Rehashing Techniques: Collision Resolution in Hashing
advertisement

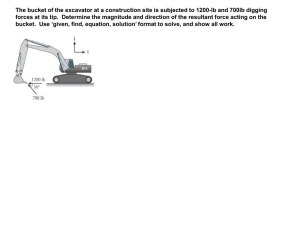
When collision occur, how do we resolve the problem???? Rehashing Techniques Prepared by Perla P. Cosme 1 Topic Outline 1. Addressing Techniques b. Direct Mapping a.1 Absolute Addressing a.2 Relative Addressing c. Directory Look-up b.1 Directory Structure as a Table b.2 Directory Structure as a Tree c. Address Calculation or Hashing 2. Address Calculation 3. Rehashing Strategies Prepared by: Perla P. Cosme 2 Rehashing Techniques 1. 2. 3. 4. 5. 6. 7. Linear Probing Two-Pass File Creation Separate Overflow Area Double Hashing Synonym Chaining Bucket Addressing Bucket Chaining Prepared by: Perla P. Cosme 3 Preliminaries To illustrate how each of the different rehashing techniques work, we shall apply these rehashing techniques to a group of words (the words the primary keys). Note: Primary keys need not, be an integer at all times; it may also of character data type. Prepared by Perla P. Cosme 4 Preliminaries These words were subjected to a hashing function to get their relative positions. The hash(ing) function is described as follows: 1. Take the ASCII value of each letter in the word. The ASCII table maybe found in almost any Computer Science or IT book; usually found in the appendix. Or, simply download one from the internet. 2. If not available in the ASCII table, convert the decimal equivalent of the letter into its binary form. Consider only the first 5 significant bits (b4b3b2b1b0) (Why?) 3. Apply XOR operation to binary numbers of the word. 4. The result is converted into its decimal equivalent. The decimal number is the relative position. Prepared by Perla P. Cosme 5 An Example Let the word to be hashed is THE. Then, relative position of the primary key, THE is 25. hash(THE) = ASCII(T) xor ASCII(H) xor ASCII(E) = 101002 xor 010002 xor 001012 = 110012 = 2510 Prepared by Perla P. Cosme 6 Let’s try this … Question: Using the same hash function, what would be the relative position of the word OF? Answer: 9 (How did we get the answer?) Prepared by Perla P. Cosme 7 Hash Function Description If we do the same process (or hashing all the words) to some common words such as those on Table 1, then, we can complete their relative positions, too. (see Table 1 – next slide, please). Prepared by Perla P. Cosme 8 Table 1. Relative addresses of the Hashed word WORD Hash(WORD) WORD Hash(WORD) WORD Hash(WORD) THE 25 IT 29 NOT 21 OF 9* WITH 2 NO 1 AND 11 AS 18 TON 21 TO 27 HIS 18 SAYS 24 A 1 ON 1 ARE 22 IN 7 BE 7 BUT 3 THAT 9* AT 21 FROM 22 IS 26 BY 27 OR 29 WAS 5 I 9 HAVE 26 HE 13 THIS 6 AN 15 FOR 27 HAD 13 THEY 0 Prepared by Perla P. Cosme 9 Some Notes About Table 1 1. The relative positions generated from the hash function ranges from 0..29 only. (why?) 2. The results or the relative positions creates a lot of collisions – best example to handle collision. Prepared by Perla P. Cosme 10 From this time thereon, we shall refer to Table 1 to illustrate how the different rehashing techniques work. Advise: Keep a copy of the table close to you as we illustrate the rehashing technique. Prepared by Perla P. Cosme 11 Rehashing Techniques 1. 2. 3. 4. 5. 6. 7. Linear Probing Two-Pass File Separate Overflow Area Double Hashing Synonym Chaining Bucket Addressing Bucket Chaining Prepared by: Perla P. Cosme 12 Question How do we handle collisions given the values in Table 1 using Linear Probing Technique? Answer: (Please refer to the board on how the collisions are handled.) Prepared by Perla P. Cosme 13 Rehashing Techniques 1. 2. 3. 4. 5. 6. 7. Linear Probing Two-Pass File Creation Separate Overflow Area Double Hashing Synonym Chaining Bucket Addressing Bucket Chaining Prepared by: Perla P. Cosme 14 Rehashing Techniques 1. 2. 3. 4. 5. 6. 7. Linear Probing Two-Pass File Creation Separate Overflow Area Double Hashing Synonym Chaining Bucket Addressing Bucket Chaining Prepared by: Perla P. Cosme 15 Rehashing Techniques 1. 2. 3. 4. 5. 6. 7. Linear Probing Two-Pass File Creation Separate Overflow Area Double Hashing Synonym Chaining Bucket Addressing Bucket Chaining Prepared by: Perla P. Cosme 16 Rehashing Techniques 1. 2. 3. 4. 5. 6. 7. Linear Probing Two-Pass File Creation Separate Overflow Area Double Hashing Synonym Chaining Bucket Addressing Bucket Chaining Prepared by: Perla P. Cosme 17 Rehashing Techniques 1. 2. 3. 4. 5. 6. 7. Linear Probing Two-Pass File Creation Separate Overflow Area Double Hashing Synonym Chaining Bucket Addressing Bucket Chaining Prepared by: Perla P. Cosme 18 Rehashing Techniques 1. 2. 3. 4. 5. 6. 7. Linear Probing Two-Pass File Creation Separate Overflow Area Double Hashing Synonym Chaining Bucket Addressing Bucket Chaining Prepared by: Perla P. Cosme 19