula
Witness-preserving assignment tester
• Polynomial time algorithms f, fw:
f: C
fw: w x
belongs to gap-3SAT5
if C(w)=1 then (x)=1
• With the most efficient probabilistically checkable
proofs (Dinur 07 combined with BenSassonSudan 08) we have || = |C| polylog(k)
Strategy
• Want to prove C is satisfiable
• Compute = f(C) and prove that it is satisfiable
using Kilian-Petrank techniques from before
• With the most efficient assignment testers we
have || = |C| polylog(k) so statement is larger
• However, since allows for a constant fraction of
“errors” less repetition is needed to make the
overall soundness error negligible
• It is ok if the prover cheats on some clauses as
long as cannot cheat on a constant fraction
Remarks
• Probabilistically checkable proofs have been used
in interactive zero-knowledge proofs
– Prover commits to PCP
– Verifier chooses at random some parts to check
– Prover opens and reveals those parts of the PCP
• We are using PCPs in a different way
– The verifier will check all parts of the PCP
– The checks have a small error probability
– But unlikely that prover can cheat on a constant fraction
Implementing the hidden random bits model
Statement: xL
CRS
(x,w)RL
E01...0
c1 1)
pk(0;r
E11…1
1pkc(1;r
; 2r2 2)
E00…1
(0;r
pkc
33 3)
K(1k) (pk,sk)
E10…0
0pkc(1;r
; 4r4 4)
Naccache-Stern encryption
• pk = (M,P,g)
sk = (M)
– M is an RSA modulus
– P = p1p2…pd where p1,…,pd are O(log k) bit primes
– P | ord(g) = (M)/4 and |P| = (|M|)
• Epk(m;r) = gmrP mod M
• Dsk(c):
For each pi compute m mod pi
c(M)/pi = (gmrP)(M)/pi = (gm(M)/pi)(r(M)P/pi) = (g(M)/pi)m
Chinese remainder gives us m mod P
Naccache-Stern implementation of hidden bits
Statement: xL
(x,w)RL
CRS
?1?
E01...0
(010;r
; 1 1)
pkc
1
10?
E
(101;r
11…1
pkc
2; 2 2)
??1
;
E
(011;r
00…1
pkc
3 3 3)
K(1k) (pk,sk)
E
???
10…0
c4; 4 4)
pk(110;r
0 if m mod pi even
1 if m mod pi odd
if m mod pi is -1
Revealing part of Naccache-Stern plaintext
•
•
•
•
•
•
•
Ciphertext c = gmrP
How to prove that m = x mod pi?
Prover reveals such that P = (cg-x)P/pi
We can raise both sides to (M)/P
Gives us (M) = (gm-xrP)(M)/pi = (g(M)/pi)m-x
Implies 1 = (g(M)/pi)m-x
Since the order of (g(M)/pi) is pi this shows
m = x mod pi
Revealing part of Naccache-Stern plaintext
•
•
•
•
•
Ciphertext c = gmrP
How to prove that m = x mod pi?
Prover reveals such that P = (cg-x)P/pi
-1 mod (M)/P)P/p
-x
(P
i
Can compute the proof as = (cg )
Can randomize proof by multiplying with s(M)/P
• Generalizes to reveal m = x mod iSpi with a
proof consisting of one group element
Zero-knowledge
• Simulator sets up pk = (M,P,g) such that
ord(g) = (M)/4P and g = hP mod M
• Simulator also sets up the CRS such that it
contains ciphertexts of the form c = sP mod M
• For any m ZP we can compute r = h-ms mod M
such that
sP = gm(g-m)sP = gmh-mPsP = gmrP mod M
• This means the simulator can open each
ciphertext to arbitrary hidden bits using = r
Final step – showing the key is valid
• The public key is pk = (M,P,g)
• The verifier can easily check P is a product of
small primes p1,…,pd
• But needs to be convinced M and g are ok
• Can do this with trapdoor permutation based NIZK
– Statement is small so it does not affect total cost
– Trapdoor permutations implied by Naccache-Stern
• So we use a small seeder NIZK to build large
scale NIZK from Naccache-Stern encryption
Summary
• Technique 1: Reduce soundness error with
probabilistically checkable proofs
Hidden bits
Proof in bits
Assumption
Kilian-Petrank
|C|∙kT∙k∙(log k)
|C|∙kT∙k∙(log k)
Trapdoor perms
This work
|C|∙kT∙polylog(k)
|C|∙kT∙polylog(k)
Trapdoor perms
• Technique 2: Implement hidden random bit string
with Naccache-Stern encryption
CRS in bits
Proof in bits
Assumption
Gentry
poly(k)
|w|∙poly(k)
Lattice-based + NIZK
G-Ostrovsky-Sahai
k3/polylog(k)
|C|∙k3/polylog(k)
Pairing-based
This talk
|C|∙polylog(k)
|C|∙polylog(k)
Naccache-Stern
Other work
poly(k)
|w| + poly(k)
FHE + NIZK